Spyware Examples: 4 Real Life Examples That Shook 2021
Not sure how spyware works or what damage it can cause? Want to get up to date with the latest spyware examples and industry trends? Let’s explore several of the biggest spyware threats that surfaced in 2021
If you’re looking for spyware examples, you’ve come to the right place. Of course, this means you probably already know that spyware is malicious software used to spy on people — the name gives it away. But do you know that spyware has powers beyond stealing your photos and data?
Spyware is malware that also can be used to:
- Lock your screen,
- Disable antivirus programs,
- Record videos using your phone’s camera, and
- Cause a variety of other issues — sometimes without leaving a trace.
In this article, we’ll look at four spyware real life examples that were discovered or observed in 2021, including how they invade victims’ devices, what damage they cause, and what techniques we can use to treat and prevent these dangerous infections.
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
Spyware Example 1: PhoneSpy
On Nov. 10, 2021, researchers at Zimperium zLabs published a report about a spyware app they found in South Korea affecting Android devices in the wild. Called PhoneSpy, this malicious program masquerades as a regular application so it can gain access to your infected machine to steal data and remotely control it. This spyware is estimated to have infected more than 1,000 Android devices.
How PhoneSpy Infects Your Device
Unknown. PhoneSpy was found in 23 legitimate-seeming apps like Yoga learning, video streaming, and messaging apps. Because these apps are not in the Google Play Store, zLabs researchers believe that the malware was distributed via other third-party platforms that attackers shared via social engineering and phishing techniques.
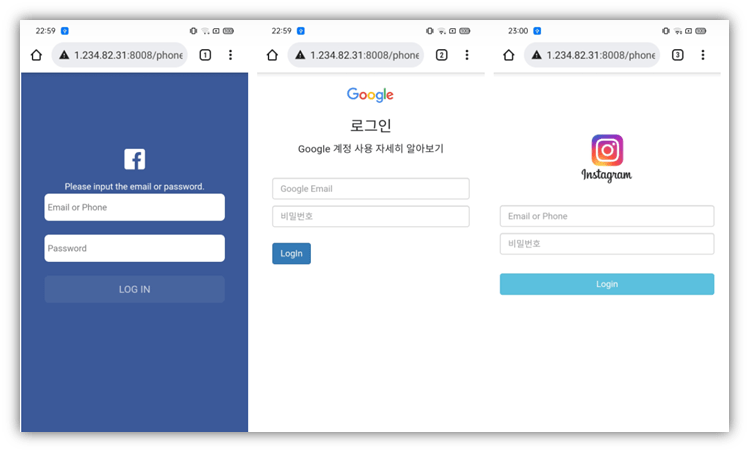
What Happens When PhoneSpy Infects Your Device
Not sure what happens when spyware like PhoneSpy gets installed on your device? Here’s a quick overview of what risks are associated with this spyware example and what it can do:
- Steal login credentials, images, contact lists, call logs, and messages
- Record video and take pictures using a device’s front and rear cameras
- Record or transmit your GPS location
- Download files and documents from the hacker-controlled command and control server (C&C server)
- View device information like IMEI (i.e., serial number), brand, device name, and Android version
- Lead victims to phishing websites to trick them into sharing credentials
How to Protect Your Device Against This Spyware Example
PhoneSpy carries out its activities without leaving a trace and conceals itself by hiding the infected app icon from the device menu. Hence, victims aren’t aware that their device has been compromised. There is no information on how much data is stolen or how they are misused.
On Nov. 22, 2021, Zimperium posted that PhoneSpy’s command and control server had been taken down and is no longer active. So, in theory, PhoneSpy should no longer be a threat. It’s possible that this spyware example was used for espionage and the campaign ended when the mission was completed. Nevertheless, you should avoid installing apps from anywhere other than official app stores (Google Play, Apple App Store, etc.) and exercise caution if anyone asks you to do so.
Spyware Example 2: Android/SpyC23.A
Advanced persistent threats (APT) are well-planned, well-organized, multi-staged attacks. They usually target government agencies and corporate giants and are operated by groups of hackers working together. As espionage is one of the main goals for APT attacks, hackers often use innovative spyware to deploy them.
One infamous APT group is ATP-C-23. ATP-C-23 use many types of attack, including Android/SpyC23. On Nov. 23, 2021, Sophos published a report stating that they’d discovered a new, powerful variant of spyware called Android/SpyC23.A. The malicious program is used by an infamous threat actor group known as ATP-C-23. Previous versions of this malware are known as VAMP, FrozenCell, and GnatSpy.
Once installed onto the target device via a compromised app, the spyware tricks the user into granting admin permission to the hackers. This access allows the attacker to:
- View your sensitive files,
- Lock the device,
- Install or uninstall apps, and
- Disable security notifications (so you’re unaware of their activities).
The new variant has the power to connect to other C&C servers in case the main server is taken down. It also hides notifications coming from security apps and the Android system, which means the victim isn’t alerted of the threat — even if their mobile has already detected the malware.
How Android/SpyC23.A Infects Your Device
Android/SpyC23.A is delivered through infected apps and distributed via SMS or similar mediums. It may be disguised as:
- App updates
- System apps updates
- Android update intelligence
After infecting a device, Android/SpyC23.A changes its display icon and name to another well-known app to disguise itself. Sophos reports that some examples of the apps this spyware commonly impersonates include:
- Google Play
- Youtube
- Botim
What Happens When Your Device Becomes Infected?
Now that we know what Android/SpyC23.A is and how it infects your device, it’s time to explore its effects:
- Read messages, documents, contacts, and call logs
- Record incoming and outgoing calls
- Take screenshots and pictures
- Record video of the screen
- Read app notifications
- Block notifications from Android and security apps
How to Protect Your Device Against This Spyware Example
Only download apps from the App Store or Play store, never from SMS, WhatsApp, or emails. Don’t give admin permissions/superuser/root access to any apps. We haven’t found any antispyware program claiming yet that they can remove Android/SpyC23.A, so the best way to mitigate the threat is to avoid infection.
Spyware Example 3: Pegasus
It’s safe to say that Israel-based NSO Group’s Pegasus spyware disrupted the world of espionage, making headlines all over the world. Although the company claims that it helps nations fight terrorism and crime, evidence suggests that people are using Pegasus software for their personal agendas. It is used to spy on activists, political rivals, workers, bloggers, media employees − anyone the client wants.
The latest attack, FORCEDENTRY affects targeted Apple users. On Sept. 13, 2021, a scientist at Citizen Lab published a report about a zero-click exploit that exploits a vulnerability in iOS’s CoreGraphics to deliver Pegasus spyware. Along with spying on the victim’s devices, it was deleting the pieces of evidence from the phone’s DataUsage.sqlite file, too.
NSO Group has clients in many countries, including the United States, United Kingdom, Saudi Arabia, United Arab Emirates, Hungary, France, and India. You can see all the latest developments related to Pegasus Spyware on The Guardian’s website.
How Pegasus Spyware Infects Your Device
Pegasus spyware is distributed via three main methods:
- Spear phishing via text messages or emails
- Zero-click attacks that exploit vulnerabilities in apps and operating systems
- Over a wireless transceiver located near a target
What Happens When Pegasus Gets Onto Your Phone
After infecting a device, Pegasus can:
- View SMS messages, address books, call history, and calendar entries
- Read and tamper with internet browsing history
- Monitor actions and conversations
- Turn on the camera to record in real-time
- Activate the microphone to record conversations
- Track GPS location
How to Protect Your Device Against This Spyware Example
Pegasus spyware is used to spy on targeted users and is not currently a threat to most of us. If you think you could be a target of Pegasus spyware, it’s best to get help from a trusted cybersecurity expert. Because this spyware is used in highly sophisticated attacks, you won’t be able to prevent it due to the vulnerabilities that exist on your phone.
However, to avoid infection, be vigilant when opening unknown videos, messages, or links. If you think your device is infected, you can always perform a factory reset to get rid of many types of malware.
Spyware Example 4: Ghost RAT
Ghost RAT (also written as Gh0st RAT) is a trojan horse made for spying. RAT stands for “remote administration tool.” This name is appropriate considering that Ghost RAT’s operators, GhostNet System, use a C&C server to control victims’ devices remotely.
The latest Ghost RAT attack was on NoxPlayer, a free Android game emulator for PC and Mac from a company named BigNox. On Feb. 1, 2021, WeLiveSecurity published a report indicating that attackers breached BigNox’s API infrastructure to host and deliver Ghost RAT and other two types of malware. It targeted users from Taiwan, Hong Kong, and Sri Lanka.
How Ghost RAT Infects Your Device
Attackers use phishing and social engineering scams to trick potential victims into downloading the infected software. Because Ghost RAT is a trojan, the payload doesn’t work until users download, install, and activate the software.
What Happens When Ghost RAT Gets Installed
After a user installs Gh0st RAT, the spyware’s author (i.e., the hacker) can:
- Access the infected device remotely
- Turn on the device’s camera, video recording, and audio recording functions
- Steal their stored data
- Use encrypted TCP channels to avoid detection
How to Protect Your Device Against This Spyware Example
The basic steps for protecting your device against Gh0st RAT spyware are the same as with any other malware:
- Install software and apps only from legitimate sources
- Carefully read reviews on the app store if you’re installing an unknown app
- Keep track of the apps on your device
- Uninstall suspicious apps
- Keep your devices updated and patched
- Recognize the difference between fake and legitimate software programs
How to Recognize Legitimate Software to Avoid Spyware (and Other Types of Malware)
Legitimate companies use code signing certificates to validate the authenticity of their software. Organizations that request these publicly trusted digital certificates must first be vetted by a third-party certificate authority (CA). The CA verifies specific types of information about your organization prior to issuing the certificate. This offers a level of trust and validity to both your organization and software by attaching your verified organization information to your software.
But how do you know whether an application is digitally signed? A dialogue box will appear that displays your verified organization’s name in the publisher’s field when a user downloads or tries to install your software.
Compare this to an example of the “unknown publisher” message that displays when a user attempts to install unsigned software:
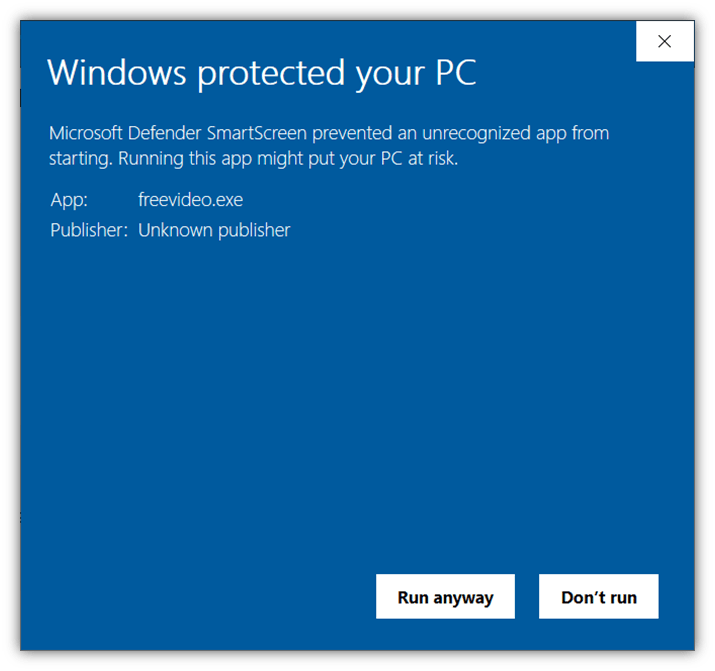
Code signing certificates come in two varieties: standard validation and extended validation. What’s the difference between the two?
- A standard code signing certificate displays your organization’s verified identity information (as shown in the graphic above).
- Ann EV certificate bypasses the warning altogether because it’s automatically trusted by Windows browsers and operating systems.
Final Words on Spyware Examples in 2021 and What This Means for 2022
There’s a misconception that only influencers and politically active people can become the target of spyware. But spyware operators have many other goals besides espionage, and virtually no one is a potential target. Cybercriminals can use spyware to use as blackmail after stealing your sensitive data. They also can sell the data they gain to advertisers who want to gain a better understanding of your likes, interests, and buying preferences.
To avoid spyware infections, always be vigilant in your downloads and when clicking links or and granting app permissions. Don’t hesitate to take experts’ help if you think your device is infected with spyware. We hope these latest spyware examples provided you with an idea of how the spyware situation was in 2021, and what you can do to protect yourself and your data in 2022.






















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security