A Man in the Browser Attack: What It Is & How to Prevent It
No individuals, small companies, or big organizations are immune to man-in-the-browser (MitB) attacks — Here’s what to know about what these cyber attacks are, how they work, and what you can do to prevent them
Let’s imagine this scenario to understand the man-in-the-browser attack in layman’s terms:
Bob finds a shirt that he likes for $20 on Amazon.com. He hits the Proceed to check out button, reviews the order summary, selects two-day shipping, and makes the payment. He receives the confirmation receipt showing details of the shirt, price, shipping address, and expected delivery date. But when he doesn’t receive the shirt within a couple of days, Bob logs in to his Amazon account to see the shipping status. Much to his surprise, there isn’t any record of the transaction!
Realizing that something fishy is going on, he immediately checks his bank statements and finds a charge of $2,000 instead of $20 for the transaction made on the same day and from the same ecommerce site (Amazon)! Bob knows that it’s unlikely that a well-known ecommerce site like Amazon would commit fraud. So, what just happened? It’s then that Bob realizes that he has become the victim of a man-in-the-browser attack!
In this article, we’ll explore what a man-in-the-browser is, execution, and some tips to prevent them.
What is a Man in the Browser Attack?
A man-in-the-browser (MitB) attack occurs when an attacker inserts a special type of trojan horse into the users’ web browser via a
- Browser Extension,
- User script, or
- Browser Helper Object (BHO).
This allows an attacker to exploit the browser’s security vulnerability. It enables hackers to read, intercept, steal, and modify the actions performed on the browser.
This MitB trojan can control the browser in one or more of the following ways:
- Adding new columns/fields on the website or modifying the existing fields.
- Modifying the transaction information entered by the users. This data can be a transaction amount, bank account number, physical address, etc.
- Hijacking the entire transaction in real-time.
- Changing the appearance of the website.
- Modifying the servers’ responses, such as confirmation messages and receipts.
- Intercepting the data entered by the user on the website.
- Removing the transaction details when the user revisits the website.
The user and the website’s server don’t have any knowledge of such modifications until it’s too late. Man-in-the-browser attacks can defraud even the most vigilant users and are immune to some well-known security mechanisms like secure SSL/TLS certificates and two-factor authentication.
Unlike the phishing attacks where users are tricked into entering their credentials on a fake site, in the MitB attacks, users perform all the actions on the legitimate site. Hence, no authentication step has been bypassed. MitB trojan modifies the data before it gets encrypted.
How Man-in-the-Browser Attacks Are Executed
Although man-in-the-browser attacks are conducted in various ways, the following hacking technique is the most common among all. Let’s understand the entire man-in-the-browser process in 10 steps.
Phase 1: Malware Insertion
- The trojan horse gets inserted in the device’s operating system when the user:
- downloads a corrupted software,
- visits any malicious site,
- opens or downloads malicious email attachments, or
- plugs corrupted external devices such as USB drives/CDs on their computers/tablets/mobile phones.
- The trojan automatically installs a malicious extension in the web browser without the user’s knowledge.
- Whenever the user restarts the browser, the extension gets activated.
- The malicious extension has a list of targeted websites which it can manipulate. Whenever the user opens a website from the list, the trojan does multiple tricks to modify the targeted webpages. For example, changing the fields of the forms or inserting JavaScript on the buttons like Submit, Done, Send, Transfer, Complete, etc.
Phase 2: Transaction Interruption
- The unsuspecting user logs in with their credentials (their user ID, email address, password, one-time password [OTP], secret pins, etc). Then, they complete the regular transaction such as transferring funds, making payments, purchasing, or filling out sensitive details such as SSN, health info, etc.
- When the user clicks Submit or any other authorization button, the malicious script modifies the transaction details. For example, changing the transaction amount, bank numbers, physical address, product, etc. and sends the modified information to the website’s server. (Note: The information is modified before it enters the encrypted channel facilitated by the SSL/TLS certificates.)
- The recipient website doesn’t suspect anything about the modified transaction because it’s coming directly from the user without bypassing any authentication step. Hence, the website completes the requested transaction.
Phase 3: Response Modification
- The website sends the receipt to the user. The receipt contains the transaction details.
- The corrupted browser modifies the receipts that match the details of the users’ original transaction.
- At this stage, even if the two-factor authentication (2FA) is activated, the user doesn’t have anything to suspect in the confirmation receipt. Hence, they provide the unique secret code or OTP, which they generally receive on the mobile or email to complete the transaction.
As you can see, both the user and the website are acting in good faith. The website has followed only the instructions that it received from the user. The user experiences a seamless transaction where the confirmation receipt reflects the same transaction details that they’d expect, so they’re not likely to assume that something is amiss.
Where MitB Attacks Are Most Commonly Used
In general, the man-in-the-browser attacks target websites where users perform any sort of transaction. For example,
- Websites belonging to the financial industry: banks, insurance, credit card, mortgage companies, etc.
- Ecommerce websites
- Utility services’ websites that facilitate users to pay bills on their platforms. For example, electricity, gas, internet, cable, etc.
- Websites offering paid membership/ subscriptions
- Websites having fundraising, donation, or charity facilities
- Online wallets
- Social media websites
- Websites that facilitate tax calculations and filing
However, the scope is not limited to the transactions only. The man-in-the-browser attacks are also used to steal the data. Here, the perpetrator steals data from the legit website’s form or login pages. Forms can be inquiry forms or contact forms. They can also add new fields such as social security numbers, phone numbers, bank account numbers, etc. in the existing forms, too. Needless to say, all the data filled by the user in such forms are instantly received by the hackers.
Hackers also execute man-in-the-browser attacks against the company’s internal website or project management websites, which employees use to store and share confidential data.
Popular Trojans Used for Man-in-the-Browser Attacks
These are some famous widespread trojans used for MitB attacks:
1. Zeus
Zeus is a widely spread trojan that man-in-the-browsers use for keystroke logging (recording user’s keyboard activity to monitor actions) and form grabbing (stealing login credentials from online forms). It gets installed on the user’s device via phishing emails or malicious software downloads.
Zeus is considered to be the most dangerous trojan as it has successfully hacked FTP accounts of well-known websites such as play.com, Amazon.com, Bank of America, United States Department of Transportation (US DOT), Cisco, NASA, BusinessWeek, ABC and Monster.com.
The Zeus trojan is used by scam artists to steal banking credentials and make unauthorized fund transfers. It also executes technical support scams by inserting a fake pop-up message on the website the user is visiting. The pop-up warns a user that their system is infected with the virus and defraud them by charging for virus removal.
2. Carberp
This trojan gets installed in the following locations:
- /ProgramFiles\NVIDIA Corporation\Updates
- /ProgramFiles\NVIDIA Corporation\Update Center
It can connect to some remote sites, check internet connection, download other malware from the internet, and run files.
One of the Carberp trojan’s most notable targets is Facebook. It infected some users’ Firefox and Internet Explorer browsers. When users used one of these corrupt browser to open Facebook, it replaced the pages the users visited with fake ones. It asked for users’ cash equivalent e-cash voucher number to defraud them.
3. OddJob
This trojan is designed to execute man-in-the-browser attacks against the banking website. It gets installed in Firefox or Internet Explorer and gets activated when the user opens a banking site. It keeps the banking session open even after the user has logged out of their account. This allows an attacker to steal the legitimate user’s real-time session ID tokens to do banking transactions on their behalf.
The most dangerous thing about this trojan is that it doesn’t get stored on the device’s disk. Hence, the anti-malware software can’t detect it. It operates directly from the command-and-control server. Every time the user opens the banking site, a new trojan gets installed and deletes itself after the transaction is complete.
4. Tatanga
Tatanga is a banking trojan that is so powerful that it bypasses the mobile’s SMS authentication to complete the fraudulent financial transaction. Unlike the aforementioned trojans that affect only Internet Explorer or Firefox, Tatanga affects all of the major browsers, including IE, Firefox, Chrome, Opera, Safari, Maxthon, Netscape, and Konqueror.
Tips to Prevent Man-in-the-Browser Attacks
Although the trojans used for man-in-the-browser attacks are evolving every single day, you can prevent them by being vigilant and with the use of some technological tools. These are five technologies or processes you can implement to prevent MitB attacks:
1. Out-of-Band Authentication
In this method, the browser is not used for two-factor or sometimes multi-factor authorization (MFA). Instead, a mobile phone’s SMS facility or an automated phone call is used to deliver the one-time password (OTP) or the secret pin.
The SMS or phone call contains all the information about the transaction along with the OPT. But the user must be vigilant and check all the information received on the SMS/phone call before submitting the OTP to the browser. However, you can’t rely on this method 100% because trojans like Tatanga, Zeus and SpyEye can corrupt the mobiles and intercept all the incoming SMS messages, too.
2. Manual Checking of Your Program Files
Some of the common man in the browser trojans have a similar storage pattern. Be sure to regularly check the following folders:
Paths:
C:/Program File
C:/Program Files (x86)
C:/Windows/Temp
If you detect any unauthorized new software, scan it with anti-malware software and conduct an internet search to get more information about it. If you find anything suspicious, remove such unknown software.
3. Use Security Software
Antivirus software can detect and remove some of the man-in-the-browser trojans. Regularly scan your devices with the antivirus software. Some of the antiviruses also show you the security dialogue box if it finds anything suspicious getting downloaded from the internet. However, antivirus software can’t prevent all the latest trojans. There is some browser security software available, too.
These five solutions claim to prevent MitB attacks:
- Mimecast: Detects and blocks MitB trojans distributed via emails.
- BullGuard: No plugin, extension, or BHO can get installed without the user’s notice as BullGuard alerts the user every time anything new has been added in the browser.
- IBM Trusteer Rapport: This endpoint protection solutions prevents malware and phishing attacks.
- Entrust: It has two solutions, Entrust TransactionGuard and Entrust IdentityGuard, that enable multi-factor authentication like OOB to prevent man-in-the-browser attacks.
- CodeSealers: It is a user interface (UI) protection software that provides protection against man-in-the-browser and MitM attacks.
4. Be Vigilant While Surfing on an Unknown Website
Be careful while downloading any software or media files such as songs, images, and videos from unknown sites. Always scan the downloaded files with a robust antivirus program.
If you suspect any links or buttons, right-click on them and hit Inspect. You’ll see a window with a bunch of codes in which you can see where exactly the link/button is redirecting you to.
Never click on the links or advertisements that look too good to be true. For example, advertisements like winning the big lottery, casino prices, making thousands of dollars while working from home, etc.
If you’re surfing an unknown website that asks you to update browser, software, or media player, never download from the link provided by those websites. If you’re using an outdated version, go to that browser/software’s official site and download the updated version directly from there.
5. Beware Phishing Emails
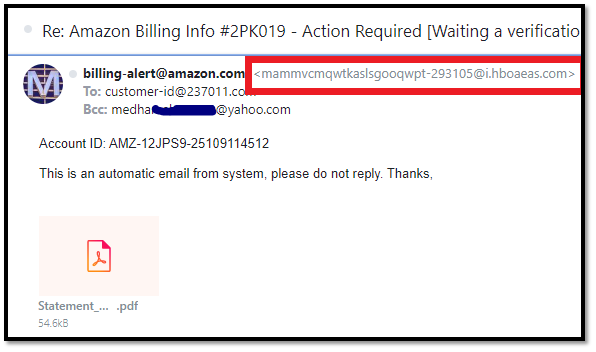
One of the most popular ways of distributing the man-in-the-browser trojan is via phishing emails. That’s why always check the email headers and the sender’s email address to ensure emails are sent from the official company’s domain name. For example, if you get an email claiming to be from Amazon, it must be from an email address that ends in “@amazon.com” instead of Gmail, Yahoo, or any other generic email address.
Don’t download any attachments from emails before having them scanned through reliable antivirus software. Before clicking on a link from an email, hover over cursor on the link and check where it actually points to.
Phishing email example:
Detection Challenges Relating to Man in the Browser Attacks
A man in the browser attack is considered one of the most difficult cyber attacks to detect and prevent. So, let’s understand why, exactly, it’s earned such a bad reputation.
Detection Challenges for Users
In the regular phishing attacks, the attackers redirect users to a website that looks similar to the original site and trick users to submit their information. Here, the users still get a chance to detect the fraud as the domain name is going to be different. But in the man-in-the-browser attacks, the users are visiting the original website only. They don’t have any reason to be suspicious and to detect the attack.
Detection Challenges for Website Servers
All good websites use robust technology such as enabling two-factor authentication, enforcing users to set strong passwords, limiting login attempts, enabling re-captcha, etc. They even send mobile/email alerts to the user if there is a suspicious login attempt from a new device or geographical location. These steps help the servers to detect and prevent brute force attacks and unauthorized access to the users’ account.
However, in man in the browser attacks, users themselves are logging in with their original credentials and completing the authentication process. Hence, the server has nothing to be suspicious about, and they can’t detect the attack.
Detection Challenges for SSL/TLS Certificate
In layman’s terms, an SSL/TLS certificate’s job is to securely communicate data between the browser and the website’s server. It uses public key infrastructure (PKI) technology, up to 256-bits AES, RSA or ECC algorithm to encrypt the session key and up to 2048 bit strong public and private key to protect the data in transit. But the SSL certificate’s protection is offered on the network side, while the man-in-the-browser attacks are executed on the application side. The trojan modifies the data on the browser level, even before the data transmits through the encrypted SSL/TLS communication tunnel.
Consider this scenario: A food delivery person’s job is to take food from the restaurant and safely delivers it to the stipulated address. But what if the restaurant manager hands over him a wrong food parcel or a wrong delivery address? In the same way, the SSL/TLS can’t prevent the man-in-the-browser attacks because the data is already modified before it is handed over to the SSL/TLS technology’s encrypted tunnel.
Final Words on MitB Attacks
Man in the browser attacks are committed against individuals and organizations. While medium and big organizations can afford to buy expensive security solutions, many small businesses don’t have extensive IT and security budgets. Small businesses must provide cybersecurity training to their employees to help them recognize phishing scams. There are many free or inexpensive training tutorials available for this purpose — for example, the DoD cyber awareness challenge.
The most challenging aspect of man in the browser attacks is the time gap. Most users don’t initially notice anything suspicious after the fraud has taken place. It usually takes a long time when users check their bank statements or to contact the website’s customer care for non-receipt of the ordered items. This gives cybercriminals enough time to eliminate the evidence of their MiB attacks and transfer the funds to the foreign bank account or cash the money and close the bank account. Hence why you must regularly check your bank statements or ecommerce accounts to detect such attacks in their earliest stages.














 (15 votes, average: 4.53 out of 5)
(15 votes, average: 4.53 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security