What Is a Quantum-Safe Hybrid Digital Certificate?
Sectigo’s Tim Callan, Jason Soroko and Alan Grau break down what quantum safe hybrid TLS certificates are and how they can help to prepare businesses for quantum-safe cryptography in Sectigo’s Root Causes podcast
Quantum computing is poised to disrupt the technological world as we know it. And although quantum computing — and all of the advantages it offers — is still realistically years away, businesses and organizations need to prepare themselves for its inevitable downside: broken cryptosystems.
Quantum computers will break our existing asymmetric cryptosystem — something that cybercriminals will be ready and eager to take advantage of. This is why it’ll be necessary to migrate your existing IT and cryptosystems to their quantum-resistant or quantum-safe equivalents.
But, of course, upgrading to post quantum cryptographic (PQC) systems and infrastructure takes time and resources. So, one of the ways to help futureproof your cyber security through this process is through the use of hybrid digital certificates such as a hybrid TLS certificate.
In the podcast, Tim Callahan, Jason Soroko and Alan Grau break down the subtle but important distinctions to know about quantum-safe hybrid digital certificates.
What Is a Hybrid Digital Certificate?
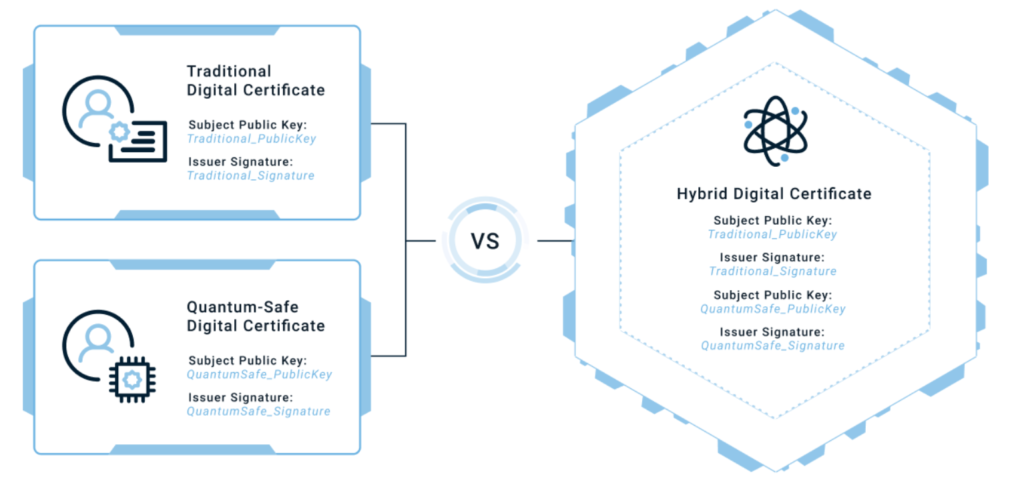
A hybrid certificate is essentially a traditional X.509 digital certificate that has additional quantum-safe components encoded within it. This type of certificate, also known as a cross-signed hybrid certificate, is a versatile way to enable your servers to meet the needs of different clients (web browsers) to allow them to connect regardless of their crypto capabilities.
However, it’s important to note that hybrid digital certificates are a means to an end but aren’t the end solution in and of themselves. What we mean is that hybrid certificates help to bridge the gap between PQC-enabled systems and non-upgraded systems through versatility. This helps during the transition period, but the ultimate goal is for everyone — clients and enterprises alike — to use quantum safe cryptography.
What this type of certificate offers is cryptographic agility, or crypto agility. (We’ll speak more on the topic of crypto agility later.) Basically, once your business starts the transition to quantum-safe systems and applications, you won’t have to try to support two separate certificates — a traditional digital certificate and a quantum-safe digital certificate — since you’d already have a two-in-one hybrid certificate in place. This provides interoperability during the transition period.
How Secure Connections Work Within Our Current Pre-Quantum Ecosystem
Website security as we know it relies on something known as public key infrastructure (PKI). This combination of policies, procedures and technologies that support public key cryptography. Examples of traditional X.509 certificates include:
- TLS certificates (transport layer security), formerly known as SSL certificates (secure sockets layer).
- Code signing certificates.
- Document signing certificates.
- Email signing certificates.
In public key cryptography, we use these certificates to help authenticate and provide encryption. For example, an SSL/TLS certificate authenticates the server that a client connects to and also creates a secure, encrypted connection between the two parties.
How Does a Hybrid TLS Certificate Differ from a Traditional One?
All TLS certificates contain digital signatures, keys, and algorithms. The difference between a traditional TLS certificate and Sectigo hybrid TLS certificate is that in addition to those traditional components:
- The hybrid certificate would contain extra X.509 certificate fields for quantum-safe keys and signatures.
- The hybrid certificate would include the encoding for a quantum safe algorithm.
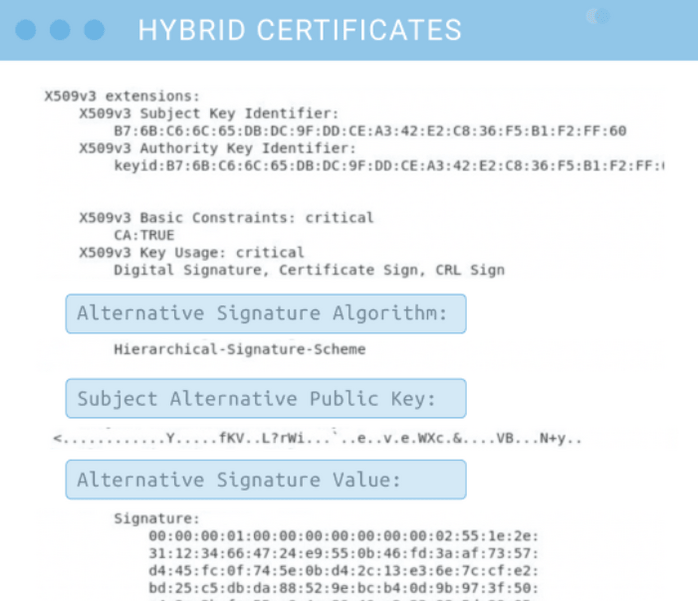
This means that even though the structure of the X-509 certificate changed, it won’t be an issue for legacy systems that receive the certificate. They’ll see fields in the certificate that they won’t recognize and will simply ignore them. As a result, legacy systems will still be able to connect right away using the existing public key algorithms that the hybrid certificates continue to support even though those certificates now also support PQC algorithms.
This means that you don’t immediately have to start upgrading your legacy systems to start using hybrid certificates, guest speaker Alan Grau explains. Rather, they can be pulled in more gradually as you update your devices and servers over time.
Podcast co-host Jason Soroko follows up with a key takeaway:
“What it means, in very plain English, is that somebody could take the toolkit today, start issuing these X-509 certificates with, say, an ECC encryption chosen with the alternate fields and traditional systems and not break a single thing.”
How a Hybrid TLS Certificate Works in Authentication
Podcast co-host Tim Callan approximates using hybrid digital certificates to being bilingual. Basically, if you speak English and French, and the person you’re communicating with does as well, then you could choose to communicate using either language. Likewise, if you’re bilingual and you’re speaking with someone who only speaks English or only speaks French, you can still communicate with them as well just as efficiently.
Grau describes it with the analogy of changing the lock on the front door of a boarding house that has multiple residents. If only one of those residents is there to receive the new stronger and more secure key (quantum safe crypto algorithm), they’d be able to use the front door. But if others aren’t there when the lock is swapped out, then they’d still have to use the back door and the less secure key (traditional crypto algorithm).
“[…] so as people access the house and you give them the new key, they start using the new front door lock with the new key that’s stronger and more secure. But even as people trail in through the back door, you can start to see who still needs to be updated. But you’ve got a period of time when both the old key and the new key can be utilized.”
It’s much the same with the hybrid certificate. So, no matter whether your users’ clients are using quantum systems or non-updated ones, authentication will still be possible without issues or disruptions. Basically, you can serve both audiences without any delays or interruptions until you can eventually make the full switch to quantum-safe algorithms only.
Of course, this type of transition won’t happen overnight. From a global perspective, it’ll take years — “a decade or more,” according to Grau. It would also likely take individual enterprises several years as well depending on their size, capabilities, and the number of internal and third-party systems that are involved.
How a Hybrid TLS Certificate Factors Into Establishing Secure Connections
When you connect to a web server via your browser using modern cryptosystems and TLS certificates, there’s a process that takes place known as a TLS handshake. Part of this process involves a negotiation that helps to determine which encryption algorithm (such as RSA, ECC, etc.) will be used to communicate between the parties.
As Grau explains:
“[…] most web servers will support some different options so they can support different versions of clients that support, perhaps, slightly different versions of TLS or keys. So, that sort of negotiation goes on today, but in a very narrow band of known encryption algorithms.”
With post quantum cryptography, the idea here is very similar. The exception, though, is that as you upgrade your systems to use the new quantum safe crypto algorithms and if you have hybrid certificates in place. Then, the idea here is that those new PQC algorithms will be put to use as they can be instead of RSA or ECC.
“The work has to happen on all of those systems. We’re not going to turn on the switch and one day we’re at RSA and the next everything’s on post quantum encryption.”
So, Just What Is a Quantum Safe Algorithm?
That’s a great question. The National Institute of Standards and Technology (NIST) is still working to define those algorithms. NIST began the process in 2017 with 69 potential algorithms to choose from that met specific criteria. As of July 2020, they’ve narrowed a list down to just 15 algorithms that made it through NIST’s PQC standardization process (so far). The list of algorithms include:
- Four third-round finalists for public key encryption and key-establishment algorithms: Classic McEliece, CRYSTALS-KYBER, NTRU, and SABER.
- Three third-round finalists for digital signatures: CRYSTALS-DILITHIUM, FALCON, and Rainbow.
- Eight third-round alternate candidate algorithms: Bike, FrodoKEM, HQC, NTRU Prime, SIKE, GeMSS, Picnic, and SPHINCS+.
So, why aren’t they narrowing it down to just one algorithm? Part of that is likely because they’d want to have different algorithms for different use cases and to allow for general cryptographic redundancy. After all, you wouldn’t want to just narrowly focus on only one tool in case it doesn’t work out — it’s best to have a few options.
Why Crypto Agility Is So Important to a Post Quantum World
Soroko cautions that assuming that NIST’s final selection will be set in stone is a mistake. This is because NIST has indicated interest in a lattice approach because of the strength of the algorithm, its factorability, and its reasonable key sizes. However, Soroko says that there are other approaches that could be optimized for various applications.
This is why being crypto-agile is crucial as businesses transition to quantum-safe environments. As standards change over time and algorithms deprecate, having tools that offer crypto agility helps to keep you from being caught unprepared.
“One of the things we may end up finding is that there’s an ah-ha moment — or, more than likely, an uh-oh moment — which is where cryptographic agility is something we’re going to need long term.” — Jason Soroko
These hybrid certificates will afford your organization the cryptographic agility you’ll need to move to PQC algorithms down the road when it becomes necessary. However, an added bonus is that they’ll also enable you to switch between RSA and ECC connections in the meantime as well when necessary.
The Challenges of Preparing Your Business or Enterprise to Be Quantum Safe
As you can imagine, preparing your business and IT infrastructure for the coming quantum transformation is going to be a lot of work. For proper implementation, these changes will essentially touch everything within your IT ecosystem.
Guest speaker Alan Grau provides an overview of some of the changes you’ll need to make:
“When you look at migrating your PKI systems from existing traditional algorithms to quantum safe algorithms, that really is a huge undertaking because there’s a number of steps that have to happen. You need to upgrade the PKI system, you need to upgrade the servers, you need to upgrade the clients.”
When it comes to preparing for quantum-safe code signing, you’ll also need to upgrade the signing application and the validation applications.
You’ll have to ensure that your internal and external third-party systems are all brought up to speed to be quantum safe.
What Makes This Type of Upgrade Difficult At Scale
RSA encryption has been the go-to for encryption for decades, and ECC has been picking up traction over time as well. However, once quantum cryptography becomes commercialized, it means that everything we as an industry currently have in place will become legacy and outdated systems.
“If you were making a system, you could just safely assume that the presence of RSA would be there. So, everything we have — every piece of software, every piece of firmware, every piece of hardware, every service in the global economy — is built on that compatibility.” — Tim Callahan
But what happens when RSA or ECC become vulnerable because of QC? Grau drives home the point that it’s not just the client and server applications need to be upgraded with new crypto algorithms — it’s the entire crypto structure. But, as you can imagine, these types of sweeping changes take resources — time, labor, and money. This is especially the case for enterprises that have to make these changes at scale.
And, often times, Callahan says, this means that companies will be doing it piecemeal to make the transition process less resource intensive. As a result, some of these new quantum-safe systems will have to coexist with legacy systems in the meantime — and this is why there’s a need for hybrid TLS certificates.
Of course, these hybrid certificates don’t mean that your IT and network guys can kick back and relax. Within your own organization, your sys admins will still need to monitor their systems and networks to stay abreast of which users and applications are using outdated algorithms and certificates. This way, they know what still needs to be upgraded before your organization fully transitions to being quantum safe.
Why Quantum Cryptography Is a Concern for Data Security
The concept of quantum computing and the concerns that stem from quantum cryptography aren’t all that new. The concept of quantum computing has been around for decades after it first came onto the scene in the 80s. However, it wasn’t until the mid-90s that concerns about its impact on cryptography really started to take hold. That’s when mathematician Peter Shor developed a quantum algorithm (Shor’s Algorithm) that could solve the factoring problem of large integers.
This highlighted the concern that our existing public key cryptographic tools could be vulnerable to quantum computer-based attacks. And considering that digital information around the world is widely protected using public key cryptography, that’s a very real concern.
Now, of course, the good news is that quantum computing isn’t going to rolling out tomorrow. So, it’s not an immediate threat. However, quantum computing is on the horizon and is something that every business must start preparing for.
But what happens to your secure connections once quantum computing does go commercial? If you’re using a hybrid digital certificate that supports both quantum-safe algorithms and vulnerable algorithms like RSA and ECC, does it somehow leave you vulnerable? Not if you’re using PQC algorithms for your connections.
What the Transition Will Look Like as We Move to PQC Systems Globally
As with any big change, the move to using post quantum cryptography in the global ecosystem is going to take time and requires a period of adjustment. And the idea is that hybrid certificates can help to serve as a go-between for the PQC systems and those using vulnerable algorithms until everyone gets their systems and applications up to speed.
According to Grau, hybrid certificates are a means to an end but aren’t the end goal themselves:
“The transition period really is designed as a transition period. Any connections that are using the old encryption algorithms no longer are going to be secure once quantum computers have hit that point that they can crack these encryption algorithms. So, once things are switched over, it’s really critical that we deprecate the ECC and RSA roots and switch them over to pure quantum safe certificates.”
Get to Know the Podcast Hosts and Guest Speaker
Sectigo’s Senior Fellow Tim Callan and CTO of PKI Jason Soroko host the podcast, which features Alan Grau, VP of IoT and Embedded Solutions.
Tim Callan is a fount of knowledge when it comes to PKI and SSL technologies. He has more than 20 years of experience in strategy marketing for SaaS and B2B software companies.
Jason Soroko is a security technology innovator who has served as an architect and developer of complex data structures and GIS technologies. His areas of expertise include climate statistics and spatial mathematics.
Alan Grau joined the team when his company, Icon Labs, was acquired by Sectigo in May 2019. He’s involves with Sectigo’s Quantum Labs initiatives and has 30 years of experience in telecommunications and the embedded software marketplace.
Final Thoughts on Hybrid Certificates
Hybrid digital certificates are all about making you crypto agile. It’s what will allow clients using upgraded systems to connect using the highest level of security without leaving any of your customers out in the cold. This way, you can serve customers who are using PQC-enabled clients while still serving those whose clients don’t yet support PQC.
Want to hear more? Tune in to listen to the full podcast.







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)






 (9 votes, average: 4.56 out of 5)
(9 votes, average: 4.56 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security