The OWASP IoT Top 10 List of Vulnerabilities
While the global IoT market projected to hit $1.1 trillion by 2026, Gartner forecasts there will be 25 billion connected devices within the next year — a scary number considering the IoT vulnerabilities that exist within these devices
If you’re here to learn about the OWASP IoT top 10 list — good. Because IoT technologies are all around us, and without proper protections in place, they’re leaving sensitive data and personal information vulnerable to craft cybercriminals.
Our lives are made easier every day with the innovations in technology, and the internet of things (IoT) is only one such advancement that brings us many wonderful perks like having a smart lock on our doors. But these conveniences often come at the cost of our security and leave us open to a wide variety of cyber attacks.
Unsurprisingly, security is considered a top concern for many consumers. In fact, data from a recent United Kingdom survey indicates that security is the third most important information for consumers making purchase decisions. Moreover, the data shows that “Among those who didn’t rank ‘security’ as a top-four consideration, 72% said this was because they expected security to already be built into devices that were already on the market.”
What is the OWASP IoT Top 10 List of IoT Vulnerabilities?
The OWASP top 10 IoT vulnerabilities list is a resource for manufacturers, enterprises, and consumers. Its goal is to help organizations and individuals gauge the acceptable risk and make an informed decision about releasing or purchasing a product.
The OWASP Internet of Things Project brings us the OWASP IoT top 10 list of IoT vulnerabilities in an attempt to help manufacturers, developers, and consumers alike understand IoT security risks better and take appropriate actions to mitigate them.
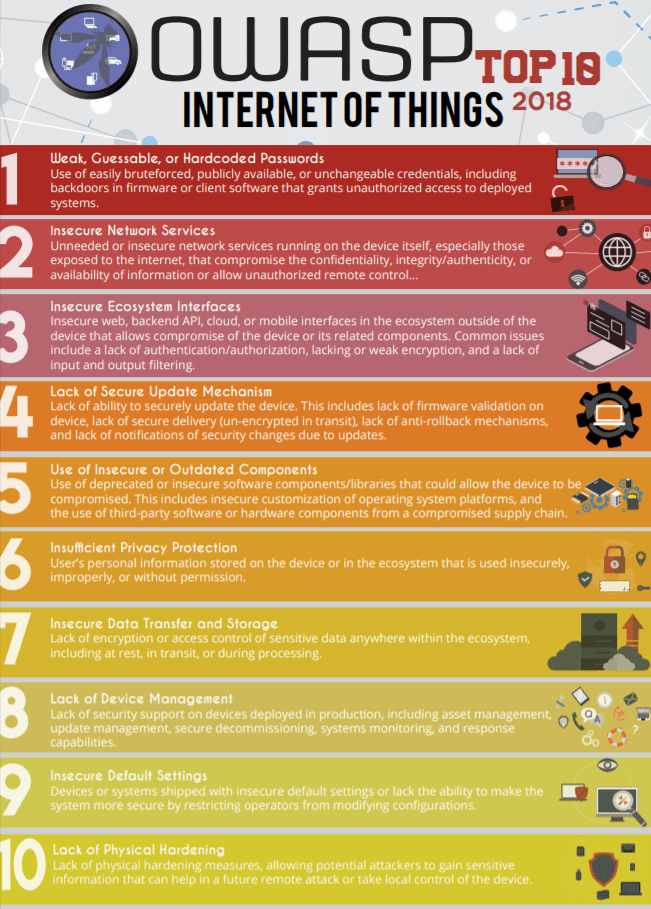
1. Weak, Guessable, or Hardcoded Passwords
It’s easy to figure out why this concern comes in No. 1 on the OWASP IoT top 10. Most IoT devices, especially the ones that come with web interfaces, are not reconfigured to allow users to change default passwords, and that leaves them vulnerable to a host of password attacks. Why would an attacker spend time trying to bypass other security controls if your password can be easily guessed or brute-forced?
Another issue is that sometimes there’s no option to change the password for your device, which is a severe flaw when it comes to IoT security. While embedding fixed passwords into smart devices might make life easier for remote technicians, it also does so for hackers trying to gain access to your devices or your network. Furthermore, many IoT products are often released with insecure firmware that contains backdoors for gaining access for debugging purposes.
2. Insecure Network Services
Next on the list of OWASP IoT top 10 vulnerabilities is insecure network services. Network security tools like firewalls, intrusion detection system/intrusion prevention systems (IDS/IPS), unified threat management solutions (UTMs), etc. continue to be relevant even as IoT devices come into play.
IoT security has often been compromised due to unauthorized access (due to default passwords, open ports, etc.) and can potentially lead to these devices being utilized as a part of a larger botnet. Botnets are frequently used to execute threats such as distributed denial of service (DDoS) attacks on targeted websites or network resources.
Some additional ways to keep your device from becoming an unwilling participant in such activities and to strengthen your network security include:
- Turning off unnecessary ports and vulnerable services,
- Having a separate network for smart devices,
- Disabling any services that provide remote access,
- Installing regular updates, and
- Taking care not to connect over insecure networks (like public Wi-Fi).
3. Insecure Ecosystem Interfaces
Insecure ecosystem interfaces are third on the OWASP IoT top 10 2018 list. It was previously divided into three categories — insecure web, cloud, and mobile interface — on the OWASP Top 10 2014 list.
Interfaces like the web, cloud, mobile, or back-end API that allow you to interact with the smart device can have vulnerabilities in the implementation of authentication/authorization (or worse, a complete lack of it), weaknesses in encryption, data filtering, etc. These security flaws can eventually lead to compromising the device or any of its related components.
4. Lack of Secure Update Mechanisms
The concern here is that many IoT devices lack the ability to securely update. This is an area where device manufacturers can really step up their game. In the United Kingdom, for example, a newly proposed law would make it so IoT device manufacturers would need to provide a minimum period of time during which their devices would receive security updates.
But update mechanisms are not always just about installing patches and closing vulnerabilities, which is why they’re on number 4 of our OWASP IoT Top 10 list. They also include implementation of features such as:
- Anti-rollback mechanisms,
- Secure delivery (not sending the update in cleartext, signing the update, etc.), and
- Firmware validation on the device.
With the lack of any secure update mechanism in place, there’s no guarantee that the security of the IoT device is as projected to end-users or as intended by developers.
5. Use of Insecure or Outdated Components (NEW)
Using outdated software or referencing insecure libraries in your code could lead to compromising the overall security of the product. From insecure customizations of the operating system to using vulnerable third-party hardware or software components, IoT vulnerabilities include anything that injects weaknesses into the device can be used as an entry point or leveraged to perpetuate an attack. Moreover, risks associated with a compromised supply chain can tamper with the manufacturing process early on and remain undetected and severely impact the security of the device.
According to an internet security threat report by Symantec, supply chain attacks continue to be a huge part of the threat landscape with an increase in attacks by 78% in 2018.
6. Insufficient Privacy Protection
Next on our list of OWASP IoT top 10 is insufficient privacy protection, which concerns the insecure storage of personal data, processing this information, or its disclosure without the user’s permission. A 2017 study by Cornell University looks into the information that can be gleaned by passive observers (such as ISPs) just by analyzing IoT network traffic — even when that traffic it is encrypted.
Data privacy, specifically where IoT is concerned, is beginning to be addressed through legislative actions. Apart from the concerns mentioned above, collection of consumer data without express consent has been an issue all along. Over collection and over retention of such data, especially now that IoT is such a huge part of our everyday lives, can also lead to compromising our security in the physical world.
7. Insecure Data Transfer and Storage
Number 7 on the OWASP top 10 list is insecure data transfer and storage. It might seem obvious at this point to maintain data security with experts constantly warning us about encryption, data classification, and proper handling of sensitive information — but considering all of the data breaches that we still see in headlines on a daily basis, it’s no wonder why we are still talking about it.
In addition to restricting access to sensitive data in general, it’s crucial to ensure that data is encrypted when at rest, in transit, or in processing. If encryption is not strictly implemented, it leaves data vulnerable and becomes a major IoT security concern if it’s missing from your smart devices.
8. Lack of Device Management
Just as it is critical to know what assets are on your network, it’s equally important to manage them efficiently. Regardless of the size of the devices or their individual costs, if they’re interacting with the network and have access to it, then managing them methodically should be one of your primary concerns. Engaging in network security best practices update management to secure decommissioning, systems monitoring, etc. should be an integral part of the process.
Failure to effectively manage your IoT devices (such as relying on old methods like asset tracking using Excel spreadsheets) can compromise your entire network.
9. Insecure Default Settings (NEW)
The default passwords or device configurations on your smart devices are often insecure. While sometimes it is just negligence on our part that we do not change default settings, at other times, it is not possible to alter system settings like hardcoded passwords, exposed services running with root permissions, etc.
Thankfully, some legislators are fighting these insecure practices. For example, California has a law that requires IoT device manufacturers to set unique pre-programmed passwords or require users to change their passwords before using the devices.
10. Lack of Physical Hardening
Hardening the device against physical attacks protects it against attempts by malicious users to extract sensitive information that can later be leveraged to launch a remote hack or gain control of the device. For instance:
- Debug ports that are usually not removed or disabled leave your devices vulnerable to access by hackers.
- Simply removing a memory card to read its content can reveal passwords or other sensitive data.
- Using secure boot helps validate firmware and ensures that only trusted software can run on the device.
In Summary: Wrapping Up the OWASP IoT Top 10
The list above of the OWASP top 10 IoT vulnerabilities doesn’t come with separate guidelines for various stakeholders but instead takes a unified approach to address IoT vulnerabilities that might be affecting our devices. The OWASP IoT top 10 team specifically adopted this style because there are already intensive guides on IoT security catering to different audiences across industry verticals.
The OWASP top 10 IoT list is published once every two years, so hopefully, sometime in 2020, we’ll see another update and take a look at how things evolved since 2014 when the first list was released.
























 (28 votes, average: 4.21 out of 5)
(28 votes, average: 4.21 out of 5)


No comments