How to Define Doxing (Doxxing): A Definition & Meaning
When Hana Mohsin Khan received a phone call from a friend, it’s when her “doxxing” nightmare began. Her photo was being circulated in an app called Sulli Deals. But Khan isn’t alone; hundreds of people suffer similar doxxing experiences every day. To learn more about this harmful activity, let’s dive into the world of doxxing…
A 2021 report by SafeHome.org reveals that although 43 million (21%) Americans have been doxxed, only 66% of those reported it to the authorities. An astounding 86% of victims experienced personal repercussions, and it led to problems at work for 40%. 51% became victims or targets of criminal activity afterward.
These stats are all the more startling when we realize that doxxing can affect anyone – rich or poor, famous or unknown, young or old – making it one of the most nerve-racking cyber threats in the world today. The effects can permeate every aspect of a victim’s life.
But what exactly is doxxing and why is it such an issue? We’ll define doxing / doxxing (answering the question “what is doxing?”) while also providing specific examples that help you understand the meaning of the term.
What Is Doxxing? A Definition and Explanation
Doxxing, sometimes spelled “doxing,” can be defined as the act of collecting and publishing the personal information of a victim online with the intent to embarrass, harass, or otherwise cause harm to the victim. Harm can come in many forms — emotional, financial, reputational, physical, psychological, etc. Doxxing can also be used to blackmail targets into making financial payments or coerce them into doing something they normally wouldn’t.
Doxxing is not a new concept. It’s been around since the days of the Usenet discussion forums of the 1990s. The first recorded doxxing occurred when author Vladimir Flomin released a list of the names and personal details of people he disagreed with.
The word originates from “docs” or documents. When a perpetrator collects a target’s information and makes it public, they are said to have “dropped the dox” on the victim. Over time, this became the term ‘doxxing.’
What Is Doxware? Define Doxing / Doxxing Malware
Doxware is malware that’s designed to extract a ransom from victims by threatening to publish their data unless they pay up. Doxware is a type of ransomware and is also known as a cryptovirology attack. First developed by Adam Young and further developed by Moti Yung, a cryptovirology attack uses public-key cryptography as an attack vector. In 2003, the duo presented the attack strategy at The United States Military Academy (USMA, also known as West Point). They also described the attack in their book Malicious Cryptography.
What Types of Information Are Used in Doxxing?
The information used in doxxing can be divided into three categories:
- Personally identifiable information (PII). This includes information such as email addresses, mailing addresses, personal phone numbers, and other identifying or personal information.
- Previously unknown information about the victims. This information, once published, can cause damage to relationships with friends, family, colleagues, and others.
- Information intended to damage the reputation of the victim. This type of information is intended to harm or humiliate the victim and damage their relationships with friends, family, colleagues, and society as a whole.
What Is the Purpose of Doxxing?
In 1763, John Adams famously observed, “[a]ll men would be Tyrants if they could.” Centuries have gone by, and the only thing that has changed is the way a person might become a tyrant. Those were the times of physical power struggles, and these are the times of digital tyranny.
Today, attackers have found a way to strike their victims without having to be anywhere near them; it’s much easier to harass someone anonymously on the internet than it is to face them out in the open. And if an attacker doesn’t have the skills required, they can enlist services available on the dark web to achieve their aims.
The usual purposes behind doxxing are:
- Revenge
- Victim shaming
- Objections to a community/cause
- Intimidation
- Sadistic pleasure
SafeHome.org reported that 52% of perpetrators of doxxing took exception to a public post from their victim, 24% had personal issues with the victim, while 20% doxxed because of gaming disputes.
What Are the Repercussions of Doxxing?
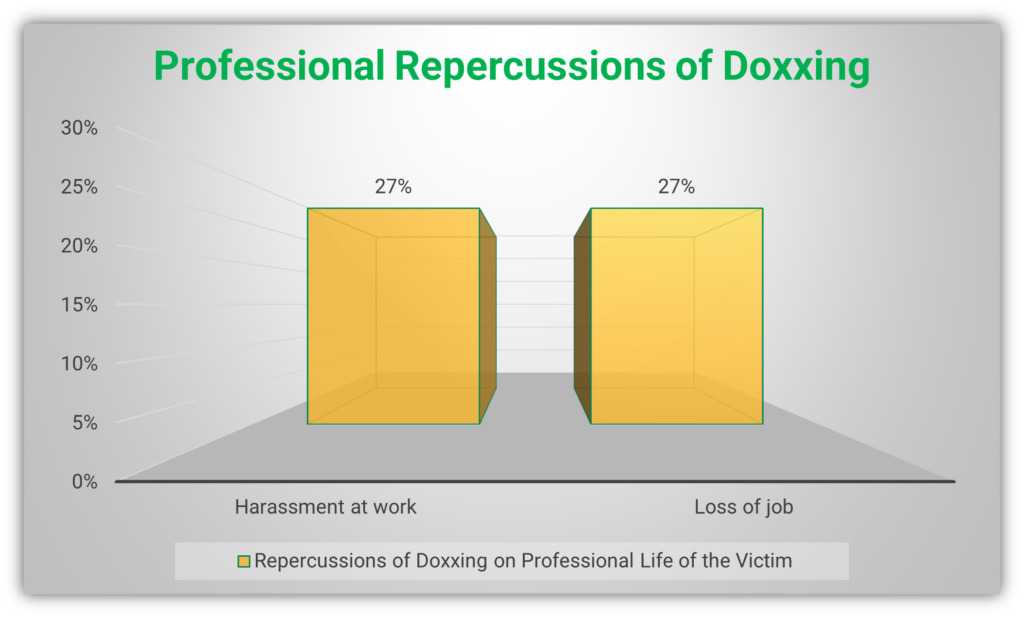
Whether it is Hana Mohsin Khan or the targets of Vladimir Flomin, all of these individuals suffered the effects of doxxing. The following figures from SafeHome.org’s research show some of the repercussions of doxxing on victims:
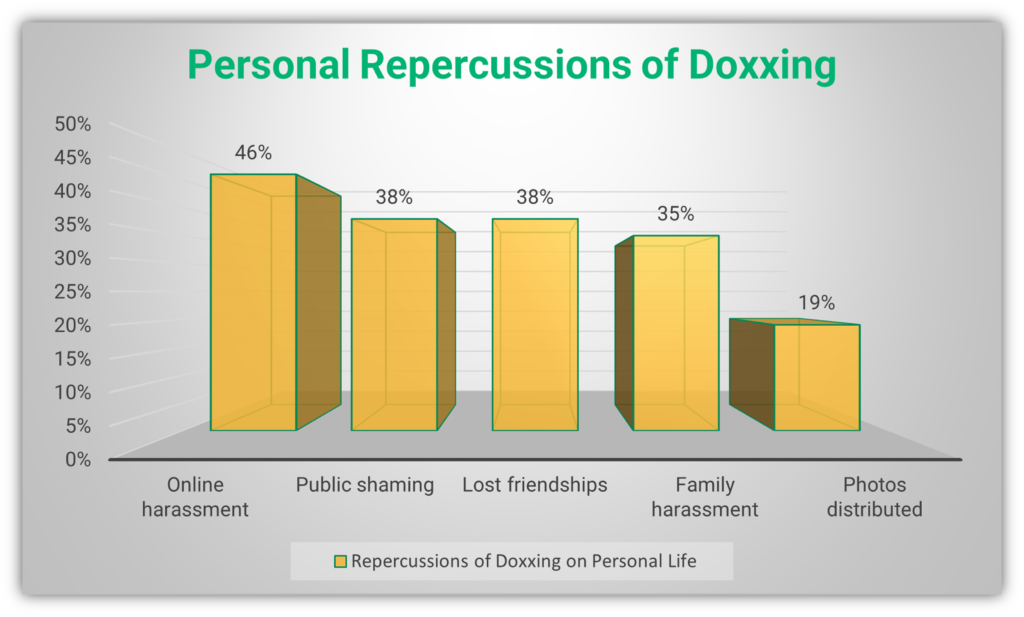
The personal life of the victim is affected on all levels. Almost half of victims face online harassment after being doxxed. Victims face psychological and emotional trauma as a result of doxxing and some go on to develop depression or even commit self-harm, including suicide.
Doxxing often happens when one individual or group of people wants to impose their version of the truth on another. A modern example can be seen in the struggle between extremist groups.
A great example is of a white woman code-named “Fallon” who uses doxxing to target people believed to be white supremacists. She is a part of a group of anti-fascist activists called Great Lakes Antifa and often emails the screenshots of abuse carried out by racists to their employer or church to teach them a lesson.
The question we’re focusing on here is not about being right or wrong, or whether we agree or disagree with the politics involved in this situation. The question we want to focus on here is this: what are the effects of doxxing on the victim?
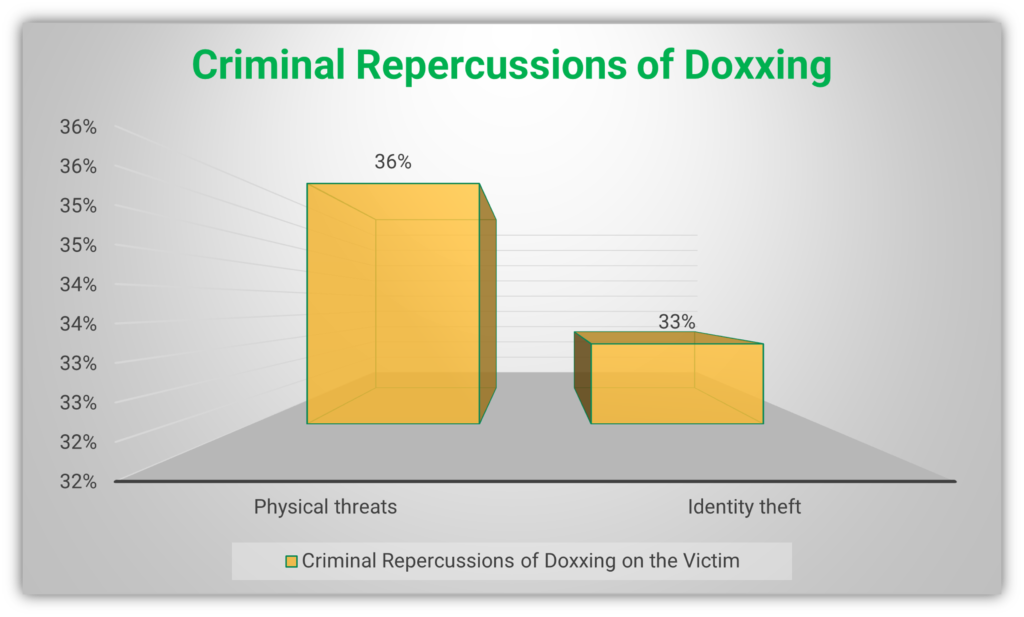
Doxxing becomes a serious issue when the victim faces criminal repercussions, including physical threats and identity theft. Swatting is a type of doxxing attack where a criminal registers a false complaint about the target with the police. As a result of the complaint, a SWAT team will descend on the target causing serious damages.
In 2017, a swatting incident led to the death of 28-year-old Andrew Finch from Kansas. During an online gaming squabble, a prankster called the police with a false report on his opponent. However, they gave an incorrect address, and the SWAT team was directed to Finch’s home. Within seconds Finch was shot by the police, losing his life without ever having had anything to do with the online game, the gamer, or the squabble.
Is Doxxing Legal?
Although it can be harmful, doxxing is not necessarily illegal. There are regulations in some countries to protect personal information, including General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) in California, and the Health Insurance Portability and Accountability Act (HIPAA).
The United Nations Conference on Trade and Development (UNCTD) reports that 66% of countries already have legislation in place for data protection and privacy, and 10% of countries worldwide have draft legislation waiting to be approved. However, if the information doxxed is obtained from legal sources, doxxing itself is not illegal.
Being a fairly new concept, laws governing doxxing are in the development stage. Doxxing is sometimes covered under laws governing stalking, harassment, blackmail, and threats. For example, if you dox a government employee in the U.S., you could be charged with federal offenses under federal conspiracy laws.
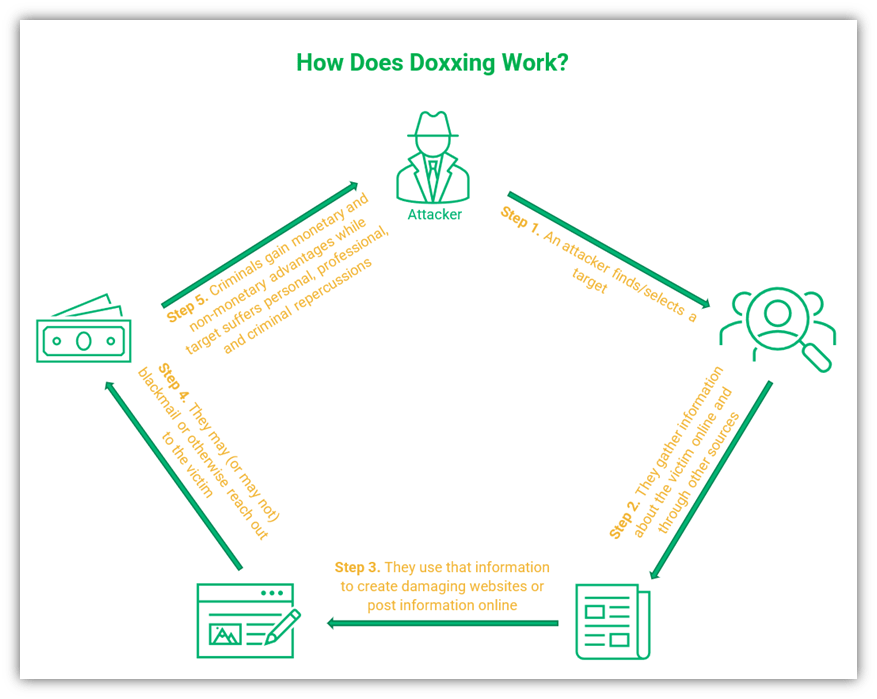
How Does Doxxing Work?
Doxxing involves gathering information about a person and then publishing it on the internet with an intent to cause harm or embarrassment. But how does a doxxer collect personal information about the victim?
Six Ways Cybercriminals Gather Victims’ Information
There are many sources of information for an attackerto dig into, and many places to post it. Some of these are mentioned below:
1. Cybercriminals Use Social Media to Gather and Post Information About Victims
Social media is the richest source of personal information. A doxxer might put together a dossier on the victim by collecting information from various social media sources, including:
- Posts and comments
- Pictures,
- Friends lists,
- Geographic information,
- Family members and pets, and
- Likes, interests, and people they follow.
Sometimes attackers can even work out the answers to security questions from this information.
2. Cybercriminals Gather Website Information From WHOIS Records
If the doxxer is searching for the owner of the domain, the WHOIS records can give that information. Lots of personal info about the owner — like their name, email address, mailing address and phone number — are available here. All of this information can be used to stalk, harass or otherwise affect the victim they’re targeting.
3. Cybercriminals Use Government Records to Obtain Personal Information
Many government records are available online. By sifting through these records, a doxxer can find sensitive information relating to the victim’s driving license, income tax, business registration, property, and voting history. Sometimes, the government keeps records of donations, which can let a threat actor know what causes the victim supports.
4. Cybercriminals Use Social Engineering Methods to Gather Information From the Victim
Psychological manipulation methods used to obtain information from a victim are called social engineering techniques. Social engineering involves using tricks to coax the victim into divulging sensitive information without them being aware. One example is phishing emails and emails containing malicious links to phishing websites that can help a doxxer collect information about the victim.
5. Cybercriminals Use Personal Contacts of the Victim to Gather Information
Usually, many people know the victim personally. Friends and acquaintances know where the victim lives, their phone number, and other personal information. A doxxer can use these people to gain access to the victim’s data. An attacker can befriend the target’s contacts – online or offline – and extract information about the target. Typically, information posted on social media can reveal a lot about a person and their contacts.
6. Cybercriminals Use Malware to Spy on Victims
A doxxer can use malware like spyware and key loggers to find out more about the victim. With malware, an attacker can find out IP addresses, sniff internet traffic to look for sensitive information, and even obtain credit card details and passwords. Online history and purchase records can reveal a lot about a person’s personal life, and a cybercriminal can obtain this information directly or through data brokers who collect and sell data for profit.
Six Different Types of Doxxing
There are different types of doxxing that can disrupt the lives of victims:
1. Celebrity Doxxing
When a doxxer publishes personal information about famous people, it is called celebrity doxxing. Celebrities including Hulk Hogan, Jay-Z, Paris Hilton, Sarah Palin, and Donald Trump are some of the people who have fallen victim to doxxing attacks.
2. Faulty Doxxing
Sometimes attackers mistake the identity of the victim and publish information that doesn’t correspond to that victim. This type of faulty doxxing can ruin the life of that person.
In a recent case of faulty doxxing, a teenage girl called “Lucy” (fake name) living in Canberra, Australia became a victim after her name and social media details were attached to a viral video showing an act of racism. However, it turns out that Lucy was not the person in the video; it was a case of mistaken identity.
As a result, Lucy faces ongoing hate messages, rape threats, and death threats against her and her family. Although the doxxer reportedly regrets his mistakes, he can’t reverse the damage caused by his actions — and Lucy is the one left facing the consequences.
3. Revenge Doxxing
Doxxing is often used as a revenge tactic to get back at the victim for something. A well-known baseball player named Curt Schilling was in the news for doxxing the people who attacked his daughter online. The incident started with Curt congratulating his daughter Gabby online when she was selected to pitch in a game. As many people joined in to congratulate her, others began to troll Gabby.
Curt found out the real identities of these men and informed their sports coaches of their behavior. As a result of his prompt response, the trolls apologized him and his daughter.
4. Swatting Doxxing
Sometimes a doxxer will call the police and report a fake crime to harass the victim. This method is called swatting, as the SWAT team is called to action.
In a horrific incident, a grandfather named Mark Herring died of a heart attack when police swarmed his home and pointed guns at him. His “crime?” Having the Twitter handle “@Tennessee” and refusing to give it up to someone who wanted to sell it for profit. Being proud of his birthplace, Herring loved his Twitter handle. When someone wanted him to give up his handle and he refused, his home address was published online. But it didn’t end there — he was then the target of a false police report.
A doxxer in the United Kingdom called the emergency services and fraudulently informed them that they’d shot a woman at Herring’s address. They also threatened to blow up the home if the police came. The SWAT team responded and raided Mr. Herring’s home, after which he’d suffered the fatal heart attack. The attacker was conspiring with another to “swat” multiple individuals whose social media handles they wanted to sell.
5. Crime Doxxing
Crime doxxing is done to incite criminal actions against the victim. A doxxer will publish sensitive information against the victim and provoke the general public to take action against them.
American dentist Walter Palmer was doxxed after he killed a beloved and well-known lion named Cecil while on holiday in Zimbabwe. His home and clinic addresses were made public leading to people sending death threats and showing up at his home to harass him and his family.
6. Political Doxxing
An example of how political agendas can be aided or fought against via doxxing can be seen in Lebanon. The country has faced major political upheaval in recent years. Political changes within the country have resulted in economic upheaval and civil unrest. Some Lebanese people who are against the new regime have taken things into their own hands, choosing to fight back digitally. They release personal information and real time locations of those in power or who are part of opposing political groups.
Please refer to our article “What is doxxing? 5 examples of doxxing and how to prevent it” for more information on doxxing.
What Next?
Doxxing is a big problem, and many countries are working towards protection of privacy for their citizens. Places like Hong Kong and the United States are developing anti-doxxing regulations to combat these attacks. However, Forbes reports that companies like Google and Facebook have threatened to cease their services in Hong Kong as a result of the region’s bill. Regulations that preserve privacy while enabling the free use of social media are needed, but there’s concern that the companies’ platforms and employees could be held liable over content they “have no control” of that’s generated by users.
Final Thoughts on Doxxing
According to Brittany Kaiser, co-founder of the Own Your Data Foundation who is also known as the Cambridge Analytica whistle-blower, “[o]ur data, our most personal information, has now become the world’s most valuable asset, more valuable than oil and gas.” Doxxing or doxing, whichever way you choose to spell it, is a malicious act where the personal data of a victim is released online with the intent to cause harm.
Doxxing leads to serious consequences for victims and can cause chaos in society. Whatever the reasons behind doxxing, a perpetrator doesn’t have the authority to punish or pursue the victim. Laws that may help to control doxxing are on the way — but, for now, this problem is only growing.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security