DevSecOps: A Definition, Explanation & Exploration of DevOps Security
SecDevOps is an approach to integrated and secure product development — considering that Checkmarx reports that 92% of surveyed global organizations struggle with integrating security into their DevOps processes, it’s crucial for businesses to take note
Most of us are no stranger to the concept of DevOps, the consolidated version of “software development” (dev) and “IT operations” (ops). We’ve heard this industry buzzword thrown around frequently, even if no one seems to know for sure what it means. (Even the National Institute of Standards and Technology [NIST] doesn’t seem to have a set definition for it!) But sometime after this term was created, we went ahead and added the much-needed “sec” (for security) into the mix. That’s what got us terms like “DevSecOps,” “SecDevOps”, or to keep it simple, “DevOps security.”
But what is the difference between these terms, and does the order in which each function is listed really matter? Yes, and we’ll tell you why momentarily. But first, let’s gain a better understanding of what DevOps security entails and how it benefits your organization.
DevOps: The Foundation for SecDevOps / DevSecOps / DevOps Security
The history of DevOps is an intersecting evolution. It’s important to understand that developers and the “Ops” guys previously worked in separate teams. The developers would write code, and the IT operations team would then have to deploy that code, which was a laborious and highly manual process. By the end of it, typically, there was a lot of contention between the two teams during these handoffs.
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
DevOps emerged as a philosophy or practice that brought together all the processes in software development from coding to deployment in one cycle, so now, instead of working in silos, they work towards the same end goal of moving into production at a faster rate, with a feedback mechanism incorporated into the whole process.
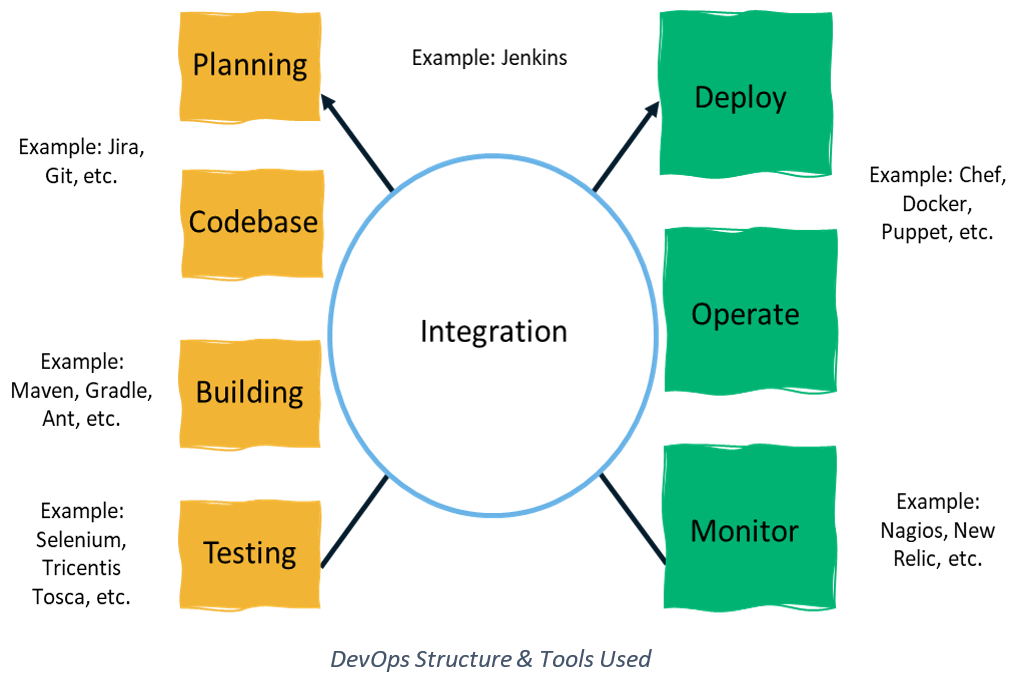
But as they began working together, industry experts started to recognize the importance of integrating security into applications and infrastructure at the start of the product development cycle. This is where DevSecOps comes into play.
DevSecOps: What’s DevOps Security?
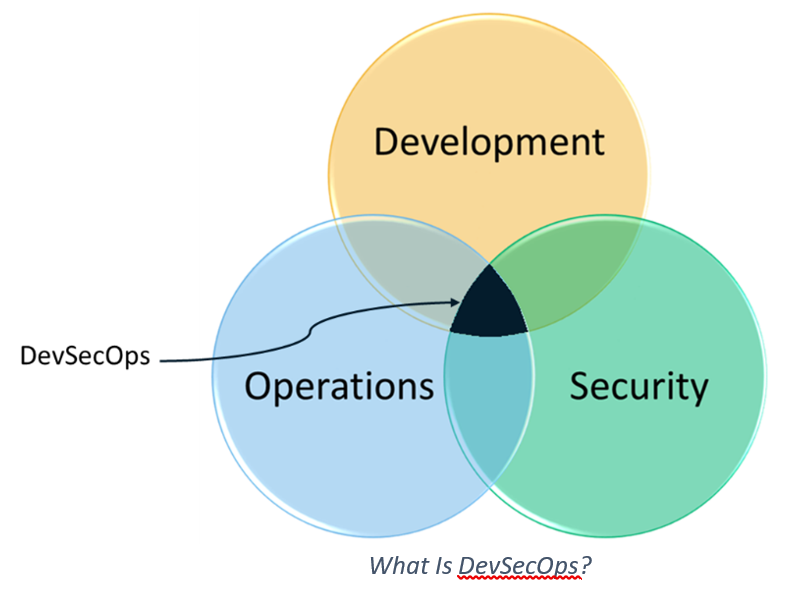
So, as you’ve likely guessed, DevOps security is the concept of integrating “security as code,” security testing, etc. into the development and operation cycle of an application before it goes to market. Security becomes the shared responsibility of everyone involved and is introduced right from the beginning rather than being an afterthought.
If you look at the DevOps environment, where everyone works together as a single, collaborative team, it brings about an overall improvement in the quality assurance process. In a pre-DevOps world, the processes were siloed, slow, expensive, and came with inherent trust issues.
All of this is great, but what is the “real” term for this collaborative approach? The answer depends on your organization and where security falls into your list of priorities. For example:
- Does security come first (secure DevOps, aka SecDevOps)?
- Is security a secondary consideration (DevSecOps)? Or
- Is security something that should be integrated at the end of the software development cycle? (DevOpsSec)?
Realistically, though, it all still boils down to the intrinsic integration of security within the production lifecycle. Ultimately, these terms all mean the same thing — it’s just a matter of how the three functions are prioritized and which term you prefer to use.
Let’s take a look at some of the important phases in DevOps to understand how security integrates with general DevOps as DevOps Security.
How to Integrate Security into the DevOps Lifecycle
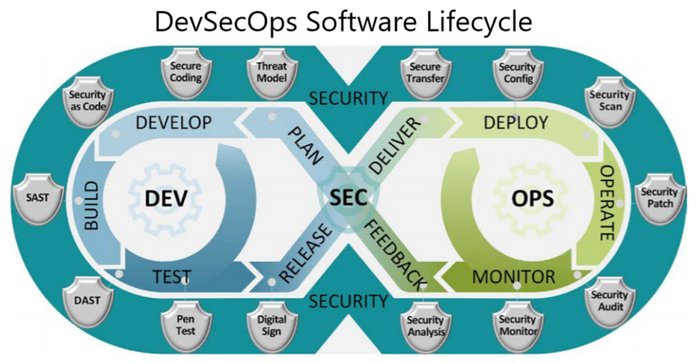
DevSecOps: Automated Testing with Security in Mind
Test automation involves writing effective test cases with maximum code coverage within the code and goes hand in hand with the agile methodology so you can deliver a sprint in a couple of weeks. On making changes to your code, if the test cases fail, you’ll know whether the code works or not. Integrating DevOps security tools (like SonarQube, Checkmarx, etc.) for automated and continuous security testing helps developers write cleaner code and build safer applications.
DevSecOps: Continuous Integration to Improve Performance and Security
Previously, there would be fixed deadlines or consistent cut-off times by when developers would be required to commit changes to the source code in a single repository. Once all the code got submitted by all developers, at night, the code would be run and tested, and a new build referred to as the nightly build would be created.
Continuous integration (CI) encourages developers to frequently commit their code in order to avoid the accumulation of errors. They can use a version control system (such as Git), and for every commit, the automated verification and build process will get triggered. With continuous build and integration (that uses tools like Jenkins), because the tests and verification services are automated and placed within the build environment, bugs can be identified quicker, and the time taken to validate and release software updates is significantly reduced.
Coming back to security — investing in static code analyzers to fix vulnerabilities during unit testing not only reduces the cost of the defect but it also builds security into the product rather than applying it at the end of the product lifecycle. However, static application security testing (SAST) tools can report false positives, and it is vital to train your tool to stop flagging false positives in the context of your application. Additionally, since most applications developed today also rely heavily on open source code, open source security management (OSSM) has become critical along with SAST (white box testing) and DAST (black box testing) methodologies.
DevSecOps: Continuous Delivery with Security at the Forefront
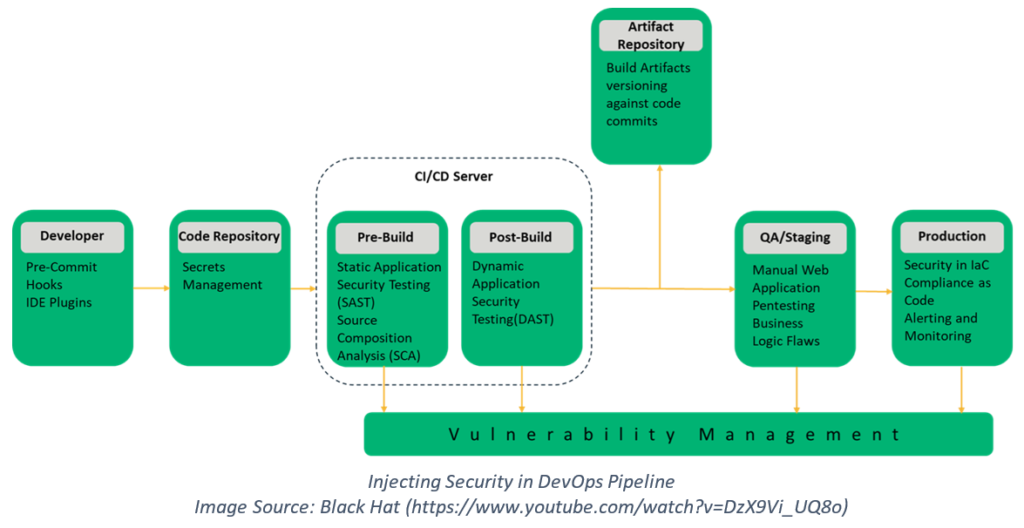
Continuous delivery (CD) expands on the process of continuous integration to automate the process of code delivery (using tools like Puppet and Chef) to a testing or production environment. You can also monitor the performance, business impact, etc. of the software deployed (using tools like New Relic). Typically, during testing and monitoring, you get valuable feedback that can be used when planning the next sprint.
With DevSecOps, we have security-focused CI/CD cycles with security audits, code reviews, penetration testing, etc. injected into the software development lifecycle. It is equally important to keep an eye out for zero-day exploits and to use infrastructure as code (IaC) tools to avoid human error.
The Challenges That Exist Within DevOps Security
Considering that Checkmarx reports that only 8% of surveyed organizations have effective DevSecOps practices, it’s clear that not everyone’s figured out how to make the process work within their environment.
The biggest obstacle that comes up in the way of implementing DevOps or DevSecOps is that it can’t be deployed and successfully executed just by using tools. It requires a massive cultural shift from within the organization — and no matter the size of the organization, such transformations require time, effort, and clear directives and guidance from its leadership.
Employees may be resistant to change and, more often than not, developers and security professionals have very different objectives. While developers have been motivated in terms of adding functionalities, infosec teams are more than happy to do away with any feature that can diminish the product’s overall security.
Unless you already have a collaborative culture with minimal friction between teams, it can be difficult to get the groups to work in unison.
It helps to think of DevSecOps in terms of people, process, and technology precisely in that order. People are the key to an effective and mature DevSecOps environment. In an organization where the employees aren’t on board with the idea, it cannot be forcibly implemented through technology.
But once your people are onboard with the concept, standardization and documentation provide the necessary structure to make the process executable and repeatable. Processes can help with defining workflows, tasks, and responsibilities. Technology comes last and equips people to provide the necessary solutions for implementing infrastructure as code, host hardening, automated scans, etc.
6 Commonly Used DevSecOps Tools
Code analysis, compliance monitoring, vulnerability assessment, etc. are essential components when we talk about adopting a SecDevOps approach. But what tools can we use to implement these technologies? Let’s dive into some of these tools that can assist you in automating and delivering continuous security.
Chef
Chef is an open source automated configuration management tool that converts infrastructure to code (IaC, or a process known as infrastructure as code). It relies on scripts, commonly known as recipes that are compiled into cookbooks, to administer and maintain policies and configurations for your networks and systems in the DevOps environment. Using Chef, an admin can ensure that all systems are set to the right states automatically as defined by the requirements in the scripts, thereby avoiding any hardware malfunction.
GitLab
With GitLab, you can not only store your code using Git version control, but you also can gain control of your DevOps toolchain. It offers a whole bunch of features, and you can go from planning to monitoring using a single interface. The best part is that because it is security-focused, you can shift left in the development process to loop in security from the start. Eventually, it can support you to avoid trade-offs between speed and security.
SonarQube
SonarQube, an open source solution offered by SonarSource, assesses the quality of the code by performing continuous code inspection and automatic reviews through static code analysis to detect bugs and security vulnerabilities even as the developer codes. This versatile tool:
- supports 27 programming languages,
- provides project insights through graphs, and also
- offers reports on unit tests, code coverage, bugs, code complexity, duplicate code, etc.
Red Hat Ansible
Ansible falls on the operations side of the product development process and helps system admins to manage their infrastructure through automation modules effectively. These modules (written in Python, Powershell, etc.) are triggered sequentially based on the user-defined specifications in the Ansible playbook (written in easily understandable YAML). It takes care of IT automation, configuration management (including security configurations), and automatic deployments so that as the business scales, consistency is maintained across environments, and there is a reduced scope of human error or compliance violations.
SaltStack
SaltStack is one of Sectigo’s currently supported solutions for DevOps. Like Chef, it’s an automated configuration management tool with one big difference being that, by default, it uses a push-based configuration model while Chef is almost always set up to be pull-based.
SaltStack is based on Python, and instructions can be written in YAML or DSL. Though the setup phase might be slightly more challenging than the rest, once set up, it is extremely simple to use. It also comes armed with an effective reporting mechanism and is perfect for environments designed with scalability and resilience in mind.
Aqua Security
Aqua is a cloud-native security platform that protects containers, serverless, and VM-based applications. It can be utilized to embed security early on at every stage of the DevSecOps pipeline. From thorough security testing to policy-driven controls and intrusion prevention capabilities, it can provide multiple layers of protection across the entire stack to detect and mitigate risks. It makes use of automation, security controls based on machine-learned behavioral profiles, and makes sure VMs, containers, and functions remain immutable during runtime to prevent unsolicited changes.
In Summary
SecDevOps has the benefit of tying in security with the product right from the beginning of the software development lifecycle. Apart from minimizing security bottlenecks and costs, it also accelerates application delivery in addition to building quality products. DevSecOps, along with agile methodologies, is the way to go as it comes with multiple benefits and emerges as a win-win situation in the long run for everyone involved.
























 (22 votes, average: 3.95 out of 5)
(22 votes, average: 3.95 out of 5)







No comments