Industry Leaders Approve the Move to a 47-Day SSL Certificate Validity Period
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate validity period reduction that will begin rolling out in March 2026.
If you’ve been around the industry over the past decade, then you’ve seen the writing on the wall: SSL/TLS certificates have been getting shorter. The industry will take the next step in shortening SSL/TLS certificate validity periods starting March 15, 2026.
As of this past Friday (April 11, 2025), the CA/Browser Forum (CABF) officially voted in favor of Ballot SC-081v3, a Sectigo-sponsored measure that will reduce the current 398-day maximum certificate validity period to no more than 47 days by March 15, 2029.
Learn why these changes are happening, when they’ll be implemented, and how you can start preparing for this transition to a shorter certificate validity period.
TL;DR: A 30-Second Overview of the Changes to the Certificate Validity Period
Got your cup of coffee ready? Good. It’s time to dive in:
- Apple’s proposed ballot was officially approved by CABF leaders on April 11, 2025.
- The current 398-day certificate validity period for SSL/TLS certificates will be reduced in three phases, starting March 15, 2026.
- The reuse period of certificates’ subject identity validation data (i.e., your organization’s business information) will also be reduced to a maximum of 398 days starting in March 2026.
- The current 398-day domain validation data reuse period for SSL/TLS certificates will decline to 10 days by 2028.
- These changes apply only to publicly trusted SSL/TLS certificates; they don’t apply to other digital certificates (e.g., code signing and document signing certificates).
When These Changes Will Roll Out
Okay, now that you know what changes will occur, it’s time to break down when they’ll happen and why.
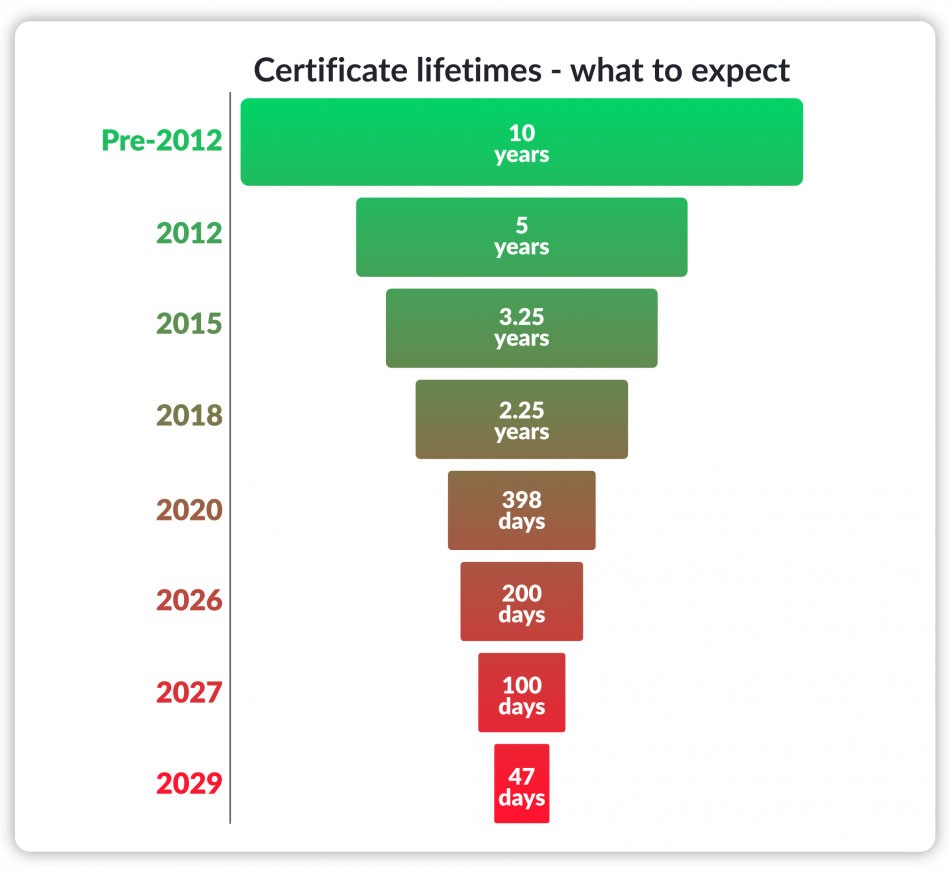
SSL/TLS Certificate Validity Periods Drop to 47 Days By 2029
- March 15, 2026: The validity period for certificates issued on/after this date will be a maximum of 200 days.
- March 15, 2027: The maximum validity for certificates issued on/after this date will be reduced to 100 days.
- March 15, 2029: Certificates issued on or after this date will have a maximum validity of no more than 47 days (or, what basically equates to 1.5 months).
Subject Data Validation Data Reuse Drops to 13 Months Starting in 2026
The current 825-day validity data reuse period will be reduced to 398 days for all organization validation (OV) and extended validation (EV) SSL/TLS certificates issued on or after March 15, 2026.
Domain Validation Data Reuse Periods Drop to 10 Days By 2029
- March 15, 2026: The maximum reuse period for domain validation data will drop to 200 days.
- March 15, 2027: The SAN-related validation data reuse period will be reduced to 100 days.
- March 15, 2029: On or after this date, domain validation data will only be reusable for up to 10 days.
Overview: Reasons for the Changes & Their Impacts on Your Company
It’s time to break down what this shift to shorter validity periods (both for certificates and their validation data) means for your team and organization as a whole.
| What Aims to Be Accomplished | Impacts on Your Organization and Team |
| Shortened certificate validity periods are thought to reduce exposure risks in the event of a key compromise | Poses an operational burden on your IT team when relying on manual certificate methods |
| Organizations will naturally shift to using reliable certificate management automation in lieu of manual methods | Automation solutions are common in enterprise environments but pose challenges and additional costs to smaller organizations |
| Addresses vulnerabilities and algorithmic changes to ensure certificates and keys are created using secure cryptographic algorithms, libraries, and components | Certificate automation ensures your organization uses the most secure cryptography without being inundated with tedious certificate management-related tasks |
| Certificates represent a moment in time, so organization validation data can become outdated or inaccurate. Shorter reuse periods help ensure certificates contain the most current information | Your organization will have to revalidate its business identity data each year (i.e., at least once every 398 days) |
| Requiring domains to be re-validated frequently helps prevent certificates from being fraudulently issued and reduces domain impersonation risks | Ultimately, you must re-validate your domain information no less than every 10 days (after the final phase has been implemented) |
If you want to learn more about the reasons why these changes are happening and the discussion that’s taken place within the CA/B Forum, be sure to check out the discussion on the CA/B Forum’s Server Cert Working Group Google Groups page.
Manage 47-Day Certificates Easily with Sectigo Certificate Manager
Manually managing hundreds or thousands of SSL certificates every month is infeasible. Sectigo Certificate Manager scales with your business and enables automation, taking the task of reissuing and renewing certificates off your plate.
Facts: Certificate Validity Periods Have Been Declining for Years
Let’s be honest: This move to shorter SSL/TLS certificate validity shouldn’t come as a surprise to anyone. The maximum validity periods have been on a downward trend for more than a decade:
- As of 2012, SSL/TLS certificates had 5-year max lifespans.
- In 2015, this was reduced to 39 months (i.e., 3.25 years) before dropping to a two-year validity in 2018.
- In 2019, Google proposed a shift to 90-day certificates, but the measure ultimately failed.
- Apple took up the cause in 2020, pushing the CA/Browser Forum (CABF) to reduce certificate validity to a maximum of 398 days.
- In early 2023, Google announced its intention to reduce SSL/TLS certificate validity to 90 days.
- Last fall (2024), Apple proposed a draft ballot (sponsored by Sectigo) that would shift to 45-day max validity for SSL/TLS certificates.
How Your Organization Can Start to Prepare Now
The good news is that these changes won’t begin rolling out until next year. However, we all know that migrating systems and changing operational processes take time. If you don’t like to wait until the last minute, then now’s the time to begin making preparations.
Implement Certificate Automation with Sectigo Certificate Manager
Sectigo offers multiple certificate automation tools to fit a wide variety of server and hosting environments, including ACME-based automation and Sectigo Certificate Manager.
SCM is more than an automation tool. This cloud-based certificate management platform provides complete visibility and control of all the PKI assets (regardless of which CAs you use) across your entire network in a single pane of glass.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security