What Is Cryptojacking? How to Define, Explain & Prevent It
Coinmarketcap.com reports that the cryptocurrency market’s worth has surpassed $393 billion. Cryptojacking is one of the ways that cybercriminals try to get a piece of the action…
What is cryptojacking and how do you prevent it? Cryptojacking, also called malicious crypto mining, is a type of cybercrime that involves the illegal mining or theft of digital currencies such as Bitcoin, Monero, Dash and Ethereum. This process generally involves compromising other devices to steal their processing power and other related resources.
In a cryptojacking attack, hackers “hijack” the processing capabilities of users’ devices to illegally “mine” for cryptocurrencies. (Hence the clever name.) In some cases, they steal previously mined cryptocurrencies from the targets’ crypto wallets.
Basically, there are four main ways to get your hands on cryptocurrencies (virtually speaking, of course) in general:
- Buy or invest in cryptocurrencies such as Bitcoin.
- Create a high-powered setup (or rent processing capabilities from others’ machines) to legally mine cryptocurrencies. Warning: it’s expensive and is super resource intensive.
- Hijack the computational resources of others’ computers to use them to mine crypto illegally without their consent.
- Steal mined crypto currencies from the cryptographic wallets of other crypto miners or investors.
As you can probably guess, the first two are legal but the last two are diving head-first into illegal waters. And the latter area is right where cryptojacking cybercriminals love to swim.
So, if you’re wondering what cryptojacking is and how it works more in depth, then you’ve come to the right place. Not only are we here to answer your question “what is cryptojacking?” we’ll also talk about how to prevent cryptojacking from affecting you and your business.
What Is Cryptojacking? A Definition
Cryptojacking is a term that traditionally describes the hijacking of computer resources and power to mine for cryptocurrencies. Basically, it’s the ugly version of cryptocurrency mining. This is the most common cryptojacking definition. For example, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) describes it as such:
“Cryptojacking occurs when malicious cyber actors effectively hijack the processing power of the victim devices and systems by exploiting vulnerabilities—in webpages, software, and operating systems—to illicitly install cryptomining software on victim devices and systems.”
However, some cryptojacking definitions also use the term to describe cryptocurrency theft, saying it’s a way for cybercriminals to use scripts and codes to illegally get their hands on the contents of your cryptographic wallet.
With this difference in definitions in mind, there are two main ways to think about how cybercriminals engage in cryptojacking:
- Cybercriminals can steal the processing capabilities of unsuspecting individuals’ devices to mine for cryptocurrencies. (This is the most common way people describe cryptojacking.)
- Cybercriminals can steal cryptocurrencies from others’ cryptographic wallets. This can be done either through the use of cryptojacking code or through the malicious use of legitimate crypto mining software.
The first example of cryptojacking is a process that’s related to cryptocurrency mining (which we’ll talk more about shortly). However, it’s the covert and often illegal version of it because it’s done without the device owner’s consent or knowledge. While crypto mining is a way that legitimate computer users can profit, cryptojacking is all about stepping on others and stealing their resources to come out ahead financially. All the while, the people who are being stepped on are blissfully ignorant of what’s happening and how their devices are being used.
As a malicious and illegal form of cryptocurrency mining, cryptojacking cybercriminals rely on the use of malicious code or cryptojacking script to do their bidding. These scripts can be delivered via phishing emails or through the use of malicious ads. Either way, malicious code loads onto your device or browser, and it enables cybercriminals to use your computing and graphics power to mine for cryptocurrencies.
Thankfully, law enforcement are trying to crack down on cryptojacking criminals. In fact, the U.S. Department of Justice (DOJ) reported at the end of 2019 that two Romanian cybercriminals were sentenced to 20 years and 18 years, respectively, for their roles in developing and distributing crypto mining malware.
What Types of Devices Are Affected by Cryptojacking
Cryptojacking attacks don’t discriminate — cryptojacking code payloads can deploy on desktop computers, laptops, tablets, smart phones, gaming systems and other devices. Basically, if it can connect to the internet, it can be a target for cryptojacking attacks.
But why would cybercriminals target smartphones? They only have limited processing power, right? True. But when you add together hundreds or even thousands of such devices, those “minimal” resources quickly add up. Cybercriminals create entire botnets that consist of thousands or hundreds of thousands of devices with the goal of cryptojacking (think Smominru or the newly discovered Prometei cryptojacking botnet). So, 1+1+1+1+1… You get the picture.
And while all of these illicit activities are occurring, you’re none-the-wiser about it and may simply be wondering why your device suddenly seems sluggish.
Cryptojacking Scripts and Code: 4 Signs Your Device or Website May Be Compromised
So, how do you know if your device or site is being used as a pawn in a cryptojacking scheme? There are a few things that indicate that your device or website may be compromised by a cryptojacking script or code:
- Your device is slow or having other performance issues (such as crashing). We already touched on this one. If your device seems abnormally slow or exhibits performance issues, you may have cryptojacking code running on your machine.
- Your battery is draining more quickly or your device is overheating. All crypto mining activities, including malicious crypto mining, are resource-intensive processes. As such, it’ll drain your device’s battery noticeably faster than normal usage.
- You notice abnormally high CPU usage and latency. If your device seems to be steaming ahead at warp speed, it’s a good indication that something’s amiss.
- You notice changes to your website’s files or code. Whenever there are changes like this that you don’t remember making, it’s always a red flag.
Cryptojacking code can be hard to detect because 1) it often doesn’t involve the use of a traditional downloader, and 2) it may piggyback on legitimate crypto mining scripts and software. However, if you discover crypto mining malware during a scan, that’s a clear indication that your system is compromised.
Now that you know what to look out for, let’s take some time to better understand how cryptojacking works. But to do that, you first need to know how legitimate crypto mining works. (Don’t worry, we’ll make this part relatively quick.)
Crypto Mining: How You Mine Cryptocurrencies Legally
Cryptocurrency mining is the law-abiding cousin of cryptojacking. Unlike its outlaw cousin, crypto mining is a way to legally generate digital money through the use of computers, encryption, and a shared list of data blocks known as a ledger. (This is also known as a blockchain.)
Of course, we’re not going to get into all of the technical specifics here — we’ve already recently done that in an article that breaks down what crypto mining is and how it works.
But to sum it up quickly, crypto mining is the process of use of massive amount of computing power to try to solve equations and verify cryptographic functions. You do this in competition with other crypto miners for a chance of being rewarded for your effort with cryptocurrency.
Let’s consider this in terms of the most well-known cryptocurrency. In Bitcoin, the crypto mining process involves the use of computers to solve equations. (Basically, you automate the guessing process to continually try to solve the equation). If successful, then they have to update a shared ledger to reflect any changes. When this happens, you’re rewarded with a new Bitcoin in your crypto wallet.
Pretty sweet, huh? Well, don’t quit your day job just yet. Crypto mining isn’t an easy process and, frankly, it involves a massive amount of computational power. This makes it incredibly expensive to do at scale, and crypto mining is all about speed. (We’ll talk more about those energy consumption costs a little later.)
If your computer can’t guess numbers quickly enough to try to solve the equations, then someone else who has a system who can is going to beat you to the punch. And if they announce their answer to the equation before you do, the jig’s up and they’re the ones who get the rewards. And all you get is a lousy t-shirt saying that you competed (and that’s only if you make such a shirt for yourself.)
Cryptomining Abuse: The Two Primary Cryptojacking Methods
As we mentioned a little bit ago, there are two main ways that cybercriminals illegally mine for cryptocurrencies. Typically, this involves the use of device- and browser-based malware or scripts. Some scripts have worm capabilities, which makes it so that they can spread across your network in order to compromise other devices.
But do cybercriminals choose one method over the other? Sure. But many opt to use both methods and achieve better results and “get a better bang for their buck,” as the saying goes.
Browser-Based Cryptojacking
This type of cryptojacking method involves creating malicious crypto mining scripts that hackers can inject into websites. There are a few ways they can choose to do this, such as by hiding the code on websites via malicious ads (malvertising campaigns), outdated plugins, or other vulnerabilities.

But regardless of the method they choose, when legitimate users visit those sites, the malicious code executes. And, of course, there are also concerns that illicit cryptomining activities continue even after you close out of a compromised site.
The Broadcom Threat Landscape Trends report from the Symantec Threat Hunter Team shows that there was a sharp increase in reports of blocked browser-based cryptojacking attempts in Q2 2020. These types of attacks spiked 163%. And if you guessed that the two most commonly stolen types of cryptocurrencies in browser-based cryptojacking attacks are Bitcoin (BTC) and Monero (XMR), then you’d be right.
One Google Chrome extension that captured the attention of cybersecurity researchers at the beginning of 2020 was, pardon the language, Shitcoin Wallet. While this particular browser extension was marketed as a way for users to conveniently manage their Ether coins and some Etherium tokens in browser, appearances can be deceiving. ZDNet reports that the extension actually injected JavaScript code on web pages. This code would allow hackers to steal private keys and passwords from the users’ crypto wallets and portals and send them to a third-party site.
In our social media scams statistics article, we also shared with you about how social media sites are a way that cybercriminals deploy crypto mining malware. Research by Bromium and Dr. Mike McGuire at the University of Surrey shows that ads, apps and various links that are posted via social media platforms also serve as payload delivery methods for various strains of crypto mining malware. Their report indicates that these cryptojacking attacks give cybercriminals $250 million annually.
Not a bad payout considering that cryptojacking jerks aren’t contributing a cent toward the costs required to run all of the devices they’re using… wouldn’t you agree?
Device-Based Cryptojacking
This type of cryptojacking involves covertly loading malware or malicious code on companies’ and users’ devices and networks to steal their resources. They can do this by using malvertising to install drive-by malware onto users’ devices, or by getting users to download malware themselves through other means such as via phishing emails or watering hole websites.
Trojans also are a way to deploy cryptojacking code and scripts. These covert types of malware are often hidden within decoy downloader apps so you don’t know they’re there.
Regardless of how the crypto mining payload deploys, once it’s done so on your device or network, it’s bad news for you. Unbeknownst to you, the malware takes over your device’s vital resources, making it seem laggy and sluggish. But doesn’t it require hackers to deploy different types of code to work with different systems? Yes, but cybercriminals are resourceful enough to even make this problem a non-issue.
An AT&T AlienLabs technical analysis of select crypto mining worms shows that once a machine becomes compromised, different variations of malicious code continuously deploy until one’s found that’s compatible with the target’s system:
“Rather than trying to select the system architecture and then download the corresponding implant, the malware authors have opted to download implants in a loop and then break the loop when the first implant sticks.”
Volgar Malware Targets Microsoft SQL Servers Across Various Industries
GuardiCore reports that cybercriminals were targeting servers running Microsoft SQL in a two-year long global campaign called Vollgar. The apparent goal of the campaign was to deploy remote access tools (RATs) and cryptominers, which they believe infected upwards of 3,000 devices per day.
A Brief History of Crypto Mining & Cryptojacking
Crypto mining really seemed to gain traction in late 2017 with the creation of CoinHive. This crypto mining service marketed itself as a way for legitimate domain owners to mine for cryptocurrency as an alternative way to generate revenue without the need to have ads marring their websites. What this service did was make it so that CoinHive-embedded sites would capitalize on the computer and processing resources of their users’ devices (while they’re on the site) to mine for cryptocurrencies.
However, this service caught the attention of cybercriminals. And as cybercriminals often do, they took a potentially positive service and turned it into something ugly.
Hackers began deploying CoinHive-based cryptojacking malware to attack and steal from unsuspecting users’ crypto wallets. But crypto mining at scale takes a lot of computational power — and that’s in part because cryptocurrencies themselves consume a lot of electricity.
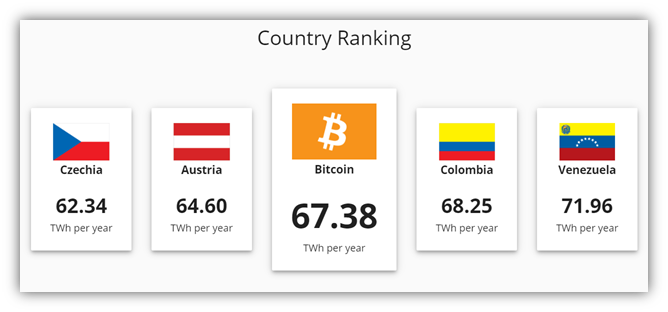
The Cambridge Centre for Alternative Finance at the University of Cambridge created a tool that estimates Bitcoin network power consumption. It’s estimated that the annualized energy consumption is 67.38 TWh (terawatt hours). That’s more energy being consumed to power Bitcoin for a year than the entire country of Austria uses for the same period.
These digital devils realized that to make this happen, they needed more juice.
Although hackers frequently used CoinHive malware as their go-to tools, that went by the wayside once the legitimate CoinHive called it quits in early 2019. Now, cybercriminals can use XMRig and Bitminer cryptominer variants, but as SonicWall says in their 2020 Cyber Threat Report, the collective volume of these two malware is just a “fraction” of the CoinHive-related malware.
What Makes Cryptocurrencies So Attractive to Cybercriminals

Cryptocurrencies are popular with investors and cybercriminals alike because they’re an alternative to the traditional, centralized banking. This means that instead of going through a bank, transactions take place using a decentralized ledger that’s maintained by a network of users.
BitCoin, the world’s first cryptocurrency, came into being back in 2009. Since then, the topic of cryptocurrency has become a big interest to investors and cybercriminals alike. According to coinmarketcap.com, there are now 7,487 cryptocurrencies in existence with a cap market value that surpasses $397 billion (as of Oct. 23, 2020).
This decentralization and lack of regulation is also what makes cryptocurrencies incredibly attractive to criminals. They like to use cryptocurrencies as a way to buy and sell less-than-savory items without government oversight on the black market, or to demand extortions from targets in ransomware attacks. When it comes to cryptojacking attacks, one of the most frequently targeted types of cryptocurrency is Monero.
Cryptojacking Is Only One Method of Cryptocurrency Theft…
But just how big of a threat is cryptojacking? Well, if you asked that question back in 2018 or early 2019, we’d say it’s a major concern financially speaking. After all, cryptojacking attacks resulted in a total of 52.5 million hits in the first six months of 2019 alone, according to SonicWall’s 2020 Cyber Threat Report.
Although it’s nowhere near “gone,” cryptojacking overall now appears to be less of a concern overall in that vein. Of course, there’s the Q2 2020 spike in browser-based cryptojacking reports. But I guess we’ll just have to see what the rest of the year holds.
But why should a cybercriminal go through all of the hassle of mining cryptocurrency illegally when they can just steal it from your wallet another way?
The Rise of Wallet Cryptocurrency Theft Through SIM Swapping Attacks
A more common — and dangerous — method of stealing cryptocurrencies is through the use of SIM swapping attacks. SIM swapping in and of itself isn’t a bad thing. In fact, users legitimately use SIM swapping to port their phone number to a new device in the event that their existing device becomes lost or gets damaged or stolen. It’s a really useful tool that phone companies can use to help their customers.
But as with many good things in life, cybercriminals like to twist this solution and use it to their advantage — and this is when SIM swapping attacks occur. In this type of attack, cybercriminals impersonate you and trick or manipulate one of your phone carrier’s employees into thinking that they’re performing a legitimate SIM swap for you. In some cases, they might even have someone on the inside that they’re paying or blackmailing into doing these SIM swaps for them.
Regardless of the reason why they do it, the result is still the same: your phone number gets ported to the cybercriminal’s new device, which means that the cybercriminal now has access to and control of any of your accounts that are linked to your phone (email, bank accounts, etc.). So, if you have a cryptocurrency wallet linked to your device, they can then use your number to gain access to it and steal your cryptocurrencies. (Because they control your phone, they often can bypass multi-factor authentication and two-factor authentication methods because one-time passwords and confirmations are often sent via SMS text messages and emails.)
So while it’s true that cybercriminals target all types of people — politicians, celebrities, CEOs, and even random users — their attacks often target cryptocurrency investors because of the potential for a big payout that’s difficult to trace and even harder for law enforcement or individuals to recover.
SMS-Based Two-Factor Authentication Isn’t as Secure as You Might Think…
Researchers and Ph.D. students at Harvard and Princeton published a six-month empirical study on wireless authentication and SIM swapping. Their research, which involves five major U.S. mobile carriers, shines a light on security vulnerabilities relating to SIM swap attacks and the use of SMS texting as a method of two-factor authentication.
One of the readers, Arvind Narayanan, shared the following post on his Twitter research account:
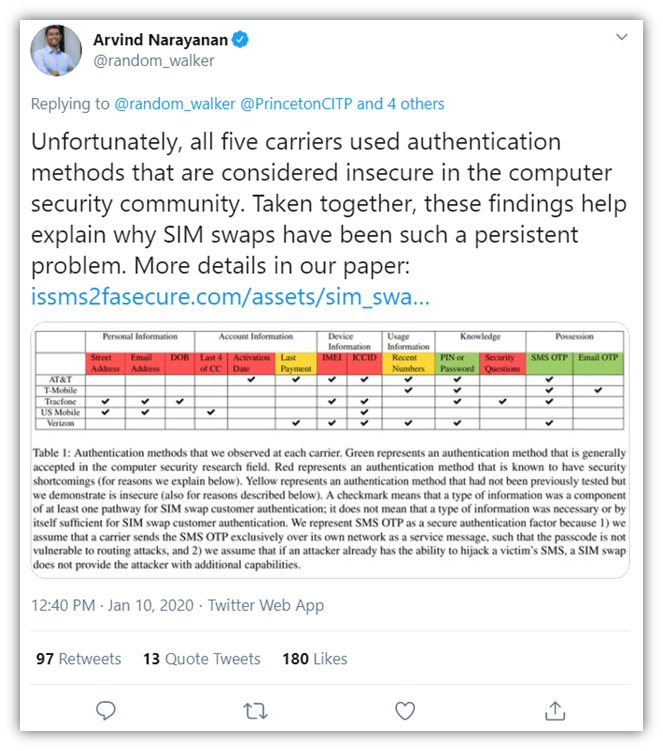
The concerns about SMS text messages being redirected or intercepted is enough of an issue that the National Institute of Standards and Technology (NIST) suggested deprecating SMS as a second factor method of MFA authentication a few years ago. Although they eventually removed some spicy language that included words like “deprecation,” what they did end up including in the final draft of SP 800-63b: Digital Identity Guidelines: Authentication and Lifecycle Management is the following:
“Use of the PSTN for out-of-band verification is RESTRICTED as described in this section and in Section 5.2.10. If out-of-band verification is to be made using the PSTN, the verifier SHALL verify that the pre-registered telephone number being used is associated with a specific physical device.”
They then quickly followed this statement with another:
“Verifiers SHOULD consider risk indicators such as device swap, SIM change, number porting, or other abnormal behavior before using the PSTN to deliver an out-of-band authentication secret.”
How to Prevent Cryptojacking From Affecting Your Site and Devices
This is a great question to ask. If you’re wondering how to prevent cryptojacking, there are a few things that you should know.
Educate Yourself (and Your Employees) About Phishing Emails & Malicious Websites
Phishing is a common way that cybercriminals try to deploy all types of malware or other malicious code. This includes cryptojacking code and malware. With this in mind, require all of your employees to engage in cyber awareness training and test their knowledge with random phishing tests. This will allow you to see how (or if) they’re applying what they learn and identify areas where cyber awareness is lacking for future training.
Train & Prepare Your IT Staff to Face Cryptojacking Threats
Of course, when we say to train all of your staff, we mean all of them. This includes your IT pros. Ensure that they have the knowledge and tools they need to identify and respond to cryptojacking-related activities and payloads.
Block JavaScript In Your Browser
Blocking JavaScript can help to protect you against drive-by cryptojacking. While it may seem inconvenient and may prevent certain functionalities, you must decide what is more important.
Install an Ad Blocker in Your Browser or On Your Mobile Device
Considering that malicious ads are a common way to deliver cryptojacking scripts and code, it’s better to avoid that issue altogether by blocking ads. Plus, you get the added benefit of no longer being bombarded by a litany of political advertisements and other ad-related annoyances.
Regularly Scan Your Website for Vulnerabilities
While this is an industry best practice that you should already be doing, we’re just going to include it here just in case another reader isn’t already doing so. (Yeah, we know you’re already doing that on a daily basis, right?)
Keep Your Devices and Software Patched and Up to Date
Remember how we mentioned earlier that some cryptojacking payloads take advantage of existing vulnerabilities such as outdated plugins? Yeah, well, this can help you avoid that issue. Regularly updating your systems, software and devices ensures that you’re not going to be a victim of an exploit that a publisher or manufacturer patched years ago but you never bothered to implement.
Final Thoughts: What Cryptojacking Is and How It Works
Yeah, this is a lot of information to cover. However, I hope that this article answers your questions like “what is cryptojacking?” as well as “how does cryptojacking work?” and “how do you prevent malicious crypto mining?”
While there’s certainly a lot more ground we could cover in an article like this, there’s only so much time in the day and we also wanted to make sure that it was something everyone could follow along with regardless of their level of tech knowledge.
So, to quickly summarize what cryptojacking is and how cryptojacking works:
- Cryptojacking is a malicious form of crypto mining.
- Unlike legal crypto mining, cryptojacking uses malicious payloads to deploy cryptojacking scripts and code onto unsuspecting users’ devices and browsers.
- These malicious tools hijack those devices’ valuable resources without their owners’ consent or knowledge. They can use these compromised devices as part of larger cryptojacking botnets.
- Cryptojacking typically uses either device- or browser-based attack vectors.
- This type of payload is often deployed in browsers and on popular websites via injections, outdated extensions, and malicious ads.
- While cryptojacking was on the decline, browser-based cryptojacking picked up traction in Q2 2020.
- There are several key indicators that your device may be running cryptojacking code, including poor device performance and high CPU usage.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security