What Does a Firewall Do? An Overview on Firewalls
We answer the question “what does a firewall do” by going through an overview of the cybersecurity tool and covering some of the most important firewall types you should know
One of the biggest headaches a business can face is dealing with a public data breach or another form of a hack. IBM estimates that it takes more than three-quarters of a year to identify and contain a data breach. Yikes! Businesses spend lots of money and resources dealing with cybersecurity issue. Wouldn’t it be nice if there was something that stopped cyber-attacks at the door and never let them through in the first places? Luckily, many tools can help do this, and maybe none more commonly used than a firewall.
Firewalls are a staple in pretty much any company’s cybersecurity toolkit. Businesses of all sizes can benefit from having firewalls protecting their sensitive data.
So, I’m sure with all this talk about how great firewalls are, you’re wondering “what does a firewall do?” Well, you came to the right place. In this article, we answer the question “what does a firewall do?” We start by going through an overview of what this tool is and also cover some of the most important firewall types you need to know about.
So, What Is a Firewall & What Does a Firewall Do?
Glad you asked. A firewall is a cybersecurity tool that protects your network by monitoring, filtering, and controlling traffic that attempts to enter or exit it. So, what a firewall does, in a basic sense, is serve as a barrier that ensures only good traffic gets in and bad (malicious) traffic doesn’t. It does this by identifying trusted traffic and untrusted traffic and acting accordingly.
Think of a firewall like a sentry who’s in charge of drawing and lowering a castle drawbridge. Their job is to inspect and monitor the traffic entering and leaving the castle. If they see anyone unusual or unauthorized attempting to enter or leave the fortress, they can either allow or block the suspicious person (or people) from entering or leaving. Firewalls work much the same way but for data transmissions instead of people.
Firewalls make up one or more layers within your cybersecurity defenses. They help to protect your network from many types of threats, including malware and brute force attacks.
Because a firewall prevents unauthorized access to your network from the internet, it also protects the devices that are connected. For businesses, this could be your computers, servers, and connected devices such as wireless printers and smart thermostats. A helpful and necessary tool, indeed!
How Firewalls Work
In a nutshell, firewalls inspect all incoming and outgoing traffic. They monitor and log traffic to provide a record of successful and unsuccessful attacks and also have alarms that alert you to suspected breaches. But how do firewalls distinguish trusted from untrusted traffic? It all has to do with the information they convey.
To understand how firewalls work, you need to understand how data travels on the internet. Data travels in packets (or “data packets”), which are fragments of data that are pieced together to make up a larger body of content. These data packets travel from device to device (often through multiple routers and servers). This video will give you a pretty good idea of how data travels across the internet:
A commonly used firewall, known as a packet-filtering firewall, will dissect key information in these packets (namely the header and payload) before allowing it into the network. Firewalls know what to look for in these packets based on a predefined set of rules. These rules help them to identify good (trusted) from bad (untrusted) traffic.
However, there are many more types of firewalls in addition to packet-filtering firewalls that you need to know about. We’re going to talk more about each type of firewall individually in a moment. But for now, just know that they come in different formats — hardware- and software-based.
Firewalls also can be installed in various areas of your infrastructure, including parts of your network, cloud, and endpoints like your computers. And they can be found anywhere — from your home computer’s antivirus program to your organization’s routers. But what a firewall ultimately does, in a general sense, stays the same: a firewall protects your network by filtering out potentially malicious traffic and allowing in authorized traffic. It’s just how they do so differs from one type of firewall to the next.
Now, to further answer the question “what does a firewall do?” in terms of how different firewalls operate, we will need to explore these firewall variations.
Hardware Firewalls vs Software Firewalls
Two categories of firewalls that you should know are hardware and software firewalls. As the name would suggest, a hardware firewall is an actual physical appliance that’s comparable to a traffic router in that it filters your network traffic. Its purpose is to provide network and endpoint protection. However, hardware firewalls attempt to protect your entire network with a single device. This makes them susceptible to attacks on the interconnected relationships of the network.
Using software firewalls would be a more granular approach as it would consist of installing a firewall on existing individual local devices. A software firewall, which is commonly included in antivirus programs and operating systems, acts similarly to a hardware firewall. It inspects and filters traffic, but only for that specific endpoint device.
Is it better to use one versus the other? A common tactic for large networks is to use both hardware and software firewalls as a way to create layers of protection.
Other Types of Firewalls That Help Answer “What Does a Firewall Do?”
As mentioned, firewalls come in many different forms and are used in many different areas. You can categorize them by format, deployment location, or in terms of what they protect. So, it can get a bit tricky when trying to learn the different types.
To learn what a firewall does, it’s best to break down the different types by processing modes. What we mean by processing modes is categorizing firewalls by their operational function. This way, you can try to visualize what a firewall does, and how and why it functions the way it does.
Packet Filter Firewalls
This is the type of firewall we were discussing a little earlier in this article. A packet-filter firewall uses a set of rules to determine whether data packets can enter your network or not. The firewall rules consist of access controls that tell the firewall what to look for in a data packet. The types of information that data packets include are:
- Port numbers,
- Destination IP addresses,
- Protocols, and
- Source IP addresses.
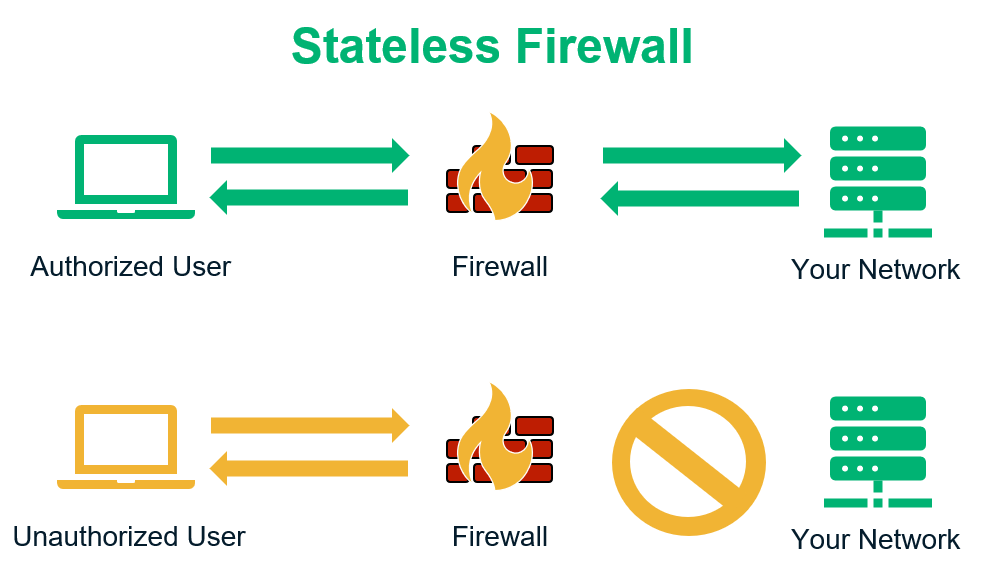
The type of packet-filtering firewall that uses these particular “access controls” is the stateless firewall (yes, we’re now discussing the “types of types of firewalls”… it’s firewall inception!). The stateless firewall operates in a very basic sense: it simply compares incoming and outgoing traffic to the set of rules/access controls that it’s been provided. Basically, it’s a network perimeter firewall, so it doesn’t monitor the traffic sessions that occur inside the network. This is also known as static packet filtering because it relies on a pre-determined (static) list of rules.
However, there’s another type of packet filtering firewall that’s more dynamic. This is called a stateful firewall, which engages in what we call dynamic packet filtering. It operates similarly to a stateless firewall in that it filters incoming and outgoing traffic using preset rules. But once the traffic gets into the network, the firewall goes beyond its counterpart by keeping tabs on its active sessions. In particular, a stateful firewall keeps tabs on the traffic’s source, ports, and destination IP addresses. Any responses that attempt to leave the network must match the data that entered or else it will be halted at the firewall.
Proxy Firewalls
This particular firewall acts as an intermediary between two systems that want to communicate through a client. This intermediary serves as a buffer between internal and external systems. The proxy firewall intercepts incoming traffic and then acts as a substitute for it. This layer of protection protects endpoints from potential attacks.
You may also hear of a proxy firewall be referred to as a gateway firewall or an application-layer firewall. These names come from the fact that they filter traffic at the OSI application layer. This firewall adds a higher level of protection due to its thoroughness, but the downside is that this extra level of effort can affect performance.
Circuit-Level Gateway Firewalls
Working at the OSI (Open Systems Interconnection) session layer, it’s the circuit-level gateway firewall’s job to authenticate the TCP (Transmission Control Protocol) handshakes of traffic attempting to enter the network. This is to make sure the connections are secure. These types of firewalls are typically built into existing software and don’t check data packets. This makes for a low-maintenance and efficient transaction. However, due to the lack of content filtering, it’s also a firewall that’s more vulnerable to certain types of cyber attacks.
MAC Layer Firewalls
The MAC (Media Access Control) layer firewall vets incoming traffic through a rather unique process. By operating in the media access control layer of the OSI model, this firewall identifies the MAC addresses of the host computer that’s attempting to access it. Equipped with an access control list that’s linked to MAC addresses, the MAC layer firewall can more easily identify and deny unwanted traffic.
A Few More Firewalls to Know
If you thought that was a complete list of firewalls, you’re mistaken. There are actually several other types of firewalls to note. We aren’t going to do a deep-dive into all of those now, but we’ll briefly touch on some of them just to help familiarize you with them.
- Hybrid Firewalls — As the name would suggest, this firewall is a hybrid of many of the firewalls you read about above. For example, a hybrid could couple proxy services and packet filtering to serve as a more complete device.
- DNS Firewall — The DNS is another area where traffic regularly passes through and could use the filtering power and capabilities of a firewall. These firewalls are unique because they operate in an external environment.
- Web Application Firewalls (WAF) — These types of firewalls are commonly used for website security. They help to filter and control traffic by way of HTTP and HTTPS connections.
- Next-Generation Firewalls (NGFWs) — These firewalls offer a little bit of everything and can be used in a variety of ways. Next-gen firewalls are different in that they inspect the entire transaction of data (i.e., the payload of the packet).
The Downsides of Firewalls
As we know, technology isn’t perfect. So, yes, there are some potential downsides to using certain types of firewalls. You just have to weigh the advantages and disadvantages of using different types of firewalls to decide which one(s) will best serve the needs of your organization. We mentioned a few already. To recap:
- Hardware firewalls can be susceptible to attacks via interconnected relationships due it being a single device trying to protect a whole network
- Software firewalls are typically installed on multiple devices, which will eat up time when configuring and RAM when in use.
- Both proxy and stateful inspection firewalls may slow down your system due to the resources they require to function.
- Another downside to keep in mind is that the more complex firewalls are often more effective but are also typically more expensive. Firewalls that are less complex and require fewer resources are typically more affordable but are also more likely to be susceptible to attacks. Of course, there are exceptions to this concern, which is why it’s important to always carefully review all of your options before making a decision.
- Finally, another downside to consider is that when you’re choosing to filter all of your traffic, you run the risk of unintentionally blocking what would otherwise be considered legitimate or authorized traffic.
What Does a Firewall Do — Final Thoughts
Firewalls constitute just one of multiple important layers in an organization’s effective security defenses, but they’re a key ingredient that should never be overlooked. While it’s true that firewalls come with many operating systems and antivirus solutions, they often don’t meet the needs of businesses. This is why organizations need to weigh the options and consider more comprehensive firewall solutions that offer greater protection.
So, when answering the question “what does a firewall do,” the most important part of that answer is that they keep dangerous and malicious traffic out of your network while ensuring legitimate and trusted traffic has access.
We hope this overview gave you a better understanding of how firewalls protect your business and what the different types are. Keep an eye out for more firewall articles in the future as we share additional insights about these helpful tools!














 (9 votes, average: 4.56 out of 5)
(9 votes, average: 4.56 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security