Hashing vs Encryption — The Big Players of the Cyber Security World
Hashing vs encryption — what exactly do these terms mean?
Encryption is used to scramble or encode a message or a file so that unauthorized users can’t tamper with or steal sensitive information. Hashing is useful in verifying the actual integrity of a file to prevent anybody from changing the content of a file or corrupting it and passing it off as the original file. They both sound very similar. So, what’s the difference between hashing and encryption? In a nutshell, encryption is more focused on data confidentiality, whereas hashing deals with data integrity.
We can’t replace hashing with encryption, or vice versa, because they are different concepts implemented in various scenarios to achieve different goals. In case any situation demands both functions to be deployed, it’s advisable by most security researchers to follow the encrypt-then-hash paradigm. Though theoretically more secure, it’s also harder to achieve.
Hashing vs Encryption: What is Encryption?
Encryption is the process in which plaintext data gets scrambled into seemingly gibberish information that, if intercepted by a malicious user on the network, is entirely incomprehensible. A mathematical algorithm is applied to encode the original message into ciphertext that can only be decoded by its intended recipient.
For example, consider Todd has suddenly come into some fortune and inherited valuables from his great grandmother. He decides to place these items in a safety deposit box that’s stored in a secured bank vault. Anyone looking at the vault will not automatically find out its contents. Only if Todd shares the key can the vault and the box inside it be opened, and its items be accessed.
ROT13 is one example of an encryption cipher or algorithm. As a variant of the Caesar cipher, it basically shifts each letter 13 places away in the alphabet.
The above example, though a weak encryption algorithm, illustrates the simple concept that encrypted data is reversible.
Let’s consider the following example: Alice is sending an email to Bob, and she encrypts it so that anyone eavesdropping on the network (such as a man-in-the-middle attacker) is unable to make sense of the data. However, it would be a futile exercise if Bob, on the receiving end, can’t decrypt and read the message.
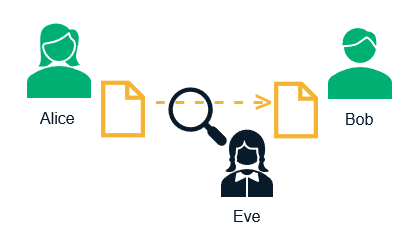
To aid this process, Alice uses Bob’s public key and her private key to encrypt her message. Now, only Bob can decrypt the message using his private key and Alice’s public key. A third party, Eve, who is listening over the wire, doesn’t have Bob’s private key. Therefore, she is unable to decrypt the message and is left with a stream of garbled data.
Types of Encryption:
There are two main categories of encryption:
Asymmetric Encryption — This encryption process involves two different keys. One key encrypts (public key) while the other key (private key) decrypts. This encryption is the foundation for public key infrastructure (PKI), which is the trust model on which SSL/TLS is based.
Symmetric Encryption — This type of encryption uses the same key to both encrypt and decrypt a message. Because there’s only one key involved, it’s a faster type of encryption that requires less processing power to compute.
In the SSL/TLS handshake process, the secret key is shared using asymmetric encryption. Once the key has been exchanged the browser and server communicates using the symmetric session key that is passed along.
Asymmetric encryption is considered to be stronger and more secure owing to its one-way nature.
Some Common Encryption Algorithms
Let’s take a look at some of the most common encryption algorithms:
- Advanced Encryption Standard (AES) – AES is an extremely efficient symmetric block cipher that’s trusted as a standard by numerous organizations. AES has proven to be reliable since the only practical successful attacks against it have leveraged side-channel attacks.
- Triple DES – Designed to replace the original Data Encryption Standard (DES), triple DES uses three individual keys with 56 bits each. Though a considerable improvement over DES in terms of security, it’s now considered a legacy encryption algorithm.
- RSA – Named after its creators Rivest-Shamir-Adleman, RSA is a public key encryption algorithm that was developed in 1977 and is still in use today. In RSA, both the public and the private keys can encrypt a message while the opposite key from the one used in encryption is used to decrypt it.
Hashing vs Encryption: What is Hashing?
Hashing is the process of converting an input of variable length to a fixed size array of numbers and letters using a mathematical function.
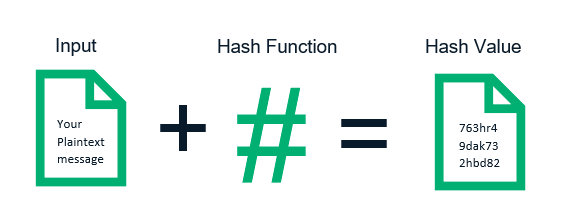
Let us look at an oversimplified example to grasp the idea of hashing better. Suppose Todd has decided to bake a cake for his daughter’s birthday. He assembles the ingredients (sugar, eggs, flour, baking powder, etc.) and, once it is properly baked, he has the perfect birthday cake ready. Todd, however, can’t revert the cake back to an assortment of its individual ingredients, nor can he discern the exact amount of each component from two such cakes. So, we have the input (the items used), and we apply the hash function (in this example, it’s the mixing and baking process) to get a unique message digest (the cake).
What are some key traits of hashing?
- Each hash value or output must be unique.
- Hashing speed is also a factor. A hash function should be reasonably quick to produce a hash value.
- A hash function needs to be secure. Even a slight change to the input file should produce a vastly different hash value.
- It is immutable in the sense that the same input must produce the exact same hash.
- It is irreversible, i.e., it’s not possible to arrive at the original input file from its hash value.
Some Common Hashing Algorithms
The following are some of the most common hashing algorithms in use today:
- MD4 and MD5 — MD4 was created in 1990 by Ronal Rivest. However, using this algorithm gives rise to a series of security concerns. MD5 was created as its successor; while its security is slightly improved, MD5 is also known to suffer from vulnerabilities. Salts are added typically to protect password hashes (as a preventive measure against brute force attacks). While using weak hashing functions such as MD5, salting is a must and so is ensuring the salt remains uncompromised.
- SHA (Security Hashing Algorithm) — There are three different SHA algorithms: SHA-0, SHA-1, and SHA-2. With SHA-1 being deprecated, SHA-2 is used in most SSL/TLS cipher suites. SHA-256 or above is the recommendation for security critical applications.
- Tiger — This is a faster and improved 192-bit hashing function that was developed by Ross Anderson and Eli Biham in 1996. Tiger doesn’t suffer from the known vulnerabilities of MD5 and SHA-0/SHA-1. In the Tiger2 variant, the message is padded with a hexadecimal value of 0x80 instead of 0x01 as in Tiger. The two variants are otherwise identical.
Hashing vs Encryption
The table below lists the differences between hashing and encryption:
| Encryption | Hashing |
|---|---|
| Encryption is a two-way function where information is scrambled using an encryption key and unscrambled later using a decryption key. | Hashing is a one-way function where a unique message digest is generated from an input file or a string of text. No keys are used. |
| The message is encoded in a way that only authorized parties can access it. It’s used to prevent unauthorized users from reading data from a file by rendering it into an unreadable form. | Hashing is the process of using hash functions on data to map it to a fixed size output. It’s similar to a checksum and is used for verifying file integrity. Hashing is useful where you want to compare an entered value with a stored value without needing to read the original content of the file. |
| The resultant encrypted string is of a variable length. | The resultant hashed string is of a fixed length. |
| The original message can always be retrieved by using the appropriate decryption key. | Output can’t be reverted to the original message. The best hashing algorithms are designed in a way that makes it virtually impossible to retrieve the original string from the hash value. |
| There are two primary types of encryption: Symmetric key encryption (or private key encryption) andAsymmetric key encryption (or public key encryption) Examples of encryption algorithms: RSA, AES, DES, etc. | Examples of hashing algorithms: SHA-1, SHA-2, MD5, Tiger, etc. |
| Purpose of encryption is to transmit data securely (i.e., protect data confidentiality) | The objective of using hashing is to verify data (i.e., protect data integrity) |







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)
















 (19 votes, average: 4.79 out of 5)
(19 votes, average: 4.79 out of 5)


![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-300x200.jpg)



No comments