10 Different Types of Cyber Attacks & How To Recognize Them
“There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked” — John Chambers, former CEO and executive chairman at Cisco
No country, organization, government, or individual is immune to cyber-attacks. Cybercriminals sure know how to turn lemons into lemonade despite an ongoing global pandemic, political challenges, and natural calamities. For example, hackers are capitalizing on a bad situation by executing different types of cyber attacks by using the COVID-19 pandemic as a cover.
It’s crucial that you understand what the different types of cyber-attacks are and how to recognize them. In this article, we have explored these ten different types of cyberattacks in detail.
- Phishing Attacks
- DDoS Attacks
- Botnet Attacks
- Brute Force Attacks
- Man-in-the-Middle Attacks
- Man-in-the-Browser Attacks
- Drive-By Attacks
- Malvertising Attacks
- Ransomware Attacks
- Spyware Attacks
10 Types of Cyber Attacks That Cybercriminals Use
1. Phishing Attacks
In phishing attacks, scammers pose as legitimate entities to trick users into taking actions that wind up victimizing them. Phishing can be done via email, text messages (smishing), or phone calls (vishing). Sometimes, scammers use deceptive domain names (for example, wel1sfargo.com, cha5e.com) and make fraudulent websites look legitimate to gain their victims’ trust.
There are several purposes for these types of cyber attacks, including:
- Tricking recipients into sharing their personal/financial details,
- Redirecting targets to spammy websites, or
- Tricking them into downloading malware-infected attachments.
Below is an example of a phishing email that I received:
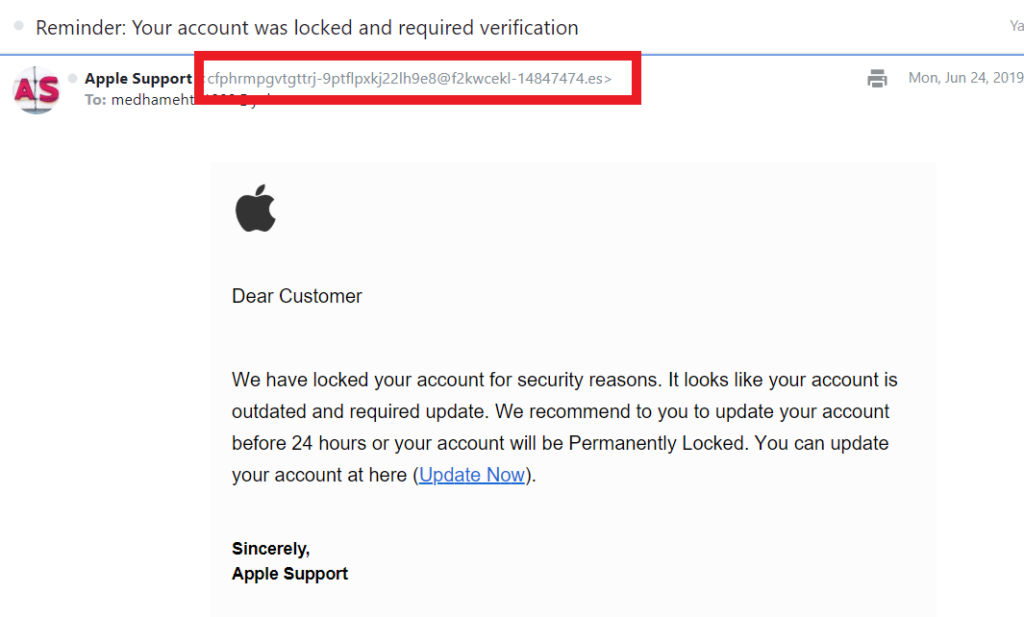
In this email, the attacker impersonates Apple’s support team to try to trick me into clicking on a malicious link. The email is signed by Apple Support and even includes the company’s logo, which may be enough to trick some email recipients.
But there are two key details that scream “DANGER” in neon lights: the sender’s email address and the poorly written message. If the email was legitimately sent by Apple, it would’ve come from an email registered with the apple.com domain — not a fake account like the one highlighted above.
Furthermore, they wouldn’t send an email to “Dear Customer” — they would address you by name. And they certainly wouldn’t send an email that’s riddled with grammatical errors!
Companies That Scammers Like to Impersonate
So, which companies are scammers’ most favorite for impersonating? Check out Checkpoint’s list of top five brands that attackers liked to impersonate in phishing attacks overall in Q1 2020 (not for any specific platform):
| Companies/Brands | % of share in the total phishing attacks in Q1 2020 |
| Apple | 10% |
| Netflix | 9% |
| Yahoo | 6% |
| 6% | |
| PayPal | 5% |
2. DDoS Attacks
DDoS attacks are a serious threat that can affect everyone from small businesses to major enterprises. NetScout Threat Intelligence saw 8.4 million DDoS attacks in 2019 alone.
In a distributed denial of service attack (DDoS attack), attackers bombard a target with numerous requests simultaneously. Targets can be a server, network, service, or website. During a website DDoS attack, for example, the unexpected heavy traffic (or an influx of packet forwarding) overwhelms the target’s server, and the website becomes slow or stops responding.
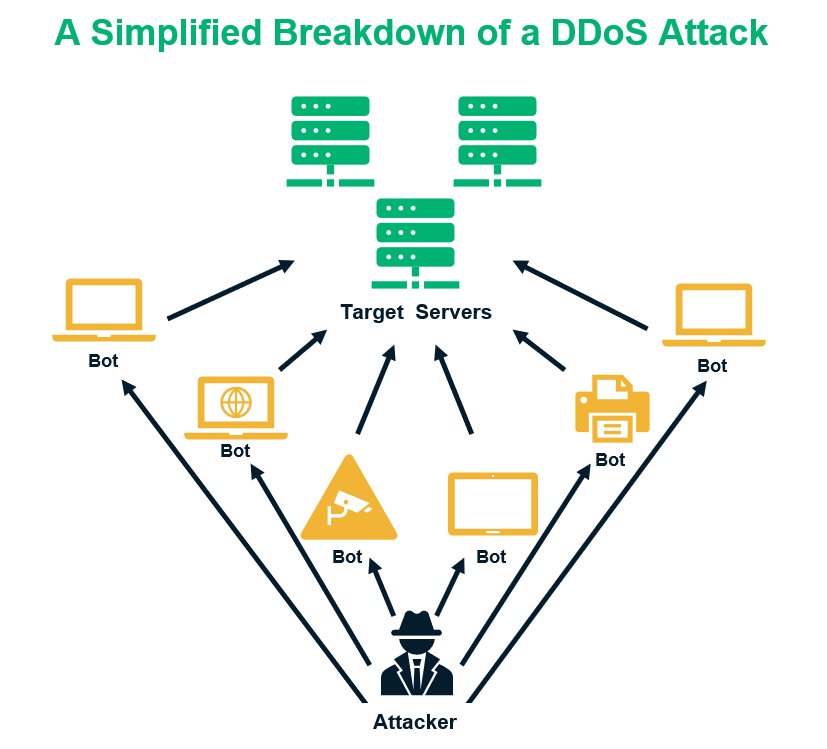
What makes these types of cyber attacks so harmful is that they disrupt the target website’s services, making them unavailable to legitimate users. Attackers use scripts or toolkits that create botnets to generate traffic from numerous sources. That’s why it’s difficult to halt DDoS attacks by blocking any particular user/IP address. In some cases, the attackers may demand a ransom from website owners to stop the attack.
Some common reasons for DDoS attacks include:
- Harming the reputation of a company or website,
- Causing financial losses to the website due to downtime, or
- Taking personal revenge against the site owner.
3. Botnet Attacks
The term “botnet” refers to a network of robots or connected devices. Here, the attackers infect a large number of IoT devices and use their collective power to execute different types of cyber attacks. While a DDoS attack is also one type of botnet attack, it’s not the only one. According to Akamai, other types of botnet attacks include those that involve:
- Validating lists of leaked credentials (credential-stuffing attacks) leading to account takeovers.
- Web application attacks to steal data.
- Providing an attacker with access to a device and its connection to a network.
To create a botnet, attackers insert botnet malware (such as trojans, computer viruses, etc.) into users’ devices via phishing emails and malicious websites. They can also use other corrupted hardware or IoT devices to infect other devices on the same networks.
Once infected with trojan malware, for example, the device takes orders from a command-and-control (C&C) server and executes the cyber attacks as per the botmaster’s instructions. While all of this is happening, the device owners don’t realize that their devices are being used to carry out cyber attacks. Spamhaus Malware Labs saw 71.5% increase of the Botnet C&C in 2019 over the previous year.
Here are a few key things to know about botnets:
- All the devices used in a botnet must be connected with the internet. Attackers can infect PCs, laptops, mobile phones, WI-FI routers, tablets, internet-connected televisions, cable set-top boxes, DVRs, VoIP devices, and IP/CCTV cameras to include them in a botnet.
- Some botnets use PKI to encrypt their internal communications. That means, no one can trace and detect their messages without a corresponding private key. It makes the detection and removal of the botnet quite difficult for security software.
- Botnets serve many purposes and objectives. In addition to the types of cyber attacks we mentioned earlier, botnets are also commonly used for crypto mining, data theft, generating fake web traffic, and spreading malware.
4. Brute Force Attacks
In brute force attacks, attackers try to find the correct login credential to access a system/site/user account. Attackers have a pre-guessed database of login credentials. They insert a script on a target website’s login page that automatically applies usernames and passwords until it finds out the correct combination. The attackers try to break into accounts of users, webmasters, the company’s key employees, or the admin of the website.
There are main two types of brute force attacks.
1. Credential Stuffing: The script automatically inserts the multiple combination of user IDs and passwords in the targeted login fields to find out the valid combination. The attacker generally gets such databases from the leaky databases or data-breach incidents.
2. Password Spraying: Here, the attacker tries out a single password against multiple user accounts. In other words, the attackers “spray” the same password across many user accounts before trying another password.
Sometimes attackers use a brute force attack to exploit URL access vulnerabilities to find the hidden webpages. Let’s consider the following example:
Suppose my hospital shares a personalized link to access my reports online that looks like this: www.myhospital.com/patientreports/July2020/report0235683. I just need this link to see my reports without any credentials. But I realize that “report0235683” is my report/file number. So, if I write “report0235684” on the same URL, I can access the next patient’s reports!
Forced browsing is an example of a type of cyber attack that can lead to a data breach. Attackers use brute force attacks to exploit such security vulnerabilities. They use scripts to generate random URLs to find such hidden and unprotected pages.
Brute force attacks are useful for:
- Stealing the confidential data,
- Putting unwanted advertisements on the website,
- Transferring funds,
- Doing transactions on behalf of victims, and
- Locking down the targets’ systems for ransomware attacks.
Sometimes attackers sell the correct pairs of user IDs and passwords in the dark web to other criminals. They may do this to make a profit or to cause general mischief.
5. Man-in-the-Middle Attacks
When an attacker eavesdrops, interprets and modifies the communication between two endpoints, it’s known as man-in-the-middle (MitM) attack. Both parties think they’re communicating directly with each other and are unaware that someone is infiltrating their connection. Hackers exploit security the vulnerabilities of WI-FI routers and/or website’s security mechanism.
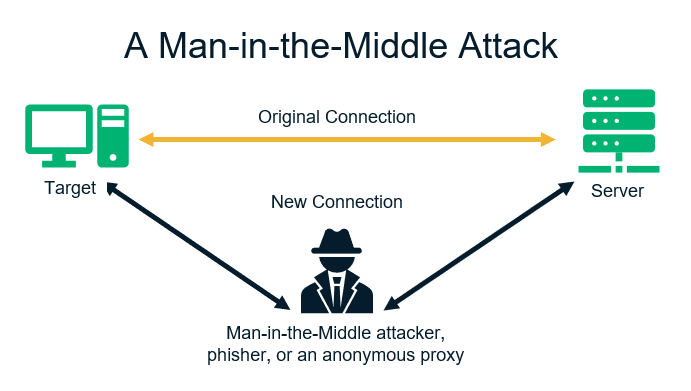
Let’s consider the following MitM example:
Suppose you want to buy a pair of shoes from an ecommerce site. You provide your credit card details, phone number, physical address, and email address to the website during the checkout process. But before your data reaches the intended website’s server, a hacker intercepts the data in transit. As a result, the hacker (i.e. the man in the middle) can read your information and use it to commit financial fraud and identity-theft related crimes.
They can also use it to access any accounts that use the information as part of their security questionnaires. Meanwhile, you and the website you’re connected to remain oblivious to what’s happening until it’s too late.
How to Protect Your Data from a Man-in-the-Middle Attack
The best protection against MitM attacks is encryption technology. Encryption means the plain data is scrambled and converted in the incomprehensible text using a mathematical algorithm. It can’t be read, interpreted, and modified by anyone without a corresponding mathematical key.
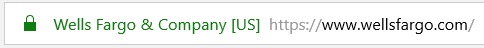
Role of SSL/TLS certificates in MitM Protection: One of the best protections against MitM attacks are SSL/TLS certificates, that use public key infrastructure (PKI) technology to encrypt and decrypt the data transferred between a browser and the server (or between two servers). If you’re a website visitor, check the padlock sign in the address bar before the domain name to make sure the website is secured with an SSL/TLS certificate.
6. Man-in-the-Browser Attacks
Man-in-the-browser (MitB) attacks intercept communications between users and the websites they visit. To do this, an attacker inserts a trojan horse via a browser extension, script, or browser helper object (BHO) into the web browser to corrupt it.
Upon activating the trojan, the attacker can:
- Modify/add/remove the fields on site forms,
- Change the appearance of the website,
- Read and steal any data entered by users on the website, and
- Edit the transactions made by site users.
MitB trojans are so powerful that they can also modify the replies, responses, and confirmation receipts coming from the website’s end. They also can remove the entire transaction from the records before the victim revisits the website!
Here, the users are visiting the legit website, and hence, they don’t suspect anything. Users make the transaction using their original credentials. The website doesn’t have anything to be cautious about, as no authentication step is bypassed. MitB attacks are commonly used against the financial industry, especially for banking websites. But it can take place on any other type of website such as eCommerce sites, utility companies, taxation and accounting firms, government websites, etc.
7. Drive-By Attacks
A drive-by cyber attack occurs when a user visits a malware infected website that downloads and installs malware in the user device. The malware-laden software can exploit the users in a variety of ways such as
- Recoding and monitoring user’s actions
- Corrupting other connected devices to create botnets
- Stealing user’s personal and confidential data
- Sending phishing emails to user’s email contacts
Drive-by software infects devices in one of the following ways:
- Legit software: Attackers infect legitimate software, files, media, etc. with malware.
- Fake software: Attackers replace legitimate software with malicious fakes and use descriptive domain names to trick users into downloading them. For example, cybercriminals are known to do this with fake antivirus software.
- Fake warning messages and update prompts: Cybercriminals can display phony warning messages that make you believe that you need to update your current software or plugins (such as your web browser or Flash). But when you try to update your current software, fraudulent software downloads to your device instead.
- Links: When users visit a website and click on a compromised link, the site may auto-download malicious software onto their devices without their knowledge or consent. For example, this can occur when an attacker puts a malicious script on a video’s “play” button or a song’s “download” button.
- Spammy websites: Some websites are so infectious that drive-by malware downloads automatically whenever a user visits them.
8. Malvertising Attacks
Malvertising is the portmanteau of malware + advertising. Basically, as the name indicates, malvertising consists of online advertisements that distribute malware. In this type of cyber attack, the scammer inserts the malware-loaded advertisements on legitimate websites, often taking advantage of browser vulnerabilities and exploits.
Malvertising comes in many forms, including:
- Pop-up ads,
- Banner and sidebar ads, and
- Phony cancel or exit buttons.
Malvertising is one of the easiest ways for attackers to spread malware because people easily trust the advertisement published on well-reputed websites. Furthermore, website owners are unaware of such advertisements because malvertising doesn’t harm or exploit the website or the server itself.
In these types of cyber attacks, there are two main malvertising delivery method categories:
- Post-click: When users click on a malicious advertisement, it inserts malware on their devices or it redirects them to a malicious website.
- Pre-click: This new and advanced type of malvertising affects users without them having to do anything. Users may find themselves being redirected to other malicious websites even if they haven’t clicked on the advertisements. In other words, the malvertising attacks can take place even without the need for user interactions to trigger them.
The worst part of malvertising is that firewalls and anti-malware software have a difficult time sensing any dangers and alert users because the attackers choose highly reputed websites to insert malware-loaded advertisements.
9. Ransomware Attacks
In these types of cyber attacks, cybercriminals use a type of malware known as ransomware to encrypt their targets’ data and hold it hostage. They demand extortion money from the victims in exchange for access to their encrypted data via a decryption key.
A ransomware attack is, essentially, the data equivalent of kidnapping. The cybercriminals use a trojan that’s designed to eavesdrop, steal, encrypt, and lockdown the data on the victim’s devices. These trojans can lockdown the operating systems, software, databases, and even entire websites, too. Ransomware attacks target both individuals and website owners.
Accordingly Cybersecurity Ventures,
- Global ransomware damage costs are estimated to reach $20 billion by 2021.
- There will be an approximately 57X increase in ransomware cost from 2015 to 2021.
Apart from the cyber attack prevention tips we’ll cover shortly, the best way to protect your organization against ransomware attacks is to regularly update your backups and them via a secure third-party cloud platform. A backup tool like CodeGuard:
- Creates automatic backups of your data,
- Scans it for malware, and
- Stores the clean copy on the cloud platform.
This makes it so that you don’t have to choose between paying a ransom and losing your data. Instead, you can wipe your systems and replace your data with the most current backup.
10. Spyware Attacks
A spyware attack is a type of cyber attack that involves the use of malware to monitor a target’s actions and activities. In spyware attacks, a cybercriminal inserts different types of malware (such as computer viruses, trojan horses, computer worms, etc.) inside the user’s devices. These nasty little tools allow criminals to:
- Monitor users’ activities and browsing behaviors,
- Record data typed on keyboards (this process is also known as keylogging),
- Take screenshots of devices’ screens,
- Steal and transfer files, contact lists, media files, etc. to the attackers.
The attackers use the data they steal to execute financial fraud or crimes associated with identity theft. They can also use the data to:
- Create political unrest,
- Access confidential professional information,
- Steal research or proprietary data, and
- Carry out other agendas.
Sometimes, spyware and ransomware attacks are executed together. First, the attacker steals the victim’s personal data through spyware. Next, they threaten to publish the victim’s private or sensitive if they don’t pay the ransom.
Final Thoughts on the Different Types of Cyber Attacks We’ve Discussed
It seems like every year is another record-breaking year when it comes to the number of cyber attacks that take place. Now that you’ve read how different types of cyber attacks are prevailing in the industry, you’re likely wondering what can you do to prevent cyber attacks in the first place.
In general, follow these basic tips to prevent different types of cyber attacks:
- Be vigilant while engaging with links and attachments in questionable emails and websites. Be sure to read the email header information and hover over link text to verify the real links.
- Never download anything from the internet before scanning it with a reliable antivirus tool.
- Keep your software current and operating systems patched and up to date.
- Never share anything on websites that use the insecure HTTP protocol (i.e., websites that aren’t protected by SSL/TLS certificates).
- Manually check your download folder, C:/Program File, C:/Program Files (x86), and C:/Windows/Temp folders to identify any unwanted/unknown programs, files, and software.
- Use robust antivirus and anti-malware solutions. Network monitoring and endpoint security solutions are important, too.
- Always maintain multiple copies of your current data backups.
- If you’re a small business owner, follow the tips provided in this article to protect your business from different types of cyber attacks.
We hope this article has helped you to understand different types of cyber attacks and how to recognize and mitigate them.














 (29 votes, average: 4.38 out of 5)
(29 votes, average: 4.38 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security