Cryptology vs Cryptography: What’s the Difference?
Explore the meaning of cryptography and cryptology in layman’s terms and know the difference between them
If you’re a newbie in the world of technology and words like cryptology, cryptography, cryptocurrency, cryptanalysis, etc. haunt you in the middle of the night, you’re not alone! Even some people working in the tech industry for decades might also not be aware of the meanings of the terms — such as cryptography vs. cryptology — and use them interchangeably. But it’s always a good idea to know the exact meaning of important tech terminologies like these and clarify the concepts at the grassroots level.
In this article, we’ll cover what is cryptology, answer questions like “what is cryptography?” and go over the difference between cryptography and cryptology.
Cryptology vs Cryptography
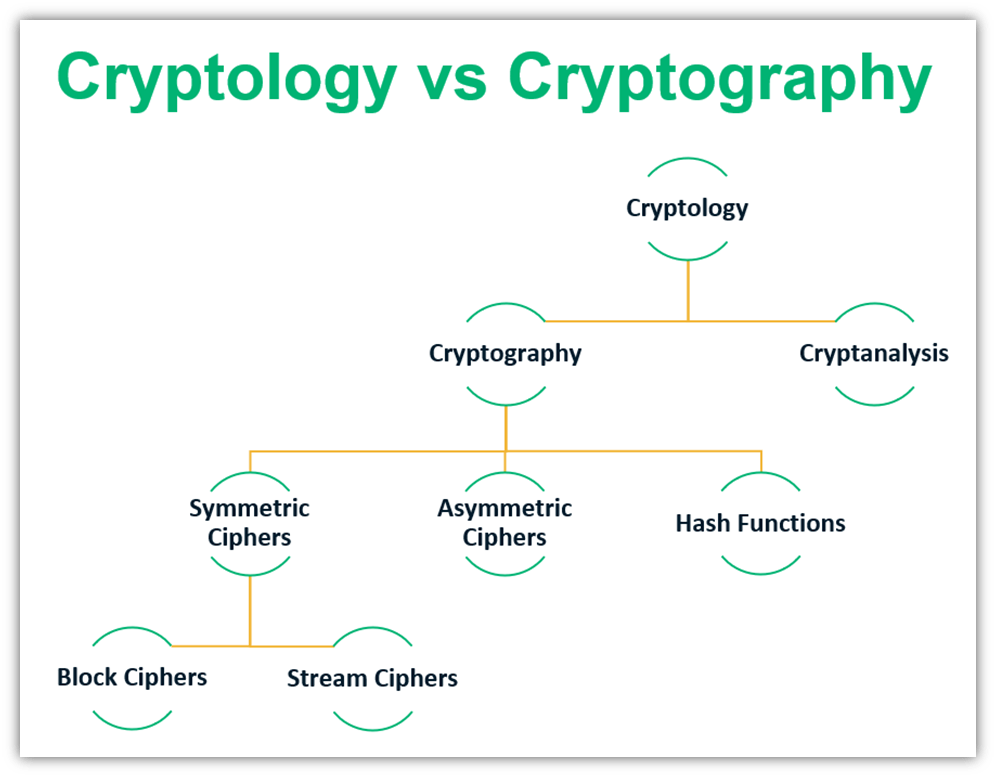
Cryptology and cryptography are two terms that relate to the hiding, disguising, or uncovering of hidden information as well as the study of cryptographic systems. These two terms are frequently used interchangeably nowadays, but when you look at the two terms at a granular level, you’ll see some important differences that distinguish them. Let’s explore the two terms individually to help you understand what we mean by that.
What Is Cryptography?
Cryptography refers to the study and application of codes and methodologies that secure information from access by unintended parties. Basically, it’s all about secure communications and data nowadays. What we mean by that is preventing unauthorized or malicious users from accessing data while still enabling the intended users to do so. In simple words, cryptography includes all the methods that are used to keep the communication between two parties secret in a way that no one else can read, interpret, modify, or otherwise steal the message.
There are two main pillars of cryptography: encryption and hashing.
Encryption in Cryptography
Encryption is integral to information security nowadays. You have locks on your doors, vaults, and vehicles to protect the things they store, right? Well, digital information must be protected in much the same way, and we are gradually shifting to a paperless world where all our information and data is stored online. Whether data is in transit or at-rest, it must be protected from malicious hackers, cybercriminals, and other unintended or unauthorized parties.
To protect the data, a technique called “encryption” comes in handy. Encryption means scrambling plaintext data into incomprehensible cipher data. For example, if you encrypt the word “Hello” with the DES algorithm, it will look something like this: W/G6lMfDBEZO+DCFRQB3bg==.
For encryption and decryption, mathematical algorithms and complex keys made of random and unpredictable alphanumeric characters are used. Imagine a regular lock and key. The lock’s mechanism is an algorithm, and the key is a cryptographical key, without which you can’t lock and unlock the door. Once the data is secure, no one can read or otherwise interpret the original data from the ciphertext without using the special key.
The encoding method where the same key both encrypts and decrypts data is known as symmetric encryption (symmetric cryptography). Only the sender and recipient should have access to this secret key. If anyone else gains access to the key, they can use it to access the data. Another type of cryptography is asymmetric encryption (asymmetric cryptography). This involves using two separate keys for encryption and decryption. The public key, which is available to all, encrypts the data. And the decryption key, which is called a private key, the recipient must keep secret and never share it with anyone.
Hashing in Cryptography
When people talk about hashing in cryptography, they’re referring to something known as a hash function. Hashing means converting an arbitrary amount of data into a fixed-length output of enciphered data. A hash is a mathematical algorithm that serves as a one-way function to transform a random quantity of data into a fixed-length output known as a hash digest. So, no matter whether you have 10 pages of data or one sentence, the resulting hash size will be the same length.
Hashing is practically irreversible. If you have a hash value, you can’t reverse it using the same algorithms. You can’t figure out the original data based on the hash value without using massive amounts of computer resources and time — thousands or even millions of years depending on how the hashing is done. That means hashing can help to keep your data secret.
Hash values are unique and no two different input data should (ideally) generate the same hash value. If they do, they “collide.” This means that a good hash should demonstrate collision-resistance. If someone makes even a seemingly insignificant change in the initial input, the output hash value changes as a result. Hence, no data tampering goes unnoticed. That’s why hashing is used to check data integrity.
Summary: Cryptography includes all these algorithms, keys, and methods that one can use to protect data from leaking, eavesdropping, and tampering.
What Is Cryptology?
Cryptology is a broad, umbrella term that encompasses both cryptography and cryptanalysis. Cryptology includes the study and practice of both cryptography (i.e., protecting data by hiding it from anyone who isn’t supposed to see, access, or change it) and cryptanalysis (i.e., figuring out how to access the data without having the necessary cryptographic key).
Hence, to understand cryptography vs. cryptology, you must have an idea of what cryptanalysis is.
Cryptography includes all the legit ways of protecting and revealing the data. That means, the only person with having the corresponding keys can access the data. But cryptanalysis includes all the ways to break the protection, even without having the keys. It also includes studies of finding hash collisions, in which two different inputs produce the same hash value (output), which makes data tampering possible.
Imagine you have put a lock on your door. The study of different lock and key mechanisms is cryptography. But if a robber is standing outside your locked door and doesn’t have access to the key, all the outside-the-box ideas he would come up with to break the lock will fall under the area of cryptanalysis.
He may try his luck by using a bunch of duplicate keys. The robber also may try to pick or break the lock with tools like a sharp hairpin, an axe, or even by shooting it with a gun. In the cybersecurity industry, on the other hand, hackers and security researchers carefully analyze the codes and key structure and crack the security mechanism by using mathematics. They use various tools, techniques, and take the help of quantum computers to break the security mechanism.
Looking for a few real-world examples of cryptanalysis?
- Alan Turing performed cryptanalysis and led cryptanalysis teams during World War II that helped turn the tide in favor of the Allies. One of his biggest achievements was using cryptanalysis to crack the Germans’ M3 Enigma code.
- Google demonstrated a SHA-1 collision attack, showing that two different PDF files could produce the same hash value. (Now, granted, they also dedicated lots of people and resources to accomplish this goal… But even still, SHA-1 hasn’t truly been considered a secure hashing algorithm for more than 15 years.)
In short, cryptanalysis includes all of the “outside-the-box” techniques to break the security walls that cryptography creates.
An Overview of Cryptology vs Cryptography
Let’s summarize the difference between cryptography and cryptology:
| Cryptography | Cryptology |
| Cryptography is a narrow concept that includes hash functions, asymmetric encryption, and symmetric encryption, as well as the different types of symmetric ciphers. | Cryptology is a broad concept. Cryptology includes both cryptography and cryptanalysis. |
| Cryptography includes study of techniques to protect content in transit and at-rest. | Cryptology includes everything in the realm of cryptography as well as cryptanalysis. Cryptanalysis includes all the methods of breaching the cryptographic security systems. |
| The purpose of cryptography is to find ways to create the most complex algorithms and robust keys that can protect the content. | The purpose of cryptology is not only to create strong security but also to test and break the cryptographical system by doing systematic mathematical calculations. |
| Cryptography is used by companies, governments, and individuals the world over to secure data between two endpoints and vouch for data integrity. The only person holding the right cryptographic keys can encrypt and/or decrypt messages. In the same way, data tampering doesn’t go unnoticed. | Security professionals use cryptology to find vulnerabilities in information systems to make the cryptographic processes and technologies that protect them stronger. But hackers are also interested in cryptology to study how to break the system to steal the data and execute various cybercrime. |
Final Words on Cryptology vs Cryptography
We all use cryptography in daily life but might not be aware of it. For, example, our emails, social media profiles, the data we share on such websites, etc. are secured with cryptographical methods. But there are security researchers and data scientists that are using cryptology not only for making a strong cryptographical mechanism but also to test those methods to identify the weak areas and patch them.














 (55 votes, average: 4.82 out of 5)
(55 votes, average: 4.82 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security