FluBot Malware: What to Know About This Android Threat
If you’re an Android user, you need to know about FluBot. The scam first appeared in late 2020 and is now spreading like wildfire through Android devices, using SMS messages to trick users into downloading malware. Let’s break down what happens when your device comes down with a case of the FluBot
Android OS has just over 70% market share in the global smartphone operating system market. For cybercriminals, it’s an irresistibly large pool of prospective targets. That’s why Android has been an evergreen target for hackers — if even a small number of their attacks succeed, the rewards can be enormous.
One of the newer threats in town is FluBot malware. It was initially discovered as affecting Android users’ devices in Spain in December 2020 before spreading to other European countries in early 2021. It has since infected devices in Australia and New Zealand and continues spreading rapidly to others as well.
In this article, we’ll answer the following questions:
- What is FluBot malware and how does it get into a user’s device?
- What happens if your phone gets infected with FluBot?
- What should you do if your device is infected with FluBot?
- How can you prevent your Android devices being infected with FluBot malware?
What Is FluBot Malware? Defining FluBot Android Malware
FluBot, which BleepingComputer says is also known as Fedex Banker and Cabassous, is a type of malicious software that infects Android smartphones and devices via SMS text messages. Once infected, the malware gives hackers access to the operations of the affected Android device.
Once a user downloads the malware, the hackers can use their access to do one or all of the following:
- Steal login credentials, credit card numbers, and other sensitive information,
- Disable built-in security mechanisms,
- Send messages from the victim’s devices, and
- Carry out many other nefarious acts on the infected device.
How FluBot Infects Android Devices: A Look at FluBot Scam Messages
FluBot travels via SMS text messages, sending a link as part of the messages to recipients. Although both Android and Apple phones can receive messages carrying FluBot, only Android devices can be infected by the malware. Messages may talk about an incoming delivery, a software update, or even state that your phone has been infected with malware or that you have been part of a data breach.
The common factor is that each message contains a link to a download page. These links are usually disguised as one of the following to entice you to download and install the software:
- Anti-virus/anti-malware software
- Voicemail notifications
- Delivery tracking apps
- Software updates
- Shared photo albums
- Other types of tempting software download
In reality, the link takes the victim to a FluBot malware download page. Your device won’t become infected unless you download and install the malware. If you receive any unsolicited SMS messages relating to these topics, exercise extreme caution and avoid clicking on any links.
Here’s a quick example of how the message looks and what occurs when you click on the fraudulent link:
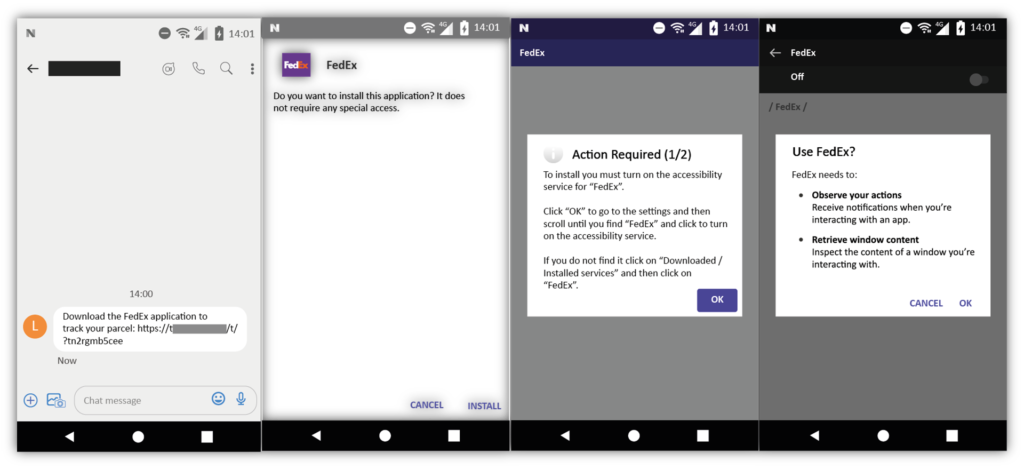
What Damage Can FluBot Malware Cause?
It seems that FluBot is spreading to every corner of the globe. According to Proofpoint’s estimates, there were 7,000 devices infected with FluBot in the United Kingdom (U.K.) by April 2021, with tens of thousands of malicious SMS messages being delivered every hour. In Australia, the government’s Scamwatch service received more than 16,000 reports of FluBot scams between August and October 2021 alone.
But what happens once a device is infected? Once installed on an Android device, FluBot can:
- Steal victims’ login credentials, including credentials for financial institutions such as banks.
- Access the victim’s entire contact list and send FluBot-laden text messages to all contacts. It blocks the recipients after sending the message, which means they can’t text back or call the sender (i.e., the original victim) to verify the message’s authenticity.
- Disable the inbuilt security features offered by Android OS and third-party security programs to avoid being detected and removed.
- Intercept SMS messages sent by banks with passwords or verification codes that are needed to authorize money transfers.
A disturbing aspect of FluBot malware is that you won’t see typical symptoms of infection such as your phone slowing down or the screen freezing. You’ll likely only notice FluBot when it’s too late — after the scammer has already done something nefarious.
How Do I Know If I Have FluBot? 3 Key Warning Signs to Look Out For
Detecting a FluBot malware infection can be challenging. However, Telstra shares three warning signs that you can look out for on your devices:
- An application labeled “Voicemail” appears on your smartphone that has an icon of a blue cassette inside a yellow envelope.
- You receive messages from friends, family, or other contacts regarding messages or phone calls that they received from you that you didn’t send or make.
- Your network provider warns that a large number of text messages have been sent from your device.
My Phone Got Infected with FluBot — Now What?
If you suspect that your phone is already affected by FluBot, you must act quickly to limit the damage and stop the malware from spreading further. Here’s what you need to do:
- Perform a factory reset. The only known way to get rid of FluBot is to return your phone to factory settings. This will delete all the data, including the virus. The steps for factory resetting vary with different manufacturers, but the process usually look something like this:
- Go to Settings
- Select System
- Choose Reset options
- Select Erase all data (factory reset)
- Select Reset Phone
- Click Erase everything
So far, no anti-malware company has claimed that they can successfully detect and remove FluBot. That’s why, for now, a factory reset is the only way to get rid of it.
- Get professional help for data backup. You must not take data backups after being infected with FluBot as it might have already spread to other folders and apps.That means taking a backup will worsen the situation, as the FluBot malware will be able to re-infect your device or other devices when you restore the data.If you need to take a backup before carrying out a factory reset, get a professional’s help.
- Change your passwords. FluBot is infamous for stealing credentials. It’s vital that you change the login details for all the apps and online accounts that you access with your phone. A couple of important points:
- Change credentials after factory reset: Don’t change details before factory reset, or FluBot will get access to the new credentials as well.
- If possible, use a device other than the infected phone: If you can access the apps and websites from your laptop, tablet, or another device that is not infected with FluBot, you can change the credentials before the factory reset.
- Enable two-factor authentication. Enabling two-factor authentication, especially for banking and financial apps, ensures hackers can’t log in to your accounts without a unique OTP or secret code sent to your phone number. This step provides an extra layer of security in the event of a credential compromise.
- Contact the relevant regulatory authority. If your country has a cybersecurity division or other authority to deal with cybercrimes, report the incident to them via their processes and procedures. Different countries have various ways to deal with cyber crimes and often have specific processes in place for reporting cyber threats. For example:
- New Zealand’s Department of Internal Affairs (DIA) and CERT NZ have instructed their citizens to forward the suspicious FluBot related text message to 7726.
- U.K. citizens can send the link to [email protected].
- Australians should report FluBot scam on the Australian government’s ReportCyber Website.
How to Prevent FluBot Scams From Infecting Your Organization’s Devices
Please note that your phone can’t be infected with FluBot malware unless you or one of your employees downloads the software. That means, even if you receive the text message that you open and click on the link, the virus can’t invade your phone unless you download the malware-laden software. Your device will show a security warning before downloading the software. If you abandon the download at this stage, you’ll still be safe.

Here are some basic awareness tips to help you avoid FluBot:
- If you are expecting a parcel delivery, track it through the seller or delivery partner’s official website. Never click on links in SMS messages claiming to be from delivery companies.
- Always use updated, legitimate versions of software from official sources. Never follow links in text messages or emails that prompt you to download or install software applications.
- If you get a message stating your device is infected with a virus/malware, don’t click on the link to download the antivirus program even if you’ve noticed signs of possible infection on your device. Instead, go to an official app store or install anti-malware programs from the official websites of reputed companies like Comodo, Malwarebytes, AVAST, Norton, McAfee, and Bitdefender.
- If you get a strange message from one of your contacts, call them directly to confirm the legitimacy of the message. If you can’t contact them via SMS text or phone call, FluBot might have blocked you on their device. Contact them via a different method like social media or landline, and don’t click on anything in the text message.
- Train your employees to recognize and respond to phishing scams and other cyber threats. Cyber awareness training is paramount for individuals and organizations alike. It’s something that can help you stay safe online and keep your accounts secure. Cyber awareness training covers a wide variety of topics, including cyber security best practices.
Final Thoughts on FluBot Malware
Imagine your friend calling you asking about the SMS he received from you, but you have no clue about it. Or receiving a message about a financial transaction from your bank account that you didn’t make. These types of incidents take place if your device is infected with the FluBot malware.
If you are an Android user who has opened a link from a text message and downloaded software, there’s a high chance that your device is affected by FluBot malware. Please follow the steps described in this article to protect your phone from further damage.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security