What Is Transport Layer Security? A Breakdown of the Secure TLS Encryption Protocol
TLS is a secure protocol that protects sensitive information exchanges like passwords and credit card numbers against theft from cyber attacks (which are up 8% year-over-year for organizations). Here’s what to know about this industry standard and how it has evolved to keep up with the most recent threats
The transport layer security (TLS) protocol can help your business protect the sensitive data your server(s) exchange over the internet from leaks and attacks. This is crucial when you consider that the number of data breaches reported each year is soaring, and so are their costs. The figures unveiled by IBM’s 2023 Cost of a Data Breach Report are astonishing:
- 95% of organizations interviewed indicated that they experienced more than one breach in the last 12 months.
- The average cost of a data breach rose to $4.45 million. This represents a massive 15% increase over the past three years.
- Surveyed organizations that employed encryption experienced an average of $221,593 lower costs per data breach.
Does all of this mean that securing your data is a lost battle? Nope. You have TLS on your side.
So, what is transport layer security, exactly? What does the TLS encryption protocol do, and how can organizations use it to secure their websites and applications? Here’s what to know about the transport layer security protocol.
Transport Layer Security Protocol (TLS Protocol): What Is It?
Transport layer security is a cryptographic standard protocol that creates a secure channel for data transmission between a client (e.g., a web browser) and a server (e.g., a web server) over a network. TLS is the successor of the secure sockets layer (SSL) protocol, which was first released in 1995.
Adding TLS to the hypertext transfer protocol (HTTP) ensures that all data transmitted via that connection is sent securely. Have you ever seen a James Bond movie? TLS contributes to generating a secure communication tunnel similar to the impenetrable lines the famous secret agent uses to communicate with the MI6 (i.e., the British foreign intelligence agency) or his team. The idea here is that it helps to prevent data interception attacks, one of the most common of which is known as a man-in-the-middle (MitM) attack.
TLS, originally created by the Internet Engineering Task Force (IETF), is now in its third iteration (TLS 1.2). This is the current standard version of transport layer security and is supported by 99.9% of websites surveyed by SSL Labs.
How can you tell? Check the URL of this page. Does it start with HTTPS? Yup, it does! Any website with a URL that starts with HTTPS (i.e., hypertext transfer protocol secure) uses TLS encryption to communicate.
The Relationship Between Transport Layer Security and SSL/TLS Certificates
TLS doesn’t work alone, though. It requires a secure socket layer (SSL)/TLS certificate and a private and public key pair — two of the essential elements of public key infrastructure (PKI). The digital certificate is tied to the validated organization it’s issued to and contains information about the domain. Although the public key is available to virtually anyone, the web server keeps the private key secret.
By installing an SSL/TLS certificate on your website, you can then enable your domain to use the TLS protocol to secure data in transit. Without the protocol and certificate, data exchanged with your server would be vulnerable to attacks and malware because it would lack authentication and confidentiality.
What Does TLS Do?
- to authenticate the two communicating parties’ digital identities and guarantee data confidentiality and integrity. TLS is so versatile and secure that it’s also utilized for other applications. Among them:
- E-mails,
- File transfers,
- Video/audioconference,
- Instant messaging, and
- Voice-over-IP (VoIP).
Right. But this is just the tip of the iceberg. What does TLS do, exactly? And why is it so crucial for businesses and customers alike? Let me explain it with a real-life example; then, we’ll go deeper into the maze of the TLS world and find out more about it.
A few years ago, I organized a birthday party for one of my friends. When I attempted to ask my favorite bakery about their options through their online contact form, I looked at the URL and noticed a little red strike over the padlock. Dang! It’s Firefox’s way of telling me the site uses HTTP only for its connection (i.e., it wasn’t secure). For a highly paranoid cybersecurity professional, this was a big no-no.
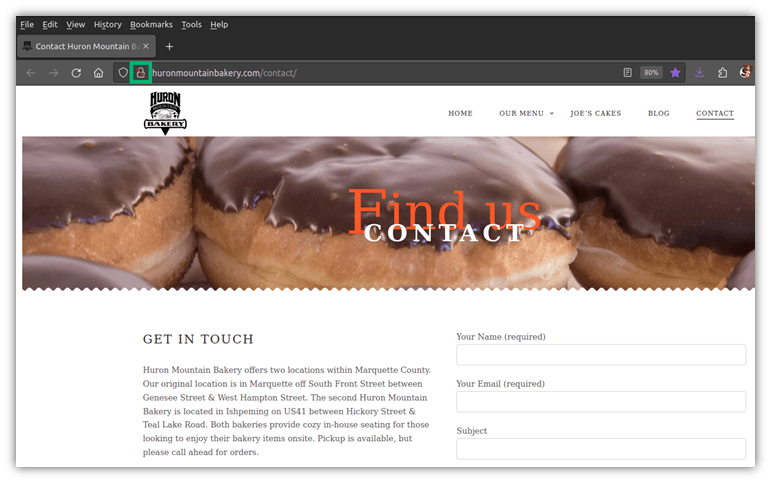
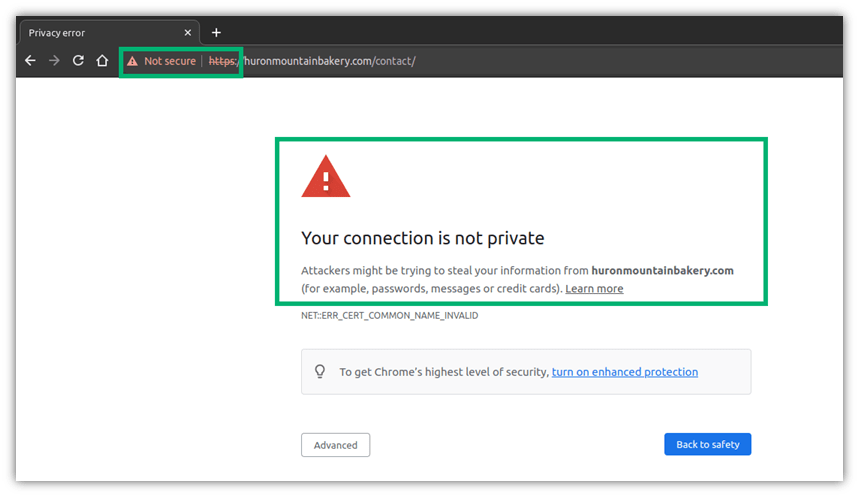
When a connection isn’t protected by transport layer security, all of the sensitive data I submit is unencrypted; thus, it’s at risk of being seen by anyone. A savvy attacker can do a lot of damage with a single piece of data, even if it’s only an email address.
For example, a bad guy can check my social media profiles to try to find the names of colleagues and friends and discover which company I work for. He could then utilize the information to impersonate my boss or a colleague to get ahold of more sensitive data.
Think I’m being paranoid? Don’t be so sure. According to ForgeRock’s 2023 Identity Breach report, third-party breaches caused by stolen sensitive data rose 136% in 2022.
How TLS Helps Secure Your Data, Customers and Organization
TLS can help you reduce these kinds of risks by doing the following:
- Enhances the security of websites and applications. the web server confirms its identity through a trusted SSL/TLS certificate during the handshake. As the data can only be decrypted by the recipient’s private key, it’ll ensure that the two communicating parties are who they claim to be.
- Protects the integrity and confidentiality of exchanged data. TLS uses a mix of asymmetric encryption (during the handshake) and symmetric encryption (when sending the data during the rest of the session). The transmitted information (e.g., credit card numbers, email addresses, and passwords) is encrypted by the sender with the public key, shielding them from prying eyes. Once encrypted, the data package is signed with a unique message authentication code (MAC). By verifying the MAC, the recipient can ensure the data hasn’t been tampered with.
- Prevents data interception attacks. A famous proverb says: “Two’s company, three’s a crowd.” That concept applies to the digital world, too. Only authorized parties should view the credit card details you entered into a website. No cybercriminal should be able to intercept, steal, or modify that data. TLS encryption will reduce the risk of such attacks and, thus, protect your precious data.
- Minimizes the risks of data breaches. Forty (40) million Britons — more than half of the British population — had their voter data exposed due to a data breach. (NOTE: Data breaches are the most common consequence of MITM attacks.)
TLS Contributes to Boost Your Online Presence and Gain Customers Trust
On top of what we’ve already listed, TLS is a precious ally for organizations of all sizes as it:
- Increases customers’ trust. TLS will enable your customers to enjoy a safe browsing experience, enhancing trust and growing sales. The 2023 Edelman Trust Barometer shows that 59% of consumers prefer buying products from a trusted brand. 73% consider brands that give them a high sense of security more valuable.
- Minimizes the risk of fraudulent transactions. With TLS, the payment details entered by your customers are secure and cannot be intercepted by cybercriminals. This means that the attacker won’t be able to use them to fraudulently purchase services or products from your website and leave you to deal with the costly consequences.
- Contributes to improving search results ranking (SERPs). Want to improve your Google search rank? TLS is a ranking factor that Google considers when positioning your websites in search results.
OK. Now that you know the importance of TLS for websites and applications, have you checked your website to ensure you’re using it? You can do that by simply pasting your hostname into our online server test tool. You’ll get the results in a matter of seconds. Do all of your pages support TLS, including your contact form page?
If some don’t, it’s probably time to change this. Before you do it, let’s get to know the different transport layer security protocol versions available so you can figure out which one to implement.
TLS Versions: What They Are and Why You Should Use TLS 1.2 as a Minimum
At the beginning of this article, we said that the web server uses an SSL/TLS certificate to confirm its identity to the client. Why is it called SSL/TLS and not simply TLS? Because even if TLS is just the evolution of the old secure socket layer (SSL) protocol, people were just too accustomed to the name SSL. And, as the proverb says, “Old habits die hard.”
But does this mean that SSL and TLS protocols are the same? Not quite. While they both have the same goal of providing a secure connection through encryption and authentication, there are some key technical differences that we’ve summarized in the table below:
| Secure Socket Layer (SSL) | Transport Layer Security (TLS) | |
| Level of Security | Low. All SSL versions are now deprecated. | High. The recommended versions are TLS 1.2 and 1.3.Versions 1.0 and 1.1 are deprecated. |
| Handshake Process | Uses an explicit connection (i.e., the client requests an encrypted connection) for the handshake (i.e., when the browser confirms the server’s identity by verifying its SSL/TLS certificate). It’s more complex and slower as it requires more steps. | Utilizes an implicit connection (i.e., the connection is encrypted from the beginning) during the handshake. Uses fewer steps, making the handshake process faster. |
| Cipher Suites | Supports a limited set of old, weak and deprecated algorithms. | Supports several sets of strong algorithms. Newer versions support the quantum-resistant algorithms approved by NIST like CRYSTALS-Kyber, and Falcon. |
| Message Authentication and Integrity | Creates the fixed-length string attached to the message (MAC) is generated using the vulnerable MD5 algorithm. | Utilizes the more complex hash-based message authentication code (HMAC) generated with more robust algorithms. |
| Alerts and Warnings | Generates 13 alerts spanning two alert levels: warning (i.e., an error has occurred) and fatal (the connection must be immediately terminated). Doesn’t encrypt the alerts. | Generates dozens of connection closure and error-related alerts in TLS 1.2 and TLS 1.3 alone. |
In summary, SSL shouldn’t be used any longer as it isn’t secure enough. But, what about your SSL/TLS certificate? Will it work with TLS, too? You bet it will; in fact, it’s what your browser is using right now to connect to SectigoStore.com. Now, let’s have a look at the TLS versions available.
TLS Version 1.0 (TLS 1.0)
Based on SSL 3.0, TLS 1.0 was written by Christopher Allen and Tim Dierks as a way to mitigate some of the security issues found in its predecessor. However, TLS 1.0 had issues, too. For example, it used vulnerable algorithms like MD5 and SHA-1, and allowed the connection to be downgraded to SSL 3.0 without changing protocol (e.g., POODLE attack). The Payment Card Industry (PCI) Council suggested organizations to go with the newest version available at the time.
TLS 1.0 was deprecated by major browsers in 2020 and IETS in 2021 (together with version 1.1) as described in the RFC8996.
TLS Version 1.1 (TLS 1.1)
TLS 1.1 was defined by RFC4346 and offered protection against cipher-block chaining (CBC) attacks where the bad guys try to guess the encrypted message, and then verify if the encryption matches one of the messages transmitted. (TLS 1.0’s implicit initialization vectors [IVs] were replaced with explicit IVs.)
It was also quickly deprecated as it supported weak algorithms and was vulnerable to several kinds of attacks such as:
- SWEET32. It exploits legacy block-cipher algorithms like the data encryption standard (i.e., DES) and triple-DES. These cyphers, commonly used by TLS 1.1, are vulnerable to birthday attacks that, if successful enable the cybercriminal to decrypt and access the information.
- ROBOT. This affects TLS versions that rely on RSA encryption. By sending a series of messages with incorrect padding (i.e., adding the wrong padding bytes) and checking the server’s response, a malicious third party can easily identify vulnerable servers and exploit them.
- CRIME. A cybercriminal can insert himself between the client and the server, exploiting the TLS protocol’s optional data compression feature. How? By using brute force to decrypt communication session cookies.
TLS Version 1.2 (TLS 1.2)
Although transport layer security protocol version 1.2 was released in 2008, it’s still the most commonly supported version of the TLS encryption protocol for websites and applications. Why? Because it helps organizations reach compliance with privacy and security regulations such as:
- Payment Card Industry Data Security Standard (PCI DSS),
- Health Insurance Portability and Accountability Act (HIPAA) and,
- EU General Data Protection Regulation (GDPR).
It also provides the minimum level of security required to protect sensitive data transmissions against most attacks, thanks to the following three key enhancements:
- Less complex and faster handshake. TLS 1.2 full handshake includes two rounds of communication. In the first round, the server sends its SSL/TLS certificate and its public key to confirm its identity (i.e., client and server hello). As a second step, the client sends a pre-master secret (i.e., a random byte string encrypted with the server’s public key) and a change cipher spec message to the server informing it that it’s going to switch to symmetric encryption.
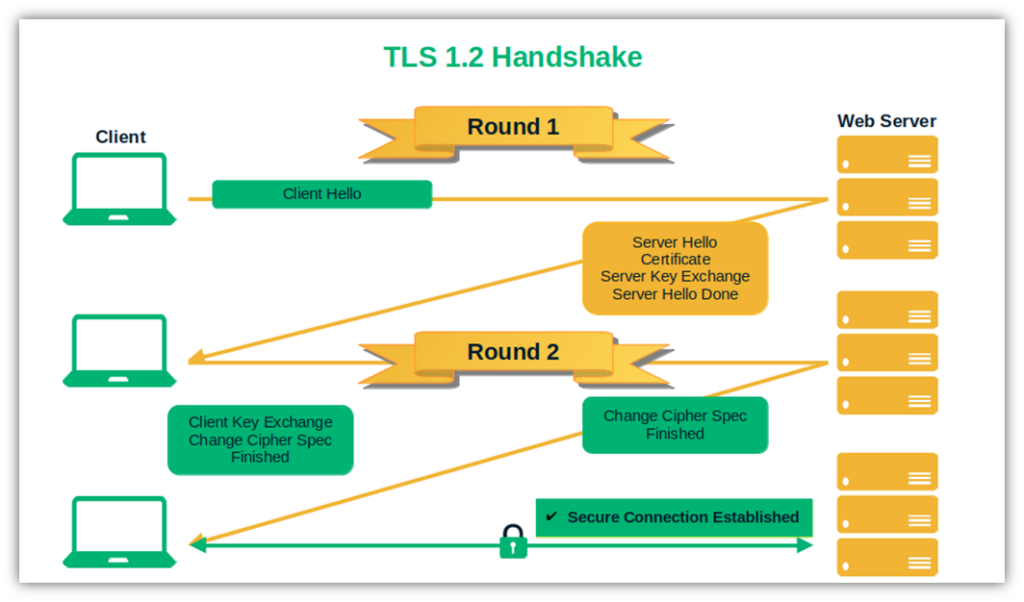
- More secure algorithm. 62% of businesses surveyed by Thales consider network decryption their biggest security threat concern. Do you remember when we talked about the deprecated and vulnerable MD5 and SHA-1 algorithms? In this version, both are replaced by the more secure SHA-256.
- Advanced cipher suites. Looking for a good alternative to the old RSA encryption cipher suites? TLS gives you the option of replacing it with elliptic curve cryptography (ECC). ECC has a smaller key, but it’s as secure as (or more secure than) RSA. To take the security of TLS 1.2 to the next level, it can also be combined with the Federal Information Processing Standards Publications (FIPS)’s advanced encryption standard (AES) for symmetric session encryption.
So, if you still haven’t implemented TLS, make sure your websites and applications support at least TLS 1.2. Looking for an even greater level of security? Then the latest transport layer security protocol version 1.3 might be the one for you. Let’s find out more about it.
TLS Version 1.3
TLS 1.3 is supported by 63.5% of the most popular websites scanned by SSL Labs. It was officially released in 2018 and is considered the most secure TLS version. Supporting only algorithms offering perfect forward secrecy (PFS) is one of its best features.
PFS is a set of protocols that forces one-time usage of session keys. In a nutshell, when TLS 1.3 is used, each session utilizes a new set of keys. The advantage? Even if the server’s private key is compromised by an attacker, they won’t be able to reuse it in the next session. Goodbye, Heartbleed vulnerability! With TLS 1.3, it won’t be an issue anymore.
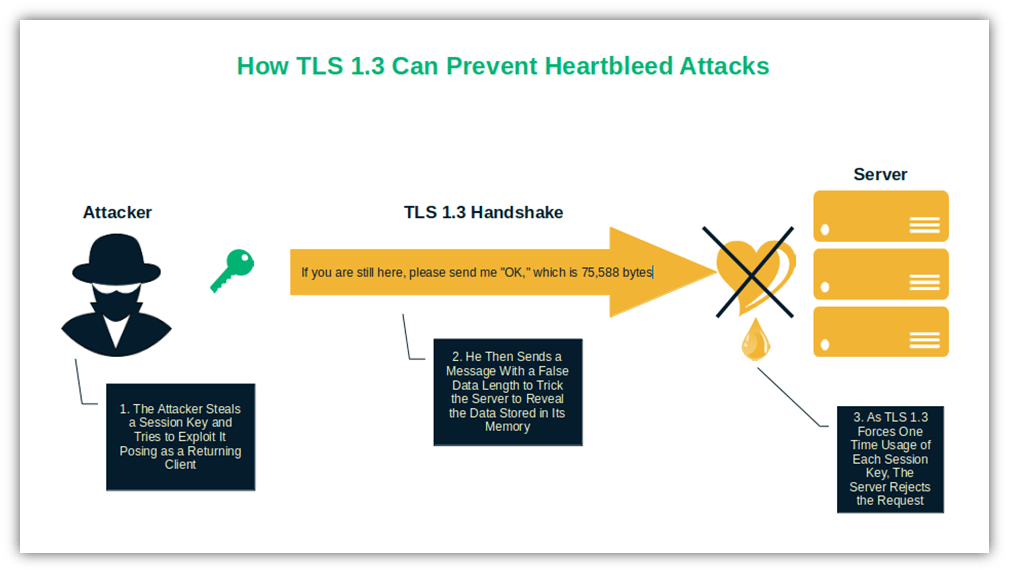
Other essential improvements include:
- Increased handshake performance. If you thought that TLS 1.2 was fast, you’ll be amazed by the speed of TLS 1.3. The handshake has been so compressed that it’s now made of one single round-trip. The client and the server share everything (e.g., cipher suites, keys, chosen protocol, and the SSL/TLS certificate) at the hello stage of the handshake. Then, the client validates the certificate, and the encrypted connection over HTTPS starts.
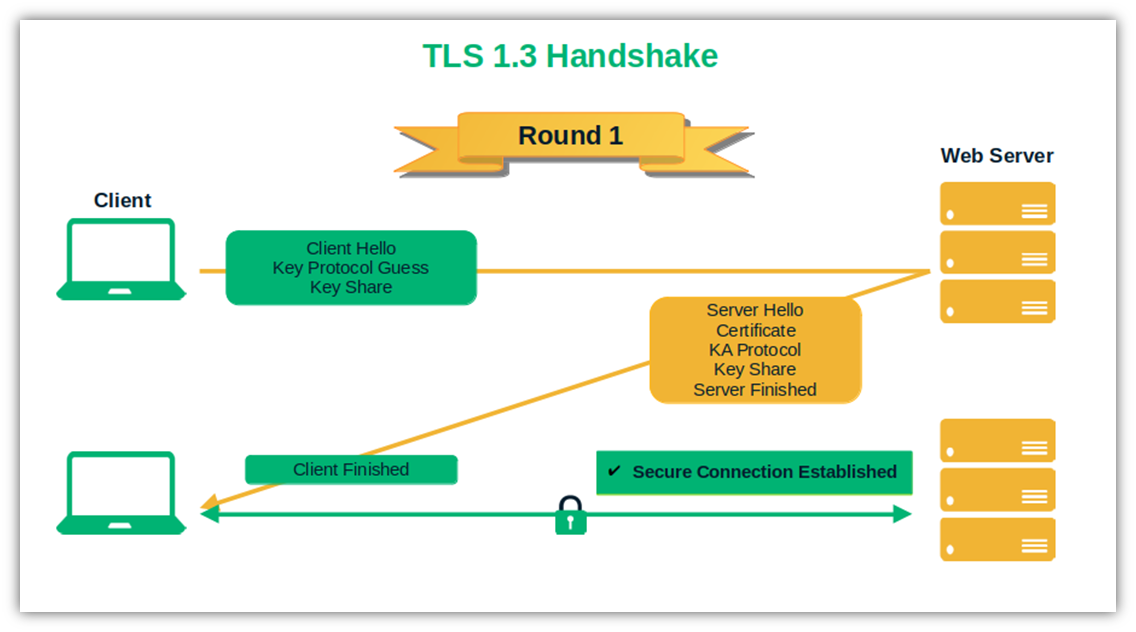
- 0-RTT Resumption. Has the client connected to the web server before? TLS 1.3 will start encrypting the exchanged data immediately, without the need for a new handshake. How? By storing the previously used session ID. Handy, right? But there’s a downside: If the stored session ID is compromised, a cybercriminal could use it to decrypt the data exchanged during the session. Bummer. Nevertheless, it’s worth mentioning it, as the issue can be limited by rotating session keys.
- Stronger encryption. TLS 1.3 supports only the strongest cipher suites and data encryption methods to further enhance its security. This makes operation modes like DES, electronic code book (ECB) and cipher block chaining (CBC) things of the past. Thus, the 37 cipher suites supported by TLS 1.2 are reduced to five in TLS 1.3. And in the case of security, fewer choices translate into fewer attack vectors.
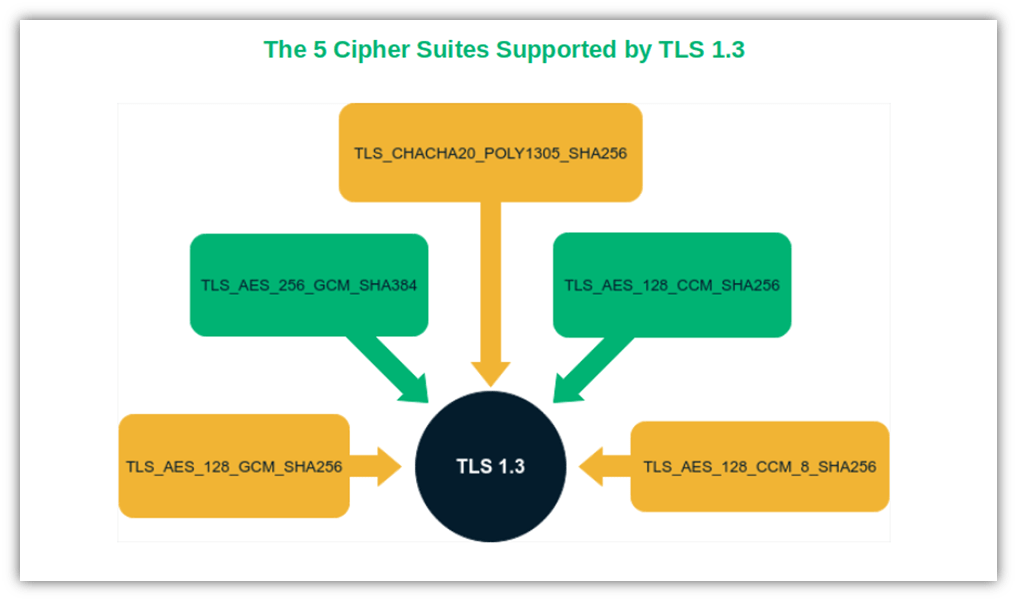
Curious to learn more about TLS? Don’t miss this Computerphile’s highly informative video:
How Can Organizations Secure Their Websites and Web Apps With TLS?
In 2022, 49% of successful data breaches were caused by stolen credentials. As we’ve learned, the transport layer security protocol can be a valid ally to prevent the bad guys from intercepting and stealing the sensitive data exchanged between clients and servers while in transit.
So, how can you implement TLS encryption to level up the security of your websites and applications?
1. Choose an SSL/TLS Certificate
If you still don’t have one, you must get an SSL/TLS certificate from a trusted certificate authority (CA). Before doing so, determine which certificate is best for you. The following table will help you pick the one that best fits your requirements and budget based on their levels of validation and what they allow you to secure:
| SSL/TLS Certificate Type | Key Benefits | Ideal For |
| Domain Validation (DV) | Cheapest certificate. Fastest validation and issuance times — issued after a simple domain check. | Informational websites (e.g., non-e-commerce and personal websites). Organizations that don’t collect sensitive data. Organizations with limited (small) budgets. |
| Organization Validation (OV) | Shipped after a basic business vetting process to confirm that your company is legit. Shows your customers that your website is owned by a real organization that a trusted third party verified. Should be used as the minimum level of digital identity validation for E-commerce websites. | E-commerce websites and registered businesses. Organizations that handle sensitive information. |
| Extended Validation (EV) | Delivered after a thorough verification process. Displays your organization’s details with a click and confirms to your clients that your website is secure. Offers greater trust and security. | Large enterprises. Companies that put customers’ security first. Organizations that want to stand out by asserting their brands’ validated digital identities. Businesses dealing with sensitive data. |
| Wildcard SSL/TLS certificates | Protects an unlimited number of subdomains with just one certificate. Simplifies certificate management. Helps save money as you won’t have to buy an individual certificate for each subdomain. | Organizations with numerous subdomains they wish to secure. Websites that don’t require higher validation. |
| Multi-Domain Certificate | Protects up to 250 domains, IP addresses, and host names with a single certificate. Available as DV, OV, and EV certificates. Simplifies and speeds up the vetting process: one certificate for all domains, one vetting process. Reduces costs and maintenance time. | Corporations and big organizations with multiple domains to secure. Organizations that want the option to implement any level of validation on their domains. |
| Multi-Domain Wildcard Certificate | Shields up to 250 different domains, IPs, and an unlimited number of their first-level sub-domains in one shot. Available as DV and OV certificates. Saves time, money, and effort. Makes SSL/TLS certificate management a child’s game. | Organizations with a complex web infrastructure that includes multiple domains and subdomains. |
Did you choose the certificate? Good. It’s time to place your order, which you can do easily through our website.
2. Wait While the CA Performs the Validation Process
Remember, SSL/TLS certificates are issued following a validation process that can be more or less complex depending on the type of certificate ordered. For example, the basic domain validation (DV) certificate can be issued in less than 5 minutes and only requires you to reply to an email sent by the CA.
On the other hand, the validation steps required to get an organization validation or an extended validation certificate are more comprehensive. But it’s worth the wait when you receive your OV or EV SSL/TLS certificate that enables you to provide digital identity verification on your domain.
Don’t worry, though. No matter which certificate you pick, you’ll get receive it in a matter of days at the latest.
3. Install Your SSL/TLS Certificate and Get Ready to Rock
Once you’ve received the certificate, the only thing left to do is to install it on your web server. The installation procedures are usually pretty similar overall, but our Knowledge Base has information about how to install a certificate on many different platforms.
That’s it. You’re now ready to boost customers’ trust in your brand (and your SEO ranking), increase conversion, and enhance the security of your brand. All this is thanks to the transport layer security protocol.
Final Thoughts on the Transport Layer Security Protocol
The TLS protocol and TLS certificates are core components of the security of any website and application. Thanks to TLS encryption and cryptographic authentication (provided via SSL/TLS certificates), you’ll ensure that all data transmitted over the network will be accessed only by authorized users.
For a secure data exchange, implement at least TLS 1.2 using a valid SSL/TLS certificate issued by a trusted CA to:
- Provide a secure customer experience,
- Protect the data exchanged from interception attacks and breaches,
- Shield your organization and customers from dangerous malware infections (by protecting data integrity), and
- Avoid your websites being flagged by major browsers as insecure.
Remember, though: Cybercriminals are constantly looking for new ways to get your sensitive data. This is why you should use TLS 1.2 as a minimum to use industry-standard security for data that transmits to and from your website and web apps.
If you can, unleash the power of perfect forward secrecy, and boost the security of your websites and applications by implementing the latest version of the protocol (TLS 1.3).



















![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-300x200.jpg)

2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security