TLS Handshake Failed? Here’s How to Eliminate This Error in Firefox
TLS handshake error can be annoying for users and site admins alike, but fixing it is easy and quick with these 8 fixes…
When you try to open a website, the TLS handshake process takes place in the background between your browser and the website’s server. In general, it’s a quick process that occurs within a fraction of a second. But, sometimes, the process takes longer than usual or fails, and the user sees a “TLS handshake failed” error while visiting particular sites.
This error can have a number of root causes–occasionally, it’s shown while accessing popular websites like Gmail, Twitter, and YouTube! This article will cover multiple tricks to fix the TLS handshake failed error in Mozilla Firefox. We’ll start with the client-side causes of this error (i.e., issues relating to your device or browser as a user) and move on to server-side causes of this error (i.e., issues with the website itself).
Troubleshooting the TLS Handshake Failed Error: Check Device’s Date & Time Settings
What if we told you that one of the most common issues cited for causing TLS handshake failed errors was simply your date and time settings being out of sync? One way this can happen is if you’ve deselected the Adjust for daylight saving time automatically setting. Check to see if the date and time listed are current and that you have On selected for the daylight saving time option (if you live in an area with Daylight Savings Time).
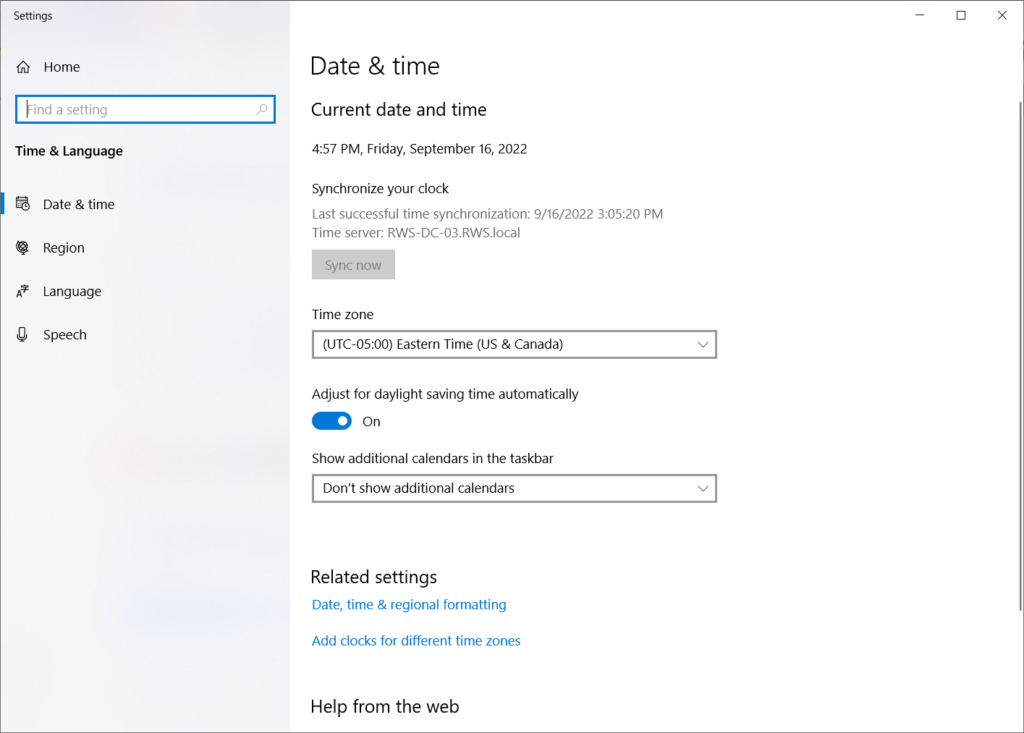
If it’s still not working, try selecting Sync now to see if it resolves the issue. If this doesn’t work, your issue could be browser related.
Troubleshooting the TLS Handshake Failed Error: Is the Issue a Browser Error?
Before we begin, you need to find out whether the issue is with the website’s SSL/TLS certificate or Firefox’s security settings. To do so, open the website in another browser and see which of the following two scenarios best fits your situation:
If You Can’t Access the Website on Other Browsers
If you CAN’T access the website on other browsers as well and encounter a “Your connection is not private” error page. This means that the issue is with the website’s SSL certificate and not the browser itself.
How to Fix the Issue
If that is the case, you, as a website visitor, can compel your browser to ignore the error. Follow the articles below to get rid of the error pages.
- Google Chrome: How to fix your connection is not private error.
- Firefox: How to fix the ‘Warning: Potential Security Risk Ahead’ error.
Reasons Why This Error Occurs
Browsers can show such errors for multiple reasons, including:
- Website’s SSL/TLS certificate is expired, revoked, or misconfigured
- Site hosts mixed content,
- Site’s server is using old ciphers, etc.
Only the website owner or webmaster can solve such issues on a permanent basis. But as we mentioned above, a website visitor can still access the website by tweaking some settings in the browser.
If You Can Access the Website Using Other Browsers
If you CAN access the website in other browsers but not in Firefox, it indicates that Firefox’s security settings are obstructing the TLS handshake process.
Let’s follow the below-mentioned steps to get rid of the TLS handshake failed error in Mozilla Firefox.
Troubleshooting the TLS Handshake Failed Error as Site User
User Solution 1: Change User Profile
According to Mozilla’s definition, “a profile in Firefox is the collection of settings, customizations, add-ons, and other personalization that a user has made or installed into their copy of Firefox.” If the user profile has some misconfigured settings, it might create hurdles during the TLS handshake process. By creating a new default user profile, you can easily eliminate the TLS handshake failed error.
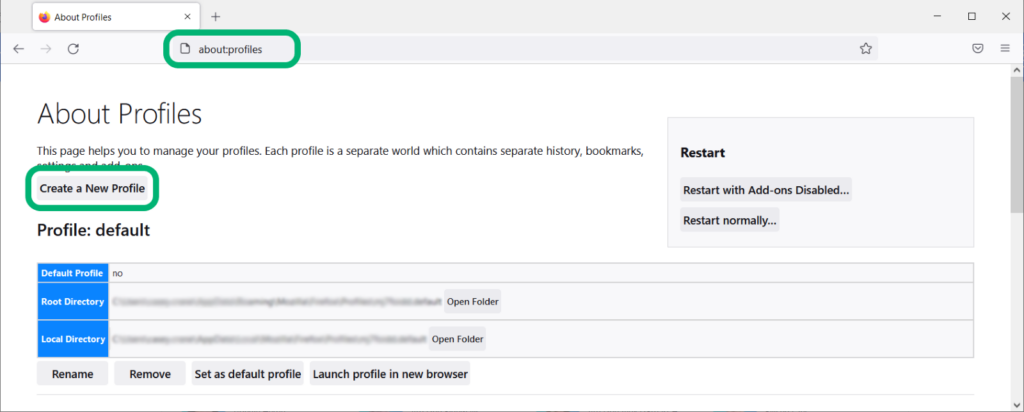
- Type about:profiles in the browser’s address bar.
- On the page that displays, click Create a New Profile at the top.
- A new window named Create profile wizard will pop up. Hit Next. Write down any profile name of your choice.
- Click Finish.
- Relaunch the Firefox browser.
User Solution 2: Delete the cert9.db (or cert8.db) Folder
Whenever you visit a website, Firefox stores the website’s SSL/TLS certificate in its local database. Some webmasters use the self-signed TLS certificate and replace it many times. Because all such certificates are generated for the same domain name, the details (such as the issuer’s name, domain name, public key, etc.) remain identical in all of the certificates.
When a user opens such a website, Firefox tries to fetch the entire collection of SSL certificates that are stored in its cert9 file. Because it attempts to complete the TLS handshake with each certificate, the process gets jammed. You can delete the pre-stored certificates from cert9 (or cert8) files. This step will force Firefox to connect only with the latest TLS certificate the website uses and ignore all other old certificates. This is a solution you’ll commonly see recommended on Firefox support pages:
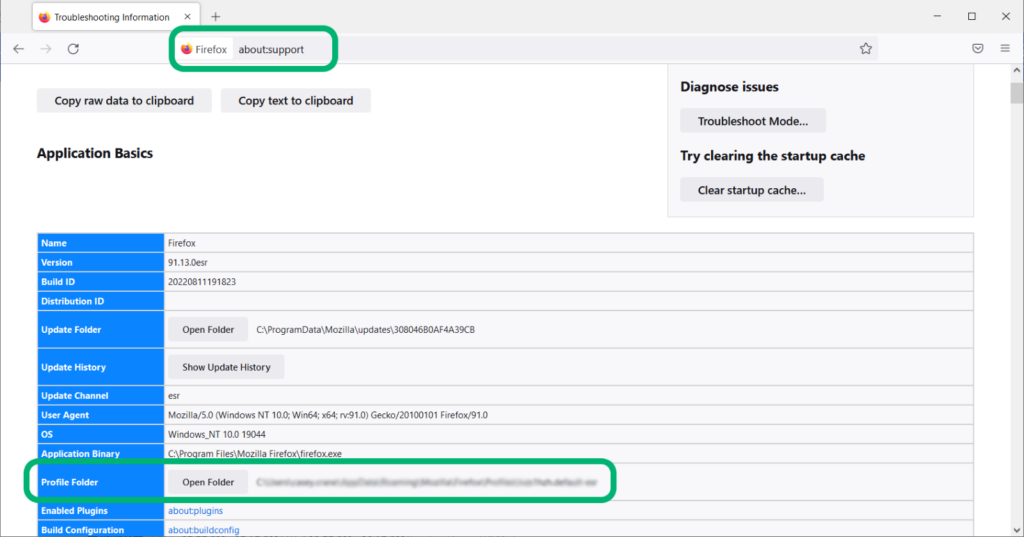
- Copy-and-paste about:support in the browser address bar.
- Locate the Profile Folder row and click on Open Folder.
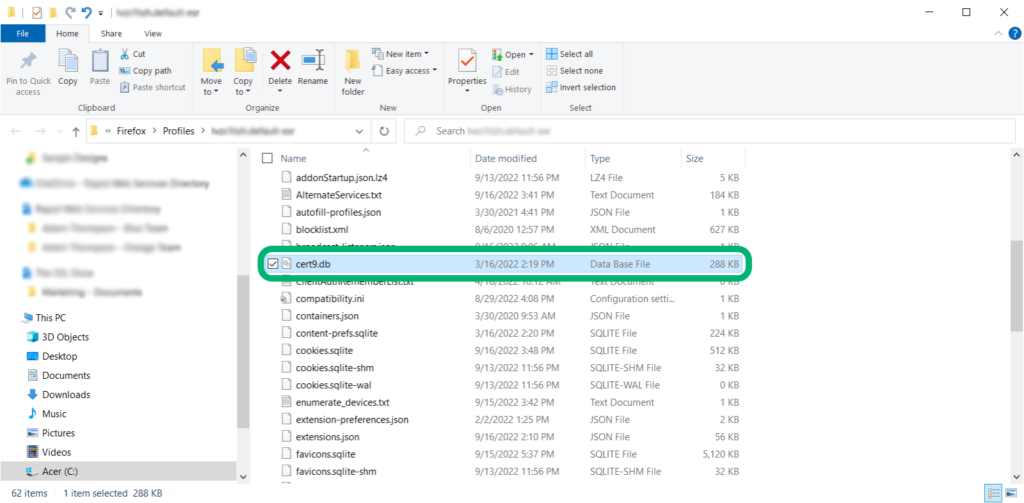
- Find the cert9.db file. (If you can’t find cert9, search for cert8. If you’re using an older version of the browser, the certificates may still be stored as cert8.db instead.)
- Either rename or delete the file.
- Relaunch the Firefox browser.
User Solution 3: Change TLS Version
Many versions of the TLS protocol have been introduced (and, in some cases, depreciated) over time in the cybersecurity industry. All browsers typically try to block the depreciated TLS versions and accept only the latest ones in order to protect their users. So, if the website you are trying to visit is still using the SSL certificate with old algorithms, Firefox will try to block it. This can result in what’s known as a protocol mismatch.
Of course, our recommendation is to make purchases from or share your information with websites that are using the TLS 1.2 protocol as a minimum. (If it’s using TLS 1.3, cool, but TLS 1.2 is still the most commonly used protocol at this time.)
However, if you just want to test and see if an outdated protocol is the error, you can apply the following trick to force Firefox to accept all the TLS versions. (NOTE: Enabling your browser to run TLS 1.0 or TLS 1.1 isn’t something we recommend doing — it’s always better to run TLS 1.2 as a minimum. Always move forward — don’t downgrade your protocol because it’s dangerous.)
To do this:
- Enter about:config in the Firefox address bar.
- Click the Accept Risk and Proceed button. This will result in displaying a page with a search bar at the top.
- Search for security.tls.version.min in the search bar. Press the edit button (i.e., the pencil icon). Type 1 in the box that appears on the right-hand side. Save the settings.
- Now, search for security.tls.version.max and write 4 on the right-hand side. (This will force the TLS 1.3 protocol; setting it to 3 would force TLS 1.2.) Save the settings.
- Relaunch your Browser and see if the changes work.
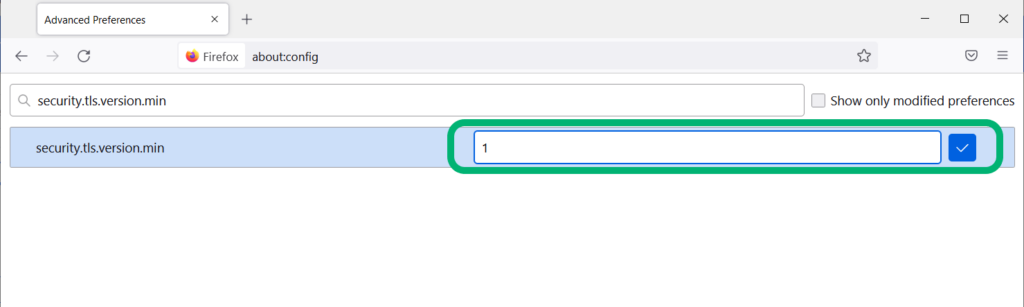
When the security TLS version is set 1 as minimum and 4 as maximum, it forces Firefox to accept all four versions of TLS certificates (i.e., TLS 1, TLS 1.1, TLS 1.2, and TLS 1.3).
User Solution 4: Clear Your Browser’s Cache, Cookies, and Browsing History
Even after the website has resolved TLS-related issues, browsers can still sometimes display various errors. This is because flawed certificates can sometimes remain stored in your browser’s cache memory, causing errors to still pop up sometimes. You can delete the cookies and cache memory to fix it. Here’s how:
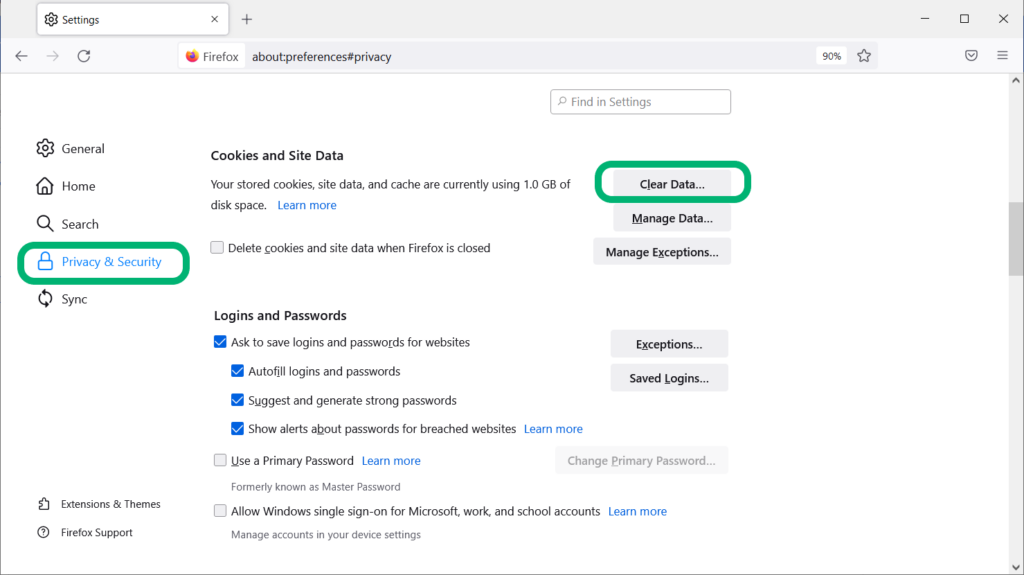
- Search about:preferences#privacy in the Firefox address bar.
- Navigate to Cookies and Site Data section.
- Click on Clear Data.
- Check the options for Cookies and Site Data and Cached Web Content. Hit Clear.
- Back in the main window, scroll down to History. Click the Clear History button.
- Relaunch your browser to see if it resolves your issue TLS handshake failed issue.
User Solution 5: Reinstall Firefox
Still can’t get rid of this pesky TLS handshake error? If you’ve not been able to figure out the reason or fixed it with any of the steps we’ve covered, reinstalling Firefox is the only option you have left. This will reset all the settings and update all the security components.
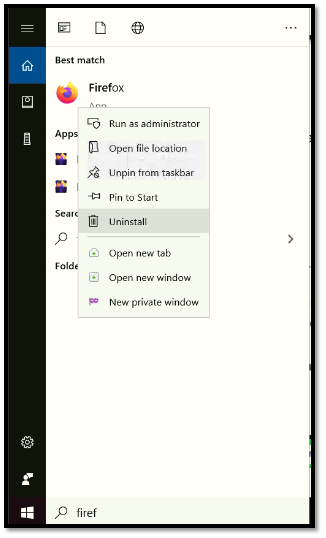
- Search for Firefox in the Windows search bar.
- Right-click on it and select Uninstall.
- Now, use another web browser to go to Mozilla’s official site. Here, you’ll need to download and reinstall the Firefox browser.
If this step and the others we’ve mentioned doesn’t fix the issue, then it means that there’s an issue on the server side. Unfortunately for you, this is something beyond your control. But you can (and should) reach out to the website’s admin to report the issue to make them aware.
Troubleshooting the TLS Handshake Failed Error as a Website Admin
We’ve seen the potential fixes that site users can try to see if it addresses the TLS handshake or HTTPS related errors. But what can you do as a website owner or admin if the issue is on the server’s end? You can run through all of those checks yourself using your Firefox browser to see if it’s a browser-related issue. But if it’s not, here are a few tricks you can try to mitigate this issue on your server.
Admin Solution 1: Check for Certificate-Related Errors (Including Expiration and Revocation)
This is No. 1 on our list for a good reason. Certificate-related issues are among the most common causes of TLS handshake failed errors. For example, if someone visits your website and your certificate recently expired or was revoked, it can cause the server to display TLS handshake-related errors to the user. This is bad news for your current or prospective customer, and bad news for you as a site owner.
Here’s what a basic overview of a valid SSL/TLS certificate looks like in Firefox:
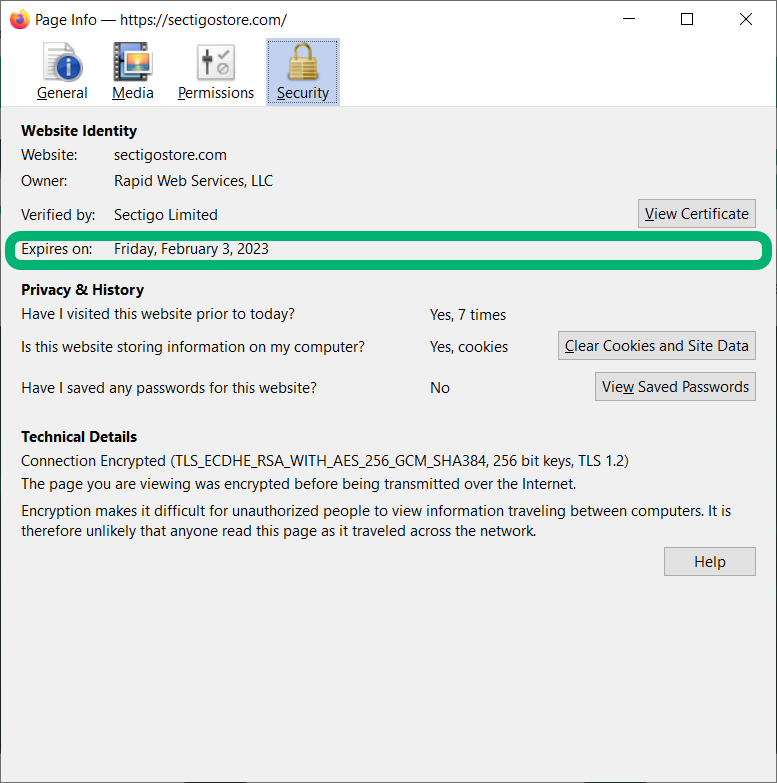
See how the expiration date is right up front and center? It’s because the certificate’s validity really is that important. Here’s a more in-depth look that also shows both the precise moment when the certificate is set to expire but also when it was issued:
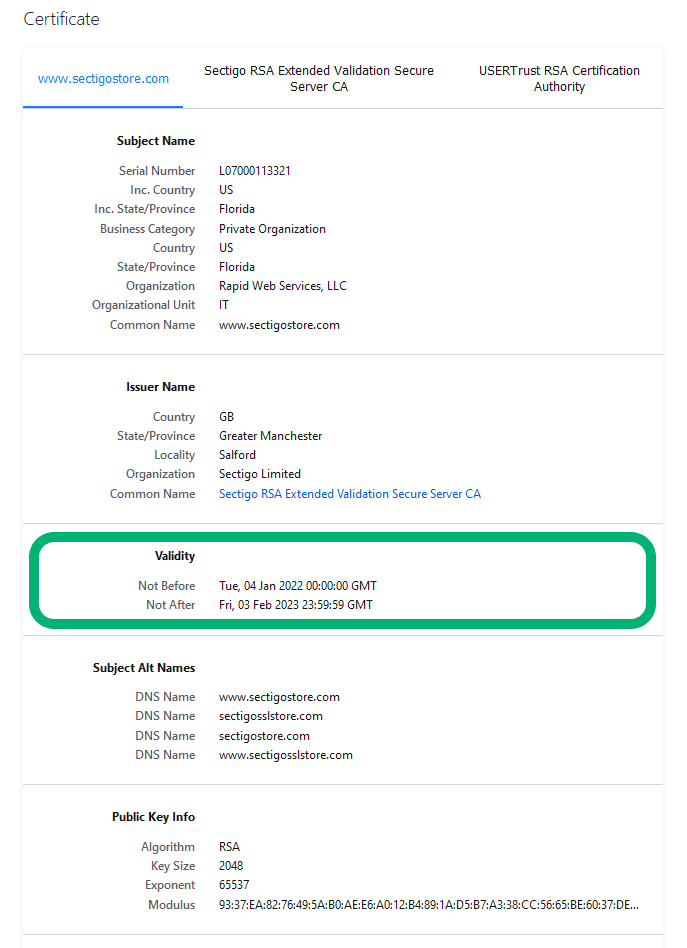
You’ll sometimes come across expired SSL certificates on websites because of two key reasons:
- Digital certificates only have a one-year lifespan (398 days). This means that once they expire, they no longer provide you with the secure, encrypted communication channel you’re accustomed to on your site.
- Some site owners don’t properly manage their certificates. When this happens, it means they’re not keeping close tabs on what’s going to expire and where the certificates are located. This results in certificates expiring without the site owner realizing it until it’s too late.
The best way to deal with this problem is to stop it from happening in the first place through certificate life cycle management. When know where all of your digital certificates are and have a clear of your IT infrastructure, you’ll know:
- What certificates you have,
- What they’re used for,
- Where they’re deployed,
- When they expire, and
- Which ones have been revoked.
This way, you can renew your certificates before they expire and do what needs to be done to take care of revoked certificates.
Admin Solution 2: Check for Any Errors in Your Certificate Trust Chain
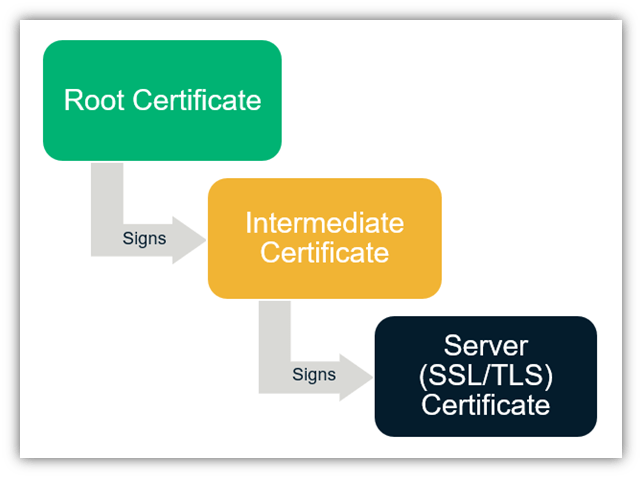
Some TLS handshake errors go by different names depending on their cause. For example, in some cases, you might see an error message talking about an invalid certificate chain.
Every SSL/TLS certificate is part of a larger line of certificates that form what’s known as the SSL certificate chain or a “chain of trust.” This means that the website certificate, also called a leaf certificate, ties back to an intermediate certificate, which then ties back to an issuing root certificate. They’re tied to one another through the use of special digital signatures that are based on public key cryptography. This creates the “chain” that your site visitors’ browsers check on the back end to ensure the authenticity of your certificate (and, therefore, the authenticity of your website).
Not sure where to find this information? Look in your certificate details. The three certificates in SectigoStore.com’s certificate trust chain are marked at the top, and down below, you’ll see the circled information for the intermediate CA that issued and digitally signed our website certificate.
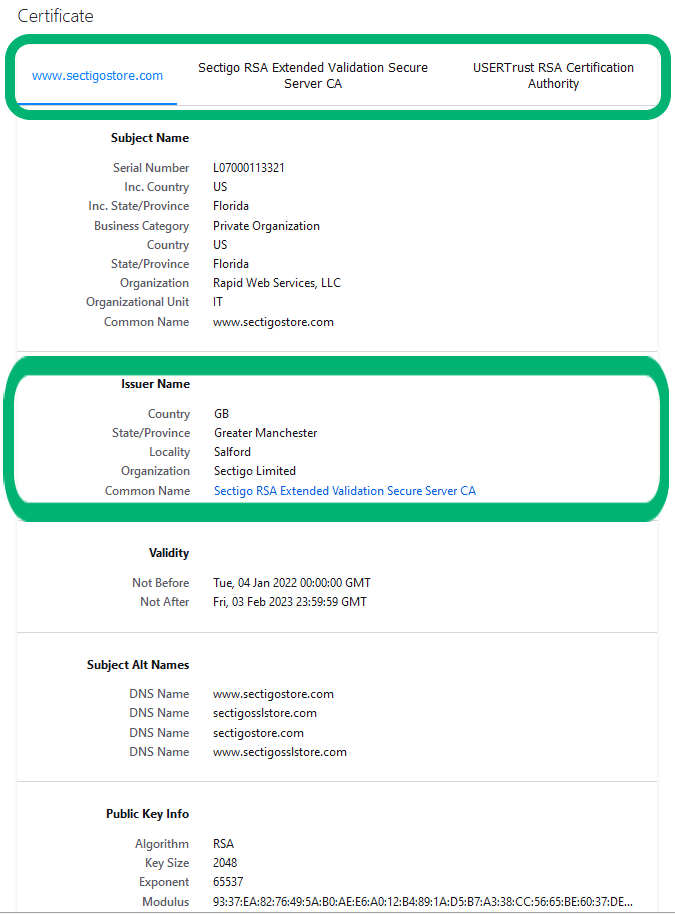
If, for some reason, a user reports that they’re receiving a TLS handshake error, it’s possible that their browsers are unable to locate your intermediate certificate (i.e., the middle certificate in the trust chain). If this happens, you’ll need to install the intermediate certificate on your server. To do this, go to the website of the certificate authority that issued the SSL/TLS certificate for your website.
If you purchased your certificate from SectigoStore.com, you would have been sent your intermediate CA certificate bundle. Otherwise, check out our Sectigo Intermediate Certificate Installation Guide to find directions on where to download and how to install your intermediate CA bundle on your server. (Directions differ depending on which platform you use.)
Admin Solution 3: Protocol or Cipher Suite Mismatch Between Your Server and Users’ Clients
Servers and users’ web clients don’t always see eye to eye, per se. What we mean by that is that some clients don’t use protocols or cipher suites that are supported by your server. While we say that the client and server have to agree on which protocol to use as part of the SSL/TLS handshake process, the truth is that the server is truly the one choosing which internet protocol or algorithms to use.
No, the answer isn’t for you to downgrade your server to an earlier protocol (unless you are mandating use of TLS 1.3). Doing so would just be foolish and leaves your site and data at risk of being compromised by enterprising bad guys. Instead, encourage users to update their browsers to support TLS 1.2 as a minimum. This way, you’re supporting all secure options.
The same can be said about cipher suites. If your server is using ciphers that aren’t supported by users’ browsers, then the user needs to ensure that their browser is updated and patched. It’s not your responsibility to use deprecated algorithms because it’ll leave your site at risk of compromise. Instead, encourage users to use the most up-to-date version of Firefox and also set your server to support valid cipher suites. This ensures you’re supporting all secure options, if possible, and more clients will be able to access your site or service.
Final Thoughts on Resolving the TLS Handshake Failed Error
We hope one of the tips in this article has helped you mitigate the pesky TLS handshake failed error. The TLS handshake is part of a larger process that results in creating a secure, encrypted HTTPS website connection. And if you’re wondering whether HTTPS is necessary, then the answer is yes in virtually all cases.
If your site collects any type of personal or sensitive user information (think usernames, passwords, personally identifying information, etc.), or if you simply want it to rank on Google, then enabling HTTPS is a must. Yes, Google views HTTPS as a ranking factor for all websites.
As you can guess, ensuring that the TLS handshake is working properly is invaluable to the security of your website and your reputation and relationship with customers.
If you’re a website owner and are still having problems with your website showing this error, be sure to reach out to our Support team.
This article was co-written by Casey Crane and Medha Mehta.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security