Watch Out for These 8 Different Types of Malware
9.9 billion malware attacks were executed in 2019 alone — let’s explore what the different types of malware are and how to prevent them from affecting your organization
When it comes to knowing about the different types of malware that exist, there’s a lot to know.
Malware, short for “malicious software,” damages or exploits any device, network, software, or server that it infects. A malware author is a cybercriminal who misuses malware-laden devices to achieve financial, personal, professional, or political gains.
Although different types of malware are coded differently, you can categorize malware based on their structures, behaviors, and common traits. Each type aims to harm the infected device in a specific way.
In this article, we’ll cover the main three types of malware (viruses, worms, and trojan horses) and other five vastly used classes of malware — rootkits, keyloggers, ransomware, spyware and adware. After that, we’ll go over the most common malware insertion techniques and offer tips for how to prevent them from affecting your organization or business.
1. Computer Viruses
Much like health-related viruses, computer viruses use hosts to infect and spread to others. The case of computer viruses, though, they spread via digital formats rather than through human hosts. Computer viruses are malicious programs that hide within:
- Hardware components,
- Software,
- Operating systems,
- Browsers,
- Media files (images, video, slideshows, GIF, etc.) and
- Documents (.doc, PDF, etc.).
Once the user downloads and activates the malicious program, the virus activates and corrupts the device. Viruses replicate themselves, alter the infected devices’ program codes, and gain unauthorized control over the devices’ hardware and software components. Computer viruses have many different structures and are useful in a variety of cybercrimes. According to Accenture, the average cost of cybercrime was $13 million as of 2018.
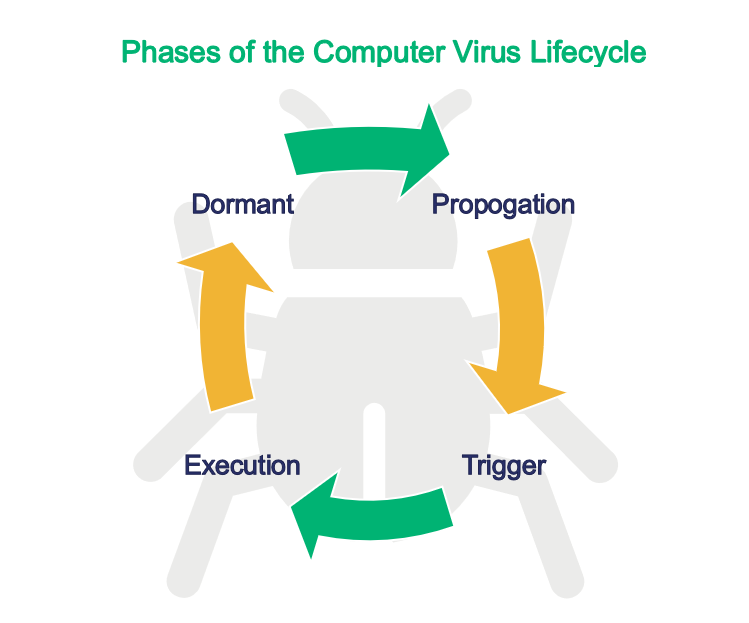
What Is the Lifecycle of a Computer Virus?
When a virus inserts itself in a user’s device, it stays dormant. It needs a trigger (i.e., a manual action performed by the host) to activate. Usually, the triggers can be activating the software, opening the infected files/media, enabling the macro, etc.
Once active, the virus starts to search for other locations to replicate itself, such as on software, hard drives and removeable hardware like memory cards and USB drives. It changes the original settings and codes of computer programs. Finally, it releases its payload. The payload is the core code that enables the virus to do what it was created to do.
There are many reasons why a cybercriminal might choose to create a virus. They can use them to:
- Crash the hardware or operating system of a targeted device.
- Compromise the system.
- Display large number of unwanted popups.
- Access the targeted user’s contact lists and email contacts.
Quick Facts about Computer Viruses
- Some viruses encrypt themselves using mathematical algorithms. Hence, the antivirus programs can’t inspect and read the codes inside the virus-containing software.
- The antivirus programs search for some well-known strings of codes to detect the virus. These codes are also known as a “virus signature.” But some viruses are so well-written that they rewrite themselves and change their codes after each infection. This makes it difficult for antivirus programs to trace the virus due to lack of similar pattern of strings. We’ll speak more to that later.
- Some new generation viruses use advanced artificial intelligence (AI) to read the requests of the user. When the user starts scanning their device, the virus makes another copy of the original file and sends only the non-infected copy of the file to the antivirus scanning, retaining the infected file hidden.
2. Trojan Horses
A trojan horse is a type of malware that poses as legitimate software and tricks users into installing it. The trojan writers either insert the malicious codes in legitimate software/files or develop malicious software that’s deceptively similar to legit programs. There are many ways that users are tricked into installing trojans on their systems. For example:
- Upgrades: When users try to access some content online, the infected website restricts the content and asks users to update a software, application, browser, media player, etc. to its latest version. But when users click on the provided links, trojans install on the users’ devices along with the upgraded software.
- Media files: The perpetrators provide links in the phishing emails or malicious sites to download free images, mp3 files, games, slideshows, or videos. But when users try to download them, either a trojan-infected version or a completely different program downloads in the users’ devices instead.
- Email attachments: The attackers send phishing emails with the trojan infected attachments.
Trojans can’t replicate themselves, and hence, they stay local — in the program/file in which they were originally stored. However, nowadays, there are hybrid malware available in the market that combine a trojan with a virus or worm. Viruses and worms provide a replication capability to the trojan. As a result, its power of destruction multiplies.
7 Types of Trojans
1. Ransomware Trojans
These types of trojans encrypt, corrupt, modify, copy, lock, and delete data. They hold the data in the users’ system as a hostage and release it after the user pays the ransom.
2. Mail-Finder Trojans
These types of trojans are tasked with finding all the email contacts from their targets’ email clients. The trojans can send the lists to their creators. In some cases, they self-propagate by forwarding themselves via phishing emails to these contacts from the victims’ email clients without their knowledge.
3. Fake Antivirus Trojans
Such trojans send fake messages to the user, informing them that their device is infected with the viruses. They sometimes use sophisticated reports and scan results, showing a high threat level to generate panic in users. Then the trojan author charges users for virus removal services.
4. Downloader Trojans
These types of trojans are somewhat self explanatory. Their purpose is to download other malicious software from the internet without the device owner’s knowledge.
5. Botnet Trojans
Botnet trojans are used to corrupt web browsers, infect other devices to force them to join the botnet army, and to execute various cybercrimes.
6. Backdoor/Remote Access Trojans
These trojans give remote access of their invaded devices to the cybercriminals who control them. For example, a trojan author can:
- Access and modify files,
- Reboot their targets’ systems,
- Install or uninstall other software,
- Send and receive information with other connected IoT devices, and
- Get many other similar privileges.
7. Spyware Trojans
Also known as spyware, these trojans monitor users’ actions such as the internet surfing behavior and things users type on the website and devices (such as personal information, financial data, login credentials, etc.). Later on, such information is used to execute identity theft crimes, financial frauds, or ransomware attacks.
3. Computer Worms
Worms are types of malware that can self-replicate and spread rapidly to other connected devices, files, and software. As such, this means that a worm is a standalone computer program that’s highly contagious! Unlike viruses, which need a trigger to activate, worms are autonomous and can start replicating themselves as soon as they get inserted in the users’ devices. They don’t require user action to activate.
Basic worms use excess bandwidth and resources of the host device, which makes it slow or dysfunctional. It also depletes the RAM and internal memory of the device and overloads the shared internet network. But to make matters worse, many modern worms are often paired with other types of malware such as trojan and viruses. These hybrid worms have the capacity to:
- Give remote access to its author,
- Encrypt files,
- Send spam and phishing emails,
- Download malware from the internet,
- Delete the files, and
- Do much more harm to the host devices with lightning speed.
The combination of worm and trojan is used for executing
- Botnet attacks,
- Man-in-the-browser attacks,
- Brute-force attacks,
- DDoS attacks
Worms are ideal for any cyber-attacks that need the participation of a group of a large number of infected devices.
4. Rootkits
A rootkit is a type of computer program that enables the perpetrators to get unauthorized access to the files/software without any required credentials. Some core components of the software need user authentication to access them, such as:
- Passwords,
- One-time passwords (OTPs),
- Secret codes,
- Security questions.
However, when the rootkit is installed on the user’s device, it corrupts the system (both hardware and software) in such a way that its author can bypass the authentication procedure and get the administrative rights without the user’s knowledge.
Although some antivirus programs can detect the rootkit, it’s still difficult to remove it once it’s inserted inside the core components of the device. If it is stored in the kernel, you need to reinstall the entire operating system to get rid of it. If a rootkit is hidden in any hardware (also known as firmware rootkit), you must replace that entire hardware component to remove it.
5. Keyloggers
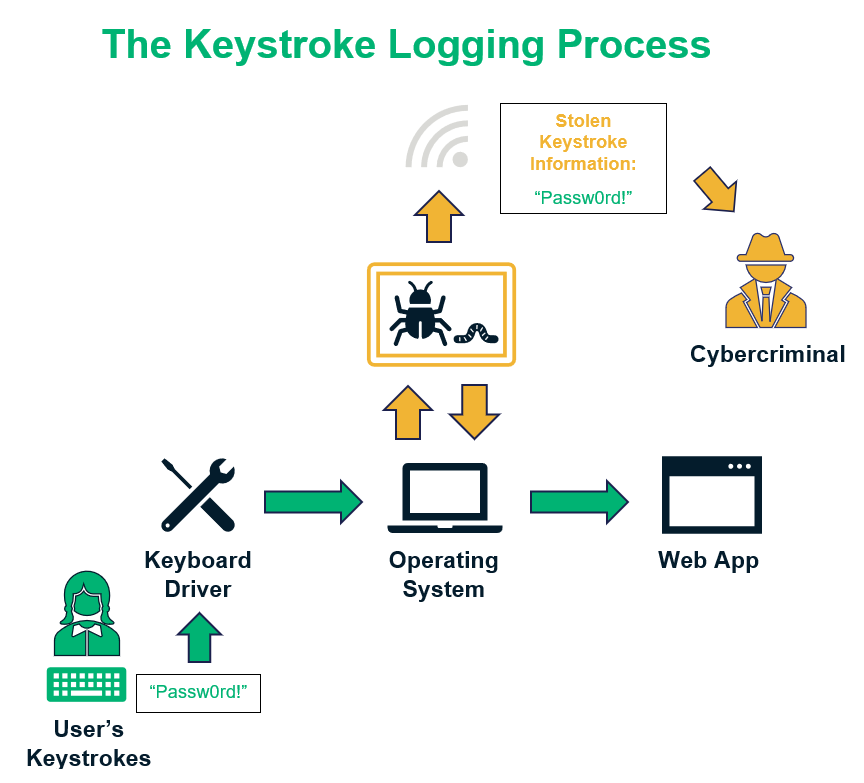
The term “keylogger” refers to a type of software or hardware-based program that monitors the keyboard activities of the user. Whenever you press a button on your keyboard, you’re creating a keystroke. This is how you communicate with your device. Keylogger programs keep logs of every keystroke you make (hence the name keylogger).
Software-based keyloggers hide themselves inside operating systems, kernel-level programs, running applications, and the web browsers of infected devices. While they’re not a threat to computers or other devices, they are a threat to the people and organizations who use them because of the types of information they steal.
It may surprise you to learn that keylogging isn’t actually illegal in all cases. For example, some organizations choose to use keyloggers to track their employees’ work. However, keyloggers fall into the malware category when they’re installed on users’ devices with the purpose of eavesdropping and stealing their information.
Some other types of malware — some varieties of worms, viruses, and trojans — also have keystroke logging capabilities. Users are tricked into downloading software in which keyloggers are hidden. Once installed and activated, keyloggers track and record users’ keystrokes.
What Keyloggers Steal
Cybercriminals use these tools to steal personally identifiable information (PII), financial data, passwords, personal communication, and even the media files. They can use it to carry out:
- Identity theft: This type of crime includes opening a bank account, taking loans, filing the tax return, etc. while using someone else’s name.
- Financial fraud: This type of fraud includes misusing payment card and bank information for unauthorized fund transfers.
- Ransomware attacks: A ransomware attack occurs when a cybercriminal threatens to broadcast or delete the data of a person or organization if they don’t pay a ransom.
Sometimes, the attackers collect the user’s personal data and sell it to the dark markets.
6. Ransomware
Ransomware is one of those types of malware that holds a target’s data hostage. For the victim to regain access to their documents, images, videos, and other important data, they must first pay a specified amount (often in cryptocurrencies).
In general, the ransomware encrypts the data with cryptographic keys, and no one can access such encrypted data without a corresponding key. Sometimes, the ransomware locks or shuts down the entire system, and its author demands extortion money to restart the system.
Ransomware can target websites as well. Here, attackers lock down all of the website’s files, databases, and even backups, effectively locking out the site owner. This is where website and data backup products like CodeGuard can be a lifesaver— CodeGuard automatically stores your backups in a third-party cloud platform and scan each backup for malware before storing it.
Ransomware is distributed as trojans or computer worms via phishing emails or malicious websites.
7. Spyware
As the name indicates, this type of malware eavesdrops on the victim’s actions without their knowledge and consent. Spyware is a broad term that includes any types of malware (trojans, keyloggers, tracking cookies, etc.) that spy on users.
Spyware steals the user’s:
- personal and professional information,
- login credentials,
- payment card numbers,
- contact lists,
- bank information,
- information about other connected devices,
- vulnerabilities in the user’s system, etc.
It can also monitor the victim’s browsing behavior.
When inserted into a corporate network or government website, spyware can eavesdrop and leak confidential data, military information, trade secrets, technical know-how, and all other types of sensitive information.
Cybercriminals misuse such information for identity theft, financial fraud, blackmailing, or causing political unrest. They also tend to sell such information in the dark market to other cybercriminals.
8. Adware
Advertising-supported software, commonly known as adware, display advertisements on users’ devices when they browse the internet or use an application/software. Some software publishers provide software for free or at a lower rate and recover the development and upgradation cost from advertisements.
It’s legal to publish software bundled with adware that tracks users’ geographical locations and displays the advertisements accordingly, to generate “pay-per-click” revenue for the developers. However, adware is considered a type of malware when it’s designed to:
- Generate unwanted popups with “unclosable” windows,
- Track the user’s actions, and
- Steal data such as users’ personal information or login credentials.
Sometimes, viruses or worms are integrated into the adware that execute various cybercrimes.
Modern Malware Presents a Changing Threat
All the different types of malware we’ve talked about evolve over time as their authors make changes. However, there are types of malware that change themselves to evade detection. Polymorphic and metamorphic malwareare the types of malware that can of change their signature patterns and codes with each insertion. But how big of a threat are these types of malware? Webroot reports that “94% of malicious executables are polymorphic.”
What differentiates these two types of malware?
- Polymorphic malware changes parts of its coding while retaining a portion of the main code. This makes it trackable by certain types of anti-malware programs but virtually undetectable by traditional pattern-matching cybersecurity tools.
- Metamorphic malware, on the other hand, is an advanced type of malware that can reinvent itself. It changes all of its code after each iteration, making it untraceable by security software.
4 Ways to Prevent Malware from Infecting Your IT Systems
We have seen how different types of malware can exploit your system to steal, corrupt, block, and encrypt the data. Now, let’s explore how cyber attackers distribute and insert this malware into your device so you can understand how to prevent malware attacks.
Importance of security software: Before we start, I want to point out that robust security software can detect and remove most of the common types of malware. Software like antivirus, antimalware, anti-spyware, and firewalls are necessary to get protection against common and well-known malware. Although the security software struggle to detect some advanced level malware, they can at least draw your attention to and alert you when anything suspicious downloads onto your device, or you are visiting an infected site.
1) Keep Your Software Patched and Up to Date
Whenever software publishers find and fix software vulnerabilities, they release the updated versions of the software. Cybercriminals are always looking for devices that are still using unpatched or legacy systems in order to exploit their vulnerabilities. In other words, vulnerabilities in the old versions are like the cracks hackers use as entry points to insert malware into your system.
Prevention: As soon as you get an update notification for the operating system, browsers, or any type of software program you are using, install the updated version without any further delay.
2) Teach Your Employees How to Identify Phishing Emails
Phishing scams involve perpetrators sending unsolicited emails while impersonating someone else. They hide malware in such emails or redirect recipients to malicious websites.
Phishing emails and their attachments are designed to look benign and like they’re coming from legitimate people and companies. For example, a phishing email may look like an email from your colleague or HR that asks for some confidential information about business or attached a file. But in reality, these types of emails are from cybercriminals, and their attachments generally contain various types of malware.
Sometimes, the bad guy sends malicious links in the emails with deceiving text to trick users into clicking on them. When unsuspected users click on such link, malware automatically downloads onto the user’s device without their knowledge.
Prevention: Always check the sender’s email address. It must be from the company’s official email address and contain the domain name after the “@” symbol. For example, if the email is coming from Amazon, the sender’s email address must contain “@amazon.com.” Never download anything from the unsolicited emails, but if you must, at least scan the attachment with an antimalware software before downloading.
3) Beware of Spammy and Malicious Websites
Hackers make some sites with the purpose of distributing malware or tricking users into sharing their confidential information. While some websites belong to legitimate businesses, but hackers have inserted the malware in their links, media, or forms without the website owner’s knowledge. Whenever the users download anything from such website or click on the infected link, the malware gets installed on their system.
Prevention: Whenever you download something from the internet, especially free software, songs, videos, images, files, etc., scan it with a robust antivirus or antimalware program. Also, you should regularly check your downloads and C:/Program Files and C:/Program Files (x86) folders. Generally, the new software stores automatically in these locations. If you find any unknown software, investigate it and remove it if it doesn’t serve any purpose.
4) Regularly Scan Hardware and IoT devices
Attackers infect the hardware components such as thumb drives, memory cards, USBs, CDs, DVDs, etc. Whenever a user plugs infected hardware into their device, the malware inserts itself onto it.
Prevention: Always scan all the above-mentioned tools with strong security software immediately after plugging them to your device.
Final Thoughts on the Different Types of Malware and How to Prevent Them
Malware authors are every day coming up with smart and innovative ways to develop various types of malware. Although the security software makers are doing their best to catch up with the advanced malware, you also must be vigilant enough while surfing online and downloading anything from the internet.
If you become a victim of any cybercrime, or if you suspect your device is compromised, immediately take the necessary steps to get the system cleaned up by the professionals or report the issue to the relevant authorities. Don’t hesitate to contact your local police, Federal Trade Commission or the US-CERT to register your complaint. You can also report malware inserted websites to Google.














 (41 votes, average: 4.66 out of 5)
(41 votes, average: 4.66 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security