What Is PKI? A Layman’s Guide to Public Key Infrastructure
If you’ve wondered what public key infrastructure (PKI) is, you’ve come to the right place. It’s something that protects our money, privacy and so much more. The crazy part, most people don’t even know what it is…
So, you’re finally ready to ask. You’ve put this off, we know. We understand, it’s a big topic. It’s okay though. We’ll walk you through this one. And before you know it, you’ll be chatting with your friends at work and dropping knowledge when someone asks, “What is PKI?”
Getting Straight to the Point: What Is PKI?
Before we dive into a deeper, more layered explanation, here is a quick definition of PKI: Public key infrastructure is something that establishes and manages public key encryption and digital signature services. For public key encryption to work, digital keys and certificates need to be created, stored, distributed, managed, revoked, used and so on. PKI allows for encryption to do all of these things with software, hardware, protocols, policies, processes and services.
If you want a quick but still more detailed explanation, check out our article on PKI basics.
If you want a deeper, more layered explanation of PKI, keep on reading!
Answering “What is Public Key Infrastructure?” — A 100,000-Foot Perspective
Like we said, we get it, this topic is tough. Just so we don’t undermine the complexity of PKI, let’s start with a riddle. What’s something that no can see but helps other’s see what can’t be seen? You guessed it, PKI!
In a way, that’s quite the accurate description. Think of public key infrastructure as the almighty helping hand. The helping hand is there for anything and everything. PKI is no different. It’s there no matter what is asked of it. PKI is the helping hand that makes online banking, paying taxes online, shopping on Amazon and so much more safe and secure! It’s there to help in anyway it can!
It’s a facilitator of sorts.
Now, maybe that didn’t help entirely (maybe we’re not as helpful as PKI), but let’s bring you down from 100,000 feet to 50,000 feet. We can do this with a little backstory about encryption, keys, and Julius Caesar.
The PKI Flashback: The PKI Story Starts Almost 4,000 Years Ago
Yes, we’re doing a flashback like Marty McFly. Or was it a flash forward? Hard to say when he’s going BACK to the future… I digress.
To truly understand PKI, you need to know some backstory. There have been signs of encryption dating all the way back to 1900 BC. Maybe the most famous example of encryption history is that of Caesar’s Cipher around 40-50 BC. Caesar used a sort of shift cipher that scrambled letters around by jumping ahead a fixed number of places in the alphabet. This proved to be an excellent tactic to protect his messages from enemies who have intercepted them.
This brings us to conventional (aka symmetric) encryption. Sticking with what Caesar did — basically, he knew what the key was to decode his messages, which means the person who was receiving the message needed to know what the key was as well. That’s how conventional encryption works.
Here’s another example of conventional encryption. Let’s say Daffy Duck and Yosemite Sam didn’t want Bugs Bunny to know they’re working together. How could they pass secret messages without letting Bugs find out? There would need to be a way to encrypt messages and a key to decrypt them, but the problem Daffy and Yosemite would run into is that they’d need to a way to pass the key. They can’t meet in person because that would ruin their plan of secrecy. They also couldn’t pass the key with the message because that would also make this process utterly useless.
Looks like Bugs got them again. The problem Daffy and Yosemite face is figuring out how two people in different places can agree on an encryption key to exchange encrypted messages. Now, if Daffy and Yosemite had PKI at their disposal, then they just might be able to pull one off this time.
To Answer, “What is PKI?” You Need to Understand Public Key Encryption
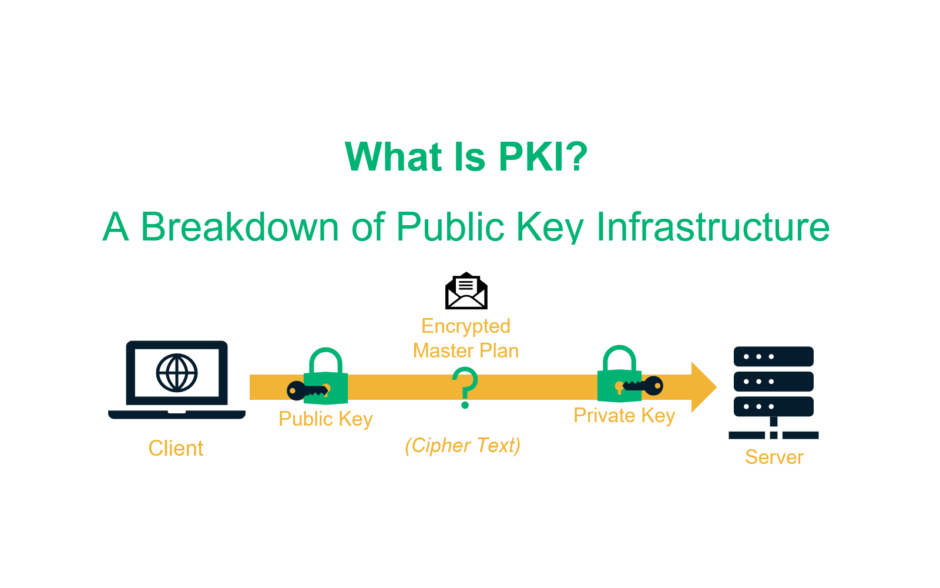
As opposed to conventional encryption, which uses one key, PKI enables what we call public key encryption (aka asymmetric encryption) to be able to use two keys. One key encrypts while the other decrypts. The two keys used are the public key and the private key. The keys are aptly named as one key is available to the public and the other one is private.
Using the public key encryption method, Daffy could encrypt his message using Yosemite’s public key. That way, only the person with the private key (Yosemite) could decrypt the message. Even if it was intercepted, Bugs couldn’t get anything valuable out of the message because the ciphertext would look like gibberish without the decryption key.
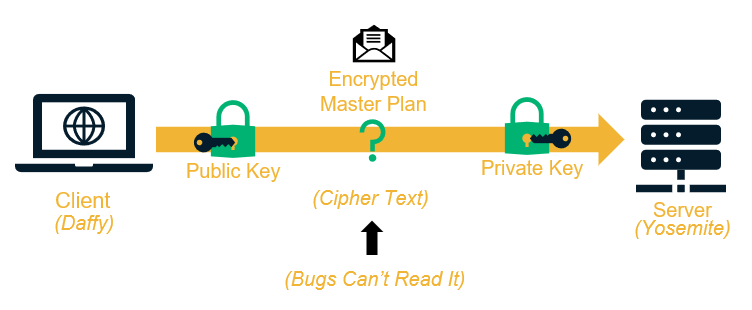
An impressive method for sure. Maybe the only thing more impressive is that I somehow turned Bugs Bunny into a hacker.
Now take this concept and apply it to two computers trying to communicate securely. With PKI, these two computers can basically speak to each other, agree, share keys and ultimately decrypt the message that was in transit.
So, I think that covers PKI from the 50,000-foot perspective. We’re going to bring you to about 10,000 feet for the rest of the way through, which will leave you with a thorough understanding of PKI, and ultimately answer the question “what is PKI?”
Who Are the Key Players Involved in PKI?
There are three main elements to PKI:
- The key pair, which we just covered is one of them.
- Certificate authorities (CAs) are another. CAs are trusted third-party bodies that develop and manage digital certificates. Trusted is the key word there as CAs hold the prestigious honor of being trusted to issue certificates by meeting ultra-strict criteria established by the CA/Browser Forum (CA/B Forum), an independent group largely made up of representatives from the world’s largest browsers.
- Digital certificates, which are created by the CAs, are the final element. A digital certificate acts as the passports of PKI. Just as you need a passport to travel internationally, you need a digital certificate to travel through PKI. That’s because a PKI digital certificate carries documentation that details information about the key and its owner. It also comes with a signature from the CA, similar to a passport coming with a signoff from the traveler’s government.
These three elements (or “players,” as the title says) make up the inner workings of this infrastructure.
Five Ways That PKI Helps Us in Our Everyday Lives
As we said in the opener, PKI is something that protects our money, privacy, and so much more. It touches our lives nearly every day. So, how does this invisible infrastructure help so many people? It facilitates and supports safety and security in nearly every facet of digital communications.
Here are five specific areas PKI does this:
Web Security
In today’s digital world, it’s vital we are able to interact with websites without having our interactions recorded or intercepted. PKI allows for HTTPS to happen. The secure HTTPS protocol allows for browsers and web servers (aka websites) to safely and securely communicate. To have an HTTPS website, you need an SSL/TLS certificate.
By installing an SSL certificate on your website, you receive the aforementioned public and private key pair. The private key is securely housed in the web server, so that a user’s browser can identity a website (server) as legitimate. This allows for users to safely shop, submit personal information, and pay while browsing websites.
Email Security
Email is another key area that PKI touches. PKI provides the framework for emails to safely travel from one person to another. This process is known as secure/multipurpose internet mail extension (S/MIME). S/MIME certificates are used to encrypt the email message and digitally sign it, so that the sender and their message can be authenticated. This also helps to prevent bad guys from tampering with emails.
Secure Messaging
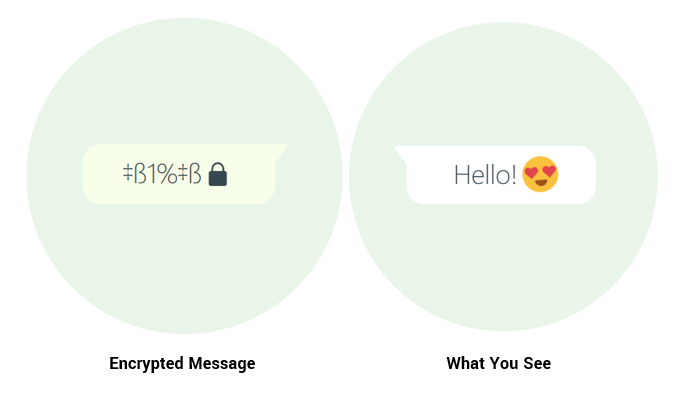
Imagine getting on WhatsApp and feeling like you can’t send a message to your friends without someone intercepting and reading it. It’s a scary thought. PKI makes it more secure to use messaging services like WhatsApp with the use of encryption.
Code/App Signing
So, PKI covers secure website communications, email and messaging. What else does it cover? Well, let’s say you download an app or software, and once you download it, it asks for you to make an account, put your credit card number on there to buy additional services and for more private information. But how can you trust this? By software developers and publishers using code signing certificates, that’s how!
These certificates ensure the developer/publisher of the file is who they say they are. PKI enables the code signing certificates to authenticate who the publisher is using public key encryption. It also helps to prevent tampering once the software or application is signed.
Document Signing
In today’s digital world, it would be completely inefficient to physically sign every document that requires you to do so. That is what brings us to document signing. PKI enables users to electronically sign documents with the ability to prove to the receiver that the signed document is coming from a legitimate source. This happens with document signing certificates. And PKI isn’t just offering a secure way to digitally sign documents, it’s also saving you from a lot of hand cramps.
A Final Answer to the Question “What is PKI?”
From Bugs Bunny to Marty McFly and Julius Caesar to HTTPS, we’ve reached the end of our story. PKI is so much more than a software or product. PKI is a fully functional everything that allows for all of us to safely and securely operate in the digital world. With encryption and authentication, it governs this world allowing messages to travel, documents and downloads to be trusted and above all us, PKI allows us to enjoy the beautiful world behind our computer screen.
For something so largely unknown, it’s a pretty remarkable thing. So, next time someone asks, “what is PKI,” make sure you don’t skip a single “key” detail.























 (17 votes, average: 4.06 out of 5)
(17 votes, average: 4.06 out of 5)






No comments