Phishing Statistics 2020: 15 Phishing Stats to Help You Avoid Getting Reeled In
Research indicates that nearly 30% of all phishing messages are opened by targeted users. Here’s what to know about this type of cyberattack & the top phishing stats in 2020
If you’ve ever had burning questions like “phishing attacks are what percentage of cyber attacks?” then you’re in luck. We get questions like that all of the time from readers and customers. So, we figured, heck, why not just write an article on the topic and provide a bunch of other phishing statistics? We’ll be your analgesic cream for that burning itch.
But before we jump straight into the numbers, let’s take just a moment for a quick refresher about what phishing is. Then we’ll give you those fun (and perhaps disturbing) phishing stats.
What is Phishing and What Are the Most Common Types of Phishing?
Phishing is a type of cyberattack that occurs when a cybercriminal uses social engineering to get a victim to do something. The goal may be to get them to provide their login credentials via a malicious website form, or it could be to get them to send funds via a wire transfer (as is the case in CEO fraud schemes).
In reality, phishing attacks come in many different forms — although they all intend to achieve virtually the same goal (just through different means). Some examples of different types of phishing attacks include (but are not limited to):
- business email compromise (BEC),
- spear phishing,
- vishing,
- smishing,
- HTTPS phishing, and
- whaling.
So, now that we have that out of the way, let’s explore the most up to date phishing statistics.
15 Phishing Statistics: How Phishing Retains Its Title as the Top Attack Vector
1. Phishing is the No. 1 Cause of Data Breaches
Shocked. Not surprised. However you individually feel about our first phishing statistic, it doesn’t change the fact that Verizon listed phishing at the leading cause of data breaches in its 2019 Data Breach Investigations Report (DBIR). We’re curious to see where phishing stands in their 2020 DBIR, but we’ll still have to wait a few more months (once they publish their next report) to find out that info.
2. 33% of Consumers Will Abandon a Business After a Security Breach
Considering that phishing is the leading cause of data breaches, it makes this statistic even more meaningful. Avanan, a cyber security platform, reports that one in three consumers halt their business with an affected company after a data breach is announced.
3. BEC/EAC Is a $26+ Billion Scam Affecting Victims Globally
The FBI’s Internet Crime Complaint Center (IC3) reports that between June 2016 and July 2019, there were $166,349 business email compromise/email account compromise (BEC/EAC) incidents globally that were reported to the IC3. More than $26,201,775,589 in domestic and international dollar losses were reported by victims in the U.S. and 177 countries.
4. Fraudulent Transfers Are Sent to More Than 140 Countries
The IC3 reports that BEC/EAC fraudulent transfers were sent to at least 140 countries during that time. The primary destinations of fraudulent fund transfers are China and Hong Kong. However, the FBI has observed an increase in these types of transfers to recipients in the U.S., Mexico, and Turkey.
5. 68% of All Phishing Websites Use HTTPS Protocol
Data from the 3rd Quarter 2019 Phishing Activity Trends Report from the Anti-Phishing Working Group (APWG) indicates that more than two-thirds of all phishing websites studied used SSL protection. This was an increase over the 54% reported in the previous quarter. According to the report, which involved tracking data from PhishLabs: “This was the highest percentage since tracking began in early 2015, and is a clear indicator that users can’t rely on SSL alone to understand whether a site is safe or not.”
6. SaaS and Webmail Users (33%) Continue to Be Biggest Phishing Targets
A list of phishing statistics without data from the APWG wouldn’t be complete. Their Q3 2019 Phishing Activity Trends Report data indicates that founding APWG member MarkMonitor observed Software-as-a-Service (SaaS) and webmail sites were the most targeted by phishing campaigns and attacks that quarter, representing 33% of the most-targeted industry sectors. This differs from attacks against other sectors such as healthcare, government, energy, and gaming, which were negligible during that period.
7. Malicious or Criminal Attacks Caused More Than Half of Data Breaches in the Last Year
Of the 507 organizations that reported experiencing a breach in IBM’s 2019 Cost of a Data Breach report, “Fifty-one percent of incidents involved a malicious or criminal attack,” which the report indicates would include “malware infections, criminal insiders, phishing/social engineering and SQL injection.” The other two categories of causes were system glitches (25%) and human error (24%).
8. 78% of Known Cyber-Espionage Incidents Involved Phishing
Data from Verizon’s 2019 BDIR indicates that phishing plays a major role in cyber espionage. In fact, more than three-quarters of known cyber-espionage incidents during the studied period involved phishing, and 87% of the incidents involved “the installation and use of backdoors and/or C2 malware.”
9. 90+% of Successful Phishing Attacks Are Done Through Phishing
Research from KnowBe4 indicates that more than 90% of successful data breaches and hacks spawn from phishing attacks.
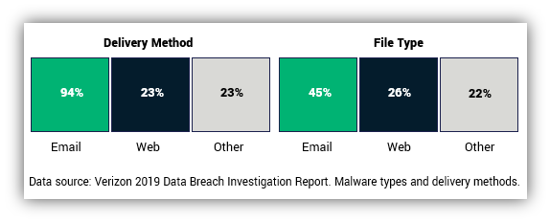
10. Nearly One-Third of Phishing Emails Get Past Default Security Mechanisms
Regardless of what any company’s marketing arm claims, there’s no way to prevent every single spam or malicious emails from making it to your inbox. Avanan reports that 30% of phishing email messages typically slip past default security methods.
11. Users Reported 9.2 Million Suspicious Emails in 2019
ProofPoint’s 2020 State of the Phish report data indicates that there was a 67% increase over the previous year in users reporting suspicious emails via their PhishAlarm® email reporting tool. The median amount of time from when such an email was received and when it was reported was one hour.
12. 65% of U.S. Organizations Measure Phishing Costs in Terms of Downtime
Downtime hours for end users is the greatest unit of measure for phishing costs for U.S. organizations, according to ProofPoint’s 2020 State of the Phish report. This number differs from the global average of 52%.
13. Phishing Resulted in Data Loss for 59% of Surveyed Japanese Organizations
Phishing attacks are a major concern for Japanese organizations. ProofPoint’s 2020 State of the Phish report indicates that “59% of Japanese organizations suffered data loss following a phishing attack” and that “45% suffered financial loss.”
14. Nearly 83% of Spam Emails Are Less Than 2KB in Size
Spam emails don’t have to be big to have a major impact. Kaspersky reports on its SecureList.com website that in Q3 2019, 82.93% of spam emails they recorded were 0-2KB in size. This is a slight decrease (4.33 percentage points) from the previous quarter.
15. More than 20% of Spam Emails Originated in China in Q3 2019
According to Kaspersky’s SecureList website data, China led the way in terms of people there sending the largest percentage of spam emails. The company reports that 20.42% of spam messages originated from China, 13.37% from the United States, and $5.6% from Russia.
Final Thoughts on Phishing Statistics
While there are many more phishing statistics out there, we thought that these would be some of the most insightful and would help to paint the most clear image of phishing from a business perspective. Phishing affects everyone — from the victims that attackers target with their phishing campaigns to the businesses and individuals that they choose to impersonate.
Are there any additional phishing statistics you’d like to share? Be sure to share them in the comments below.
























 (16 votes, average: 4.50 out of 5)
(16 votes, average: 4.50 out of 5)






No comments