What Is Passwordless SSH? A Look at SSH Passwordless Authentication
With the rise of remote work in the pandemic era, remote desktop (RDP) and secured shell (SSH) exposures have surged; Edgescan reported an increase of 40% in 2020 alone. Passwordless SSH promises to make SSH more secure by eliminating the use of weak or cumbersome passwords. Let’s learn some more about passwordless SSH authentication
Secured socket shell, often called secure shell or SSH, was written by Tatu Ylonen in 1995 and has since evolved into OpenSSH and other products. SSH is a network protocol that helps establish a secured communication channel between two devices over an open network (i.e., the internet).
SSH is almost unavoidable whether you are a network administrator, DevOps engineer, or chief information security officer (CISO). It’s available in Unix, Linux, and Mac systems. However, it traditionally involves an admin manually entering a username and password to authenticate to gain access to the server. Using a weak password that’s easy to guess leaves your organization and its data at risk to brute force and credential stuffing attacks. This is where passwordless SSH authentication can help.
But what is passwordless SSH? And what are five SSH passwordless authentication best practices you should keep in mind for your organization? Here’s our take on the topic…
What Is Passwordless SSH?
As the name implies, passwordless SSH refers to the process of proving your identity to your server (authenticating) via secure shell without using a password. This approach bypasses the need to create complex, hard-to-remember passwords and avoids the issue of relying on weak ones that can become compromised.
You see, SSH authentication can be achieved through a few different methods, the main two being passwords or cryptographic key pairs:
- The traditional method involves manually entering your username and password (i.e., a secret) to prove your identity. This authenticates you and enables you to gain authorized access to secure resources.
- Passwordless SSH allows you to authenticate by presenting a cryptographic key on your device via your SSH client instead of entering your username and password. Of course, this private key may require you to enter a password for the first session connection, but you won’t have to do that again for subsequent sessions.
We’ll speak more about how it all works a little later in the area. But the main takeaway from this section is that SSH passwordless authentication gives you access to your account (and everything that entails) using cryptographic keys so you don’t have to type a password every time.
What Is Passwordless SSH Used For?
SSH is the primary method for remotely accessing and administering Linux servers. As such, SSH is used by organizations of all sizes to admin web servers and other servers that they don’t manage via direct physical access. Because nearly 80% of the internet runs on Unix (according to W3Techs), that makes SSH a very commonly used protocol.
Examples of these server admin-related activities include:
- Transferring files over SSH via the SSH file transfer protocol (FTP) or FTP over SSH
- Accessing and managing databases,
- Installing or updating server software and web applications,
- Performing server backups,
- Running remote console commands and/or GUI programs, and
- Perform troubleshooting on servers.
The two communicating devices through the SSH protocol are the user’s client and the server. A client can access the server by entering a username and password in the system.
SSH is designed to be secure, but bad actors need not break the protocol to launch an attack; they can simply break the password protecting it. Group IB lists distributed brute-force attacks on remote access interfaces, including RDP and SSH, as one of the looming threats in 2020-21.
True, having longer passwords (or, better, passphrases) helps, but do you know what’s better? A passwordless environment for transferring your data. That’s the reason society is moving towards passwordless SSH. With a passwordless SSH connection, the user doesn’t have to enter the password again and again to get access — this saves you valuable time as a developer or administrator.
How Does Passwordless SSH Work?
Passwordless SSH works on the principles of asymmetric encryption or public key cryptography. It uses a set of two cryptographic keys — a public key and a private key. The private key is a long string of random characters stored in the SSH client’s memory. As the name suggests, the private key is kept private or secret. The public key is derived from the private key (but the private key can’t be generated from the public key) and can be shared with everybody, with both the client and the server having access to it.
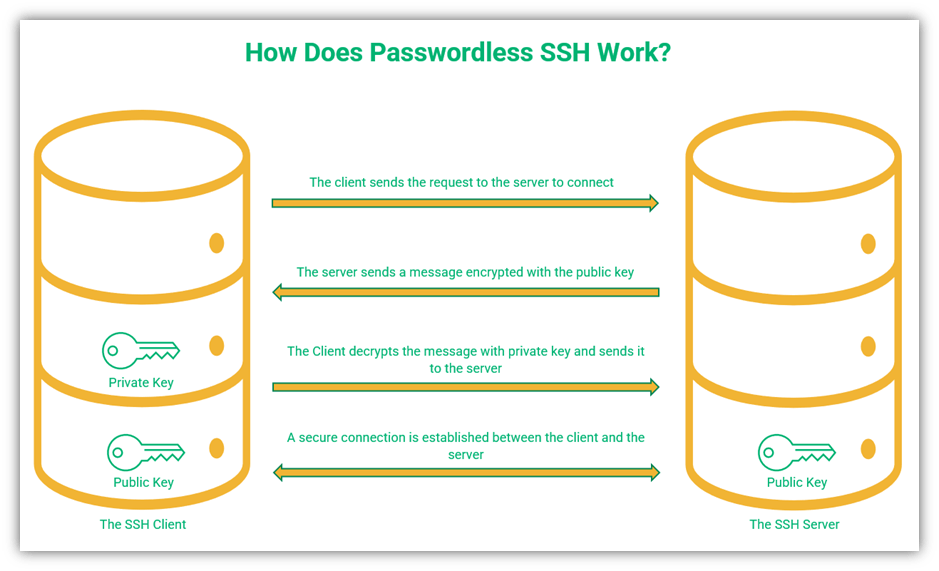
The steps to authenticate the client and to establish a secure communication channel for transferring data are given below:
- The SSH client sends the server a request to connect along with its username and public key.
- The server replies with a random message encrypted with the client’s public key.
- The client decrypts the message sent by the server using its private key.
- The client sends the decrypted message to the server to prove that it has access to the private key.
- The server checks the message to ensure it matches. If it matches, this authenticates the client and allows the server to approve its request to connect.
- A secure connection is established, and the server and the client can now communicate securely via SSH.
Why SSH Keys Are More Secure Than SSH Passwords
There are several key reasons (excuse the pun) why using SSH key-based authentication is more secure than using traditional SSH passwords:
- SSH keys are more secure. Using a key also avoids the issue of users creating and relying on weak passwords. SSH keys are long and complex, which makes them difficult to guess or brute force.
- They offer convenience without compromising security. You don’t have to remember a password to type in, which can become list, compromised or stolen.
- SSH keys don’t require transmission to the server. Because the public key is stored on your server, you don’t have to worry about them being transmitted across an insecure network. And since your private key stays with you, it never gets sent to the server. On the other hand, a password would have to be sent to the server, which put it at risk of being stolen or compromised.
How to Set Up Passwordless SSH
Now that we know what passwordless SSH is and why it’s important, let’s explore how you can put this process to work within your organization. To set up passwordless SSH within your IT environment, it requires you to complete three main steps:
1. Generate Your SSH Key Pairs
In this process, you have the option of creating a passphrase for additional security, but doing so isn’t a requirement. By default, your key will be stored in your ~/.ssh directory, typically in the file /id_rsa.pub. To create your key pair, use the following command to specify the keygen algorithm and key size:
ssh-keygen -t [algorithm] -b [keysize]
So, it would look something like this if you choose to use the RSA algorithm:
ssh-keygen -t rsa -b 4096
For additional security, you can also tie your email address to the key as a comment as well using the following modified command:
ssh-keygen -t rsa -b 4096 -C “[email protected]”
2. Upload the Public Key to the Host (i.e., the Server You Want to Access Remotely)
By completing this step, you’re providing the server with the tools it needs to recognize you as a legitimate user when you log in using your key in lieu of a password. To upload your authorized public key and ID, use the following command:
ssh-copy-id [your_username]@[remote_server_ip_address]
So, it would look something like this:
ssh-copy-id [email protected]
3. Test the Login Process on the Server to Ensure Everything Works Properly
Once these other steps are complete, it’s time to ensure that the key actually works as intended. To test the key’s functionality, log in to the server via your SSH client using the username and newly minted key using the following command:
ssh [your_username]@[remote_server_ip_address]
So, this would look something like this:
ssh [email protected]
Pros and Cons of Using Passwordless SSH
Much like everything else in life, passwordless authentication — including that for SSH — has its pros and cons. However, if you know these before you start using this authentication method, then it’s much easier to deal with the potential risks before they can become issues. Let’s examine both.
Pros:
- Makes secure SSH authentication a breeze
- Enables you to connect more quickly than traditional SSH authentication methods
- Provides better security against brute force attacks than password-based SSH authentication
- Allows the creation of a server-side whitelist of authorized IP addresses
- Enables the user to limit client access rights
- Allows access to the device whether it is manned or not
- Allows automated and interactive file transfer securely
Cons:
- Private keys will pile up if you don’t follow SSH key management best practices
- Proper key management is an extra administrative task (and thus can create an additional expense)
- Passwordless authentication can lead to man in the middle attacks if keys are stolen or otherwise compromised (which is why key management is so important)
- It becomes tedious to add and delete user keys once they are no longer required
Winding Up Our Exploration of Passwordless SSH
Passwordless SSH is a network security protocol that authenticates the user and creates a secure communication channel between a server and client. It does this with the help of public key infrastructure or asymmetric encryption. Despite being a widely used protocol, SSH has some areas of vulnerability when used in practical life. If these vulnerabilities are addressed with caution and best practices are followed, it can become a near-perfect network protocol.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security