How does Code Signing work?
A digital signature is a unique string of letters and numbers that can be attached to a file or program. Starting June 2023, the process includes an additional layer of security: the private keys used for these digital signatures must be stored either on a secure USB token or a hardware security module (HSM) that meets specific security standards.
When the signature is added to the software code, it creates a hash digest (hash value) that’s then encrypted using a private key. The signed hash value is packaged with the code, signed hash, and code signing certificate. This creates the cryptographic digital signature that provides authenticity and integrity protections.
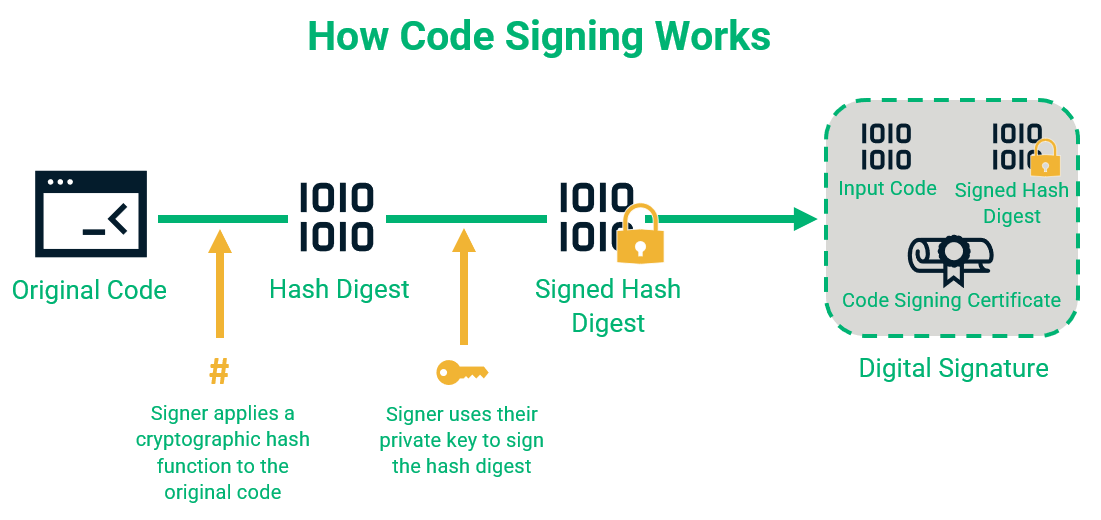
When a customer downloads the software, their browser or operating system examines the digital signature for authentication. After this step, the browser or operating system performs its own hash function and compares the resulting value with the one accompanying the program. A matching pair of hash values confirms the file's integrity.
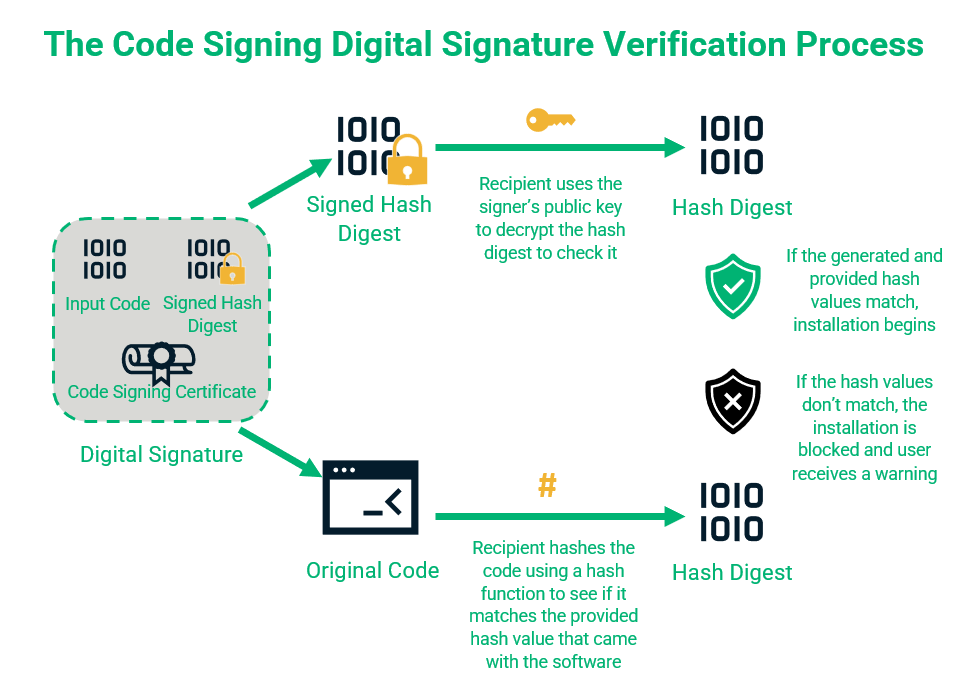
The reliability of this process lies in the nature of hashing, which maps data of varying lengths to a fixed-length output. For example, SHA-256 is a standard hashing algorithm used in SSL/TLS protocols. It produces 256-bit long hashes, typically represented by a 64-character hexadecimal string. The uniqueness of each hash value ensures that no two data sets can produce the same output, making the algorithm secure and reliable.










