7 Different Types of Malware Attacks to Look Out For
What is a malware attack? And how to protect your devices from it?
Malware, a portmanteau of “malicious software,” is any malicious code, scripts, or software that’s developed to gain unauthorized access to your data, network, devices, or other IT systems. Any cyberattack deployed using malicious code is known as a malware attack.
Google reports that it finds hundreds of malware-infected sites each week!
All types of malware have different structures and behavior. Popular malware types are computer viruses, worms, trojan horses, adware, rootkits, etc.
In this article, we’ll help you familiarize yourself with seven of the most common and highly dangerous types of malware attacks.
7 Common Types of Malware Attacks
1. Ransomware Attacks
A ransomware attack involves blackmailing the victims. The attacker inserts malware into a user’s device that can lock and encrypt the files, folders, applications, software, servers, or the entire device. The attacker demands a ransom from the victim in order to decrypt the data, restore the system, or reopen the applications.
Generally, an attacker uses public key infrastructure (PKI) technology and encrypts the data with a cryptographical key. The data can’t be unlocked without a corresponding private key. Only after a victim pays extortion money, the hacker provide a private key to decrypt the data. (However, in some cases, the hacker won’t ever provide a key. They’ll simply take off with the extortion money, which is frequently paid using cryptocurrencies.)
Sometimes the attacker threatens the victims to leak their personal/sensitive data or confidential files if they don’t agree to pay the ransom. Emsisoft estimates that ransomware costs could reach nearly $1.4 billion in 2020 alone.
Check out the example of a message for the Wana Decrypt0r 2.0 ransomware attack:
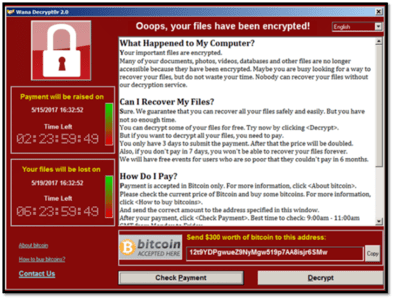
2. Spyware Attacks
For this type of malware attack, a special type of malware known as spyware is installed on a victim’s device. Just like ransomware, spyware can also read, interpret, encrypt, and remove data. Spyware can also monitor user activities, take screenshots, record the user’s browsing behavior, and send all the collected data back to the hacker.
“Spyware attack” is a broad term that includes ransomware attacks. But not spyware attacks are deployed to get the extortion money from the victim. Some spyware attacks are used for espionage, to gain key political and military-related information, or to steal scientific research data or schematics.
Sometimes, spyware attacks are deployed against an organization to steal data on:
- Trade secrets,
- Technical data,
- Future marketing strategies,
- Key stakeholders, and
- Other types of confidential information.
The spyware author (hacker) might also collect confidential information from the user’s device and sell it on the dark web.
Attackers can also use spyware to steal the payment card numbers, bank account details, passwords, social security numbers, or other useful information from victims’ devices. They can use this information to carry out financial fraud scams or identity theft.
3. Malvertising Attacks
Malvertising is another type of malware attack where the attacker hides malicious codes inside seemingly innocuous digital advertisements. Hackers rent the space for the advertisement on legitimate websites and hide the malware in the ads. They might use the popular third-party ad distributors (like Google Adwords, Zedo, AdButler, AdPlugg, Propeller Ads, etc.) or directly contact the websites and put ads by themselves.
The ads might look like regular product/service ads or show something that lures the victims to click on the ad immediately.
A few examples of such ads include
- An unbelievable deal or discount on a product,
- Gossip news article,
- “Work from home” jobs with a big salary,
- Some interesting online games,
- Dangerous virus infections.
When people click on such ads, the malware gets inserted in the users’ devices. Some of the pre-click malvertising are hiding drive-by malware. When a victim visits a corrupted site, the malware gets downloaded in their device even if they don’t click on the advertisements.
Antivirus software generally alerts users when they are visiting a spammy website. But in this case, they won’t warn you because malvertisements are often posted on legitimate websites.
In general, the malware gets inserted in the user’s device only if they click on a malicious advertisement. These types of malvertisements are known as post-click malvertisements. However, nowadays, hackers have developed pre-click malvertisements that download the malware as soon as the user visits the landing page of a spammy website. In other words, malware can enter your device without any interaction on your part.
Here’s an example of a malvertising attack that involved Microsoft games. A Microsoft Community forums poster (bhringer) shared the following fake virus warning popup (see below). When users would click on the given link, a potentially unwanted application (PUA) would download onto their devices.
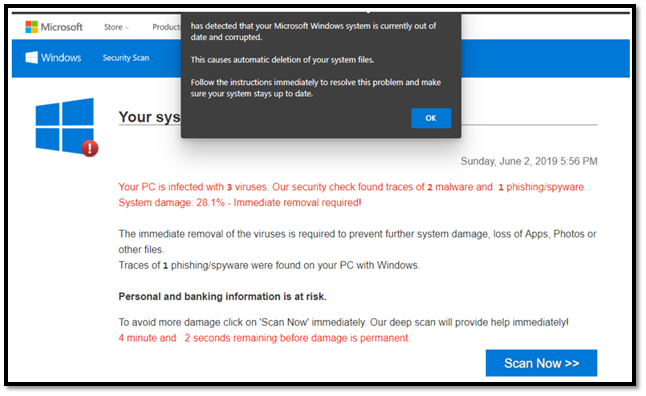
4. Man-in-the-Browser Attacks
A man-in-the-browser (MitM) attack is a nasty thing. In this type of malware attack, the attacker inserts a trojan horse into the web browsers via extensions, scripts, or browser helper object (BHO). A man-in-the-browser trojan (MitB trojan) corrupts users’ web browsers (such as Internet Explorer, Firefox, or Chrome) to intercept the communications between users and websites they’re visiting.
MitB attacks are commonly used against the financial industry, especially for banking websites. But it can take place on any other type of website such as ecommerce sites, utility companies, accounting firms, and government websites.
A MitB trojan can modify, add, remove the fields on the forms, and steal the data entered by users on the website. Not only that, the malware can also change the entire appearance of the website to misguide the victims. MitB trojans are so powerful that they can also modify the responses and confirmation receipts coming from the server’s (website’s) end. They can remove the entire transaction from the records before the victim revisits the website!
Let’s consider the following example. Say, you visit your bank’s website and transfer $100 to your spouse’s bank account. But a MitB trojan changes the amount to $10,000 and writes the attacker’s bank account number in the recipient’s field. You don’t notice the alteration and proceed with the transaction. The malware modifies the confirmation receipt and (or confirmation message) you receive from the bank and shows the details you expected ($100 to your spouse’s account)! Later on, when you log in to your bank account, you find a mysterious $10,000 debit entry in your bank statement!
MitB attacks are so dangerous that even the TLS protocol, two-factor authentication (2FA), and multi-factor authentication can’t prevent them. Users think they are dealing with a legit website and the transection is going on as per their expectation. So, they provide the OTP, secret pins, or use their biometrics to complete the transaction.
What makes this type of malware attack so worrisome is that they’re difficult to detect. Servers (websites) can’t detect them as transection is done by the legit user without bypassing any authentication steps. (So, in the eyes of the server, there’s nothing to be suspicious about.) That’s why MitB attacks are some of the most dangerous malware attacks.
5. Botnet Attacks
A botnet is a network of robots or zombies (compromised internet- or network-connected devices). For this type of malware attack, the hackers develop a special malware known as botnet trojan, which can be combined with viruses and worms as well. The malware writer, also known as botmaster or bot herder, infects a large number of IoT devices (computer, mobile, camera, Wi-Fi routers, tablets, internet-connected televisions, printers, etc.) with the botnet malware to create an army of infected devices.
Botnets are useful for a variety of cybercrimes, such as:
- Deploying server-side attacks like DDoS attacks and brute force attacks,
- Stealing sensitive data,
- Generating fake web traffic,
- Spreading malware, and
- Mining cryptocurrencies.
The infected devices follow the attacker’s commands and execute the cyberattack accordingly. The owner of the device stays unaware that their device is a part of a botnet. Some botmasters use PKI to encrypt the malware, commands, and botnet’s internal communication. That means no one can enter the botnet, read the commands, or hijack the botnet without a corresponding cryptographical key.
A botmaster communicates with the infected device through a master computer known as the C&C server. Spamhaus Malware Labs reports seeing a 71.5% increase in botnet C&C servers in 2019 over the previous year.
A botnet can also use a more advanced communication technique called peer-to-peer (P2P) network. This allows bots to communicate without relying on a central server. Because there is no central C&C server, this makes it difficult for cybersecurity professionals to track the communication chain. Even if they take down some infected bots from the network, all other bots continue to communicate with each other, which allows the botnet to continue to exist.
6. Exploit Kit Attacks
An exploit kit is an instrument to exploit the vulnerabilities of a software or application. A vulnerability is a weakness, such as an error or bug in software or an application, that hackers can use as entry points to insert malware into a target’s system. An exploit kit has special codes that can scan the connected host’s systems, find vulnerabilities, and deliver a payload.
Hackers hide the exploit kits in the fraudulent websites or on the websites with weak security postures. When you visit such a compromised site, the kit will redirect you to another landing page where the exploit code is inserted. It will immediately start scanning your device, browsers, software, and applications (Microsoft Silverlight, Adobe, Java, Runtime Environment, Flash Player, etc.) for vulnerabilities. If it finds any, it will deploy the malware in that vulnerable software.
If all the components are updated and patched to their latest versions, the exploit attack will cease. This entire process takes place silently in the background in a way that you won’t notice anything.
Exploit kits are easy to deploy, and a perpetrator without programming knowledge can also use it. The exploit kits makers rent them in hacker marketplaces and on the dark web as a SaaS product.
Please note that the best way to protect against an exploit kit is to keep all your software and applications patched. Also, be sure to train your employees to not engage with unknown links or advertisements.
7. Backdoor Malware Attacks
A backdoor is a way to access systems and software from the back end, often without detection. This isn’t always an attack, however, as there are administrative backdoors that are built into many systems. But it’s definitely bad news in the case of a backdoor malware attack.
This type of malware attack is executed against a variety of IT-related systems, including website servers and applications. In a backdoor malware attack, a hacker searches for and exploits gaps in your security defenses to insert malware to gain unauthorized access. Some potential security loopholes include:
- Outdated plugins, themes, or software.
- Unprotected input fields.
- Leaky or weakly protected database.
Backdoor trojans can steal sensitive data and insert exploit kits, adware, viruses, or even redirect links into a target’s system or site. Because backdoor malware attacks occur in the background, the target’s system owners often have no clue about what’s happening. This is by design, as cybercriminals often mask backdoor shell files or encrypt their code.
Small businesses are the most vulnerable for backdoor attacks because they generally don’t have the budget to invest in website/app security or are simply inexperienced or unaware of cyber risks. Malwarebytes detected 672,495 instances of backdoor malware deploying against businesses in 2019. This is a marked increase of 14% from their backdoor malware detections in 2018.
But the good news is that you, as a small business owner, can protect your website/app even without expensive security products.
First of all, keep all your website/app components updated to their latest versions. Also, there are many free, paid, and freemium security products (such as firewalls, malware scanners, server-side PHP scanners) available in the market. You should also validate and sanitize inputs.
What’s the Purpose of a Malware Attack?
Hackers typically use malware for:
- Stealing, encrypting, and deleting sensitive data (such as personally identifiable information, financial records, medical information, and trade secrets).
- Monitoring and recording the users’ actions and keystrokes.
- Executing financial fraud and identity theft.
- Gaining unauthorized access to users’ devices, social media accounts, email clients, etc.
- Infecting other connected systems, software, browsers, and applications to distribute malware.
- Shutting down servers and other devices to impede or halt services for legitimate users.
- Stealing information from websites’ databases.
- Infecting websites and advertisements to further spread malware to website visitors’ devices.
The Role of Social Engineering & Phishing in a Malware Attack
Social engineering is a great way to get unsuspecting users to engage with malicious links and emails. That’s because social engineering is all about manipulating targets and tricking them into some type of action. Often, this results in them doing something they’d normally never do, such as providing account information or engaging with infected files.
There are two main purposes of social engineering attacks:
- To make people download malware-laden software/applications.
- To trick people to share their personal information like passwords, social security numbers, payment card numbers, etc.
Social engineering often involves the use of phishing emails, which are a convenient way for hackers to deliver malware to their targets. They often disguise malware as seemingly harmless Microsoft Office files. Certain types of phishing attacks (such as spear phishing and SEO fraud) can be very effective because cybercriminals tailor the messages to their targets to make them more convincing.
Let’s consider the following three scenarios for how social engineering attacks are useful for delivering malware.
Example 1: An attacker might start a conversation with you on a social media site. After gaining your trust, they’ll then send you an infected video or image file. When you open the video/image, malware downloads onto your system.
Example 2: In this scenario, a hacker might send you a phishing email that looks like it’s coming from a legit company. The email contains a benign-looking transection receipt, media file, PDF document, or even free software. But when you download it, you’re unaware that you’ve now just downloaded a trojan horse or computer virus onto your device.
Example 3: Let’s say you get an SMS phishing message (smishing) that looks like coming from a company that you trust. The text talks about a special deal or discount on a product and contains a link. But when you click on this link to get the discount, it directs you to a spammy site. This is where drive-by malware auto-downloads to your smart phone.
The malware allows the attackers to gain access to the victim’s system, steal data, launch ransomware attacks, or use the system for botnet attacks. You should be vigilant to download anything from the internet and scan everything with an antimalware software before downloading it.
Wrapping Up on the Different Types of Malware Attacks
Statista reports that there were 9.9 billion malware attacks executed in 2019 alone. Such a huge number shows that any device, website or organization can become victims of malware attacks.
These are some things you can do to protect yourself and your organization against different types of malware attacks:
- Implement a layered approach to security.
- Use antivirus and anti-malware software (behavior- and signature-based security software for advanced malware detection).
- Put firewalls in place that alert you when you are accessing a malicious site or when anything suspicious downloads onto your system.
- Review traffic logs to keep an eye on any suspicious activities.
- Use email filters, DKIM, SPF, DMARC and email signing certificates to protect yourself and your recipients from phishing emails.
- Keep all applications and software patched and up to date so that they’re using their latest versions.
But that’s not enough. You must stay vigilant while surfing online and downloading anything from the internet. This is where cyber awareness training can be useful.
Follow these tips from Google Chrome Support to remove unwanted ads, pop-ups and malware from your device.
If you’re an SMB, be sure to check out this article on cybersecurity for SMBs. It offers tips to help you protect your organization from malware attacks and other cybersecurity threats.














 (21 votes, average: 4.62 out of 5)
(21 votes, average: 4.62 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security