Botnet Attacks: What Is a Botnet & How Does It Work?
Juniper Research estimates that there will be 83 billion IoT devices in existence by 2024, — a lot of potential zombies for botnet armies.
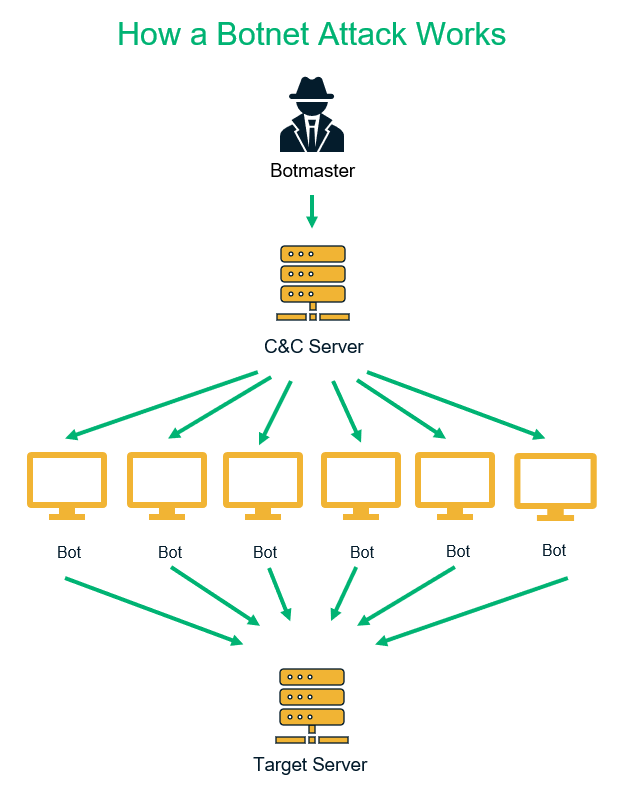
The term “botnet” refers to a connected network of malware-infected devices that are controlled by hackers. To put it simply, a botnet is a robot network of compromised devices that cybercriminals frequently use for a variety of cybercriminal activities. A botnet attack is a type of cyber attack that uses a botnet as part of its strategy.
The Four Key Components to a Botnet (and the Roles They Play in Botnet Attacks)
A botnet consists of four key components:
- A botmaster or bot herder (botnet herder) is the hacker that organizes the botnet attacks.
- A command and control (C&C) server is the central computer that cybercriminals use to communicate with all other infected devices. Please note that not all botnets use C&C servers (for example, random topology botnets). They make peer-to-peer botnet networks to transmit the data instead. (We’ll cover that point in detail later in this article.)
- The bot code is the trojan horse that is designed for botnet attacks. They are also called botnet malware.
- Botnet hosts, bots, or zombie devices are the botnet malware-infected devices. Botmasters use internet-connected devices (i.e., IoT devices such as cell phones, computers, cable boxes, IP/CCTV cameras, Wi-Fi routers, etc.) as botnet hosts.
How Botnet Works? Explore 3 Main Phases
Phase 1: Recruiting New Hosts to Join Botnet Army
A prerequisite of a botnet attack is ensuring that you have enough infected hosts operating on the same C&C server. A botmaster typically infects new devices by using the following common malware insertion methods:
- Phishing emails: The attacker sends their targets phishing emails while posing as legitimate companies, recruiters, tech support teams, employers, colleagues, etc. These emails contain malicious attachments, macros, or links to redirect users to a spammy website. When users download infected attachments or click on the malicious links in the emails, the botnet malware may auto-install on the users’ computers.
- Malicious websites: Some websites hide malware in images, videos, songs, slideshows, files, software, and ads. Links and buttons may also be infected with malware. Whenever users visit these sites and either download infected media files or click on corrupt links, the botnet trojan then infects their computers or devices.
- Vulnerability exploits: The botmaster scans the internet for connected devices that have known vulnerabilities such as CVE-2019-3396, CVE-2020-5902, etc. They exploit these vulnerabilities to insert malware into the devices. Once a device gets infected with a botnet trojan, it also searches for other vulnerable devices to infect and make them join the same botnet network.
Phase 2: Establishing Communication Between the Host Device & Bot Herder
For establishing the internal communication in a botnet, the botmaster creates one of these two paths.
Client-Server Network:
Here, all of the infected hosts (clients) take commands from and report back to a single central server. In some cases, the attacker will use an Internet Relay Chat (IRC) network to communicate. This means that all of the compromised clients must know the right IRC server, port, and channel to connect to in order to communicate with the master server.
Website: Sometimes, the bot herder uses a website (domain name or IP address) as the central point of contact. When the infected bots reach out to the website, they get access to a list of commands to execute. Operating the website is way easier than the IRC network, especially when the client bots are in a large number. Plus, the entire botnet can get the benefit of an encrypted HTTPS channel to hide their communication.
The downside of using this method for cybercriminals is that if the hosting site discovers unusual activity, they can instantly take down such a website. Then the hacker has to create a net centralized point of contact for their botnet.
Peer-to-Peer Botnet Network
This is a more advanced channel. Here, the bots don’t receive commands through a centralized C&C server; rather, they the pass on commands they receive to other bots directly. The government and cybersecurity researchers face many challenges when trying to detect P2P networks because they’re frequently decentralized. It’s challenging because they can’t target, monitor and take down any particular server because bots are not communicating with any centralized C&C server.
Not all P2P networks are made in the same way and have different topologies based on their structures. The structure would be different for a P2P network that has devices behind firewalls or just proxy server access.
Bots sometimes use public key infrastructure, too. The digital signature component makes the detection and interception of peer-to-peer networks quite difficult for security researchers. Digital signing involves using asymmetric encryption that involves two keys — one public, one private.
Asymmetric keys: Here, attacker inserts a public key into the malware that infects the zombie devices. To avoid the hijacking of the botnet, the attacker signs all the commands with the corresponding private keys before distributing them to botnet. The bots authenticate the commands using the public key to make sure the commands are coming from the botmaster only.
Symmetric keys: In some P2P botnets, each bot generates its own symmetric key and other bots can use it to transfer information with each other. So, the symmetric key is used by both the botmaster as well as other bots to pass on the information to other bots. In this scenario, no other clients can join the peer-to-peer network without a corresponding private key.
Phase 3: Using Botnet Malware for Cyber Attacks
When the perpetrators recruit a large number of infected devices under a botnet umbrella, they can use them to execute various types of botnet attacks.
But what kinds of criminal activities do these device-controlling networks engage in? According to the Senate testimony of Joseph Demarest, who served as Chief Operating Officer of the Criminal, Cyber, Response & Surveillance Branch at the FBI:
“Once the botnet is in place, it can be used in distributed denial of service (DDoS) attacks, proxy and spam services, malware distribution, and other organized criminal activity. Botnets can also be used for covert intelligence collection, and terrorists or state-sponsored actors could use a botnet to attack Internet-connected critical infrastructure. And they can be used as weapons in ideology campaigns against their target to instigate fear, intimidation, or public embarrassment.”
These are some common types of botnet attacks that these networks execute:
Distributed Denial of Service (DDoS) Attacks
Being compromised in a DDoS attack through the use of a botnet is one of the top 7 information security threats we’ve talked about previously.
In a DDoS attack, all the bots visit a targeted website and bombard it with numerous requests simultaneously. Due to the unexpected heavy traffic or flux of packet forwarding, the website’s bandwidth starts to get exhausted, and the website becomes slow or stops responding at all.
Successful DDoS attacks disrupt services and make websites unavailable to legitimate users. Some popular botnets for DDoS attacks are Nitol, AgoBot, Cyclone, SDBot, Cutwail, and PhatBot.
Brute Force Attacks
A botnet can execute a successful brute force attack on the website even if the webmaster has enabled limited login attempts feature. In an average brute force attack, an attacker uses a pre-configured list of values (user IDs and passwords) to try to guess login credentials. They’ll use this process to try out different combinations one by one on login pages until they gain access to the system.
Attackers frequently use scripts to automate this process. But websites can easily prevent brute force attacks by limiting the login attempts per IP address. The login pages freeze for any individual IP address after a specified number of failed login attempts.
In botnet brute force attacks, the bots receive a list of websites (or IP addresses) and some pairs of usernames and passwords (generally less than three) from botmaster for each IP address. The bots try to authenticate the given set of credentials on the designated IP. If successful, it reports back to the C&C server. If not, it continues its journey to other IP addresses.
Because the hosts use different IP addresses and try the combinations less than the website’s failed login attempts limits, the target websites can’t detect the brute force attacks executed by botnets.
Data Theft
Another benefit of using a botnet is that it allows cybercriminals to steal sensitive information from their host devices. The trojans installed on host devices for botnet attacks are able to do any or all of the following and send the information back to the botmaster:
- Track all of the users’ activities,
- Records the information stored on the host computers,
- Monitors the users’ online transactions.
- Uses keystroke logging to record users’ keyboard activity and
- Uses form grabbing (aka formjacking) to steal login credentials from online forms.
A botmaster can steal and misuse a variety of information from users to commit financial or identity fraud, including:
- First and last names
- Credit or debit card numbers
- User IDs and passwords
- Email addresses
- Physical addresses
The botnet attacks are also used to steal confidential government, political, or military-related information.
Spreading Malware
Once a device gets infected, its self-propagating malware passes on to other devices to recruit bots under the same network. One example of this is when, the infected device sends malware-laden links, attachments, and phishing emails to the host’s social media/ phonebook contacts and email contact lists, without the user’s knowledge. They also corrupt the other connected devices.
For example, if a laptop becomes infected with a botnet trojan, it spreads the malicious code to every other IoT device you connect to it, such as a printer, Wi-Fi router, USB drive, and even mobile phone and CCTV camera that has been connected with the infected laptop via Bluetooth or USB cable.
Crypto Mining
Here, botnets are programmed to do mining for the selected cryptocurrency. The botmaster uses the cumulative calculative power of thousands of computers simultaneously. Hence, the result can be quicker, and the botmaster can steal more cryptocurrencies. Some popular botnets for crypto mining are Smominru, Adylkuzz, Bondnet, PyCryptoMiner.
Fake Traffic
Infected bots are instructed to visit a website to generate more traffic and click on the advertisements to gain more money from the revenue-per-click (RPC) advertisement model. It is called click-frauds.
5 Real World Botnets Examples
There are hundreds of types of botnets. These are some popular botnets that are used for perpetrators more frequently.
1. Bashlite
Bashlite was first discovered in the year 2014. For the last six years, it has been continuously targeting IoT devices, especially DVRs, cameras, and home routers. It has many variants such as Qbot, Hoaxcalls, Lizkebab, Torlus, and Gafgyt. In April 2020, Hoaxcalls exploited Symantec’s Secure Web Gateway 5.0.2.8. In the year 2016, Bashlite corrupted more than one million IoT devices to execute the DDoS attacks.
2. Mirai
The Mirai botnet, which uses Mirai malware, targets Linux-based servers and IoT devices such as routers, DVRs, and IP cameras. Mirai uses the encrypted channel to communicate with hosts and automatically deletes itself after the malware executes. Hence why it’s difficult for organizations to detect.
Mirai botnet operators primarily use it for DDoS attacks and cryptocurrency mining (cryptomining). It has targeted some of the popular organizations such as GitHub, Twitter, Reddit, Netflix, Airbnb, Krebs on Security, and Rutgers University.
3. GoldBrute
In 2019, GoldBrute botnet had brute-forced about 1.5 million remote desktop protocol (RDP) servers. This Botnet was communicating with its C&C via AES-encrypted WebSocket connections.
4. Smominru
Smominru is a crypto mining botnet that attacks legacy Windows systems. It’s responsible for compromising more than 526,000 Windows hosts and raking in millions of dollars’ worth of cryptocurrency for its operators. As one of its attack methods, botnet operators would use Taylor Swift’s image to hide malware payloads.
5) Dark Nexus
Dark Nexus (also written Dark_nexus) is the latest botnet discovered by Bitdefender in December 2019. It was created using some of the same malicious code that was used in the Mirai and Qbot botnets. It frequently updates itself, making it difficult to predict its behavior.
According to Bitdefender’s report, its core components changed 30 times in three months! It infects IoT devices and uses credential stuffing to execute brute force attacks. The developers of the Dark Nexus are renting the botnet to other cybercriminals for as little as $20 per month!
How to Detect a Botnet
In order to protect your organization (more specifically, your servers and other devices) from botnet attacks, you first need to be able to detect the botnets. There are three main methods of detecting a botnet:
1) Signature-Based Detection
This method utilizes deep packet inspection (DPI) to monitor network traffic. It scrutinizes the inbound packets flows to detect signs of malicious the known patterns (i.e., the signature) of the malware. It can detect the initial incoming intrusion attempts by analyzing the frequency of the traffic and packet flux.
But the signature-based method can only detect the malware patterns which are stored in its botnet database. So, it can’t detect a completely new or unknown type of botnet. It also can’t detect the entire botnet if the members of the same botnet family are using different behavior patterns. Furthermore, it can’t detect the encrypted or compressed malware, either.
2) Flow-Based Detection
This method monitors the network traffic flow by analyzing packets with the same source and destination. It doesn’t inspect each packet, but rather its abstract data from the packet header to monitor the flow size, duration, and mean packet size. It can detect the encrypted and compressed bots, too.
Another advantage of this technique is that it’s not dependent on the malware patterns. It can detect entire botnet families even if the bots are using the different signatures.
3) Detection via Honeypots
Honeypots are intentionally vulnerable systems that companies create to lure and divert attackers away from their genuine servers. Honeypots are designed to have weak security structures and don’t contain any valuable data in them. The goal is to make hackers waste their time and resources on these faux servers instead of attacking the real ones.
When honeypots experience unusual traffic or flux of packet forwarding, the webmaster can get the idea about the botnet attack in its earliest stage. Your organization’s security team gets time to study the attacker’s methods and type of payload before attackers target the main servers.
False Positives Detection Results
Detecting a botnet attack is difficult because the detection tools have to differentiate the botnet traffic from the real web visitors’ traffic and requests sent by vulnerability scanners. Some vulnerability scanners’ behaviors are same as botnets when they’re scanning servers to find bugs. They inspect the resources so fast that some botnet detection tools might consider their actions a potential botnet attack.
In the same way, white hat hackers also inspect the servers and websites to find the vulnerable databases and security loopholes. Some companies even hire such white hat hackers to examine their servers for bugs before the hackers find them. The hacking tools used by security researchers or white-hat hackers generate the same payload patterns as a botnet. That’s why the security software might trigger the false positives.
How to Prevent Botnet Attacks
When we talk about preventing botnet attacks, there are two components involved here.
1) You protect your devices from getting infected by the botnet trojans (so they can’t be used in botnet attacks against others):
- Software updates: Regularly update all the software to the latest version.
- Phishing emails: Beware of phishing emails. Make sure the sender’s email address belongs to the company it claims to. For example, if you get an email claiming to be from Wells Fargo bank, the sender’s email address must contain “@wellsfargo.com.” Know more about phishing emails from this article: Phishing email scams.
- Online downloads: Avoid downloading any attachments or click on any links in the emails if the email is from an unknown sender. Be careful while downloading any software, images, videos, songs, etc. from unknown sites. Scan everything with a trusted anti-virus solution before downloading them.
- Security software: Install robust anti-malware, anti-spyware, and firewalls on your devices.
- Manually checking folders: Regularly Check your C:/Program File and C:/Program Files (x86) folders. If you see any unknown program, make an internet search for it. If it’s not from a trusted publisher, delete it from its original location and also from the recycle bin.
2) If you are a website owner, you need to protect your website from being the target of various types of botnet attacks. Here are a few of the ways you can do that:
- Limit access and login attempts: For brute force attacks, enabling limited login attempts facility might not be enough. Establish a two-factor or multi-factor verification method, in which the users receive a secret code or one-time password (OTP) on their mobiles via SMS or automated voice calls.
- Use firewalls: Deploy a Web Application Firewall (WAF) on your server.
- Implement DDoS protection tools: For reducing the effects of DDoS attacks, use tools to monitor and control the traffic reaching to your website or application. The following are examples of some robust security tools:
- Load balancers (these enable SSL bridging and SSL inspection),
- Content distribution networks (CDNs),
- Network intrusion detection systems (NIDS) and
- Access control lists (ACLs)
- Use software solutions that have ability to prevent botnet attacks. These types of software have ability tomonitor, detect botnet threats and break the interaction between the bots and the C&C server.
Wrapping Up the Topic of “What Is a Botnet and How Does It Work?”
If your device is misused for any botnet attacks, you might also face legal inquiry when the government or security firms investigate the root of the attack. Of course, you get a chance to prove that you’re unaware of such malware insertion, but the legal investigations are going to be lengthy and exhausting. So, it’s advisable to stop the botnet attacks from the get-go by preventing them from infecting your devices in the first place.
Our main takeaways for businesses are the following:
- Teach your employees to be vigilant while surfing online and when using email.
- Regularly update and patch your software, hardware, firmware on all of your software and devices.
- Use strong anti-malware solutions.
- Increase the security of your server by using the aforementioned tools and techniques.













 (7 votes, average: 4.43 out of 5)
(7 votes, average: 4.43 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security