How to Use Google Cloud KMS with Sectigo Code Signing Certificates (2025 Guide)
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a Sectigo Code Signing Certificate
Google Cloud KMS users can now enjoy the security and familiarity of managing their Sectigo Code Signing Certificate keys.
This article will walk you setting up and storing your secure code signing certificate and key pair using Google Cloud KMS’s hardware security module (HSM).
Table of Contents: Skimmers Can Jump Ahead
- How to Get Started: Buy a Code Signing Certificate
- Step #1: Create a Key Ring in Google Cloud KMS
- Step #2: Create a Public-Private Key Pair Using Google Cloud’s HSM
- Step #3: Download the Key’s HSM Attestation Record
- Step #4: Generate the Certificate Signing Request (CSR)
- Step #5: Submit the CSR and Key Attestation Information
- Sign Your Code Using a Sectigo Code Signing Certificate + SignTool
How to Get Started: Buy a Sectigo Code Signing Certificate
Google KMS + Sectigo Code Signing = Secure Key Storage for Cloud Signing
Before you can set up your Google Key Management Service (KMS) or start signing code, you first must purchase a code signing certificate. To fight the misuse of compromised signing keys, all new code signing certificates and keys must be generated and stored on FIPS-compliant hardware.
Sectigo supports the following secure devices:
- YubiKey 5 FIPS Series (USB token)
- Luna Network Attached HSM v7.X (physical hardware)
- Google Cloud KMS (cloud HSM)
If you want to use Google KMS for your cloud signing projects, choose Install on Existing HSM as your Certificate Delivery Method when purchasing a Sectigo Code Signing Certificate from SectigoStore.com.
Once your order is complete, you’ll be taken to your account’s My Orders page. Here, you’ll see a link (shown below) that will take you to start the Certificate Generation process that we’ll cover in Step #5.
Step #1: Create a Key Ring in Google Cloud KMS
If you wish to use an existing Google Cloud KMS key ring, jump to Step #2 to generate your key. Otherwise, if you need to set up a new key ring, you can do so using Google Cloud KMS’s guide to creating a key ring.
NOTE: Be sure to grab your Google Cloud KMS key_ring value, as you’ll need this in Step #4.
Step #2: Create a Public-Private Key Pair Using Google Cloud’s HSM
Now that the key ring is good to go, it’s time to generate a new key. In Google Cloud, make the following selections:
- Select HSM protection
- Next, choose HSM-generated under the Key Material field.
- Click Asymmetric signing as the Purpose and Algorithm selections and specify 3072-bit RSA – PKCS #1 v 1.5 padding – SHA256 Digest (recommended)
Once finished, you’ll see a key listing like this (3072-bit RSA key, PKCS #1 v 1.5 padding – SHA256 Digest [recommended]) in your key ring:
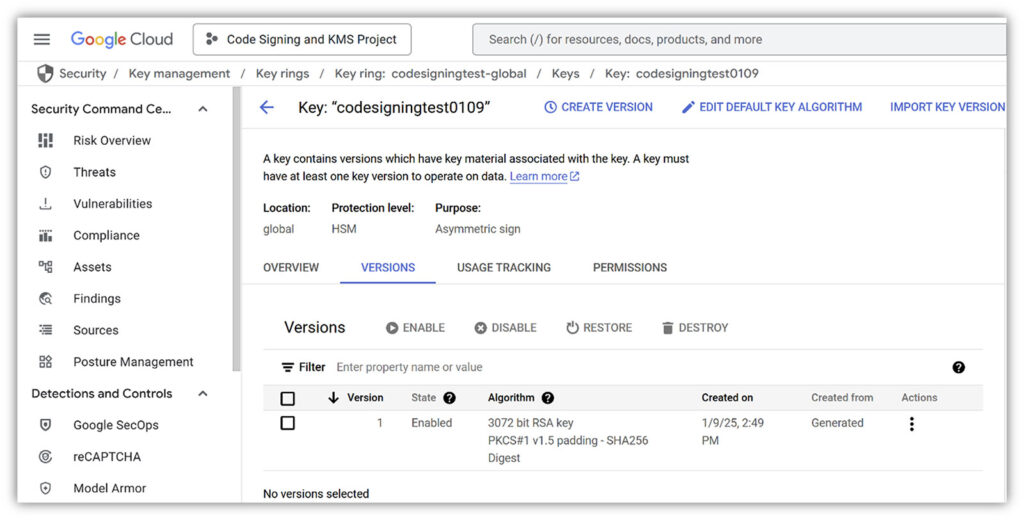
Step #3: Download the Key’s HSM Attestation Record
The next step is to show that your key has been generated using a secure device by downloading the key attestation bundle. (You’ll need this shortly, so go ahead and grab it now.)
- Select the three vertical dots under the “Actions” column shown in the screenshot above.
- Click Verify Attestation in the drop-down menu.
- Choose the Download Attestation Bundle option (this is a .zip file).
Step #4: Generate the Certificate Signing Request (CSR)
Use your preferred method of CSR generation. In this case, we’ll walk you through how to generate a CSR using the key you just created in OpenSSL on Linux (Ubuntu). This process involves:
- Downloading and installing OpenSSL and the libengine-pkcs11-openssl package
- Extracting the Google PKCS #11 library and configuring OpenSSL to use it
- Setting up a YAML configuration file for the KMS_PKCS11_CONFIG environmental variable to point to. (NOTE: This is where you’ll need the key_ring value you collected earlier in Step #1.)
- Setting up your authentication method via Workload Identity Federation or create a Service Account in Google Cloud. You can do this by selecting a project under IAM-Admin > Service Accounts. This will require granting specific permissions to the Cloud KMS’s Admin and Crypto Operator roles and creating a new JSON key that will need to be saved to the server or computer used to generate the CSR.
- Setting the environmental variable so it points to the key file.
- Generating the CSR using a customized version of the following variable: openssl req -new -subj ‘/CN=Your Company Name, LLC/’ -sha256 -engine pkcs11 -keyform engine -key pkcs11:object=your_key_name > code_signing_request.csr.
- Replace the value your_key_name with the key file name (e.g., “codesigningkey” rather than the resource URL, as there’s a 100-character limit that’s notorious for errors)
- Double check your digest algorithm matches the one you selected in Step #2 when generating the key.
Check out the Create the CSR section in our technical guide on how to generate the CSR and download the key attestation in Google Cloud for more specific information.
Step #5: Submit the CSR and Key Attestation Information
To complete the certificate enrollment (CSR generation) process, you’ll need to submit your CSR and key Attestation file(s) to Sectigo. Reminder: This is the .zip file you downloaded earlier in Step #3.
To submit your CSR and complete the certificate enrollment process, log into your account on SectigoStore.com and access My Orders. Here, you can choose the option to generate a certificate. This will take you to CertificateGeneration.com page. Here, you must:
- Provide your name and organizational details
- Enter the organizational contact’s information
- Add an email address (optional), if you want to receive a verification email
- Select your preferred certificate collection method (I’ll address the specifics of this step in the bulleted list below)
- Agree to the Certificate Services Agreement
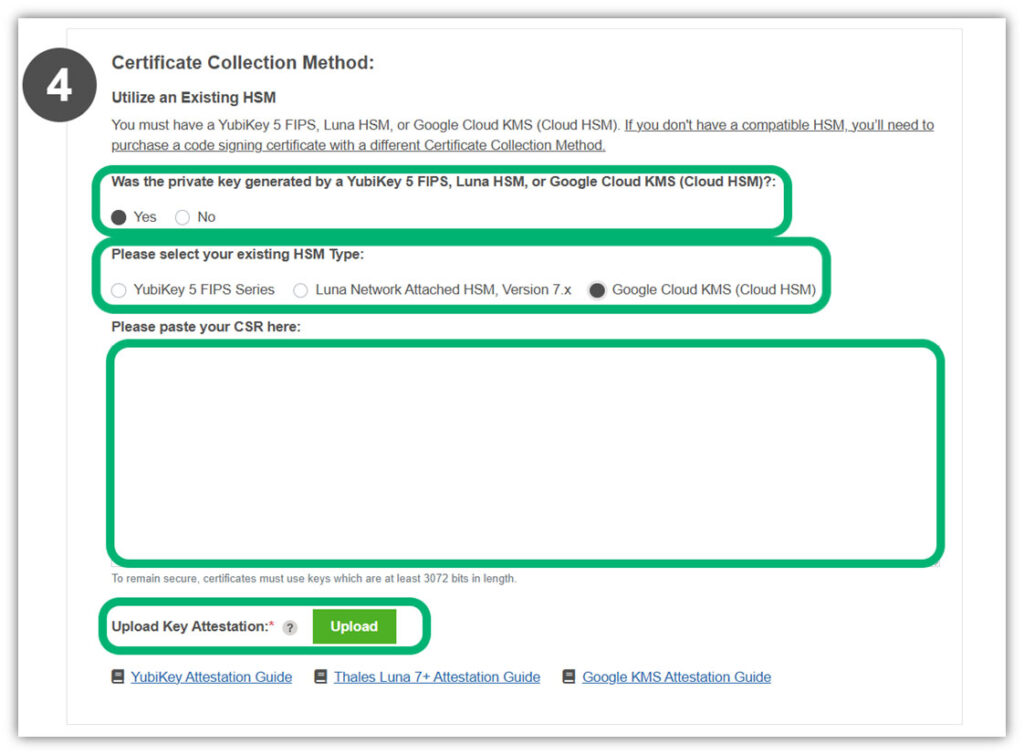
The additional steps indicated in #4 above are as follows:
- Click Yes in response to the question about whether the private key was generated using one of the listed secure hardware options
- Choose Google Cloud KMS (Cloud HSM) as your existing HSM type
- Copy and paste your CSR details that you generated in Step #4
- Upload your Key Attestation file(s) downloaded in Step #3
That’s it! Now, Sectigo will begin its code signing certificate validation process; once complete, the certificate will be issued.
Sign Your Code Using a Sectigo Code Signing Certificate + SignTool
The hard part is done — it’s now time to enjoy the fruits of your labor. Once your code signing certificate is ready, you can start using it to sign your software executables using SignTool.
To start signing software using SignTool on Windows:
- Ensure you’ve got the latest version of SignTool installed. If you don’t, you can install SignTool as part of the Windows Software Development Kit (SDK).
- Install the latest Google Cloud KMS CNG provider release on your device.
- You’ll first need to authenticate your machine to Google Cloud. This will involve running Google Cloud’s authentication application using the command gcloud auth application-default login.
- Sign your software using the following command with your customized certificate and key resource path variables: signtool sign /v /debug /fd sha256 /t http://timestamp.sectigo.com /f path/to/mycscertificate.crt /csp “Google Cloud KMS Provider” /kc projects/PROJECT_ID/locations/LOCATION/keyRings/KEY_RING/cryptoKeys/KEY_NAME/cryptoKeyVersions/1 path/to/file.exe

















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security