Top 5 Key Considerations for Secure Remote Access
Remote work has increased substantially due to the COVID-19 pandemic. But Ponemon Institute’s data shows that the move to remote working has negatively affected organizations’ IT security — only 44% of respondents believe in the effectiveness of their organizations’ security measures. But what do you need to know to implement secure remote access? Let’s break it down
As COVID-19 made its way to every corner of the world, more and more organizations encouraged their employees to work from home. In fact, Owl Labs report that 70% of full-time employees are working remotely during the COVID-19 pandemic. But with remote work comes a greater risk from cyber threats. This is why businesses and organizations of all sizes should make secure remote access a priority
According to the NTT Threat Intelligence Report, 88% of surveyed cybersecurity professionals agree that cyber threats have increased due to the pandemic. Combine this with the increase in remote work and you have a recipe for disaster if appropriate security measures aren’t in place.
In this article, we’ll look at the top five considerations for implementing and maintaining secure remote access within organizations.
Top 5 Considerations for Secure Remote Access Control
Secure remote access means using robust security solutions and strategies to establish a network that only authorized personnel can access from wherever they are. This means it should be impenetrable by non-authorized people. To achieve the most secure remote access, organizations must work on two fronts — both at the employee and enterprise levels.
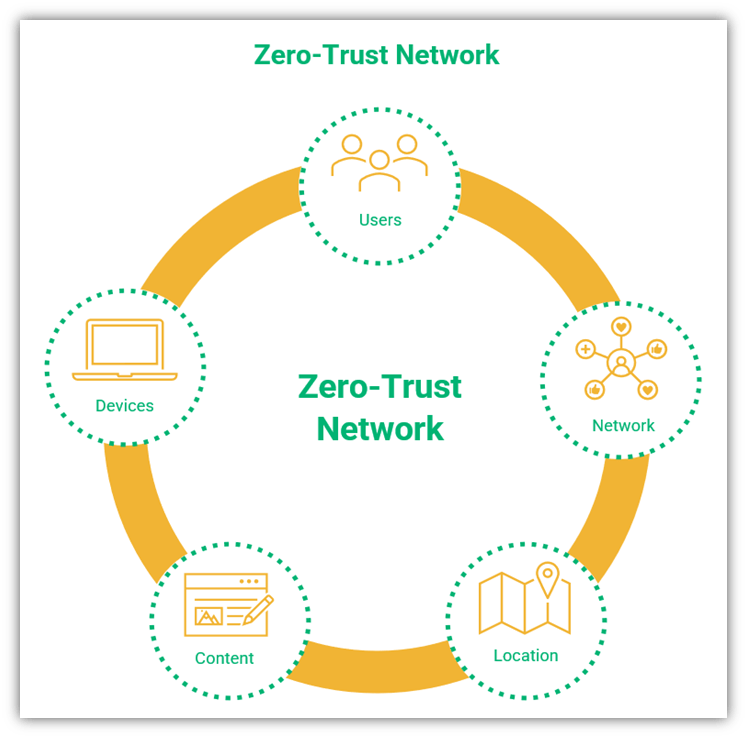
1. Use the Zero-Trust Model
A zero-trust model limits the access of information to employees on a need-to-know basis. So, if an employee doesn’t need access to a particular piece of information, they don’t get authorization to access it. With a zero-trust model, even the most trusted employees don’t have access to information they don’t need for their job.
At its core, zero trust is about minimizing your attack surface to mitigate risks to your systems and the sensitive data they contain. There are five areas that can be controlled in a zero-trust environment:
- Users: Management decides what information should be shared with each employee, and users are verified before access to the network is granted. Additionally, the internet protocol (IP) address of the network location is hidden to increase security. Through their IT staff, management has centralized control over the entire network and the information shared thereon.
- Devices: The organization defines the devices that employees can use to access sensitive data. For instance, management can make it so an organization’s sensitive data can only be accessed via company-issued devices. If an employee tries to access this data from any other device, they won’t be able to do so.
- Location: The organization can make sensitive data available in certain locations only. For example, you could make some sensitive information accessible only in the company headquarters. If they are not on premises, access to the information or resources can be restricted. This restriction protects the data from theft or compromise via man-in-the-middle attacks. When sensitive information doesn’t travel over insecure channels, threat actors have limited opportunities to gain unauthorized access.
- Content: As well as limiting access to data, a zero-trust model can also restrict users from accessing specific websites, like non-HTTPS sites or sites likely to invite phishing activity, like gambling or adult websites. Often, such websites are infested with malware, so restricting access to them ensures the safety of company data.
- Network: An organization can require employees working remotely to use a company virtual private network (VPN) or other secure networks. Using an insecure network can leave the organization vulnerable to man-in-the-middle attacks.
With a zero-trust model, management can be certain that no unauthorized person is accessing sensitive data. It’s important to conduct audits from time to time to determine if the strategy is working efficiently.
2. Protect All Endpoints (Including Servers and Other Critical IT Infrastructure)
When setting up secure remote access, it’s vital to ensure that both endpoints are as protected as possible. Often, companies secure the devices on their end but fail to do the same for their employees’ devices that connect to their network. Allowing employees to introduce their insecure or potentially infected devices to your network can be a liability for the company — if their devices aren’t secure, then the network isn’t secure, either.
Endpoint security used to be as simple as installing antivirus software on endpoint devices. However, with the rise in malware threats, your organization’s overall defenses have to be upgraded, too (i.e., using an antivirus alone isn’t enough). Defense systems need to be comprehensive and multi layered, ranging from powerful anti-malware software and regularly systems patches and updates to the use of network security measures like firewalls and secure authentication measures.
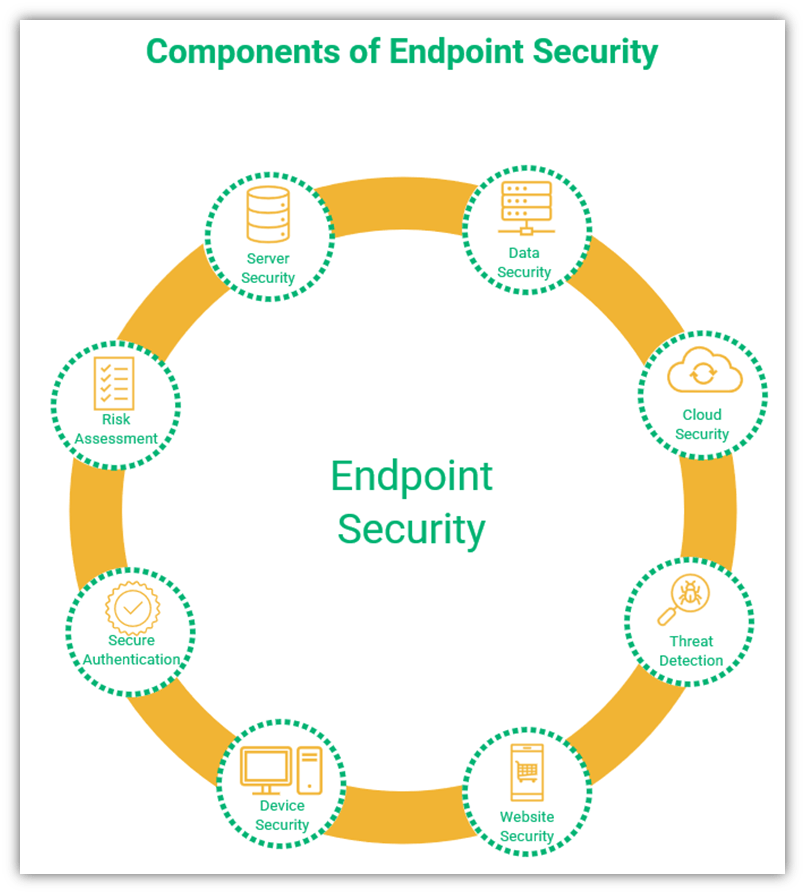
Let’s explore several critical components of endpoint security:
Server Security
The server is connected to all remote employees, and stores most of the data within an organization. Therefore, the server must be secured with firewalls and anti-malware software. Server hardware should also be updated regularly to mitigate the vulnerabilities that patches aim to fix. Access to the server should be granted only to those people who need it to do their jobs.
Data Security
Company data, in motion and at rest, should be protected. The use of secure protocols like TLS, HTTPS, FTPS, SFTP etc., can help you protect data in motion. Data at rest can be protected by using encrypted drives.
Cloud Security
Access to data stored in the cloud should be based on the zero-trust model, with access granted only after proper (and continuous) verification of all users and devices. When you opt for third-party cloud providers, it’s crucial to vet their security features before you make a contract with them. Many cloud service providers have add-on security features, including penetration testing, perimeter firewalls, intrusion detection system, and encryption for data-at-rest. These security procedures protect your data against cyber attackers.
Threat Detection
Continuous threat detection exercises should be carried out in your network systems to identify and eliminate threats as quickly as possible. These can be conducted by in-house teams or external security experts.
Website Security
Every organization’s website should have a valid TLS certificate to protect its sensitive company and customer data. If you accept online payments or collect customer data, it’s your legal obligation to protect this data. Regulations like GDPR, CCPA, HIPPA, and PCI DSS are designed to maintain citizens’ privacy. If your organization suffers a data breach as the result of noncompliance, you’ll likely face fines, lawsuits, reputational harm, and other damages as a result.
Device Security
All devices used by employees, including IoT devices, must have adequate malware protection, firewalls, and endpoint security solutions. One way to help make your devices more secure is to whitelist (allowlist) applications that can be used on company devices and block other apps from being installed. Plus, restrict the use of secure remote desktop applications to admin users only.
Most people are not as conscious about securing their mobile devices as they are about securing their laptops and desktops. This makes mobiles a huge potential target for cybercriminals. Often, mobiles are used as the second factor of authentication for MFA. If mobile is lost or stolen, care should be taken to secure the accounts before the criminals hack them. Make sure your employees use their mobile in a secure and safe way.
Secure Authentication
Secure authentication is the first line of defense against a cyber attack. Despite having every other safeguard in place, your network and systems might still be vulnerable to cyber attacks if your authentication measures are insufficient. Follow certain rules to have a stronger authentication for your networks:
- Passwords: Use stronger and longer passwords with special characters, numbers, and capital letters
- Passphrases: Use passphrases instead of passwords. Passphrases are easier to remember and use
- Multi-factor authentication: Multi-factor authentication (MFA) for logging into your accounts is a much more secure way than passwords or passphrases
- Passwordless authentication: Passwordless authentication is a method of verification using two types of factors – ownership factor and inherence factor. This method provides a much robust security as a combination of ownership (something you have) and inherence (something you are) is used.
Risk Assessment
Even after following all these steps, continuously assessing your organization’s cyber security risk is crucial. This process entails conducting audits of network activities, software, and hardware at regular intervals to alert the organization to developing problems and potential threats.
3. Raise Cybersecurity Awareness Among Employees
Cybersecurity awareness involves training your employees to consciously think about their actions while working online. It’s crucial to update training regularly and follow up on whether employees are adhering to the company policies. Employee security training should cover:
- Guidance on good password practices
- Data privacy and confidentiality policies
- What devices to use and how to keep them secure
- Guidance on securely updating devices and software
- Using multi-factor authentication (MFA) for accounts and devices
- How to spot social engineering and phishing attempts, dodgy websites, and other threats
- What to do if an incident occurs
4. Protect Data in Transit
Data in motion means data as it moves from one place to another. This includes the internal transfer of data between endpoints as well as data transferred to and from a remote server. Data in transit is vulnerable to man-in-the-middle attacks, so creating a secure channel to transfer this data is imperative. One of the best ways to protect this data in motion is by using SSL/TLS certificates.
Transport layer security (TLS) certificates, or what are commonly referred to as SSL certificates, verify the sender’s identity and create a secure channel for communication over insecure channels like the internet. There is a much greater risk of data breach without sufficient transport layer protection.
The following chart data from NTT highlights the risks of data exposure through insecure connections in various sectors:
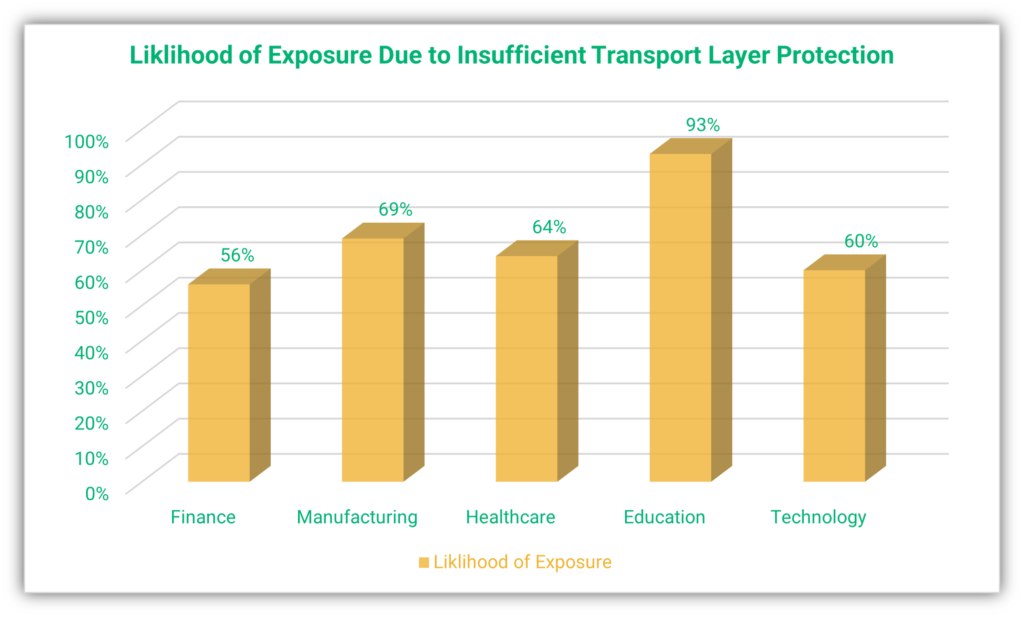
Data source – 2021 Global Threat Intelligence Report by NTT
The level of security depends on the version of the TLS certificate used. TLS 1.2 offers better security than TLS 1.1, and TLS 1.3 offers higher security than TLS 1.2.
It’s important to note that the TLS certificate must be valid. An expired certificate or a certificate with a compromised key doesn’t provide sufficient security. So, renew all certificates before they expire and upgrade when necessary. Also, be sure to follow certificate management best practices to ensure you always know what certificates you have, where they’re located, who’s responsible for them, and when they’re set to expire.
5. Set Up a Secure Network Connection
Another way to prevent cybercriminals from accessing your network is to use a VPN. This service allows employees working remotely to connect securely to your network. Before the COVID pandemic, Keeper Security reported that 22% of employees worked from remote places. After the pandemic began, they reported that 58% employees worked remotely. The current situation has made the security of remotely connected devices all the more important. So, when we speak of any type of security, we mean the security of the remote employee network also.
Network security refers to the provision of a secure connection for the transfer of data from one node to another. Network security for secure remote access is much more than the protection of data in motion, and includes the following:
Set Up Hardware Controls
Hardware controls include protection of routers, cables, devices, and all other kinds of hardware used in the organization, whether in offices or in remote locations. Hardware should only be purchased from and maintained by authorized vendors to maintain the integrity of the system. When the employees are working remotely, extra care should be taken to implement strong security measures for the devices used by them.
Implement Software Controls
Software controls involve buying, implementing, updating, and discarding software in accordance with the organization’s security needs. Software must be kept updated to avoid security threats, as outdated software is full of vulnerabilities that cybercriminals love to exploit.
In the case of employees using their own devices (i.e., bring your own device, or BYOD environments), only vetted applications and websites should be allowed on the device. Sometimes, insecure applications and websites can infect the device and, in turn, the company network.
Put Administrative Controls in Place
Administrative controls are also crucial for creating secure remote access. Management should authenticate all users, what information is shared with each user, and what software, hardware and networks are used. IT staff should observe the network for any discrepancies in policy implementation and correct them as soon as they find out. Network access control (NAC) can be set up to ensure that no unauthorized person can access the network.
Remote employees should be restricted from using open networks such as coffee shops, hotels, restaurants, or libraries. Such open networks can’t control who logs in and can leave your company vulnerable when bad guys gain access to your network via a remote employee’s device using an insecure connection. Instead, the company should provide VPN access for safer network requirements.
Moreover, the employees should be trained effectively to understand the need for security procedures. They should implement the standards set by the organization in their everyday life. An organization should have clearly defined rules for passwords, devices, network requirements, software, and hardware.
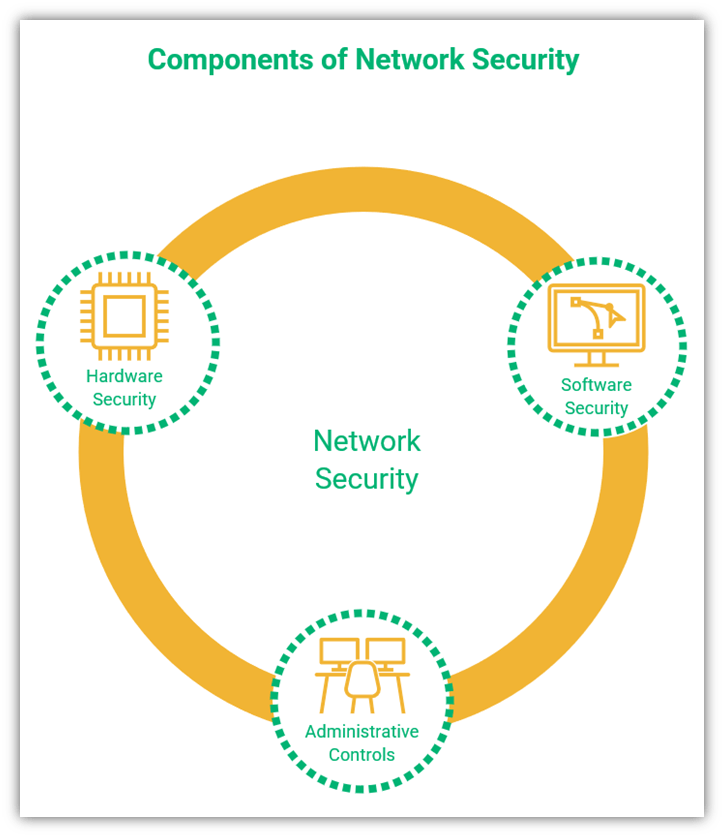
A figure showing the components of network security for remote access
Final Words on Our Top Five Considerations for Secure Remote Access
It’s clear that remote working isn’t going anywhere. To work safely from a remote location, all members of an organization need to be aware of their role in keeping your organization’s network, devices and data secure.
Achieving more secure remote access is possible if everyone involved understands and follows the best practices. These guidelines given here can help you formulate a solid plan to help you set up secure infrastructure and keep your organization and employees safe from cyber threats.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security