What Is SSL Inspection and How Does It Work?
Quit wondering if your server is being bogged down by requests from illegitimate sources — here’s what to know about HTTPS inspection and how it works
If you’ve been wondering what the terms “SSL inspection,” “TLS inspection,” “SSL interception,” or “HTTPS inspection” mean, we’re here to help. In this article, we will delve deeper into these concepts.
With Google’s effort to push for encrypted web traffic, most of our communications now occur over a secure HTTPS connection. Because encrypting your traffic protects your data from being stolen or manipulated, installing an SSL/TLS certificate is a definitive step towards improving website security.
However, bad actors can leverage these encrypted connections to distribute malware and steal confidential data out of corporate networks. The SSL inspection mitigates such risks and provides extra layer of security to your website and users.
What Is SSL Inspection? How Does It Work?
In a nutshell, SSL inspection (HTTPS inspection, TLS inspection) is a way to identify malicious activity that occurs via encrypted communication channels. SSL inspection works like an authorized man-in-the-middle (MitM) attack, where the encrypted traffic between the client and the server is decrypted and examined.
Of course, this may make you ask, “doesn’t that defeat the purpose of encrypting the data to prevent eavesdropping and tampering?” And in some ways, you wouldn’t be wrong, and the whole process might even seem counterintuitive. But since most hackers use encrypted channels to spread the malware, it doesn’t leave us with much choice apart from investigating the traffic that flows between the servers and browsers.
Many security tools can’t detect malware in encrypted traffic and, therefore, pass through unnoticed. Because SSL inspection can be used to inspect all traffic, it means that it can be used on inbound and outbound traffic alike.
What Are SSL Inspection Tools?
There are different terms that people use for the SSL inspection appliances. For example, an interception device, often referred to as a middlebox, decrypts and analyzes the traffic and filters out any malicious content.
In a typical corporate network, you might have
- next-generation firewalls,
- network sandboxes to monitor and analyze suspicious traffic,
- intrusion detection systems/intrusion penetration systems (IDS/IPS),
- data loss prevention (DLP) solutions,
- web gateways, etc.
When you deploy an SSL inspection software, it intercepts the traffic, and after decrypting, it scans the content. It can also forward the content to an IDS/IPS, DLP, etc. in parallel. After obtaining the results, the traffic gets re-encrypted and forwarded to its destination.
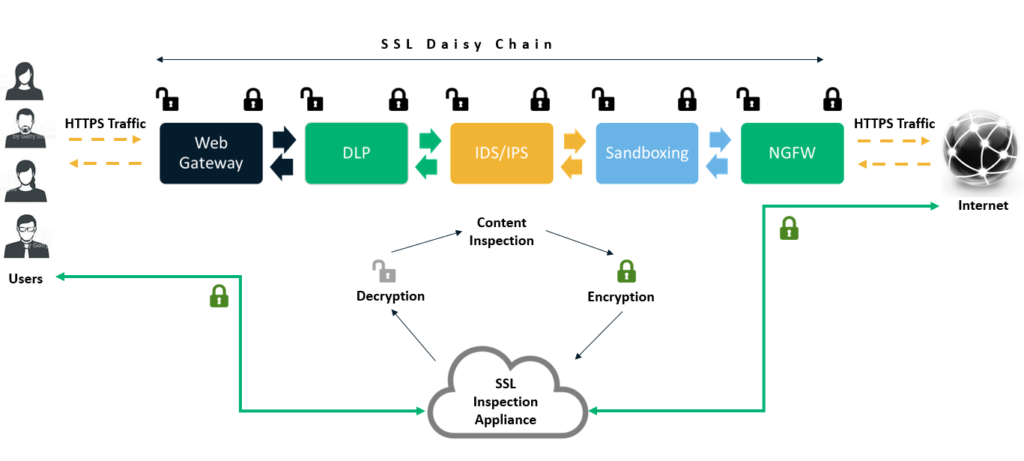
The figure above depicts both the scenarios:
- The traffic being decrypted and re-encrypted at every level, and
- The traffic passes through a device handling HTTPS / TLS inspection.
An SSL inspection appliance can, in turn, decide whether to run the unencrypted traffic through a DLP, firewall, etc., and can send it over to multiple software for filtering the traffic in parallel to minimize latency. Because, if the incoming or outgoing traffic is decrypted, inspected, re-encrypted, and then forwarded at each layer, it may introduce multiple single points of failure, impact performance, increase latency, and ultimately accounts for inelegant design.
What Are the Advantages of Enabling HTTPS Inspection?
Now that we understand how TLS inspection works, you may well be able to outline the benefits of using an SSL inspection appliance in your network. Let’s take a look at some of the benefits of inspecting HTTPS traffic. It gives you the ability to:
- Detect malicious requests and block them to prevent a potential DDoS attack
- Gain greater visibility of malicious users and IP addresses
- Monitor the traffic flowing out of your network
- Have the right tools in place to deploy any artificial intelligence (AI) or machine learning (ML) solutions in your environment (which shed light on traffic patterns).
What Are the Disadvantages of Performing a TLS Inspection?
In place of a continuous connection between the client and the server, two individual SSL connections are established — amongst the server and the interception device, and between the interception appliance and the client browser. This interruption, unless the implementation is done correctly, may impact efficiency and introduce security concerns of its own:
- Using earlier, obsolete cryptographic standards for decrypting and re-encrypting the traffic can significantly reduce the encryption strength and jeopardize the overall data security.
- Based on the advisory warning issued by the U.S. Department of Homeland Security’s US-CERT group, middleboxes performing HTTPS inspection often don’t verify certificate chains accurately before forwarding the traffic, which leads to weakening the overall security benefits of TLS encryption.
- A study by cryptography experts from several prominent organizations who analyzed 12 popular network middleboxes shows that only one (Blue Coat ProxySG 6642, which is owned by Symantec) preserved security and mirrored the client browser’s capabilities. The rest were found suboptimal, vulnerable to known attacks, or severely broken. The research also looked at anti-virus software running on consumer computers. According to the data:
- Out of nearly 8 billion SSL/TLS handshakes that were analyzed, 10.9% of them were intercepted.
- 62% of the traffic that passed through middleboxes experienced reduced security, and
- 58% of the traffic demonstrated vulnerabilities that could be exploited later (either because of susceptibility to known attacks or due to the introduction of severe security weaknesses).
How SSL Offloading Helps in SSL Inspection?
The primary function of your web server is to serve the pages and all related content requested by the client browser. Getting caught up in SSL-related functionalities is resource-intensive for your server and puts a strain on it, which affects your website’s performance. This is where offloading can help in the SSL inspection process.
Offloading SSL uses a load balancer tool to take the pressure off your application server. There are two ways in which this can be accomplished:
- SSL Termination — In this method, an incoming request from a client browser connects with the SSL terminator (what’s also known as an SSL load balancer or a proxy server) over an HTTPS connection. However, the connection between this edge device and the server is unencrypted, (i.e., over HTTP). Since the traffic between the server and the terminator flows in plaintext, it leaves the data vulnerable to security breaches, if you have an attacker inside your network.
- SSL Bridging — With SSL bridging, the traffic between the edge device and the server flows over an HTTPS connection after it is re-encrypted by the edge device.
Where DPI SSL Fits into the Equation
Another term that’s frequently thrown around in conversations about SSL inspection or HTTPS inspection is DPI SSL. So, what is DPI SSL? It signifies the deep packet inspection of encrypted SSL traffic (typically done by a firewall). This process involves decrypting and analyzing data before determining whether to block the traffic or re-encrypt and forward it to its destination. All you need to do is obtain an SSL/TLS certificate for the DPI SSL firewall that’s trusted on both sides by the client browsers as well as the server.
It’s also useful in cases where someone tries to get past content filtering by going through a proxy site. This is especially helpful for an organization that wants to block certain sites or restrict the bandwidth taken up by streaming services on business networks. Without DPI capabilities, signature-based firewalls can’t identify and block HTTPS traffic because it’s rendered unidentifiable on account of being encrypted. However, for deep packet inspection, you’ll need to invest in a firewall with higher processing power.
Wrapping Up the Topic of SSL Inspection
We hope this article answered your “what is SSL inspection?” question and provided you with a better understanding of how it works, and what its benefits and pitfalls are. Of course, having this knowledge of SSL inspection may leave you wondering whether you should examine the HTTPS traffic within your organization to detect malware, or maintain the status quo with your fingers crossed.
From a theoretical perspective, HTTPS inspection is the obvious choice and should be implemented without the shadow of a doubt. However, since using a middlebox might ultimately compromise security (depending on how it handles TLS connections and whether it supports the latest cryptographic standards), its implementation is a choice that needs to be debated carefully before you make a move one way or the other.
Besides the nature and scope of your business, a lot depends on the specific product you choose because it might either improve your overall security or punch a hole right through it.














 (16 votes, average: 4.69 out of 5)
(16 votes, average: 4.69 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security