Top 25 Recommendations for Small Business Cyber Security
When it comes to small business cyber security (and a whole bunch of other things), you’re only as strong as your weakest link! You can rest assured (or maybe not) knowing that hackers will find a way to breach your network’s security via the route that offers the least resistance. Not to freak you out, but if you’re still using your grandmother’s maiden name as your password, it should come as no surprise that a hacker could guess it.
Security professionals have urged netizens about using strong passwords and issued warnings against phishing attacks so many times it’s almost a cliché!
Even for small businesses, SMB cybersecurity should be a priority, at least if we’re to believe the statistics. Score reports that 43% of cyber attacks target SMBs. According to another report by Juniper Research, SMBs account for only 13% of the overall cyber security market in terms of expenses on security products. Security analysts predict that data breaches will triple each year over the next five years with an average annual increase of 9% in terms of budget allocation for cyber security.
There’s a general apathy towards cybercrime and a false belief that if you’re an SMB, you can fly under the radar of cybercriminals. Of course, this thought is a lie we choose to believe — according to SiteLock, a website is exposed to cyber attacks more than 50 times a day on average. Therefore, it comes as no surprise that SMBs, especially the ones without a security strategy in place, are desirable targets for cybercriminals.
Before discussing cyber security solutions for small businesses, let’s look at some of the biggest security threats they face:
- Ransomware Attacks
- Phishing Attacks
- Privilege Escalation Attacks
- Fraudulent Apps
- Weak Passwords
- DDoS Attacks
- Social Engineering Attacks
We have prepared a list of recommendations, keeping in mind small business cyber security needs which will help you accomplish your security goals.
Small Business Cyber Security Solutions
If you’re an SMB and cybersecurity is near the top of your list of priorities, read on to find out how to limit exposure to your sensitive data and secure your network.
1. Conduct Cyber Awareness Training for Employees
Small business cyber security efforts need to be the responsibility of every employee within your organization. More often than not, humans are the weakest links — especially when it comes to social engineering attacks. With regular repeated training on best practices and security pitfalls to avoid, employees will gain the knowledge they need to develop a security-conscious mindset.
2. Streamline Your Patch Management Process
Cybercriminals are aware that not all companies immediately install updates to prevent a new attack. That’s why it’s vital to keep your systems up to date. Update your software (including your OS) regularly on all the devices and turn on automatic updates where you can. This includes updating and patching your website software and plugins as well.
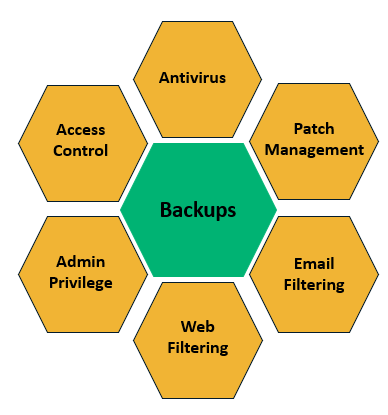
3. Back Up Your Critical Business Data
One of the most foolproof ways to prepare your defenses against ransomware attacks is to have data redundancy. If your data is taken as hostage, having multiple backups off-site or on-premises helps to minimize the impact on your business and operations.
4. Use Firewalls, WAFs, IDS, IPS or a Unified Threat Management System
Depending on your network design and architecture, it’s essential to have some form of traffic monitoring and filtering tool set up as part of your small business cyber security defense measures. This helps you to assess the traffic flowing to and from your trusted internal network and the outside internet.
5. Secure Remote Access to Prevent Unauthorized Use
Apart from using firewalls and reviewing server logs for malicious activities, ensure that unauthorized users can’t access your machines remotely. Restrict functionalities based on access control lists, use a virtual private network (VPN) for encrypted communication, and implement multi-factor authentication (MFA) to prevent unauthorized access to the business network.
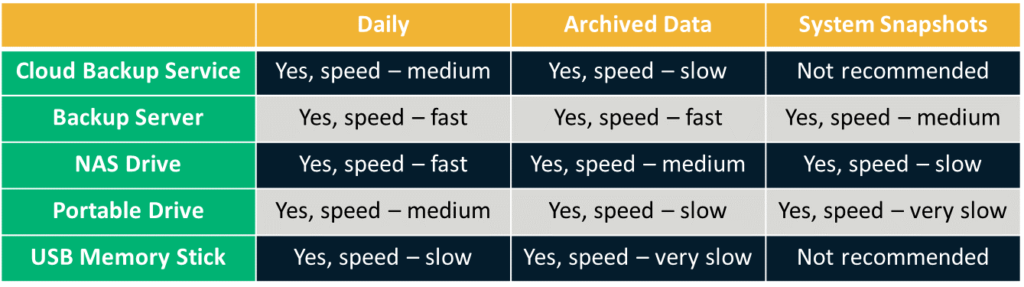
6. Run Regular Antivirus and Anti-Malware Scans
Invest in a reputed antivirus product. It’s critical to have the latest version installed on all devices on the network and to run daily scans. You can also use free open source tools like ClamAV if you’re comfortable with using a command-line interface.
As far as website security goes, investing in an integrated solution like CodeGuard that scans for malwares, performs automatic updates, creates backups, etc. could prove to be useful.
7. Invest in an Anti-Ransomware Software
According to reports from Beazley Breach Response (BBR) Services, 71% of the ransomware attacks in 2018 were targeted at small businesses. Remote Desktop Protocol (RDP) was used as one of the most common attack vectors, which is why it is vital to lock it down. Using anti-ransomware, creating and storing backups at multiple locations, and using good judgment to avoid falling prey to social engineering attacks are some of the countermeasures that can be implemented.
Avast Free Ransomware Decryption Tools and Trend Micro Ransomware File Decryptor are some of the free alternatives in the market. You can also check out the decryption keys repository at nomoreransom.org.
8. Use VPN When Connecting to Your Business Network
Enforce the use of VPN when third-party vendors or employees need to connect to your business network remotely. It’s inherently unsafe to connect to the internet via untrusted connections such as public Wi-Fi due to eavesdropping, man-in-the-middle attacks, and “evil twin” phishing attacks. But if you must use public Wi-Fi, then be sure to use a VPN so an attacker on the network can’t sniff your traffic.
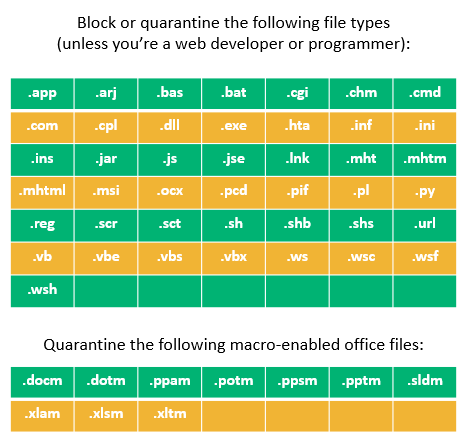
9. Use Email Filtering to Block Malicious Files
Consider blocking the filetypes you would never require as a business. Block any attachment with executable content to prevent accidental execution of malicious scripts on your devices. Here is a list of file types to consider blocking or quarantining:
10. Use Web Filtering Tools to Prevent Ads from Executing
Block web pages or parts of it that contains scripts, advertisements, viruses, etc. You can do this through the use of Websense Web Filter solutions or OpenDNS.
11. Use DNS Filtering to Block Sites With Malware
Use DNS filtering solutions that block access to sites known to be infected with malware or viruses. Quad9 is one such free solution that you can use.
12. Don’t Grant Admin Privileges to Employees
Deploy identity and access management (IAM) tools such as CyberArk, OpenIAM, or WSO2 to grant access based on pre-defined needs. Implement application whitelisting to block programs that are not on the list of authorized software. Employee accounts should be running as standard users where they can’t install software or run unapproved applications. Grant administration privileges to trusted and limited personnel only if there is a business justification.
13. Limit Permissions to Thwart Privilege Escalation Attempts
Use an access control list (ACL) to limit access to resources on a need-to-know basis. An ACL specifies the permissions or the rights a user has to access system objects such as files and directories. Regularly review and decommission old user accounts.
14. Implement a Strong Password Policy
Implement a strong password policy that details minimum restrictions on complexity, requires the use of multi-factor authentication, disallows the use of old passwords, manages account lockouts, etc. A password manager like Dashlane or LastPass can be used to manage passwords across several accounts.
You can also perform a quick search for tools that review if your accounts have been compromised. For example, haveibeenpwned.com checks whether your email account was compromised in a security breach.
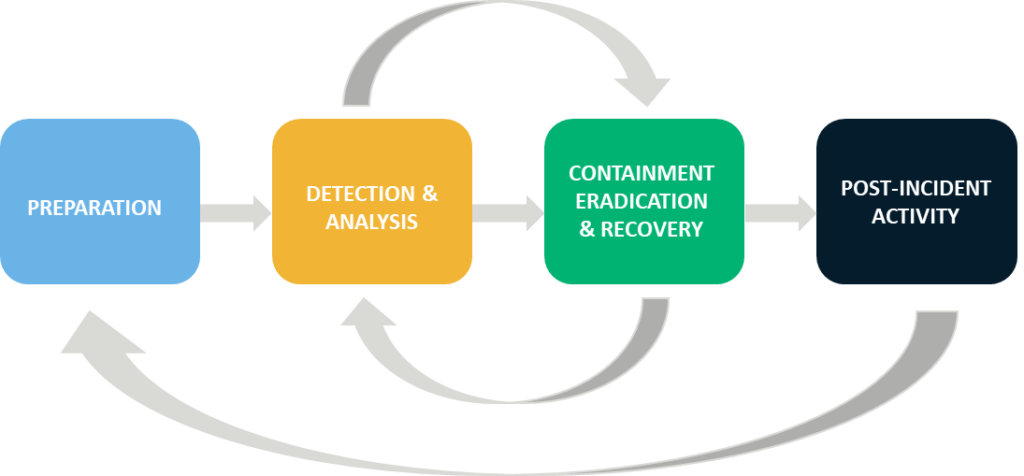
15. Formulate a Security Incident Response Plan
Spend some time figuring out how the organization will deal with a security incident just in case it occurs. Define a process, escalation points, recovery strategies, roles and responsibilities, etc. Get guidance from already established frameworks and checklists.
16. Invest in Cyber Insurance
Consider investing in an insurance plan to protect your business against any unprecedented losses due to a cyber attack. Cyber insurance can cover a wide variety of costs, including:
- data theft on third-party systems,
- loses due to threat of extortion,
- incident management expenses,
- third-party damages such as website defacement,
- intellectual property rights infringement.
17. Establish Security Policies and Practices to Be Followed at an Organizational Level
Get your employees to sign off on adhering to security policies laid down by the company at the time of appointment. Clearly outline data classification policies, disposal of confidential documents after use, clean desk policy, etc. Also, have your learning and development (L&D) team set up mandatory security awareness training to ensure your employees have a fair understanding of what these policies entail.
18. Restrict Unauthorized Physical Access to Computers and Network Devices
Discourage employees from helping with tailgating. No laptops should be left unattended without being locked to the desk.
19. Create a BYOD or Mobile Device Action Plan
Unless the devices are company-issued and can be wiped remotely, restrict the information that can be accessed via mobile devices since they can be left lying around or stolen. They pose significant security risks, especially if they are given access to the corporate network. Apart from access to emails over encrypted channels, block downloading client information, or any other confidential documents.
20. Secure Your Networks
When it comes to small business network security — besides blocking unused ports, using firewalls and VPNs — it’s crucial to configure your Wi-Fi to use the correct configurations. Enable WPA2 / WPA3 encryption on your router, change the default login credentials and the SSID broadcast name. Update the router firmware regularly. Be sure to turn off WPS (Wi-Fi Protected Setup) since it has a well-known security flaw that can easily be exploited to gain access to your network.
21. Block Removable Media or External Storage
Block removable media or restrict access to USB ports to prevent the unauthorized transfer of confidential data. This also helps to prevent malware and viruses from being introduced from an external source into the network.
22. Perform Vulnerability Assessment and Penetration Testing
You can use free tools like Vega to scan your website for vulnerabilities. If, however, your website accepts credit card payments, you’ll need to run vulnerability scans using a PCI approved scanner such as HackerGuardian.
When it comes to penetration testing, this process can be done by a security analyst using manual methods or semi-automated tools. Tools like Wireshark, Nmap, or even frameworks like Metasploit or Immunity Canvas can be used. These assessments can be done on a quarterly or annual basis depending on how critical your business is. You might need to hire a reliable security professional who can perform these tests.
23. Use SSL/TLS Certificates to Encrypt Your Website Traffic
Always use HTTPS on your websites to ensure that the communication channel between the client browser and your server stays secure. Installing SSL/TLS certificates on your web servers not only provides you with encrypted channels, but it also asserts your identity to the clients. It establishes trust in your customer base and adds to your brand value.
24. Use S/MIME to Encrypt All Emails Containing Sensitive Data
Emails are not the most secure way to communicate. S/MIME (Secure/Multipurpose Internet Mail Extensions) changes that by allowing you to encrypt and sign your emails. This way, the recipient can be assured that the message hasn’t been altered and really was sent by you. Pretty Good Privacy (PGP), an old standard for emails, might require plugins but S/MIME is built into most email clients.
25. Frame a Business Continuity and Disaster Recovery Plan
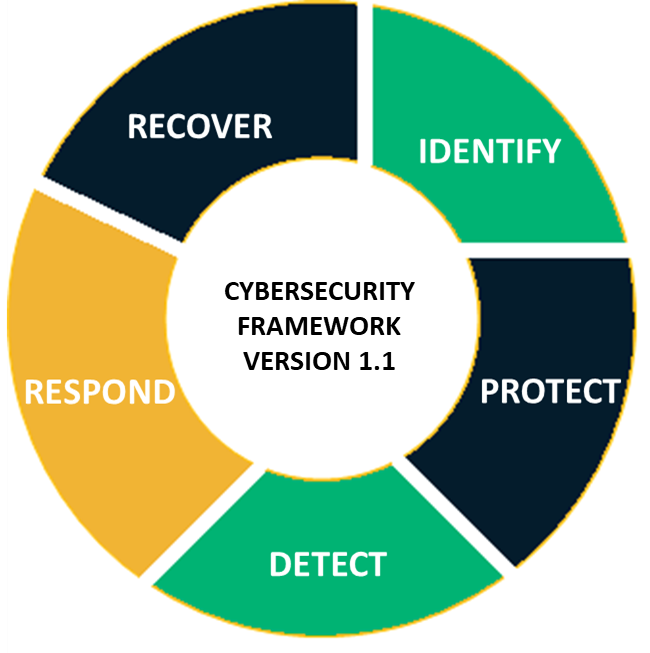
When all is said and done, no matter how strong your cyber defense is, there’s always a possibility that a cyber attack could entirely cripple your network. If you wait for the day when you’re attacked to come up with a plan, chances are you’ll lose a lot of your money along with your cool. Build a comprehensive, well-documented strategy along with backup and recovery plans with detailed steps to bring up critical systems, BC/DR team details, specialist contact details, etc.
Final Thoughts
To summarize, when it comes to cyber security for small and mid-sized businesses, using a few necessary security solutions, being cautious and using good judgment goes a long way. While it is understandable that having high-end security solutions might not be feasible, it’s essential to realize that there are several equally good open source and affordable alternatives.
No matter what you choose, there are always costs involved with cyber security. The question is whether you invest it in securing your organization’s network or in rebuilding brand image after a breach.
























 (66 votes, average: 4.76 out of 5)
(66 votes, average: 4.76 out of 5)






No comments