How to Tell If an Email Is Fake: 7 Tips to Spot a Fake Email
FireEye reports that one in every 101 emails is malicious! But how do you know if an email is fake or legit? Let’s find out from these 7 tips!
Ever wonder how to tell if an email is fake? When we talk about fake emails, we’re referring to hoax emails that are sent to defraud you or trick you into doing something you shouldn’t. Such emails are also known as phishing emails.
Phishing emails are used to execute various cybercrimes. We all receive many emails every day — many of which wind up in our spam folders. But many times, phishing emails easily escape from the email client’s scrutiny and get delivered in our inboxes.
So, if you’re wondering how to spot a fake email — or, more specifically, how to tell if an email is fake or real — we’ve got you covered.
7 Tips for How to Tell If an Email Is Fake
1. Inspect the Email Header Info to Verify Whether the Sender’s Address is Legitimate
The first sign of a phishing email is that attackers pose as legitimate companies or people. By posing as a legitimate person or business, the cybercriminal’s target is more likely to believe the email is legit and will engage with it.
Legitimate organizations typically send emails from email addresses containing the company’s domain name after the “@” symbol. For example, xyz@wellsfargo.com, xyz@amazon.com, xyz@apple.com, etc. In other words, the company’s domain should be what comes after the “@” sign. To get such an email address, you must own the domain name, or an authorized person from the company needs to create one for you.
If you get an email claiming to be from a well-known organization, here’s how you can easily tell if the email is fake:
- The sender’s email is coming from public domain email addresses such as Gmail, Hotmail, Yahoo, AOL, etc.
- The email is sent from an unknown domain name.
- The sender’s name and the name in the email address don’t match.
For example, if the sender claims that email is from Chase bank, the sender’s email address must have @chase.com or @jpmorgen.com in it. If the sender’s email address ends with “@gmail.com” or some unusual domain name after @, it’s a big red flag.
Check out the example below:
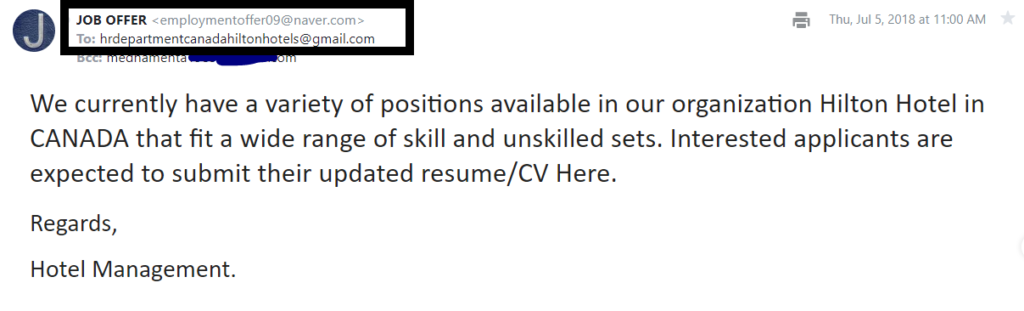
As you can see in the screenshot above, if the email were from Hilton, it would have “@hilton.com” in the sender’s email address instead of “@gmail.com” or some unknown domain like “@naver.com.”
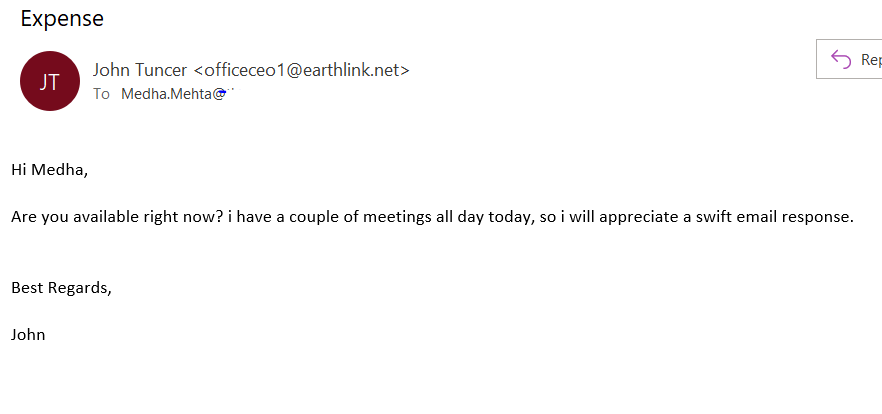
Check out another example below. Here, a spammer impersonates my employer, John Tuncer. But it’s easy to recognize such a fake email because of the non-company related email address:
Look for Deceptive Domains and Spellings in Email Addresses
Some attackers are smart enough to not use a generic email address. They buy domain names that look similar to the legitimate company’s domain that they wish to impersonate. They commonly add extra words or replace some of the letters/words in the original domain name. Check out the below table to get a clearer idea of how scammers use deceptive domains:
| Trick | Example | Example |
| Original domain | Duplicate domain | |
| Replace “S” with “5“ | chase.com | cha5e.com |
| Replace “m” with “rn“ | macys.com | rnacys.com |
| Replace “L” with “1” | wallmart.com | wal1mart.com |
| Replace “O” with “0” | wellsfargo.com | wellsfarg0.com |
| Add extra words | apple.com ebay.com | apple-online.com ebaysupport.com |
Now, even if email recipients are vigilant, they might fail to see the difference between [email protected] and [email protected]! A perfect example of this occurred recently when an employee of “Shark Tank” star and entrepreneur Barbara Corcoran fell for a phishing email. The attacker sent an email to Corcoran’s bookkeeper while impersonating her assistant and instructed the bookkeeper to pay to a vendor that Corcoran allegedly invested in.
Thus, it’s vital that you always review the sender’s email address with extra caution.
2. Watch Out For Uncommon Uses of the Email Bcc Field
In some emails, you will find your email address listed in the Bcc field instead of the recipient lines. Although there’s technically nothing wrong with keeping the recipient in the Bcc field, it unusual for organizations to do when communicating with customers. For example, no legit company would send a blind carbon copy email to verify your account information or to request customers to download the transaction receipts. Why? Because they would reach out to you directly.
So, if you see your email address in the Bcc field instead of in front of “To:” or “Send To:” it’s a good sign that the email is a fake.
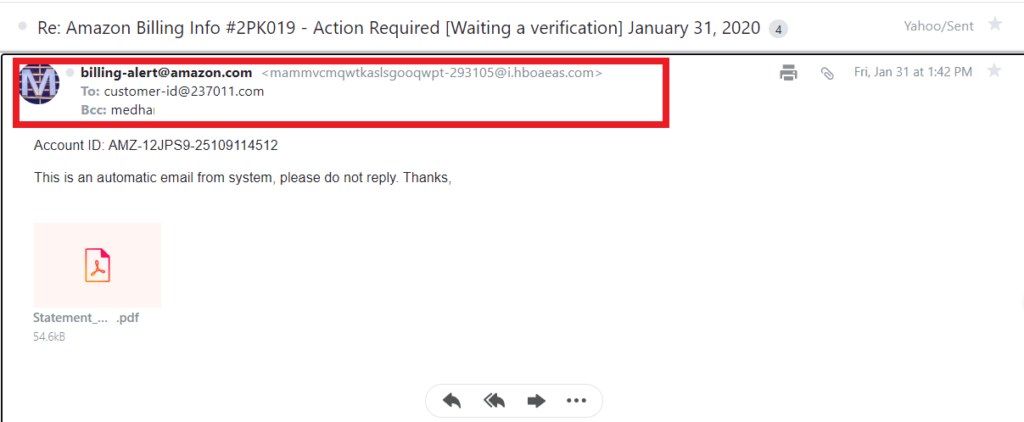
Let’s consider the example phishing email in the screenshot below. Check out how the sender lists my email address in the Bcc column instead of the recipient (To:) field. Also, see how smart the sender is by including “@amazon.com” as part of the sender’s display email address to deceive the recipient.
3. Check Whether Embedded Links Redirect to Unexpected Websites
Another characteristic of a fake email is unexpected redirect links. The embedded links given in the email must take you to the same web page as written in the link. However, scammers include text that looks like it will take you to a legitimate website, but the hyperlinks they embed take you to a phishing or malicious website instead.
For example, you get an email that looks like coming from PayPal. It’s warning you about an unauthorized login attempt and asking you to change the password to protect your account. There is a link given to change your password: https://www.paypal.com/account/passwordChange. You think it’s safe to click as the link looks legit. But when you click on this link, you’ll be redirected to some spammy website that looks legitimate because they use PayPal’s site design, colors, fonts, and logo. Here, the fake website will try to trick you into sharing your login credentials or other confidential details.
Some links might lead users to a malware-laden website that auto-downloads malware onto users’ devices without their knowledge. According to Verizon’s 2020 Data Breach Investigations Report (DBIR), most malware is sent via email.
Sometimes, malicious redirects are hidden in the “Unsubscribe” tab as well.
But how can you tell whether a link is legitimate without actually clicking on the link? There are two ways you can check for fake links in suspicious emails:
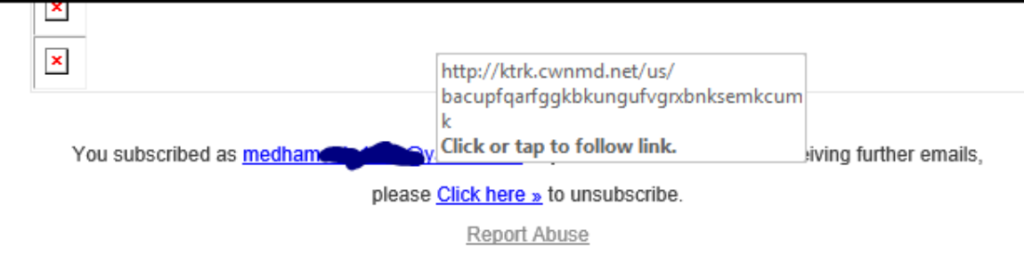
1. Hover your cursor over the link to display the real URL. As you can see in the screenshot below, hovering over the link will show you where the link is redirecting to. If the pop-up URL differs from the information that displays in the linked text, it’s likely a malicious link. Don’t click on it!
2. Right-click on the link (or button) in question and select on “Inspect” in the drop-down menu.
- On the right-hand side (or at the bottom), you’ll see a new window pop up with a bunch of code.
- Here, you’ll see a URL after <a href= text.It is where the given text/media links to. In other words, it shows that if you click on the link, it will take you to that specific URL.
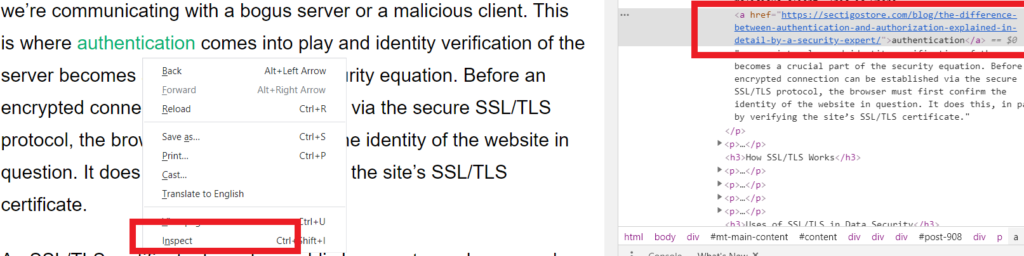
In the above example, I have right-clicked on the word authentication and clicked on the Inspect. On the right side, you can see the URL of the page that is linked to the word authentication. (NOTE: Not all email clients will allow you to inspect elements this way.)
By following this technique, you can always inspect the suspicious links, media, and buttons.
A Bonus URL Inspection Tip
If one of the links you see uses a URL shortened (links that start with tinyurl, bit.ly, goo.gl, is.gd, t.co, etc.), you can see the expanded URL by using this website: getlinkinfo.com
Historically, people would shorten URLs to make links look more professional and less space consuming. But nowadays, spammers are also using the URL-shorting tools to hide their original malicious links.
4. Pay Attention: Don’t Ignore Unusual Spelling and Grammatical Errors
If an email contains many grammatical, spelling, or punctuation errors, it’s a red flag. Legit companies follow strict email etiquette and editorial standards. Although some small typos can happen on occasion, it’s uncommon to see multiple mistakes in a single message. Never ignore such errors.
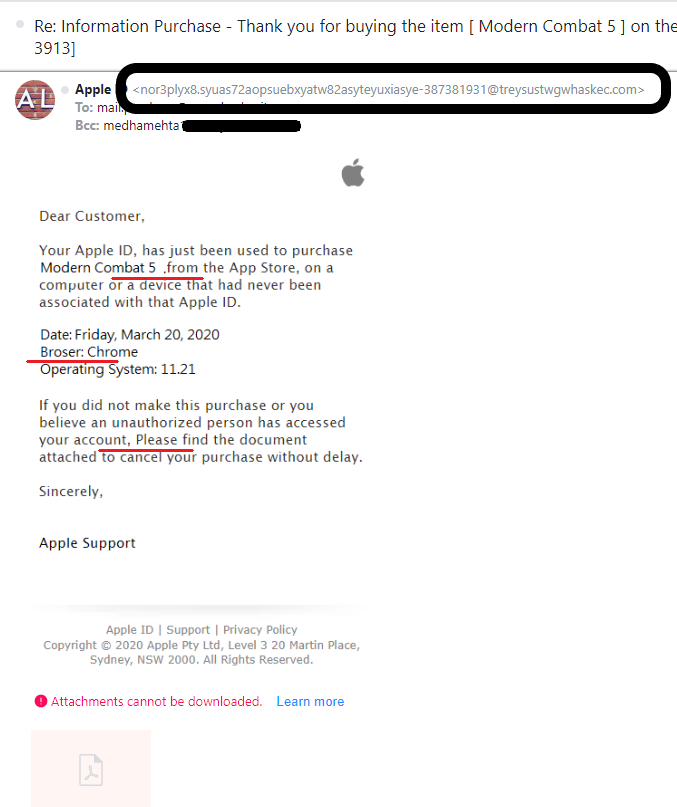
See the example below that highlights several examples of how to tell if an email is fake. Although you can spot that the email is fake from the sender’s unusual email address, there are other red flags, too. Check out the spelling and punctuation errors (marked with red underlines). A reputable company like Apple doesn’t send an email with so many glaring errors.
5. Ask Yourself Whether the Language Seems Fishy, Pushy, or Urgent
Scammers will try to trigger emotional responses like anger, shock, empathy, panic, curiosity, etc. By doing so, they’re more likely to trick their targets into doing something they normally wouldn’t do.
For example, they might send you emails on the following subjects:
- An unbelievable deal/discount on the product
- A high-priced lottery winning
- Offering a job
- Unauthorized access of your account
- Data-breach incident of your credentials
- Free credit reports
- A (fake) purchase from your account (see Amazon’s the screenshot in the previous point)
- A fundraising campaign for poor/people suffering from rare diseases/victims of natural calamities
There are many subjects that elicit emotional responses from email recipients. Hackers know this and will use email subjects that will spur targets to take action without stopping to inspect or investigate the emails properly.
Check out the screenshot below as an example of how to tell if an email is fake:
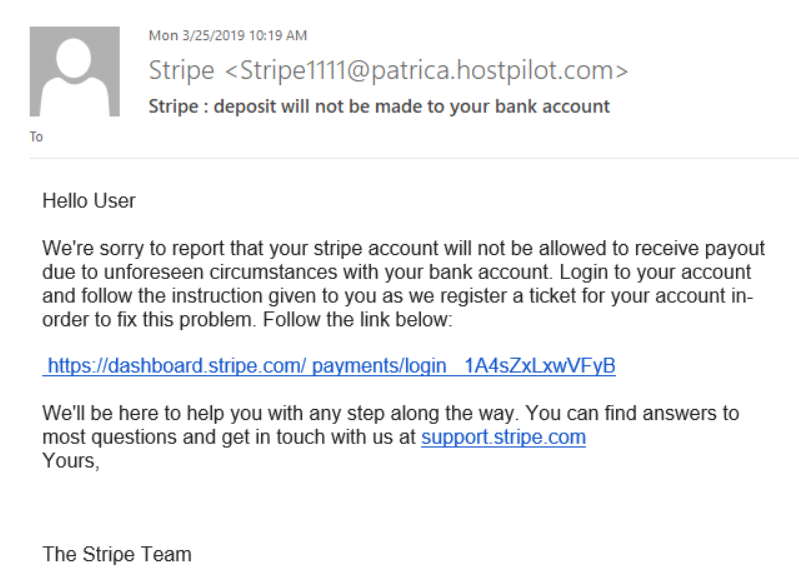
As you can see, this example email mentions a temporary hold on the Stripe account due to some unexplained bank-related issues. Now, it’s likely that people using Stripe on a regular basis (businesses, freelancers, advertisers, remote employees, etc.) would get anxious after reading such an email and try to respond immediately.
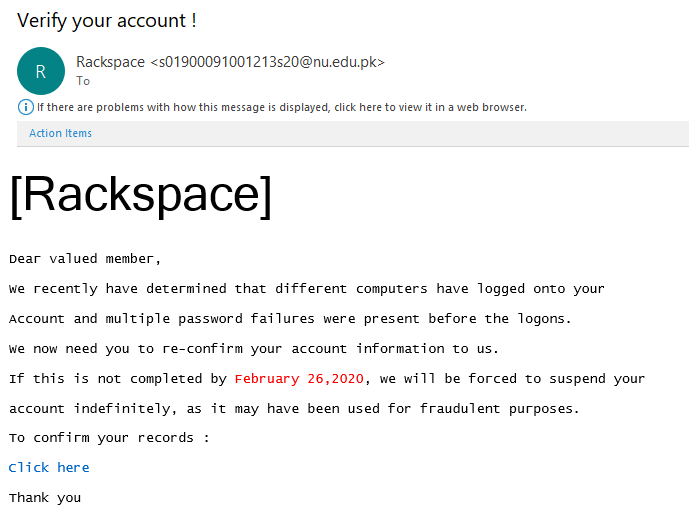
Hackers like to create a sense of urgency. Sometimes, scammers impose time limits to force users to take prompt action in panic. Check out the following email example. Along with the account suspension threat, there’s also a deadline mentioned. Often times, attackers will impose deadlines of 24 or 48 hours. Such deadlines pressure users to take the prompt actions suggested in the email.
6. Ask Yourself if Email Attachments Are Unsolicited or Unexpected
A good rule of thumb when it comes to email attachments is to ask yourself: Did I request this information? Frequently, cybercriminals will send emails with phony attachments to get you to inadvertently download their malicious executables. These attachments could come in many forms, including:
- Invoice documents
- Receipts for payment
- Photos or other graphics
- Pricing sheets
- Spreadsheets
Check out the following examples of phishing emails one of my colleagues received. These unsolicited emails contain Word docs and other attachments:
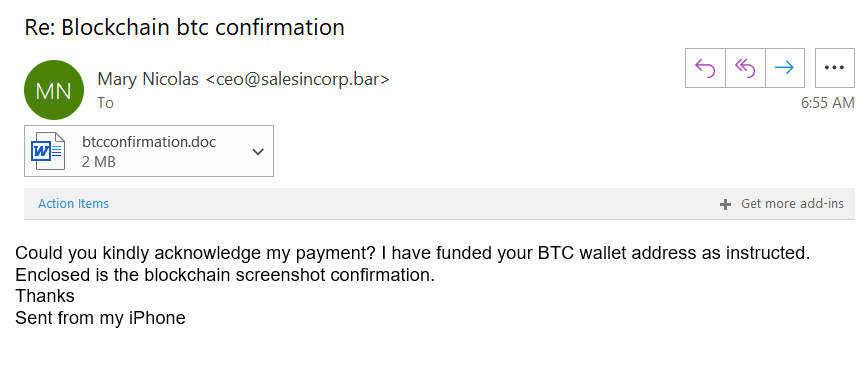
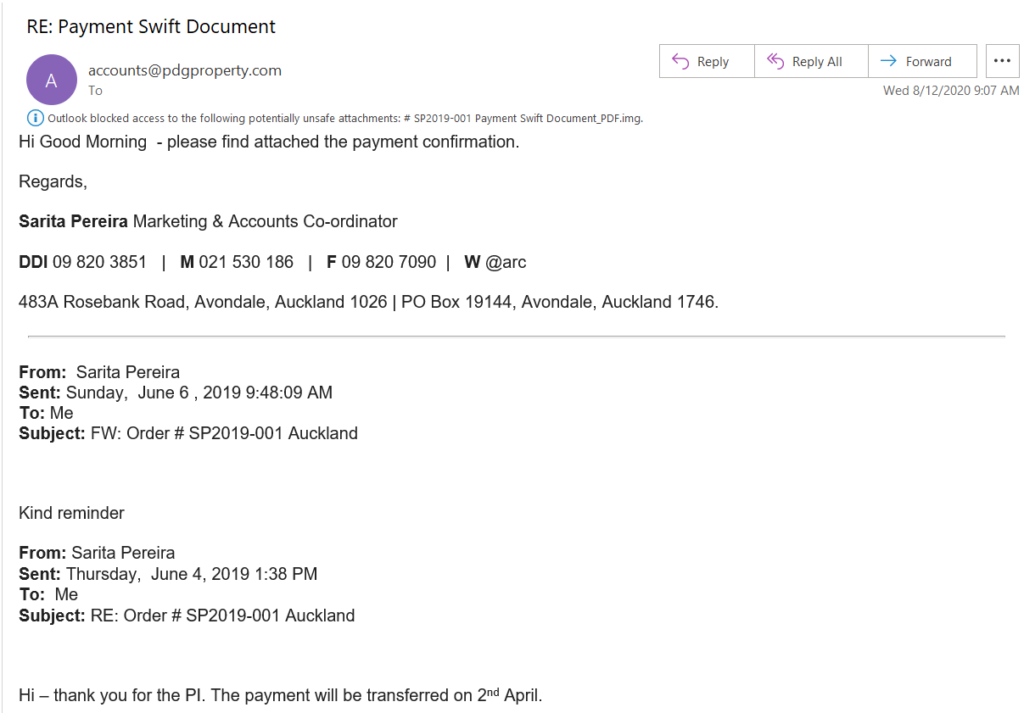
In this example, Outlook was able to easily identify the attachment as a suspicious or unsafe file. However, that’s not always the case and many times malicious attachments pass through email filters.
Document-based malware like this has become relatively common. This is because Microsoft and Adobe added the ability for Word docs and PDFs to work like executables via scripting and macros. Sophos shares some additional concerns:
“Some document-based malware types have the ability to spread to other documents on an infected system. Once there, any legitimate document a user sends to friends and colleagues could end up spreading the malware.”
When in doubt about whether an email or its attachment is fake or legitimate, reach out to the sender directly. Preferably, call them via phone using a number that’s listed on an official source such as a company contact directory. Never use the contact information that’s listed in a questionable email!
7. Be Vigilant (Even If the Email is From a Legit Email Address)
The above tips will help you to know if an email is fake when the attacks use a fake email address. But what if you get an unusual or unsolicited email from a friend or relative from their authentic email address?
There are different types of malware and cyber-attacks that can corrupt a users’ devices and send phishing emails on their behalf to other victims. These types of malware can delete the emails from the sent folder, and the victims remain unaware of such compromise. There’s no exact way to define an “unusual email,” but just use your instincts. Something about the email may look or feel “off” — for example, the email may ask you to:
- Immediately transfer money to help them.
- Open a website to get the benefit of an unbelievable (unrealistic) deal/discount.
- Donate money to some unknown organization.
- Reply with your phone number, some files or personal information.
- Download a software, attachment, or a media file.
If you get such an email, this is another time when you should reach out to the sender personally (even if the email is from a legit email address) via phone before taking actions suggested in the email. Your loved one’s email account might be compromised, and they have no clue about it!
Why Cybercriminals Send Fake (Phishing) Emails
Scammers are becoming smarter and more innovative with their email phishing techniques that even the most vigilant people become victims of email phishing scams.
Phishing emails are sent to:
- Create a sense of urgency to get victims to engage with them.
- Deliver malware to the victim’s computer via attachments or links.
- Redirect victims to a malicious website or a website that looks the replica of a legit company’s website.
- Trick recipients into sharing their login credentials, financial, or other sensitive information.
Needless to say, it’s high time that you and your employees learn how to spot a fake email in order to protect yourself and your organization from email phishing scams.
Wrapping Up: What To Do If an Email Is Fake
The aforementioned seven tips will definitely help you spot a fake email. But, what to do after you receive such an email? Ignoring such fake emails won’t be enough. You should also delete phishing emails as soon as you get them. But before deleting them, you should:
- Block the sender: Click on the More (three vertical dots) option on the email. It is located in different places in all the email clients. For example, Google Chrome’s More tab is located on the upper right side of the email. In Yahoo, it is located at the bottom of the email. So, search for the three vertical dots and click on the “Report as spam” and “Block this user.”
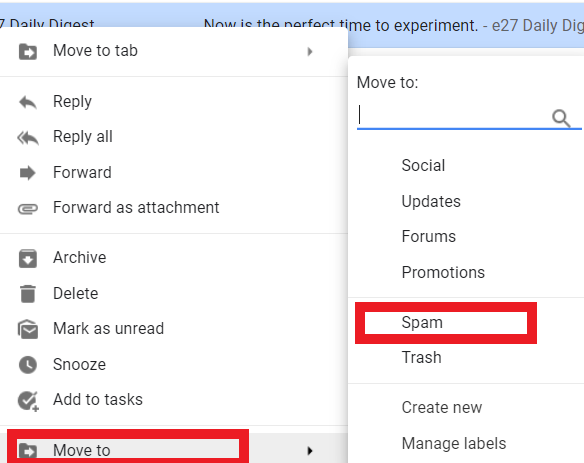
If you don’t want to open the email, you can right-click on it in your inbox. In the drop-down menu in Gmail, for example, go to Move To and click on Spam.
Report the Fake Email: If you receive a phishing email from someone impersonating a company, forward the email to that company’s official customer support email address to let them know.
If you have become a victim of cybercrime due to a phishing email, register the complaint with the following groups:
- FBI Internet Crime Complaint Center (IC3)
- U.S. Federal Trade Commission
- The Anti-Phishing Working Group (APWG): [email protected]














 (66 votes, average: 4.76 out of 5)
(66 votes, average: 4.76 out of 5)





2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security