Port 443 — Everything You Need to Know About HTTPS 443
Did you know that more than 95% of requests over Chrome are served using an HTTPS connection via port 443? Here’s what else you should know about port 443
In light of ever-increasing cyber-attacks, providing a safe browsing experience has emerged as a priority for website owners, businesses, and Google alike. With the support of almost all of the other major browsers, the tech giant flags websites without an SSL/TLS certificate installed as “Not Secure.” But what can you do to remove this security warning (or to prevent it from ever appearing on your website in the first place)? Use a tool that enables you to connect using a secure protocol via port 443.
Installing an SSL certificate on the web server that hosts the site you’re trying to access will eliminate this insecure connection warning message. An SSL/TLS certificate lays down an encrypted, secure communication channel between the client browser and the server. This means that the next time you visit the site, the connection will be established over HTTPS using port 443.
What Is Port 443?
A port is a virtual numbered address that’s used as a communication endpoint by transport layer protocols like UDP (user diagram protocol) or TCP (transmission control protocol). Network ports direct traffic to the right places — i.e., they help the devices involved identify which service is being requested.
For instance, the port that’s responsible for handling all unencrypted HTTP web traffic is port 80. When we use a TLS certificate, the communication channel between the browser and the server gets encrypted to protect all sensitive data exchanges.
All such secure transfers are done using port 443, the standard port for HTTPS traffic. However, HTTPS port 443 also supports sites to be available over HTTP connections. If the site uses HTTPS but is unavailable over port 443 for any reason, port 80 will step in to load the HTTPS-enabled website.
How Does HTTPS Work?
So, what happens behind the scenes, and how does HTTPS really work? Let’s find out!
When your client browser sends a request to a website over a secure communication link, any exchange that occurs — for example, your account credentials (if you’re attempting to login to the site) — stays encrypted. This means that it can’t be read by an attacker on the network. This happens because the original data is passed through an encryption algorithm that generates a ciphertext, which is then sent to the server.
Even if the traffic gets intercepted, the attacker is left with garbled data that can only be converted to a readable form with the corresponding decryption key. Here’s a visual representation of how this process works:
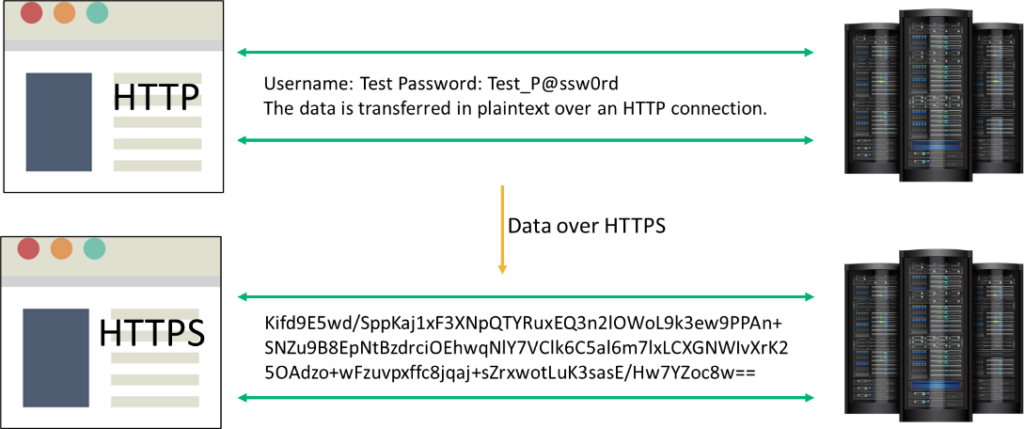
HTTP over an SSL/TLS connection makes use of public key encryption (where there are two keys — public and private) to distribute a shared symmetric key, which is then used for bulk transmission. A TLS connection typically uses HTTPS port 443. Alternatively, the client may also send a request like STARTTLS to upgrade from an unencrypted connection to an encrypted one.
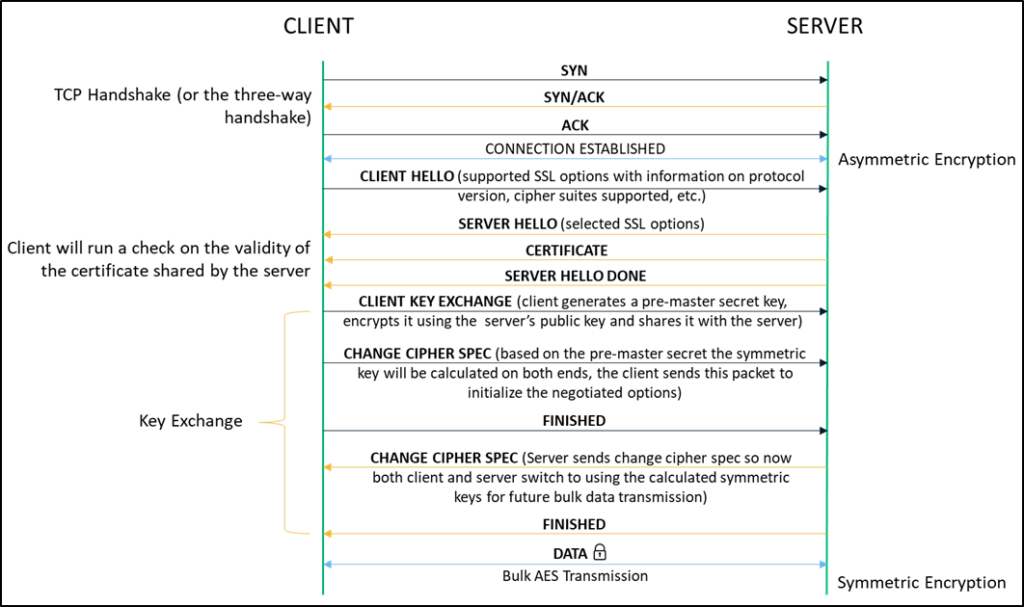
Before a connection can be established, the browser and the server need to decide on the connection parameters that can be deployed during communication. They arrive at an agreement by performing an SSL/TLS handshake:
- The process begins with the exchange of hello messages between the client browser and the web server.
- Once the protocol negotiation commences, encryption standards supported by the two parties are communicated, and the server shares its certificate.
- The client now holds the public key of the server, obtained from this certificate. It verifies the validity of the server cert before using the public key to generate a pre-master secret key. Next, the pre-master secret is encrypted with the public key and shared with the server.
- Based on the value of the pre-master secret key, both sides independently compute the symmetric key.
- Both sides send a change cipher spec message indicating they’ve calculated the symmetric key, and the bulk data transmission will make use of symmetric encryption.
What Does HTTPS Port 443 Protect and Why Do We Need It?
HTTPS is an application layer protocol in the four-layer TCP/IP model and in the seven-layer open system interconnection model, or what’s known as the OSI model for short. (Don’t worry, we won’t get sucked into a mind-numbing monologue about how TCP/IP and OSI models work.) In a nutshell, what this means is that it ensures that your ISP (or anybody else on the network) can’t read or tamper with the conversation that takes place between your browser and the server.
Basically, the takeaway is that it encrypts those exchanges, protecting all sensitive transactions and granting a level of privacy.
When a website uses an SSL/TLS certificate, a lock appears next to the URL in the address bar that indicates it’s secure. However, this secure lock can often be misleading because while the communication channel is encrypted, there’s no guarantee that an attacker doesn’t control the site you’re connecting to. Besides, several other security vulnerabilities could lead to a data compromise, and only using SSL/TLS certificates can’t protect your server or computer against them. For example, your computer can still download malware due to drive-by download attacks, or the data you enter on a site can be extracted due to an injection attack against the website.
To avoid making any assumptions about what HTTPS can and cannot protect, it’s important to note that the security benefits don’t travel down the layers. What we mean by this is that while HTTPS encrypts application layer data, and though that stays protected, additional information added at the network or transport layer (such as duration of the connection, etc.) may be revealed. When your browser makes an HTTPS connection, a TCP request is sent via port 443. However, once the connection is established, although the application layer data (the message exchanged between the client and the server) is encrypted, that doesn’t protect users against fingerprinting attacks.
Apart from the actual conversation, certain types of information can be read by an attacker, including:
- The user’s IP address and location,
- The size of the message,
- The website to which the connection is made, and
- The frequency of these connections.
One final important note: Although it’s a common misconception, using HTTPS port 443 doesn’t provide an anonymous browsing experience.
In Summary on the Topic of HTTPS Port 443
Whether you’re a website owner or a site visitor, browsing over an unencrypted connection where your data travels in plaintext and can be read by anyone eavesdropping on the network poses a serious threat to security. Though there are limitations to the security benefits provided by an SSL/TLS connection over HTTPS port 443, it’s a definitive step towards surfing the internet more safely.
There are several reputable certificate authorities (CA) who can issue digital certificates depending on your specific requirements and the number of domains you want to secure. Additionally, another consequence of Google’s initiative for a completely encrypted web is the way that websites are ranked. Since 2014, Google has been using HTTPS as a ranking signal for its search algorithms. And with a majority of netizens avoiding unsecure websites, it means that SSL certificates have become a must.














 (85 votes, average: 4.38 out of 5)
(85 votes, average: 4.38 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security