The Top 7 Information Security Threats & How to Mitigate Them
Cybersecurity Ventures predicts cybercrime damages will hit $6 trillion annually by 2021 — we’ll cover the best ways you can stop your organization from becoming the next statistic
At one point or another, virtually everyone has had that stomach-churning fear that they’ve been hacked. And, hopefully, it’s nothing more than a passing anxious thought. But considering the lurking information security threats that are waiting for us to slip up and make a mistake, it’s a mighty miracle if you’ve managed to avoid being touched by even just one cyber-attack or data breach.
Information security breaches are costly in many ways. Apart from the obvious financial and legal implications of security breaches, there’s also the reputational damage to consider, as it weakens the trust customers have in your brand.
While many different security threats plague us on a daily basis, we’ll discuss seven of the most common in no particular order and see what they are and how to mitigate them. Without any further delay, let’s get started!
How to Identify and Protect Your Organization Against Information Security Threats
Information security threats exist both outside and inside your organization. And considering that damages of cybercrime are estimated to cost businesses $6 trillion annually by 2021, this serves to underscore why it’s crucial to harden your defenses against all avenues of attack.
Here are seven ways you can make yourself a more challenging target for cybercriminals:
1. Build Your Defenses Against Malware Attacks
Malware is any piece of software or code that’s designed to perform malicious operations on a system or a network. This type of security threat can be classified into various categories based upon the distinctive characteristics or attributes of each type.
Different types of malware include:
- Viruses and worms are programs that self-replicate and spread across the network,
- Trojans are malicious programs that appear to be legitimate, and
- Spyware are programs that monitor and collect information on user activity without their knowledge
Proposed Method(s) for Mitigating These Types of Information Security Threats:
There isn’t a single best solution that can be implemented to prevent malware-based attacks although anti-malware solutions do a decent enough job. Here’s a list of some other pointers that might come in handy:
- Consider using a well-reputed endpoint security solution (these usually include antivirus, antimalware, etc.) across all network endpoint devices, especially since malware has a tendency to infect the entire network.
- When it comes to information security threats, the importance of regularly installing software updates and patches cannot be stressed enough.
- Train your staff to help them differentiate between legitimate and suspicious emails or websites. Regular and mandatory cyber awareness workshops can educate and train employees to avoid security risks and raise their knowledge around online threats.
2. Safeguard Against Eavesdroppers Listening in via MITM Attacks
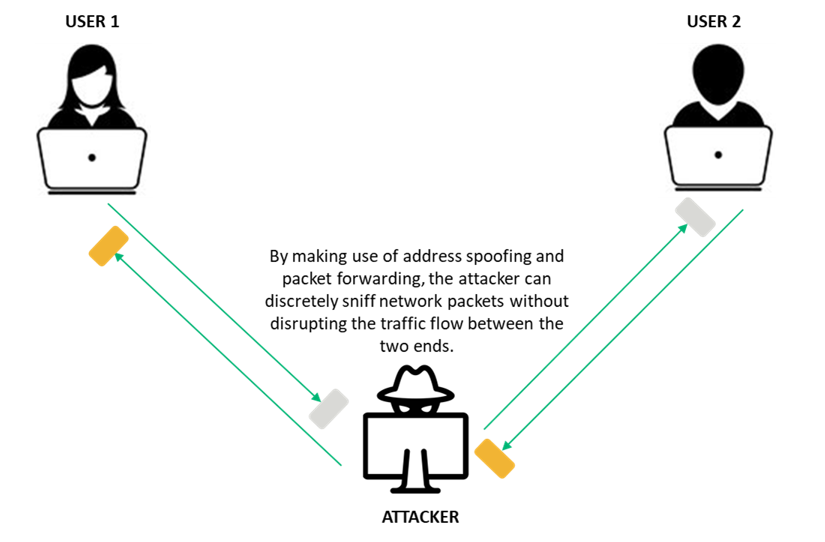
A man-in-the-middle (MITM) attack is one of those information security threats that occurs when a malicious agent intercepts the communication between two parties (such as two computers, or a computer and a network appliance) to eavesdrop or tamper with the data. The attacker spoofs their address to make it appear as though it is the intended recipient.
By making use of packet forwarding and tools like Ettercap, the attacker can discretely sniff network packets without disrupting the traffic flow between the two ends. Consider the following example:
Proposed Method(s) for Mitigating These Types of Information Security Threats:
There are several ways to prevent these attacks. The list below highlights a few methods that you can employ to keep such information security threats at bay.
- While on the internet, use HTTPS — i.e., connect over encrypted channels wherever possible. Encryption keeps your data scrambled in an unreadable form, and even in the event of a successful MITM attack, the encrypted data is no good to an attacker without a decryption key.
- Eliminate insecure redirects with HTTP Strict Transport Security that allows only HTTPS connections. Sometimes attackers can hijack a connection using tools like sslstrip if the request was first made to an unsecured HTTP site before it gets redirected to secure HTTPS. Using HTTP Strict Transport Security (HSTS) removes this ambiguity and ensures that only HTTPS connections are established between the client and the server.
- Avoid clicking on links, downloading attachments or software from questionable sources. Phishing emails and malware can also be used to further a man-in-the-middle (MitM) attack. Avoid clicking on any links in emails and carefully consider before downloading any attachments, especially if an email looks suspicious and you haven’t verified the message header. Additionally, before downloading any software onto your system, ensure they have been signed using a code signing certificate. It’s a way to ascertain whether the program is legitimate and hasn’t been modified by an attacker.
- Use anti-ARP spoofing tools to avoid spoofing attacks and always surf via a secure, trusted connection. Deploying anti-ARP spoofing solutions or adding only static ARP entries into the cache in case of smaller networks can help mitigate the risk of spoofing. Additionally, if you must connect over an insecure connection like a public Wi-Fi, be sure to use a virtual private network (VPN).
3. Protect Yourself From Being an Unsuspecting Victim of a Drive-By Download Attack
Imagine a scenario where you’re idly surfing the web on a lazy Sunday afternoon and, without clicking on any links or downloading any software, you manage to infect your phone or system with malware quite unintentionally.
Think it’s not possible? Unfortunately, it is. Drive-by downloads exploit vulnerabilities in the operating system, browsers, or apps, which is why installing patches and updates are so essential. They can spread malware by means of malicious code distributed through compromised websites.
Proposed Method(s) for Mitigating These Types of Information Security Threats:
While it can be tricky to guard against security threats that aren’t triggered by an action from the victim, and when well-crafted can pass off unnoticed, there are certain measures we can take to prevent these types of information security threats from being successful:
- Keep your systems and programs running on them updated with the latest patch to cover any security loopholes through which malicious drive-by-download code could slip in.
- Using antivirus and antimalware solutions to scan the system regularly is highly recommended. Disabling JavaScript within PDF document settings is also a precautionary measure.
- Though reputed websites aren’t immune to compromise, the likelihood of drive-by attacks being propagated through suspicious sites is far higher, so avoid visiting pages you don’t trust. Installing web filtering solutions like OpenDNS or Websense Web Filter can block websites with suspected harmful content. However, upon infection, a full OS reinstall is recommended.
4. Teach Your Employees to Not Take the Bait in Phishing Attacks
Phishing is a type of social engineering attack that increased by 667% in March 2020 alone. Most of us have received suspicious emails urging us to click on a link or open an attachment. Social engineering attacks prey on the gullibility of humans by using adept social skills to gain their confidence to get them to reveal sensitive information.
Some types of sensitive data include:
- Personally identifiable information (PII),
- Financial or health records,
- Proprietary information, or
- Organizational information that can be used either directly or indirectly to compromise security and gain entry into the corporate network.
If they’re unable to get the necessary information from one source, they reach out to multiple people, assembling and building upon the intelligence they have acquired to create a credible and convincing storyline.
Proposed Method(s) for Mitigating These Types of Information Security Threats:
While you can place a spam filter to block suspicious emails, social engineering attacks are really about getting people to talk or take some type of action. The best thing we can do is to stay alert about information security threats and ensure our staff undergoes regular cyber awareness training to always keep security on their radar.
- Prevent yourself from getting manipulated into disclosing any private info. Stay cautious, especially when you’re online. Be diligent when it comes to the details you post or share online about the privacy settings on your social media account.
- Be wary of unsolicited phone calls, or unknown individuals who reach out. This includes people who contact you to enquire about your organization or claim to be from your bank.
- Verify, and verify again. Get into the habit of verifying and cross-verifying credentials and authorization before sharing any sensitive information. Use official contact information (such as the person’s phone number from your organization’s internal contact directory) and not information that’s provided to you by the suspicious individual.
5. Avoid Getting Compromised If You’re Hit With a DDoS Attack
Ever landed on a site to be greeted by a chatbot ready to help you out in case you have any questions? Most of us have, but unfortunately, not all bots are created equal. For example, a botnet is a network of many interconnected devices (PCs, servers, IoT devices, etc.) that are infected by malware and controlled by an attacker. The botnet army (aka a zombie army) is a serious threat to organizations of any size and can be used to send spam emails, engage in fraud campaigns, carry out DDoS attacks, etc.
A distributed denial of service (DDoS) attack involves botnets flooding a target system (like a web server) with more requests than they can serve, eventually rendering the victim inoperable and unable to process any legitimate requests from users.
Proposed Method(s) for Mitigating These Types of Information Security Threats:
DDoS attacks — where the aim is to saturate the target’s bandwidth or consume resources, making them unavailable or painfully slow for actual customers — can take time to detect. Let’s take a look at some of the ways to tackle this security threat:
- Protect your network using an anti-DDoS solution and deploy technology that monitors it thoroughly for any signs of an attack.
- Patch and update your firewall and security applications.
- Plan and determine the best course of action, outlining all the steps to be taken in the event of a DDoS attack, ahead of time.
6. Defend Against the Dangers of Advanced Persistent Threat Attacks
Advanced persistent threats (APTs) prioritize stealth to remain undetected after breaching a network. These attacks are prolonged and targeted towards high-value entities (like governments, intellectual property, national defense, etc.), with the primary motivation being espionage or data theft rather than immediate financial gains.
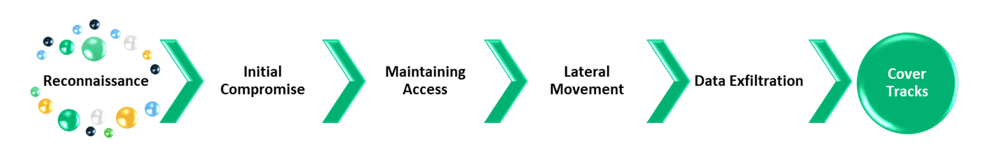
Often perpetrated by nation-state actors, the goal of these information security threats is to maintain ongoing access and to move laterally within the network to increase the foothold and pursue data exfiltration.
Proposed Method(s) for Mitigating These Types of Information Security Threats:
APTs play the long-term game, are well funded, and usually rely on zero-day attacks to evade detection by security solutions deployed on the network. For these reasons, mitigation becomes a challenge, but the steps below highlight a few concrete actions we can take in the right direction:
- Harden your perimeter defenses. For the most part, when we talk about network security, we’re really referring to securing the perimeter. But with APTs, we need to carefully monitor the flow of traffic within our internal networks. To achieve network security goals, we need to deploy firewalls, UTMs, IDS/IPS, etc. and keep them configured correctly with sound rules, install updates, patch vulnerabilities, etc.
- Monitor both incoming and outgoing traffic. It is crucial to stay vigilant not only of the traffic flowing into the network but also of the outgoing traffic.
- Implement updates and enforce security policies. Some additional ways to prevent attacks include whitelisting allowed applications, establishing least permissive policies, minimizing administrative privileges, patching the OS, etc.
7. Prevent Insider Threats Within the Organization From Undermining Your Security
Anyone from within the organization who may have access to the business network and sensitive data can share sensitive data with malicious agents. Insider threats include gullible personnel, disgruntled employees, third-party contractors, etc.
While employees with an ax to grind may purposefully reveal business-critical information, some simply fall prey to social engineering attacks. External vendors may also pose serious security threats, and these risks need to be assessed and managed before allowing them to be onboarded and given access to the business network.
Proposed Method(s) for Mitigating These Types of Information Security Threats:
Businesses with monitoring technologies in place have continued to report data theft and fallen victim to insider threats despite the right tools. There is no one solution that makes security threats disappear; rather, there’s a series of controls that can be implemented to reduce the chances of a breach.
- Offer regular cyber awareness training and workshops. Regular, interactive cyber awareness programs, simulated phishing attacks, etc. can help train employees to identify and react better to information security threats.
- Assess the security prowess of vendors before providing them with access. It makes sense to conduct a comprehensive, end-to-end vendor risk assessment for third parties to understand and evaluate their security posture before providing any access to the business network and prior to sharing any critical data.
- Increase visibility within your organization and limit access to critical systems. Using DLP solutions or cloud access security brokers (CASBs) for organizations using cloud file storage, disabling USB ports, limiting access on a need to know basis, temporary accounts for contractual workers, multi-factor-authentication, and minimal privileges are some additional ways to keep a check on insider threats.
In Summary
Because it’s difficult to cover every other risk out there, more than a few information security threats such as ransomware, cryptojacking, lack of encryption, IoT vulnerabilities, etc. have been left out. However, one common negligent practice that can be easily rectified is the timely renewal of SSL/TLS certificates.
Expired digital certificates can introduce unintended weaknesses into the network infrastructure, with the average cost of certificate mismanagement per organization being more than $11 million. By taking proactive actions to defend against security risks, we have a better chance of not merely reacting to cyber-attacks but preventing them from breaching our networks in the first place.
























 (16 votes, average: 4.50 out of 5)
(16 votes, average: 4.50 out of 5)






No comments