TLS Version 1.3: What to Know About the Latest TLS Version
TLS 1.3 is used by 30% of connections on Chrome and 27% on Firefox, according to the IETF. Here’s what to know about TLS 1.3 and what this latest TLS version of website security means for your business
One of the things that I love most about the SSL industry is that it’s always changing. There’s always something new to talk about, discuss, debate, and learn about. Today, we’re going to talk about something that’s relatively new in the SSL world. We’re going to get under the hood of TLS 1.3, the latest TLS version of the cryptographic protocol that’s supposed to take SSL security and performance to new heights.
Before I get to TLS 1.3, I’ve got a question for you. Can you shift your car directly in fifth gear? Well, no, you can’t, right? In the same way, it’s essential to learn what TLS means before we get to TLS 1.3. So, let’s get started!
What Is TLS (Transport Layer Security)?
As the cliché goes, necessity is the mother of invention. The necessity of the TLS protocol was created in the early 1990s when more and more people started using the internet and there was suddenly a need to protect users’ privacy. To address this concern, SSL (secure socket layer), the first internet security protocol, was invented. So, what’s the difference between SSL and TLS?
SSL, first developed by Netscape, was released in 1995 as SSL 2.0. SSL 1.0 was never released. Subsequently, TLS became the successor of SSL. So far, three versions of TLS have been released, and TLS 1.3 is the latest one.
TLS provides a secure connection between a client (typically, an end user’s web browser) and a web server. This secure connection is established by encrypting the data-in-transit. TLS data encryption is supported by many IP-based internet protocols, including HTTPS, POP3, SMTP, and FTP.
In everyday use, TLS is employed through what’s known as an “SSL certificate.” These digital certificates are also known as “TLS certificates,” but most people use the legacy term “SSL certificate” because it’s more common. These certificates are the reason why your critical information doesn’t get leaked on the internet whenever you submit information to a website.
How TLS 1.3 Came Into Existence
As time has passed, the tech industry has made significant strides as far as computing power is concerned. Today’s technology has enabled us to use devices and share data at an unprecedented speed. However, with increasing performance prowess and data sharing, there comes a concern in the form of security. The more the computing power, the more vulnerable old security mechanisms, and that’s what happened with TLS 1.0 and TLS 1.1. Both these protocols were secure enough for a period but have since proven that they couldn’t stand the test of time when security vulnerabilities were discovered in them.
That’s why TLS 1.2, the most widely used TLS protocol, came into existence in 2008. It’s been the longest-serving TLS protocol — but, as it goes with all security technologies, it, too, has vulnerabilities. However, the majority of the weaknesses of TLS 1.2 are theoretical in nature, and that’s why it’s still a secure protocol to use. The potential flaws in TLS 1.2 underscored the need for a more secure successor of TLS 1.2, and that’s where the quest to develop TLS 1.3 began.
The road to the release of TLS 1.3 hasn’t been an easy one by any means — it took 28 drafts for Internet Engineering Task Force (IETF) to define it. There were many roadblocks, such as middleboxes and undermining attempts by commercial elements. But finally, after a decade of efforts, TLS 1.3 was released in 2018.
How TLS Version 1.3 Is a Significant Upgrade Over TLS 1.2
First, let us state it once again that there’s no need to panic as TLS 1.2 is still a safe protocol to use. In fact, as of May 2020, more than 67% of the websites surveyed by SSL Labs support TLS 1.2, whereas only 29.7% of sites support TLS 1.3. Having said that, TLS 1.2 was released in 2008, and that’s why it has some concerns that need to be addressed, keeping the future in mind.
Amongst many technical differences, TLS 1.3 version offers three upgrades that are quite critical to an ordinary user. These advantages are:
- Increased Speed
- Better Security
- Simplified Cipher Suites
Let’s learn about each of these benefits in a bit more detail.
TLS 1.3: The Performance Benefit of a Shortened Handshake Process
At the heart of all SSL/TLS protocols, there’s a process known as the “handshake process.” This handshake process occurs when the client and the server connect to transfer the data securely by the processes of authentication and encryption. It’s a series of back and forth communications between both parties.
As far as the TLS 1.2 handshake is concerned, it involves two round trips of communication between the client and the server. Therefore, the number of negotiations required becomes four. While this isn’t a big idea when you have just a few users on your website, it hurts the network performance when you’re doing it at scale.
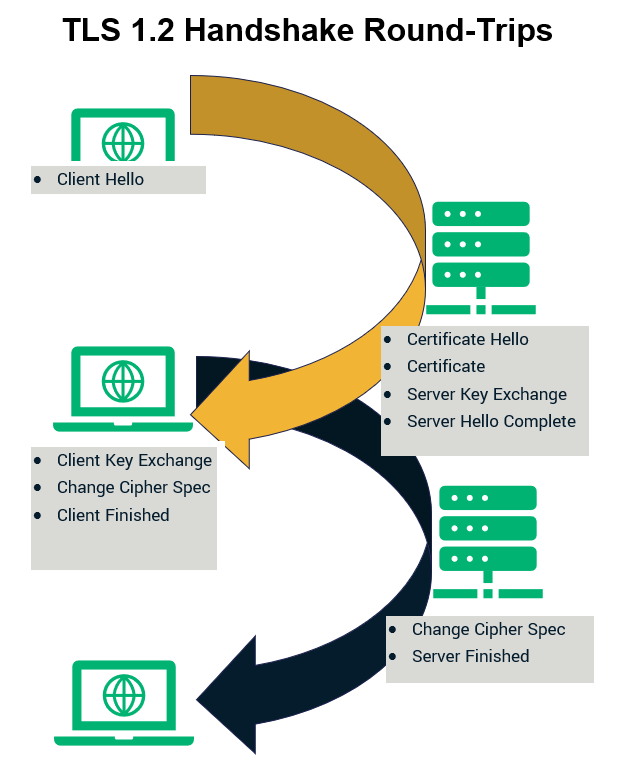
TLS 1.3 addresses this concern by reducing the handshake to a single round trip. That’s because the negotiations take place between the client and the server only twice. This results in increased network speed. The difference might be in milliseconds, but in domains where even a microsecond can make a world of difference, this is undoubtedly a significant advantage.
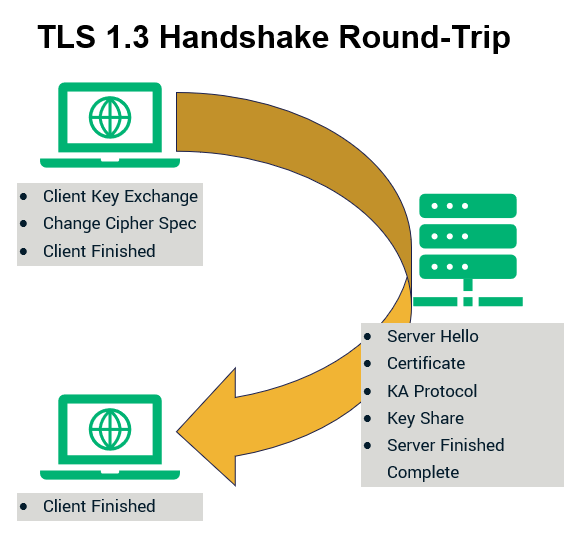
Not only that, but TLS 1.3 also introduces another feature that will have a considerable impact on the performance. This feature is known as “Zero Round Trip Time Resumption” (0-RTT). Much like its name implies, the 0-RTT feature paves the way for SSL/TLS handshakes that have zero roundtrips.
The 0-RTT feature comes into play when a server and client are resuming a connection. Therefore, on websites that you’ve visited in the past, no back and forth communication happens, and data encryption occurs with the first message you send to the server. This is done by resumption master key. 0-RTT decreases the load time significantly.
TLS 1.3: The Security Advantage
The most obvious but also the most essential benefit of TLS 1.3 comes in the form of security. TLS 1.3 has discontinued support for some of the older, potentially insecure ciphers and algorithms that were supported in TLS 1.2. These deprecated items include:
- RSA Key Transport
- Various Diffie-Hellman groups
- CBC Mode Ciphers
- RC4 Steam Cipher
- DES
- 3DES
- MD5 Algorithm
- EXPORT-Strength Ciphers
TLS 1.3: Simplified Cipher Suites
As we saw previously, the number of negotiations between the client and the server have been cut in half. This reduction results in a decreased cipher size. TLS 1.2 and its previous TLS versions used cipher suites that had four ciphers in them. Therefore, it made dozens of cipher combinations possible and didn’t have any clear guidance in choosing the right cipher combination for better security.
TLS 1.3, however, simplifies this process of selecting the right cipher combination as it has only five ciphers to choose from. These cipher suites are as below:
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_GCM_SHA256
- TLS_AES_128_CCM_8_SHA256
- TLS_AES_128_CCM_SHA256
Do Browsers Support TLS 1.3?
Initially, when the TLS 1.3 version was released, there were some concerns, and the browsers took a bit of time to adopt it. However, today, all major browsers have enabled support for TLS 1.3. However, as a site user, you must make sure that you’re using an updated version of your browser to take advantage of it as older versions may not be compatible with TLS 1.3
Final Word: Start Using TLS 1.3
Had it been up to security enthusiasts like me, we’d make it mandatory for all sites to use TLS 1.3. Fortunately — or unfortunately, depending on how you look at it — that’s not the case. Although it’s undoubtedly a saddening thing seeing only a fraction of websites supporting TLS 1.3 considering all of the benefits it offers. However, there’s a silver lining since that number is increasing day by day.
If you have a website, then you must make sure that you’ve enabled support for TLS 1.3. If you’re not sure about it, you can go to the SSL Labs website to check the TLS protocols your server supports. If your site is still supporting TLS versions preceding TLS 1.2, then you should disable their support ASAP as it could put your website at substantial risk. And if you find your web server not compatible with TLS 1.3, you know what to do. Right?














 (46 votes, average: 4.74 out of 5)
(46 votes, average: 4.74 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security