Zero Day: What Is a Zero Day Attack, Exploit or Vulnerability?
Although zero day attacks aren’t the leading cause of data breaches, that doesn’t mean that these types of attacks can’t affect your organization in other ways
A zero day attack is the sucker punch that you may not see coming.
In the cybersecurity industry, we spend all day talking about the dangers of cyber attacks and how we need to harden our defenses against known attacks. But what can you do to protect yourself against a type of threat that you might not even know exists (or have only recently discovered)?
What is a Zero Day Vulnerability, Zero Day Exploit, or Zero Day Attack?
Okay, there are a lot of terms that get thrown around relating to zero day ____ — zero day vulnerability, zero day exploit, zero day attack, n-day attack, etc. But what you may (or may not) realize is that not all of these terms are not interchangeable and have related but different meanings. Let’s break ‘em down, starting with zero day vulnerabilities, to provide a little clarity about each of the terms.
Zero Day Vulnerability
A zero day vulnerability is a chink or weakness in your armor that you may or may not yet know exists. This is something that could be exploited in an attack if someone chose to do so, but it’s not actually about the attack itself. A zero day vulnerability may have been publicly disclosed by researchers or vendors, but it’s something that hasn’t yet been patched.
Yeah, it’s tricky. A zero day vulnerability is something that you can often find in software, firmware, or hardware and can include examples like:
- Flaws in operating systems.
- Bugs in popular (and lesser known) software applications.
- Critical holes in firmware.
Now, once an update or patch has been issued for the vulnerability, Trend Micro says that it’s no longer considered a zero day vulnerability and instead becomes known as an “n-day” vulnerability. However, some sites and organizations lump zero day attacks and n-day attacks together because they’re both something that threat actors can use to their advantage.
Zero Day Attack (or Zero Day Exploit, Zero Hour Attack, etc.)
A zero day attack, on the other hand, is a term that involves taking advantage of that unknown (or publicly disclosed) vulnerability to do something bad.
The National Institute of Standards and Technology (NIST) succinctly defines a zero day attack as “an attack that exploits a previously unknown hardware, firmware or software vulnerability.” Basically, it’s an advanced type of cyber attack that occurs when a cybercriminal exploits a gap in your security before you have a chance to patch it. (Hence why some people use the terms “zero day attack” and “zero day exploit” interchangeably.)
Trend Micro also has a great description for these types of exploits or attacks:
“When hackers or threat actors successfully develop and deploy proofs of concept (PoCs) or an actual malware that exploits the vulnerability while the vendor is still working on rolling out a patch (or sometimes, unaware of the vulnerability’s existence), it becomes a zero-day exploit or attack.”
Basically, the difference between these terms can be pictured in a very simple way. Imagine that you have a sturdy, reinforced concrete wall protecting your organization. A zero day vulnerability represents the existence of a crack or hole in that barrier that you haven’t noticed. A zero day exploit would be when an enemy actually mounts an attack and comes through that hole or crevasse.
What Makes Zero Day Attacks Such a Threat
FireEye Mandiant Threat Intelligence research shows that there were “more zero-days exploited in 2019 than any of the previous three years.”
It’s virtually impossible to prevent zero day attacks as a whole. Why? Because the definition of a zero day attack is an attack that takes advantage of vulnerabilities that you don’t know exist or are newly discovered. How can you block a punch when you don’t know one’s coming? This is where the people mentioned in the next section can help.
But first, it’s important to note that the majority of data breaches don’t result from the exploitation of zero day vulnerabilities. Rather, most breaches (and ransomware attacks) often stem from:
- Poor cybersecurity hygiene,
- A severe failure to implement updates and patches, and a
- General lack of cyber awareness amongst employees and other end users.
Who Finds Zero Day Exploits
Is it a little tongue-in-cheek to say “anyone?” But, really, finding zero day vulnerabilities and identifying how to exploit them isn’t something that’s limited to just the “good guys” or the “bad guys.” Even tech-savvy end users can find security issues.
In reality, there are a lot of people who search for zero day vulnerabilities in the wild that can be exploited — vendors, researchers, bug bounty hunters, individual black/white/grey hat hackers, and hacker groups alike. Heck, there’s even a division of Trend Micro — the Zero Day Initiative (ZDI) — that’s dedicated to hunting these bugs and releasing security vulnerability advisories!
Bug bounty hunting can also be very profitable. For example, in 2019 alone, ZDI reported that it awarded more than $1.5 million in cash and other prizes to bug hunters. The contributions of everyone involved resulted in the release of 1,035 advisories in 2019. Of course, these numbers are likely to change throughout 2020 as the vulnerabilities identified in late 2019 will result in advisories in 2020. But the numbers are less than the 1,450 advisories published in 2018.
According to the FireEye Mandiant Threat Intelligence research we mentioned a little bit ago:
“While not every instance of zero-day exploitation can be attributed to a tracked group, we noted that a wider range of tracked actors appear to have gained access to these capabilities. Furthermore, we noted a significant increase over time in the number of zero-days leveraged by groups suspected to be customers of companies that supply offensive cyber capabilities, as well as an increase in zero-days used against targets in the Middle East, and/or by groups with suspected ties to this region. Going forward, we are likely to see a greater variety of actors using zero-days, especially as private vendors continue feeding the demand for offensive cyber weapons.”
How Zero Day Exploits Are Identified
You’ve likely noticed that vulnerabilities are usually identified by long numbers that start with CVE. (For example, CVE-2020-1234, CVE-2019-12345, etc.) But what do these names actually mean? And, moreover, who’s coming up with them?
Who’s Responsible for Naming Common Vulnerabilities and Exploits
There’s a group of organizations that, together, are known as CVE Numbering Authorities (CNAs). These organizations have been given the ability to metaphorically rubber stamp common vulnerabilities and exposures (CVEs) by assigning them ID numbers. These numbers are used to identify the vulnerabilities in their first-time public announcements and are used by a variety of individuals including vendors, researchers, and vulnerability disclosers.
As of May 28, 2020, the MITRE website reports that there are 128 organizations from 21 countries that are CNAs. The overwhelming majority of them — 77 — exist within the United States alone.
What’s in a Name: Let’s Take a Closer Look at CVE Naming Conventions
Let’s break down the naming convention of these vulnerabilities for CVE-2020-1234:
- CVE stands for “common vulnerability and exposure”
- The next four-number component refers to the year in which the vulnerability is discovered
- The next set of numbers, consisting of four or more digits, identifies the specific vulnerability
CVE products include:
- Software (both closed and open source),
- Hardware,
- Cloud and software as a service offering, and/or
- Protocols, standards, and APIs.
If it’s just one product that’s affected, it’s considered a single vulnerability. If multiple products have vulnerabilities, then they would be considered separate vulnerabilities However, many products nowadays tend to share code — in this case, if multiple products share the same vulnerable code, that means that they’d all be lumped under one shared vulnerability ID.
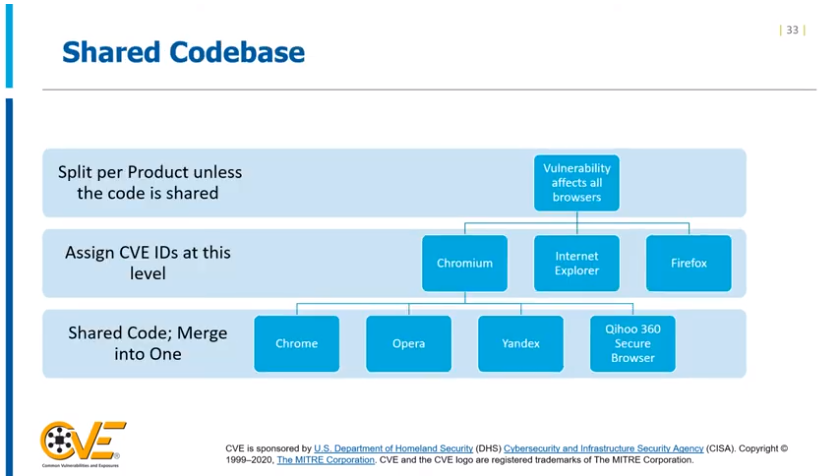
Of course, if a CNA isn’t sure about whether multiple products share the same code, it’s best to err on the side of caution and list them as separate vulnerabilities.
Where to Find the List of Known CVEs
You can search the CVE list on the MITRE website for any specific CVE entries or IDs. You can also find CVEs on the National Vulnerability Database (NVD) page of the NIST website.
Examples of New or Recent Zero Day Vulnerabilities
Now that you know what a zero day vulnerability is and how it works, let’s explore three examples of some critical zero day vulnerabilities.
1. Windows 10 Vulnerability Spoofs Authentication in Executables
Earlier this year, the NSA disclosed a critical vulnerability (CVE-2020-0601) within their public key infrastructure that would affect the cryptographic function of 32- and 64-bit Windows 10 operating systems and specific versions of Windows Server.
This specific type of vulnerability exists in the process of how Windows CryptoAPI validates elliptic curve cryptography (ECC). The risk here is that a bad guy could use a spoofed code signing certificate to exploit this vulnerability and sign an executable to make it believable to unsuspecting users. Of course, attackers can’t pull this off entirely on their own — they’d need a victim to actually engage with it to activate it.
The end result? The signed file would appear to come from a trusted and reputable source. Thankfully, Microsoft was quick to move forward with putting out an advisory and patching the vulnerability.
2. Netgear Zero Day Firmware Vulnerability Leaves Routers Open to Takeover Attacks
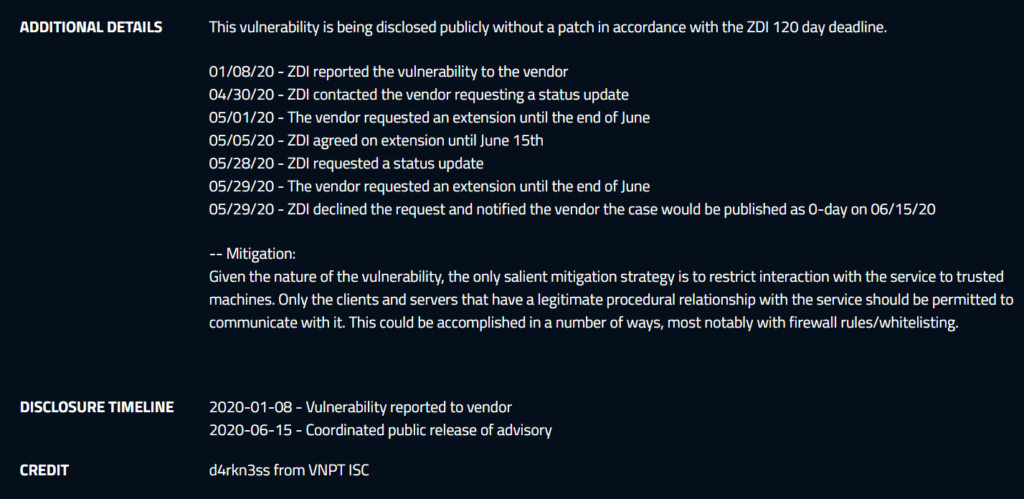
In January 2020, ZDI researchers informed Netgear about an unpatched zero day vulnerability in the firmware of their routers. Initially thought to affect only the R7000 router series, it was later discovered by Grimm cybersecurity firm researcher Adam Nichols to affect “79 Netgear devices and 758 firmware images that included a vulnerable copy of the web server.”
In his blog post on SOHO device exploitation, Nichols says about the vulnerability:
“In most modern software, this vulnerability would be unexploitable. Modern software typically contains stack cookies which would prevent exploitation. However, the R7000 does not use stack cookies. In fact, of all of the Netgear products which share a common codebase, only the D8500 firmware version 1.0.3.29 and the R6300v2 firmware versions 1.0.4.12-1.0.4.20 use stack cookies. However, later versions of the D8500 and R6300v2 stopped using stack cookies, making this vulnerability once again exploitable. This is just one more example of how SOHO device security has fallen behind as compared to other modern software.”
Netgear recently released hotfixes for some of their routers to address some of the vulnerabilities. However, they also state that “Until a firmware fix is available for your product, NETGEAR recommends that you follow the workarounds and best practices in this advisory.”
Here’s a breakdown of the timeline from when Netgear was first notified until the date when the vulnerability advisory was made public:
3. Zyxel Vulnerabilities Within Firmware for NAS and Firewall Solutions
In February 2020, Brian Krebs of Krebs on Security reported that both network attached storage (NAS) devices and firewalls from Zyxel had critical flaws that resulted in zero day vulnerabilities.
The NAS flaw, labeled CVE-2020-9054, took advantage of a pre-authentication command injection vulnerability within specific firmware versions. Essentially, the flaw would allow hackers to remotely execute arbitrary code on affected devices by using an OS command injection.
According to Zyxel’s updated security advisory, the exploit affected UTM, ATP and VPN firewalls running firmware versions ZLD V4.35 Patch 0 through ZLD V4.35 Patch 2. The firmware versions prior to the ZLD V4.35 Patch 0 remained unaffected.
The problem, however, would be that while they had patches available for affected models that fell within warranty and support periods, they weren’t as helpful with legacy systems:
“For affected NAS products that reached end-of-support in 2016 or earlier, firmware updates are no longer provided. We strongly recommend that users follow the workaround procedure […] to remediate the vulnerability.”
3 Real World Zero Day Attack Examples
Now that you’ve seen some examples of zero day vulnerabilities, let’s take a look at some of the biggest zero day attacks that have been carried out in recent years:
1. Hackers Exploit WhatsApp Vulnerability to Distribute Spyware
This critical zero day vulnerability, known as CVE-2019-3568, was discovered as being used to facilitate the spread of malware to specific target devices in 2019. Basically, it was a buffer overflow vulnerability that was used to distribute spyware via affected versions of the WhatsApp mobile app for Windows, iOS and Android. this exploit allowed them to remotely execute code that they’d send to those target phone numbers via RTCP packets.
In a federal lawsuit against Israeli mobile surveillance firm NSO Group, WhatsApp claimed that the group exploited an audio-calling vulnerability to send government-grade spyware to “approximately 1,400 mobile phones and devices.” The idea here is that since WhatsApp is end-to-end encrypted, they had to find a workaround to obtain message data. So, instead of trying to hack the messages directly, they’d go after the devices instead.
Although WhatsApp was quick to patch the vulnerability, others followed behind it, making 2019 a really tough year for the Facebook-owned company.
2. Hackers Use Microsoft Windows Vulnerability to Carry Out Government Espionage in Europe
Buhtrap, a hacker group that’s known for cyber bank robbery initiatives, exploited a Windows OS vulnerability to carry out zero day attacks against Eastern European government institutions in June 2019. Cybersecurity writer Davey Winder explains that the hacker group carried out their attack by exploiting a vulnerability that affected older versions of Windows OSes and Windows Server 2008.
The flaw, identified as CVE-2019-1132, was a privilege escalation issue relating to Win32k memory objects. It was one of the vulnerabilities that Microsoft addressed in a July 9, 2019 patch Tuesday update.
According to a report by SecurityWeek:
“The group used decoy documents to deliver a piece of malware designed to steal passwords from email clients and browsers, and send them to a command and control (C&C) server. The malware also gave attackers full access to the compromised device.”
3. ‘EternalBlue’ Exploit Affected Hundreds of Thousands of Devices Worldwide
2017 marked a bad year for IT administrators and businesses worldwide. It was the year in which EternalBlue, one of several exploits that was developed by the NSA and released by a hacker collective known as the Shadow Brokers, was deployed as part of the WannaCry ransomware attacks.
Of course, the exploit was used in other malware and cyber attacks (TrickBot, WannaMine, Coin Miner, etc.), but WannaCry was one of the first and best known variants because it’s thought to have affected more than 200,000 computers in more than 100 countries.
The way the zero day exploit worked was that it allow hackers to remotely exploit a software vulnerability that existed within Microsoft’s Windows OS server message block (SMB) version 1 protocol. This access would allow them to compromise the entire network that an infected device was connected to, along with any devices associated with the network.
Part of the reason WannaCry was so successful as a cyber attack is that although Microsoft released a patch for EternalBlue the month before the WannaCry attacks began, many businesses failed to deploy the patch on their systems. One such example was the United Kingdom’s National Health Service (NHS).
The UK’s National Audit Office reports that the NHS was warned about security issues relating to legacy systems in advance of the WannaCry attacks but lagged in their response. According to Amyas Morse, the head of the NAO:
“The WannaCry cyber attack had potentially serious implications for the NHS and its ability to provide care to patients. It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice. There are more sophisticated cyber threats out there than WannaCry so the Department and the NHS need to get their act together to ensure the NHS is better protected against future attacks.”
4. Stuxnet Wreaks Havoc on Iranian Nuclear Facility Before Going Public
We’ll conclude this list by talking about the other best-known zero day exploit — Stuxnet. The Stuxnet exploit wreaked havoc in Iranian nuclear facilities by affecting its uranium enriching centrifuges back in the late 2000s before going public.
The sophisticated computer worm, developed by U.S. and Israeli governments, eventually spread to devices in 115 countries, according to report from ZDNet. Although Stuxnet is, by modern day standards, considered old news, this worm is still relevant in the sense that it was the first known publicly known type of cyber attack to target industrial systems around the world.
Final Thoughts on Zero Day Vulnerabilities & Attacks (and How to Protect Your Organization Against Them)
Although we’ve certainly seen enough high-impact zero day attacks that should cause the IT and security community to sit up and take notice, the fact is that patching remains a big issue. This is true for many businesses and organizations alike regardless of their sizes or locations.
But patching isn’t the only thing that businesses, governments, and organizations can do to protect their IT infrastructure, networks, and data:
- Have IT disaster response and recovery plans in place.
- Identify and train key team members so they understand their roles and responsibilities.
- Purge legacy systems and technologies.
- Regularly back up your data and follow the 3-2-1 backup rule.
- Train your employees to be cyber aware so they can identify common threats and know how to safely respond to them.
- Use continuous monitoring solutions to identify unusual activity and advanced persistent threats.
- Regularly assess your network and other cybersecurity defenses to identify vulnerabilities.
- Use multi-layered cybersecurity defenses.














 (7 votes, average: 4.43 out of 5)
(7 votes, average: 4.43 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security