Is Zoom Secure? Breaking Down 10 Zoom Security Issues
Serious security vulnerabilities, cyber attacks, meeting-crashers, and data leaks — these byproducts came along with Zoom’s rapid growth during the pandemic. But is Zoom secure now? Here’s what the experts have to say…
We asked several industry leaders, “is Zoom secure?” We unanimously got positive answers.
Rueben Yonatan, the CEO of GetVoIP, a company that runs a review platform for video conferencing providers, says the following:
“I will be the first to admit that in the past, Zoom had serious security issues. After the uproar that occurred when people noticed these weaknesses, Zoom moved quickly to address all the possible weak points. So, currently, yes, Zoom is secure.”
Don't make the same mistakes
Yahoo, Equifax, Home Depot,
LinkedIn, and Ericsson did!
Get our free 15-point checklist and
avoid the same costly pitfalls.
Contact details collected on InfoSec Insights may be used to send you requested information, blog update notices, and for marketing purposes. Learn more...
But then, why is there so much fuss about Zoom’s cybersecurity issues? Due to some serious allegations, many users still think Zoom is not safe. And part of this concern likely stems from the lack of response from Zoom regarding specific security-related concerns.
In this article, we’ll cover the top 10 zoom safety issues and whether the company has been able to fix them. In the next section, we’ll also go over the responses from several other industry leaders and tech experts who answered the question, “is Zoom secure?”
The Top 10 Zoom Security Issues
Let’s explore what (or were) the biggest Zoom safety issues.
1) Zoom’s End-to-End Encryption Controversies
Zoom faced criticism from the Federal Trade Commission (FTC) for its “deceptive and unfair” encryption standards and policies. Zoom told users that it provides end-to-end encryption. However, the FTC alleges that it stores its cryptographic keys on its server.
Zoom’s Response
In an April 2020 blog post, Zoom admitted that they used the “end-to-end” term in a different way. The data first goes to Zoom’s servers before it reaches to the person you’re communicating with. As a result, Zoom’s management can decrypt and view customers’ video calls and chat if they want.
On the article, Zoom admits that it stores the cryptographic keys but mentions that:
“We have implemented robust and validated internal controls to prevent unauthorized access to any content that users share during meetings, including – but not limited to – the video, audio, and chat content of those meetings. Zoom has never built a mechanism to decrypt live meetings for lawful intercept purposes, nor do we have means to insert our employees or others into meetings without being reflected in the participant list.”
Zoom added end-to-end (E2E) encryption to add an additional layer of protection to tackle this issue. This means that all data transfers will occur directly between two Zoom clients without Zoom’s server being a mediator.
It’s important to note, however, that this encryption method isn’t part of the default setting for all Zoom calls because it disables some Zoom functionalities. So, users need to enable E2E encryption manually in order to use it. Check out these instructions from Zoom to learn how to enable E2E encryption on their platform.
2) “Zoom Bombings” and Meeting Disruptions
This is one of the biggest problems which made a lot of headlines relating to Zoom security issues. Historically, anyone with a Zoom meeting link or ID could enter the meeting room and eavesdrop on an entire conversation. There were some instances where uninvited guests crashed digital meetings to display inappropriate content or make offensive gestures.
In a “Zoom bombing,” the host had little to no control of the situation. They can’t decide who can enter the meeting, suspend the user’s activities, or pause the meetings.
Basically, if such things happen, the host has no option but to end the meeting and rearrange everything — in other words:
- Reschedule the meeting with a different meeting ID or link,
- Resend new invites to all the participants so they can use the new link or meeting ID to reenter the meeting, or
- Move the meeting to another virtual conferencing platform.
Zoom’s Response
Zoom addressed the “Zoom bombing” issues by introducing the following new features:
- Creating a waiting room
- Making passwords compulsory when joining with a personal meeting ID (PMI)
- Providing the option to remove passcodes from meeting URL
- Adding lock meeting feature
- Giving the option to suspend participant activities (by pausing the meeting instead of ending it)
- Enabling meeting hosts to decide who can share the screen
- Adding two-factor authentication
- Providing various file transfer options so the host can decide what type of files participants share over chat-box.
Want to learn more about how to secure Zoom meetings? We’ve got you covered in our other article on Zoom security settings.
3) Zoom’s Inability to Play Nicely with Apple Devices
There are many iOS vulnerabilities that hackers exploited via Zoom application and targeted Apple users. A security researcher Jonathan Leitschuh showed how he could turn on participants’ webcams during calls even if they have selected the option “turn off my video when joining a meeting.” He was also able to make participants join a meeting without their permission. If hackers use such code, they can turn any Mac device into a spying machine with Zoom.
Leitschuh also said that Zoom used to download itself on Apple devices without users’ knowledge. Zoom’s installer bypassed Safari’s in-built safety settings and automatically launched itself using Mac operating system even if the user has deleted Zoom in the past.
Security researcher Felix Seele also shared his concerns about the way Zoom behaves like malware. It abuses the preinstallation scripts, unpacks itself, and auto-installs on devices without users’ consent. He also said that Zoom can give unauthorized users root access.
Mac hacker Patrick Wardle showed how local unauthorized people can secretly tamper with or replace binary codes to gain root privileges.
Zoom’s Response
Both Zoom and Apple have fixed that bug in their updates. Zoom changed its localhost web server settings, which allowed Mac users to uninstall the Zoom app manually from the menu bar. It also removed the RingCentral and Zhumu apps that were using Zoom’s technology and installing automatically onto Mac users’ devices without their knowledge. Seele also wrote a tweet saying that Zoom has fixed the auto-installation issue.
4) Zoom Data Handling Issues and Privacy Concerns
Zoom faced allegations that it shares (or sells) users’ data to Facebook.
Zoom’s Response
Zoom admitted that such data sharing happened because it gave users the option of logging into Zoom via a Facebook Software Development Kit (SDK). After that, Motherboard (the platform that discovered the data sharing in the first place) has confirmed in its article that Zoom has removed all of the codes and the Facebook SDK to prevent such sharing in the future.
However, there was another data handing issue Zoom was dealing with. On April 13, 2020, Bleeping Computer published an article mentioning that the data for more than 500,000 Zoom accounts was up for sale on the dark web. Hackers executed credential stuffing attacks to exploit Zoom’s security vulnerabilities to get this data.
And what was Zoom’s response to that? That’s a good question. I haven’t seen any response from them about it.
5) Zoom’s Vulnerability to CSRF Attacks
Zoom had a security vulnerability that could allow hackers to execute cross-site request forgery (CSRF) and crack its six-digit meeting password in just half an hour. Security researcher Tom Anthony shared how easy it is for hackers to find the right combination of Zoom meeting’s passwords using bots.
Zoom’s Response
In the same blog post, Anthony shared that Zoom took the web client offline and fixed the vulnerability. The default password no longer is six numbers; instead, it’s a combination of alphameric characters. Furthermore, Zoom has also allowed users to manually change the default password and make it more complex by adding extra characters.
6) Zoom’s Chat Box Security Issue
Bugs are a common issue with different applications and software. And Zoom’s chat function is no different. Talos, a cybersecurity firm, noticed that hackers could send malware by creating GIF files and code snippets. Another problem was, Zoom was allowing users to send any type of files in its chat box, including:
- Compressed files like .zip files,
- Untitled.html,
- Untitled.properties,
- Untitled.rtf, and
- Untitled.txt.
These file types can easily transport malicious codes and corrupt the device wherever they are stored. Zoom doesn’t validate the contents of such files.
Zoom’s Response
Despite the popularity of GIFs, Zoom decided to disable their GIPHY integration to prevent this issue. However, where file types are concerned, Zoom has left the meeting hosts to decide which file types they would like to allow participants to share in chat.
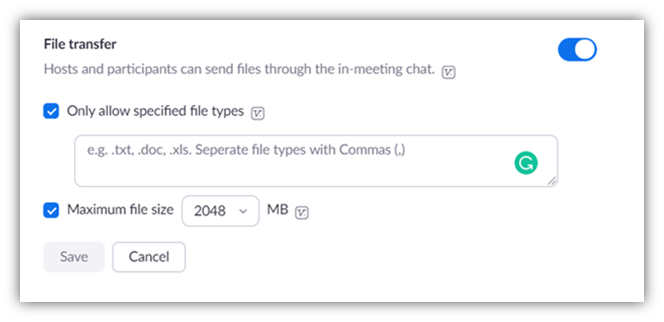
Is Zoom secure? This Zoom screenshot shows how specific types of files can still be shared through the in-meeting chat feature. This gives meeting hosts the ability to limit which file types users can share.
7) Zoom’s Vulnerability to Brute Force Attacks
In the FTC’s complaint against Zoom, the commission said that the company stores customers’ video recordings in an unencrypted format for 60 days on its servers. It means that if hackers break into Zoom’s servers and databases, they can easily access all our last two months of conversations.
Part of the issues stems from the fact that Zoom meeting recordings are easily accessible on the cloud through predictable URL patterns. This is true even after you have deleted such videos from your account. A security researcher Phil Guimond made a tool named “Zoombo” that can brute force the Zoom platform, find the password, and access any meeting recordings or enter a live meeting.
Zoom’s Response
Zoom has integrated the “Captcha” feature to patch the issue, which makes it almost impossible for Zoombo or any other bots to execute brute-force attacks. However, the structure of Zoom meeting URLs is still the same. We’re not sure whether Zoom still stores our recordings on its server — and if so, for how long.
8) Zoom’s Weak Anti-Tampering Mechanisms
Zoom’s anti-tampering mechanism has a vulnerability. All good applications have anti-tampering mechanisms to protect their systems from cyber attacks. Zoom also has one, but it’s weak. A third-year college student wrote an article on syscall.party claiming that the hacker can bypass Zoom’s anti-tampering dynamic link library (DLL).
DLL is a piece of software that consists of commands and codes. Each DLL is made to perform a specific function in the entire application. For anti-tampering, Zoom has developed DllSafeCheck.dll. In general, if a user inserts their own DLL into an application, the application’s anti-tampering mechanism either blocks it or allows only if that DLL is signed by Microsoft Authenticode. Plus, the anti-tampering DLL must also be pinned, meaning that if someone tries to replace the original DLL, the application must reject it.
However, Zoom’s DllSafeCheck.dll has vulnerability because it is not pinned and doesn’t check the authenticity of the new non-Zoom DLL. That means the hacker can not only install a malicious DLL but also disable and replace Zoom’s anti-tampering DLL itself.
Zoom’s Response
Unknown. I haven’t found a response from the company about these concerns.
9) Zoom’s Windows Security Issues
ACROS Security showed how Zoom allowed hackers to insert malicious codes into Windows users’ devices (7 or earlier versions), access them remotely, and execute arbitrary code. Unfortunately, users won’t see any security warning for such an attack.
Zoom’s patch: An article from ZDNet shares that Zoom has since fixed the vulnerability by issuing a patched version of their software.
10) Zoom Has Connections to China
The U.S. Department of Justice (DOJ) issued a warrant against Zoom’s Chinese employee Xinjiang Jin, also known as “Julien Jin,” for leaking Zoom’s users’ and meetings information to the Chinese government. Jin faced the accusation that he was:
- Supplying information such as Internet Protocol addresses, names, and email addresses – of users located outside China.
- Monitoring Zoom’s meetings and terminating any meetings that were deemed illegal or otherwise unacceptable according to the Chinese government’s rules.
- Suspending some users’ accounts who were (according to Jin) engaged in illegal activities without any proof.
Example: There was a video commemoration meeting going on for the anniversary of the 1989 Tiananmen Square massacre. Jin disrupted and censored the meeting and terminated some of the participants’ accounts. To justify his actions, he helped another person to create a fake email address and Zoom account. He asked that person to register a false complaint that the host and the participants of that meeting were involved in some terrorist and child pornography activities. Later on, these claims were proven untrue.
Zoom’s Response
Zoom fired Jin and also responded on the Zoom blog that:
“We have significantly enhanced our internal access controls. We have also ceased the sale of direct and online services in China and launched engineering hubs in the United States, India, and Singapore.”
Is Zoom Secure? Experts Weigh In
All of these Zoom safety and security issues leads us back to our original question about whether the platform is secure. So, I asked some industry leaders point blank whether they have any Zoom security concerns and “is Zoom secure?”
The overwhelming response I received is that Zoom is safe to use. Of course, I’m keeping an eye on how Zoom responds to its security vulnerabilities and will continue to test its new security features. It’s good to know that multiple industry experts are confident that Zoom is secure. But what exactly did the experts have to say about Zoom’s security? Here are some of the answers I received…
Michael Miller, CEO of VPNonline, says:
“Zoom is very secure! They’ve already made updates that countered and prevented meetings from being hijacked. The security issues that alarmed the population have been addressed and are now in the past. No further instances of security breaches have been reported. To ensure that your security is improved, I suggest you update your app regularly. This will ensure that your app is protected from new security issues.”
Yes, updating your Zoom app/client is highly important. Whenever Zoom fixes any security vulnerability, it publishes the updated version of its app. The user has a duty to install the updated version to protect themselves.
When we asked Harman Singh, director of a cybersecurity firm Cyphere, he says he’s quite impressed with the way Zoom addresses its security concerns:
“Zoom has been sufficiently and proactively accepting and working with security researchers to fix flaws in its product. They even hired some top-notch security consultants (such as Alex Stamos) from the security industry to show their seriousness towards security and privacy.”
However, there are still some security concerns that exist. Chris Parker, a digital security expert at WhatIsMyIPAddress.com, shares his concerns about Zoom phishing emails:
“One very popular Zoom scam both professional and private users should watch out for are fake Zoom invite emails. These phishing scams send emails to users telling them they’ve missed — or are about to miss — an important meeting, creating a sense of urgency and panic. They include a link to a fake website designed to mimic Zoom and encourage users to log in to register or attend the meeting.”
More savvy users will be able to notice the many red flags across these pages, such as suspicious URLs and non-functioning links. However, less experienced and older users could easily be tricked into typing in their email address and password on this unsecured site being monitored by hackers.”
Emily Andrews from RecordsFinder says she thinks that Zoom is safe but also warns us about the dangers of Zoom’s phishing scams:
“Beware of emails with typical subject lines like ‘Zoom Account,’ ‘Missed Zoom Meeting,’ ‘Check your missed conference,’ etc. Scammers use such phishing email tactics and provide link[s] to the recipients. If users click on such links, they are asked to log in with their credentials to access the video recordings or join the meeting. But these login pages are fake, and hackers steal users’ users’ credentials. Sometimes, malware gets downloaded on their system.”
Conclusion on “Is Zoom Secure?”
As you have read here, Zoom has worked aggressively to solve most of its security issues. So, it would seem that Zoom is safe to use when users know how to leverage Zoom’s safety features. As Carla Diaz, Cofounder of Broadband Search tells us:
“Zoom can be secure if you use it correctly. The reason I say “if you use it correctly” is because behaving in a safe way when using Zoom will mean your data is more likely to be safe. Doing things like password protecting meetings, using the waiting room feature to double-check participants before starting, and locking the meeting once it’s begun will all make a big difference to your security. If you behave in the right way, you’ll avoid a lot of issues.”














 (48 votes, average: 4.58 out of 5)
(48 votes, average: 4.58 out of 5)







2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security