8 Healthcare Cyber Attacks You Should Know About
Bitglass reports that more than 26 million individuals’ protected health information got compromised in 2020 alone! Let’s explore 8 eye-opening cyber attacks in healthcare that you should know about and learn from to protect your healthcare organization & patients
When it comes to mitigating the damage of a healthcare cyber attack, one of the biggest things to remember is to always keep your organization’s sensitive data secure. The healthcare industry involves not only personally identifiable information (PII) of patients and healthcare workers but also protected health information (PHI) as well, which can be a virtual goldmine for attackers.
That’s why healthcare cyber attacks have always been a big concern. Attackers use this information to execute various identity theft-related scams and financial fraud, including:
- Creating fake insurance claims,
- Getting prescription drugs in the victims’ names and selling them at higher rates,
- Demanding extortion money from victims in exchange for not leaking their sensitive health information, and
- Asking ransom from healthcare institutes for unlocking their important data or system.
These are just some of the examples of how dangerous cyber attacks on the healthcare industry can be. We published another article that talks about five of the biggest cyber security issues in healthcare and will continue with that theme here in today’s article. We’ll cover eight data breach and cyber attack situations that show how hackers exploit security vulnerabilities within the healthcare industry to access organizations’ confidential and sensitive data.
1) Personal Data of 24.4 Million Patients Got Exposed in the AMCA Data Breach
The American Medical Collection Agency (AMCA), a company that provided collection and billing services to laboratories, physician groups, and hospitals, found itself in the spotlight due to a massive data breach that was discovered in 2019. Between August 2018 and March 2019, one or more hackers gained unauthorized access to AMCA’s servers, where they accessed patients’ personal, medical and financial information.
The attackers were able to access some or all of the following information about 24.4 million users:
- first and last names,
- dates of birth,
- addresses,
- social security numbers,
- phone numbers,
- healthcare providers’ names,
- balance information, and
- payment card and bank account information.
Some of the biggest victims were AMCA’s clients Quest Diagnostics, whose 11.9 million users’ data got compromised, followed by LabCorp whose 7.7 million patients’ data got leaked in this breach. Some other well-known companies affected by this breach include:
- Optum360,
- CompuNet Clinical Laboratories,
- American Esoteric Laboratories,
- Clinical Pathology Laboratories,
- BioReference,
- Arizona Dermatopathology Inform Diagnostics, and
- West Hills Hospital & Medical Center.
It is one of the biggest healthcare cyber attack events we’ve seen so far.
AMCA reached a settlement with 41 states and was ordered to pay $21 million dollars in fines if they violate the terms of their agreement. The company and its parent company, Retrieval-Masters Creditors Bureau, Inc., filed for bankruptcy as it couldn’t carry on the operations after such large fines and reputation loss.
2) Phishing Attack Leads to Mednax Data Breach, Exposes 1.3 Million Patients’ Records
Mednax, Inc. and Pediatrix Medical Group discovered that their 1,290,670 users’ data is accessed by an unauthorized user via their business email account, hosted on Microsoft Office 365. After further investigation, they discovered that the email account got compromised due to a phishing attack.
The attacker was able to access the following information, which was stored unencrypted and left unprotected:
- Personal identification (first and last names, social security numbers, driver’s licenses and state ID numbers, and dates of birth),
- Financial information (financial account information and billing details), and
- Health insurance and medical information (medical treatment information, insurance claims, health insurance details, and Medicaid/Medicare numbers).
A particularly concerning aspect of this breach is that Mednax didn’t warn the affected victims about the breach for six months after it was detected. Mednax offered a free 12-month credit monitoring service membership to the breach victims. Mednax is right now facing two separate lawsuits, filed in January 2021 and February 2021, for this breach.
What makes matters worse is that this breach could been prevented by implementing authentication mechanisms and encryption to secure their data and accounts. It’s a lesson for companies to keep all the documents encrypted when they are in transit and at rest (i.e., stored on the email client).
3) Healthcare Organizations’ Data Breached via Vendor Ransomware Attack
Blackbaud, a cloud computing software and data intelligence services provider to non-profits, announced that they were the target of a ransomware attack. A ransomware attack is a cyber attack that occurs when cybercriminals use malware to encrypt data and block a company’s access to their critical IT systems and devices. In this type of attack, bad guys demand payment in exchange for returning access to those data and systems.
In May 2020, Blackbaud noticed that some hackers were trying to interrupt the business operations by preventing companies to access their own data and server. Blackbaud recognized the ransomware attack and acted immediately, blocking further access by the hackers to their sensitive IT systems. Unfortunately, before Blackbaud took any steps, the cybercriminals were able to abstract a large piece of data from Blackbaud’s hosting environment. They asked a ransom for destroying that data, which Blackbaud paid to make sure hackers don’t misuse the stolen data.
According to Blackbaud’s announcement, the cybercriminal(s) may have accessed unencrypted information like social security numbers, bank account information, usernames, and/or passwords for select customers.
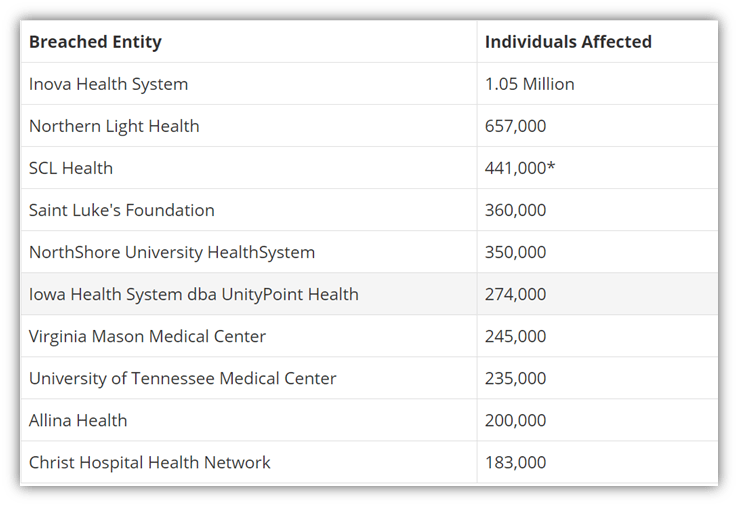
Many of the victims were healthcare institutions and the data breach falls under HIPAA. A total of six million people’s data that belong to Blackbaud’s healthcare clients have been exposed. These are the 10 most-affected health care institutes, according to bankinfosecurity.com.
4) Unpatched Vulnerabilities Expose Records of 3.5 Million FHKC Patients
On Dec. 9, 2020, Jelly Bean Communications Design, where FHKC’s website was hosted, got hacked due to severe security vulnerabilities in the hosting platform and its databases. Jelly Bean Communications failed to apply security patches and fix the bugs, due to which some unauthorized person was able to access and tamper with the following information of 3.5 million individuals:
- full names,
- dates of birth,
- email addresses,
- telephone numbers,
- addresses,
- social security numbers,
- financial information (like wages, alimony, child support, royalties, other income, and tax deductions), and
- secondary insurance information.
The most shocking thing about this healthcare cyber attack was that the vulnerabilities spanned seven years, starting in November 2013 until FHKC was notified in December 2020. In such a long duration, the hackers might have already misused as much data as they wanted.
5) Hackers Accessed 1 Million Patients’ Protected Health Information in Dental Care Alliance’s Breach
Dental Care Alliance is affiliated with 320 dental practices across 20 states. It became a victim of a data breach incident where hackers got unauthorized access to the protected health information of 1,004,304 patients between Sept. 18 and Oct. 13, 2020. According to documentation from DCA’s legal representatives, these breached records include:
- names,
- addresses,
- patients’ account numbers,
- billing and bank account information,
- dentists’ names,
- diagnoses,
- treatment information, and
- health insurance information.
Many of this information falls under the protected health information category under HIPAA. DCA became aware of the breach on Oct. 11, 2020 and fixed the vulnerability within two days. In January 2021, the company was sued for maintaining the data in a reckless manner.
6) Dominion National Hack & Data Breach Go Undetected for 9 Years
Dominion National’s two main business units, Dominion Dental Services and Dominion National Insurance Company, got affected by a data breach that started from August 2010. Some unauthorized person(s) got access to its servers and was successfully able to access information such as
- names
- addresses,
- email addresses,
- dates of birth,
- Social Security numbers,
- bank account and routing numbers,
- taxpayer ID numbers,
- member ID numbers,
- group numbers, and
- subscriber numbers.
Hackers can easily use information like SSNs, bank account numbers, and taxpayer ID numbers for committing financial fraud. A total of 2,964,778 members’ information got breached in this incident. On April 24, 2019, Dominion National was working with a cyber security firm to investigate an “internal alert” when they discovered unauthorized access on its servers dating back to August 2010. They quickly took steps to protect their servers, but the worst part of this healthcare cyber attack and data breach is that it took Dominion National nine years to realize what was happening!
To all the 2.9 million victims, Dominion National offered two years of free membership to its credit monitoring and identity theft protection services.
7) EyeMed Became Victim of Data Breach Due to Unauthorized Email Access
Can you imagine how much damage using a weakly protected email client can do? Ask EyeMed Vision Care LLC! An unauthorized individual gained access to EyeMed Vision’s mailbox starting from June 24, 2020, until the breach was detected and access was terminated on July 1, 2020. The mailbox contained the following information about EyeMed’s customers:
- names,
- addresses,
- social security numbers,
- passport numbers,
- health insurance information
- treatment information,
- diagnosis, and
- prescription information.
According to the U.S. Department of Health and Human Services Office for Civil Rights, the data of more than 1.47 million users got exposed in this breach.
EyeMed took the corrective steps and secured the compromised email account. It also made its employees use complex passwords. It also provided mandatory security awareness training to its users. It also offered two years of free credit monitoring and identity protection services to the breach victims.
8) LabCorp Website Vulnerabilities Leaks 10,000 Documents
LabCorp is one of the largest clinical laboratory networks in the world. In January 2020, at least 10,000 documents were left exposed on LabCorp’s website due to a security vulnerability in a connected back-end system.
Some of the web pages were unprotected with passwords and available on Google. Anyone could access those web pages just by tweaking some serial numbers in the URLs. Those pages contain the following details of the cancer patients:
- Patient names,
- dates of birth,
- social security numbers, and
- lab tests and the results.
Information like patients’ lab tests and diagnoses is called protected health information (PHI) under HIPAA. It is the data collectors’ responsibility to keep this information secure. A set of cybersecurity policies and processes must be followed to mitigate vulnerabilities during the creation/deployment of back-end systems.
It was TechCrunch that notified LabCorp about the breach and LabCorp immediately fixed the bug.
Final Words on Healthcare Cyber Attack Situations
As you can see, most of the healthcare cyber attacks we included here resulted in data breaches and leaks. Healthcare data is the founding stone of many big cyber attacks like phishing attacks, and ransomware attacks.
As we mentioned before, the compromised data can be used for many insurance scams, payment card frauds, and various crimes that involve identity theft. But as an individual, you can do very little to protect your own data if the healthcare institute you are involved with doesn’t have a robust security posture. Luckily, HIPAA has made some strict regulations to guide and force institutions to make them protect your data carefully to avoid grave data breaches and reduce cyber attacks in the healthcare industry.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security