Which Type of Cyber Attack Is Commonly Performed Through Emails?
Proofpoint data shows that 65% of organizations admit that they experienced one or more successful phishing attacks in 2019! And, according to FireEye’s report, 1 in every 101 emails contains malware! It’s high time for you to know what type of attacks use email.
Valimail reports that 3 billion spoofed emails are sent every day! When you read such scary statistics, it is obvious for you to wonder which type of cyber attack is commonly performed through emails and how to spot a fake email. Data from the same Proofpoint survey also indicates that 51% American workers can’t tell you what phishing is! But specifically which type of cyber attack is commonly performed through emails most often?
Cybercriminals are very clever these days. They typically won’t send you the “Nigerian Prince” or “$10 million lottery” types of scam emails anymore (although some still do). Instead, they’ll try to send well-researched and creative emails that you might not be able to resist clicking on. That’s why it’s high time for you to know the seven most common types of frauds that attackers deploy using emails. We’ll also talk about the effects or damages these emails cause and how they’re used to scam and defraud victims.
Which Type of Cyber Attack Is Commonly Performed Through Emails?
Phishing
Hands down, phishing is among the most common type of cyber attack attackers perform via emails. Phishing means using various tactics to trick users into taking actions that they shouldn’t (and normally wouldn’t). Such actions lead them to become victims of various types of cyber attacks. Although phishing can occur via other channels (phone calls, text messages, etc.), email is the most commonly used platform to execute phishing scams.
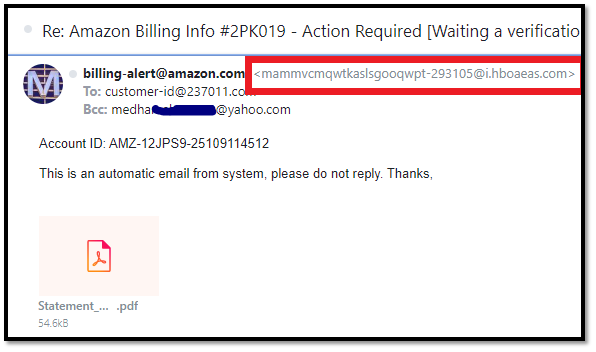
Email spoofing is one of the most successful email phishing techniques. Here, a threat actor (bad guy) poses as someone else (such as a vendor, colleague, executive, or a trusted organization) to gain the email recipient’s trust and trick them into:
- Sharing their personal information,
- Wiring money or making other fraudulent monetary transactions,
- Visiting corrupt websites, or
- Downloading malware-laden attachments.
Of course, not all email scams are phishing. But email phishing is an umbrella term that describes many types of email-based scams that we’re going to cover in this article.
Phishing Emails Often Contain Malicious Attachments & Phishing Links
Scammers often include phishing or malicious links (or infected attachments) in their emails and write the body content in a way that tempts you to click on them. In general, they try to get an emotional response from you — like generating panic, excitement, anger, frustration, amusement, or curiosity — to lure you to click on a link. But what harm these links so?
- Redirect recipients to malware-laden websites. These websites are stuffed with viruses, trojan horses, computer worms, adware, spyware, etc. Often, malware will be hidden in the advertisements (known as malvertisements), songs, videos, images, slideshows, PDFs, in-between content, or similar type of objects. Some of the advanced malware will get downloaded to your device as soon as you arrive on the website, even if you don’t click anything. So, as soon as you click on the links, a malicious program downloads onto your device.
- Lead you to phishing websites. A phishing site often looks like a well-known legitimate site. Here, users are asked to input their confidential information via forms, login with their credentials, or even do a financial transaction. Needless to say, such information never reaches the legitimate company. Instead, it’s sent directly to the hacker who has nasty plans for it.
Whaling Attacks
In this type of email scam, the attackers target high-profile employees like CEOs, CTOs, CFOs, COOs, and senior managers. This is a highly customized attack in which the scammer patiently collects the target’s information using various online and official sources, and via social engineering. They might even go to the extent of making a fake website, documents, or social media profiles to sound legitimate to the victim.
After detailed and careful planning, the attacker sends an email to the target posing a legit source and asks them to take actions that they shouldn’t.
Example: Attackers send emails representing the bank manager with whom the company is dealing for many years. The email states that the target should immediately change the password by clicking on the given link, as the bank has noticed some unusual activities in their account. The recipient gets panic and clicks on the link, which redirects them to the phishing site that looks exactly like the original bank’s site. Here, the victim is asked to input their user ID, old password, and new password. As soon as they do so, the attackers get hold of the companies’ official bank account credentials!
Business Email Compromise (BEC) & Email Account Compromise (EAC)
If you are a business owner and wondering which type of cyber-attack is commonly performed through emails, BEC is something you must be aware of. Much like whaling attacks, BEC scams also relate to executives but in a different way. Here, instead of targeting one or more of the executives, the attacker instead targets mid- and lower-level employees. They also may send emails to employees pretending to be someone from a third-party organization that generally deals with the company.
BEC scams often involve cybercriminals pretending to send emails from legitimate users’ accounts. But if they manage to actually gain access to those users’ real accounts, they move into what’s known as email account compromise (EAC) territory.
Check out a few example BEC scenarios:
- A scammer sends an email to the human resource department pretending to someone working in the company and requests to change the bank account number in the records for the future salary remittance. Needless to say, the new bank account number belongs to the attackers themselves.
- An attacker sends an email pretending to be your boss/supervisor or an executive and asks for some important files or information to send them in the reply.
- A legitimate-looking email appears to come from your IT department. It instructs recipients to install or update software they’ve attached to the email. But in reality, this email is from an imposter and the software can be a trojan horse or other type of malware.
- Your manager asks you to make payment to your regular vendor or affiliate and provides a bank account number in the email. You think the email is legit, follows the instructions, and inadvertently transfers money to the attacker’s bank account.
These are just a few examples. But BEC can be very dangerous. According to the FBI’s 2020 Internet Crime Report, companies lost more than $1.8 billion due to a combination of BEC and EAC scams.
Pay-Per-Click Ad Scams (Click Fraud)
Just like the previous tactic, the attacker will send a tempting email that directs you to a website. But this website won’t have any harmful malware or fake login pages on it. Rather, it’s a benign site with lots of advertisements. The way the site owner makes money is by driving as many users to their site as possible. This way, they can claim higher numbers with more page views and PPC commissions.
Some click fraud scams, however, are malevolent in nature. Their goals are to deplete companies’ digital advertising budgets by targeting their ads with as many phony clicks as possible. Although cybercriminals often use bots for this purpose, they’ll sometimes use phishing emails as well to attract real users.
The sender attracts users by sending emails containing links to bogus deals, fake “breaking news,” or something else that motivates users to click on them. However, when a recipient reaches the website, there isn’t anything on the site that the email promised. Hence, users become nothing more than pawns for the scammer to make more money off of by making them view advertisements.
Malware Attachment-Based Attacks

In this type of attack, a cybercriminal includes malware in the email itself via embedded images or other attachments. The attackers will use urgent or convincing language to tempt you to open or download the attachment. They might send you attachments or links that appear to be
- Transaction receipts,
- Bank notices,
- Warning alerts documents for suspending some services,
- Interview details or offer letter, or
- Free items of interest, such as software or books.
Of course, once you open such a link or engage with the attachment, malware installs onto your device. Once the malware invades your device, it can:
- Spy on you,
- Steal your important data,
- Monitor and record your actions,
- Lock the data or device for extortion money (known as ransomware attack),
- Use your device as a bot to execute cyberattacks (known as botnet attack),
- Show irritating advertisements,
- Send phishing emails or messages using your email clients and social media profiles
Fake Sales/Promotion Scams
Some online businesses use such unethical email marketing tactics. They send emails to the new or existing customer offering some exciting “too-good-to-be-true” offers, schemes, and discounts. But when you visit the site and get engaged, they give you a smaller discount than promised in the email along with some excuse for why it’s lower.
Example: X company sends you an email with the text “Flat 70% on all apparels if you use the coupon code 70%OFF.” You click the email, browse the products, and add your favorite apparel to the cart. But at the time of checking out when you apply the coupon, it won’t work. You see an error message stating that the coupon is expired, and you will be given alternative “valid” coupons that give a 30% discount.
In the above example, some consumers still choose to buy as they already have spent a lot of time browning and shortlisting products. Other disappointed users will abandon the shopping cart. But the website’s analytics track their actions and use this information in their PPC campaigns to show the well-targeted customized ads.
2 Key Motives of Email-Based Cyber Attacks
What do cybercriminals try to accomplish in such email scams? The main two motives are data, which they can steal and sell or use for identity theft-related crimes, and money or other financial gains. There are other motives as well, such as espionage, revenge, or other personal or political agendas, but we aren’t focusing on those today.
Data Theft
Data theft is not a type of cyber attack in and of itself but rather a result of them. Data is a crucial component for many types of crimes that involve identity theft, blackmailing (like ransomware attacks), and doxxing. And cybercriminals love to steal data so they can use it to carry out other types of cyber attacks, trade or sell it to other bad guys, or use it for other purposes.
The attacker sends you an email in a way that you willingly share your confidential information with them! For example, they’ll pretend to be the boss that asks to send you some e-files immediately. Do you dare not send them? In the same way, attackers pose themselves as
- Friend/relative,
- Reputed Company,
- Bank,
- Recruiter,
- Government agency,
- Utility company,
- Educational institute,
- Teacher/professor, etc.
They sometimes ask you to send your private information like physical address, phone number, social security number, date of birth, health information, income, etc. Often, they ask for your organization’s confidential information like customers’ details, technical know-how, trade secrets, secret financial data, etc.
Example: A scammer poses as a recruiter of a big company and says they’ve hired you. As part of their scheme, they ask for your personal details under the guise of performing a background check and say they require your social security number for credit checking and tax-related purposes.
As these are common hiring-related procedures, you don’t find anything suspicious about it and provide all the documents as request. But by the time you figure out it’s a scam, the cybercriminal is long gone. They vanish after receiving your information and either use them for executing identity theft-related crimes or sell them to other attackers in the darknet.
Financial Fraud
As the title indicates, the attackers use emails to commit fraudulent financial transactions. Sometimes, they stead your payment card numbers or bank account details. Often, they make you send the money to them. Here are three such example scenarios:
- A cybercriminal sends an email posing a philanthropy organization. In their messages, they share images of people in distress and ask you for donations to help them. But the pictures are fake,
- A scammer poses as a recruiter whose company requires you to cover specific up-front costs. They might ask you to buy training material, saying it’s a requirement of the training process. Or, they may ask for money for conducting background checks.
- A bad guy pretends to be a major company you do business with & directs you to a fake site. They might redirect you to cybersquatting domains (i.e., domains that look similar to a popular brand/business) like amzon.com, facbook.com, or welsfargo.com to trick you into making a payment for a product or service.
Wrapping Up on “Which Type of Cyber Attack Is Commonly Performed Through Emails”
We hope our article has helped you to understand what types of cyber attacks use email as an attack vector. Now, you have a better idea of how to protect yourself and your organization by identifying such fake emails. We have written three articles that have various tips and tricks to help you recognize email phishing frauds and help you to prevent getting spoofed. Have a look:














 (34 votes, average: 4.76 out of 5)
(34 votes, average: 4.76 out of 5)





2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security