How to Disable HSTS in Chrome & Firefox
Follow these easy-to-implement steps to clear HSTS settings in Chrome and Firefox
If you’re here because you’re searching for phrases like “HSTS Chrome disable,” “clear HSTS Chrome,” and “disable HSTS Firefox,” then we’ve got you covered. This article is all about clearing HSTS settings in Chrome and Firefox.
When you try to open a website, sometimes you might come across error messages such as “Your connection is not private” or “Security risk ahead.” But you don’t have the option to bypass these warnings. There could be many reasons for seeing these types of warnings, such as the website’s SSL/TLS certificate is self-signed, expired, revoked, etc. One of the reasons could be that site has enabled HSTS connection.
To get rid of these errors, you’d have to disable HSTS in Chrome or Firefox (if you’re using either of those browsers).
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
So, what is the HSTS connection, and how you can disable HSTS in your browser? In this article, we’ll cover how to disable HSTS in Chrome and Firefox. We’ll also talk about some of the dangers of why you may want to reconsider doing so.
What Is HSTS?
HSTS stands for HTTP strict transport security. It forces browsers to open websites with secure HTTPS connections only. (If you are not aware of how HTTP, HTTPS, and SSL/TLS certificates work, scroll down to the last section of this article). So, if anyone tries to open a web page using HTTP, their browser will block that request and show the error message.
The way that website owners enable HSTS connections on their websites is by including specific code in the websites’ headers. HSTS protects the website visitors from some dangerous cyber threats such as SSL stripping and man-in-the-middle attacks. But unlike any other SSL error, users can’t bypass the HSTS error pages by clicking on the “Advanced” tab and clicking on Proceed to anywebsite.com (unsafe).
But there are ways to disable HSTS in Chrome and Firefox by tweaking some settings in the browsers. By doing so, you are forcing the browsers to bypass the website’s HSTS headers and access web pages using HTTP. However, this is a highly dangerous practice, and we don’t recommend it.
By using HTTP instead of HTTPS, all the communications between you and the website will be in plaintext. This means that hackers can steal a variety of your sensitive information, including:
- Bank account details,
- Payment card numbers,
- Social security number,
- Health information,
- Phone number,
- Physical address, and
- Login credentials.
Having said that, if you still want to access the site and aren’t planning to input any sensitive data, you can disable HSTS in Chrome and Firefox by following the below steps.
How to Disable HSTS in Chrome
To clear HSTS settings in the Chrome browser, do the following:
Step 1: Write chrome://net-internals/#hsts in the address bar.
Step 2 (optional): If you want to check whether the website you are trying to reach has enabled HSTS, write the domain name (without HTTPS or HTTP) under the Query HSTS/PKP domain.
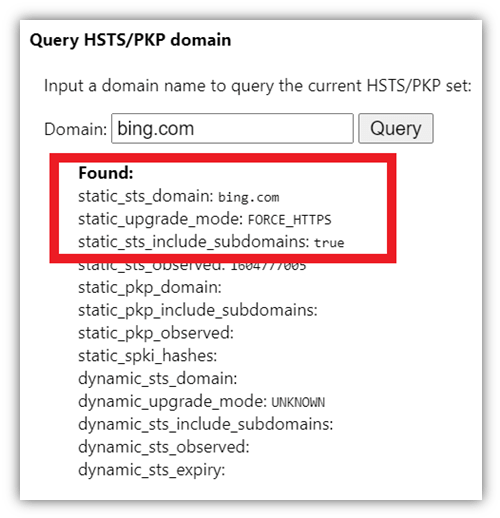
Step 3: Scroll down the page to the Delete domain security policies section. Type the website’s web address (for the site you’re trying to reach) in the field and hit Delete. Please make sure you write the domain name without HTTP:// or HTTPS://. (For example, amazon.com or www.amazon.com)
Check out the screenshot below for reference:
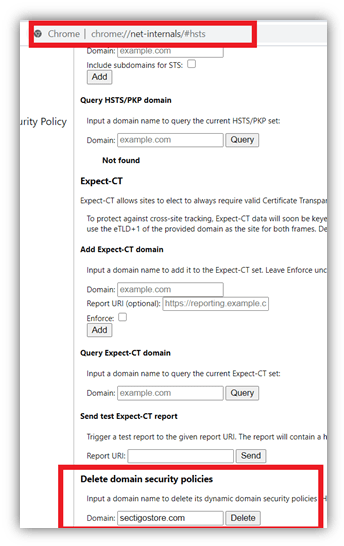
That’s it! This is all you need to disable HSTS in Chrome.
How to Disable HSTS in Firefox
There are actually a few ways to disable HSTS in Firefox. To clear HSTS settings in Firefox, choose any of the following steps and see which one works for you.
How to Manually Disable HSTS in Firefox For a Specific Website
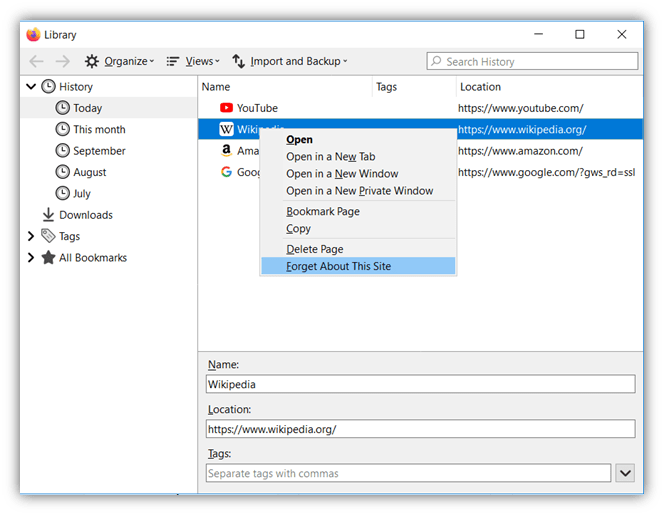
Step 1: Open Firefox and hit Shift+ CTRL+ H (or Cmd + Shift + H on Mac) to open the History window.
Step 2: Find the website for which you want to disable HSTS. You can do this by either selecting the site from the list or by using the Search History feature in the top-right corner.
Step 3: Right-click on the website and select Forget About This Site.
Please note that this step will delete all the saved data (like credentials for auto login) from your cache for this website. For the changes to take effect, you may need to exit and restart Firefox.
How to Change Browser Settings to Disable HSTS in Firefox
Method 1
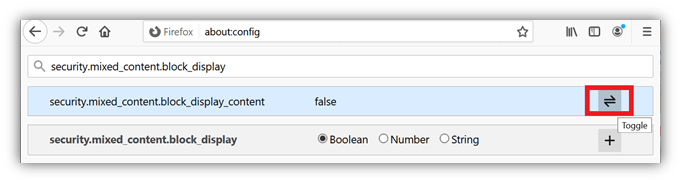
Step 1: Write about: config in Firefox’s address bar.
Step 2: Click on click on the Accept the Risk and Continue button.
Step 3: Search HSTS in the search bar.
Steps 4: Double click on security.mixed_content.block_display_content and set it to true.
Method 2
If the above tip doesn’t work, simply delete the site preference.
Step 1: Open the History tab from the library option.
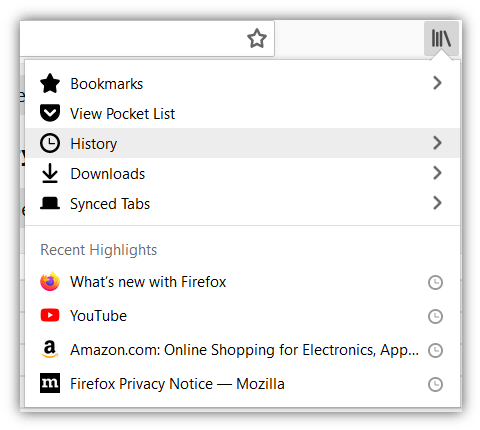
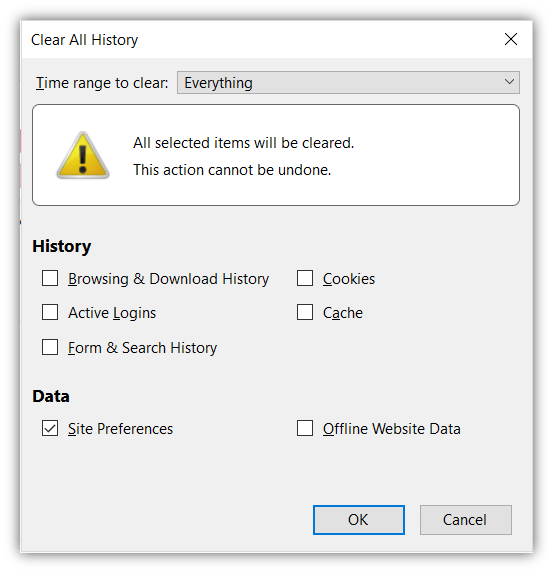
Step 2: Click on Clear recent history.
Step 3: Select Everything in the time range toggle. And select Site preferences under the Data title. Click OK.
Step 4: Restart the browser.
The Basics: How HTTPS Works & Why Websites Prefer HSTS
HTTP stands for hypertext transfer protocol. By default, all the data transferred between a website and its users travels via HTTP. But in HTTP, the data transmits in plaintext format. That means if a hacker intercepts your internet connection via hacking your router or public Wi-Fi ports, they can read, interpret, and steal your sensitive data.
That’s why a more secure communication channel, HTTPS, was developed. HTTPS, which stands for hypertext transfer protocol secure, provides a secure, encrypted channel to transfer the data. Encryption means transferring the plaintext data into an incomprehensible form using a mathematical algorithm. No one can decrypt and interpret the encrypted text without the corresponding cryptographic key.
To enable HTTPS, the website owner installs an SSL/TLS certificate. After the installation, the webmaster needs to do 301 and 302 redirects to transfer all the web pages from HTTP to HTTPS. For example, if I write http://sectigostore.com, it automatically redirects me to https://sectigostore.com. But often, the redirects don’t work properly, and the pages are still accessible with HTTP. Sometimes companies intentionally keep some web pages on HTTP or keep them available on HTTP and HTTPS both.
Risks Associated With Using HTTP Instead of HTTPS
Accessing a website via HTTP is a risky practice. As we pointed out earlier, hackers can intercept your connection to read and steal sensitive data in MitM attacks. Hackers sometimes execute SSL/stripping attacks using a tool called SSLstrip to force browsers to load websites via the insecure HTTP connection.
SSLstrip strips the connection between a user and the server of its secure HTTPS protocol to deploy a man-in-the-middle attack. Whenever the user tries to open a website with HTTPS, the hacker intercepts that request and continues to establish an HTTPS connection between himself and the server instead. So, while the connection between the website visitor and the hacker remains in HTTP, and the hacker and website’s server in HTTPS.
Here, the hacker acts as a bridge between the user and server. They can steal all the user data as it remains in plaintext in HTTP channel. But the server doesn’t get a clue about it as it is establishing an HTTPS connection from its end.
How HSTS Prevents Cyber Risks Associated with Using HTTP
HSTS was created in response to an HTTPS vulnerability that was discovered by computer security researcher Moxie Marlinspike. With HSTS protocol, the website forces the browsers to open the website strictly with HTTPS only. Hence, if someone tries to open a website with HTTP or tricks browsers into loading websites via HTTP, the HSTS protocol blocks such requests.
But the good (and bad, depending on your view) thing about HSTS is that it blocks all types of HTTP requests. That means if an HSTS-enabled website’s SSL certificate is having issues, the browsers won’t allow users to bypass the error page with the regular tricks to get rid of “your connection is not private” or “Security risk ahead” page. But you can use the above mention tips to force your browsers to ignore the HSTS protocol.
Wrapping Up on How to Disable HSTS in Chrome and Firefox
HSTS plays an important role in data security. In fact, the U.S. General Services Administration (GSA) announced in June 2020 that they want to force all the .gov domains run on HTTPS and use HSTS for the same.
But as a website visitor, if you want to disable HSTS, all the prominent browsers will allow you to do so. Just make sure you don’t share any confidential information on the site running on HTTP. Attackers can steal that information and make you a victim of financial fraud or identity theft-related crimes.














 (45 votes, average: 4.38 out of 5)
(45 votes, average: 4.38 out of 5)







2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security