9 Tricks & Resources to Help You Protect Sensitive Information
According to Verizon’s 2021 Data Breach Investigations Report (DBIR), 85% of data breaches occur due to human-related security issues or negligence. Don’t let it happen to your data! Here are nine easy tricks you can immediately apply to protect sensitive information
When it comes to protecting sensitive data online, you might have felt helpless on many occasions. For example, you don’t know how a website you’re interacting with has stored and secured its databases, or what kind of technical measures they take while transferring the data from one endpoint to another. Thankfully, there are some tricks you can apply to protect your sensitive information.
In this article, we explore nine easy-to-implement tips to help you know how to protect sensitive information. Most of the resources we have mentioned are free (or freemium) and you don’t need technical expertise to use them.
Note: This article is written for general internet users. If you’re a business owner and want to know how to protect a website or web app, check out this excellent article: How to Protect a Website.
9 Practical Tips That Will Help You Protect Sensitive Information
Follow these easy-to-implement yet powerful tips to protect sensitive information while it is stored or in transit.
1. Password-Protect or Encrypt Files, Folders, and Cloud Storage
When it comes to securing your data, you can require users to enter a password to access the information or you can encrypt the data outright. While the first is more convenient in terms of ease of use as a user, the latter is the more secure option.
When you password-protect data, you require users to know a secret — a password, one-time PIN (OTP), one-time link, etc. This differs from encrypting data using cryptographic keys, which actually uses mathematical algorithms to convert data into an unreadable format. Encrypting your data prevents unintended users from reading, interpreting, and stealing it without having access to a special key (i.e., a decryption key).
Here are some ways to protect sensitive data to keep it away from prying eyes:
- Install an SSL/TLS certificate on your server. If you’re a site owner, you’ll want to secure your site using encryption. What this does it help to protect data that transmits to or from your databases and servers while it’s in transit. If you’re not a site owner, then you’ll want to make sure you’re only sharing data and uploading files via secure, encrypted connections (i.e., HTTPS connections) — more on that later.
- Password-protect your files before emailing or uploading them to a server. Always password-protect important files both in transit and at rest (i.e., while it’s transmitting and stored on your server).
- To password protect Microsoft products, go to: Files > Info > Protect Document/Workbook > Encrypt with Password.
- For phones, apps like Folder Lock help to add passwords on files, folders, and apps.
- Password-protect your cloud storage. If you are using cloud storage apps like Google Drive, Google Docs, iCloud, etc., protect them with passwords, too. If a hacker gets access to your phone via malware or lose your phone, all your cloud storage data will be in danger. Check out these guides for more instructions on how to do that.
- How to protect your iCloud account
- How to protect your Google Drive and docs
Some freemium file encryption tools include:
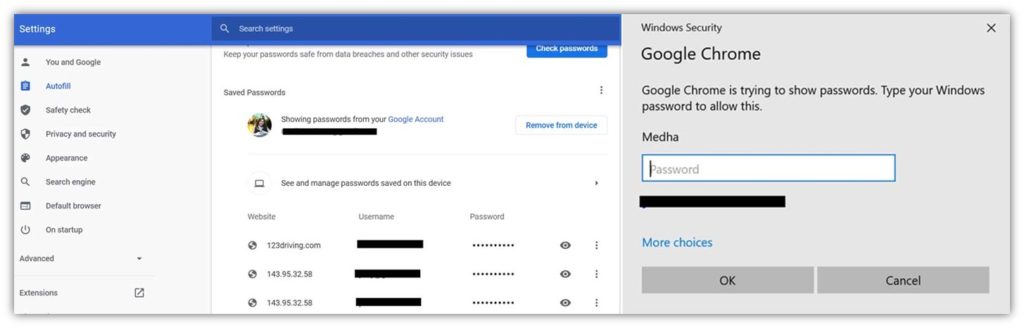
2. Don’t Let Browsers Store Your Passwords
Do you know that your web browser may be storing user IDs and passwords for a large number of your online accounts? Anyone with access to your device can view this information, meaning that they can easily log in to your various accounts, make transactions, and intercept sensitive information. This is highly risky. Here’s what you need to do.
For Chrome:
- Locate the menu (three vertical dots) on the upper right side
- Go to Settings
- Find Autofill and select Passwords
Here, you’ll see a list of passwords for various accounts, which you can delete or export and then delete.
3. Install Security Extensions
Some websites are so malicious that your device becomes vulnerable to malware infections like spyware, viruses, and trojans just by visiting them. This malware can record all your actions and corrupt your data. To protect sensitive information (and your device and accounts’ security in general), you must avoid these sites. Unfortunately, some websites are designed so cleverly that you won’t even recognize that they are malware-laden or phishing sites. Luckily, some free browser extensions block such sites or at least warn you if you’re on a suspicious site.
Check out these free Google Chrome extensions and Firefox add-ons:
- Online Security Pro by Comodo: Blocks phishing and malicious websites
- Smart HTTPS: Automatically changes HTTP pages to HTTPS (we have covered HTTPS in detail in the next point)
- VT4Browsers: Analyzes files, and URLs and identify viruses, worms, trojans, and other kinds of malicious content
- UBlock Origin: Blocks malicious ads with malware, scams, and cryptocurrency miners
- Bitdefender TrafficLight: Blocks only potentially harmful elements, letting you view the rest of the site
Note: We are not affiliated with any of the above extension providers. These suggestions are based on their popularity.
4. Never Share Sensitive Data on HTTP Sites
Open any website and check if you see a padlock symbol in front of the URL in the address bar. This symbol indicates that the website is using HTTPS (hypertext transfer protocol secure), which is a secure protocol. If you see a circle or triangle with an exclamation mark or a sign showing “Not secure,” the website is transferring data using HTTP (without “S”) protocol. What does that mean?
HTTP (hypertext transfer protocol) is an insecure protocol that transfers data between your browser and the website’s server you’re connecting to in plaintext. As the data remains in a readable format, a hacker can easily intercept your sensitive data. However, if you use an HTTPS connection, it means the communication channel is protected with robust secure socket layer /transport layer protocol (SSL/TLS) technology. This keeps your data secure while it’s in transit (i.e., transmitting between your browser and the server).
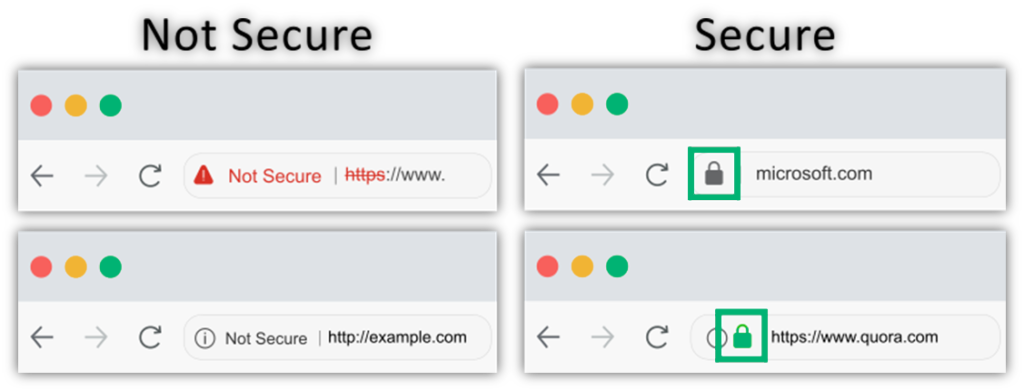
Put simply, avoid sharing any data on a site without a padlock sign.
5. Protect the Data On Your Hard Drive Prior to Selling Your Device
Did you know that even after you delete data, your hard drive still carries it? If you sell your device (phone, laptop, PC, etc.) or it gets stolen, the next user can retrieve everything from the hard drive. In the same way, if a hacker inserts malware into your device, they can also access all your data, including hard drive data.
To protect your hard drive, first encrypt the drive while you’re using the device and then wipe the entire device before you sell it. Here’s how you can complete both steps.
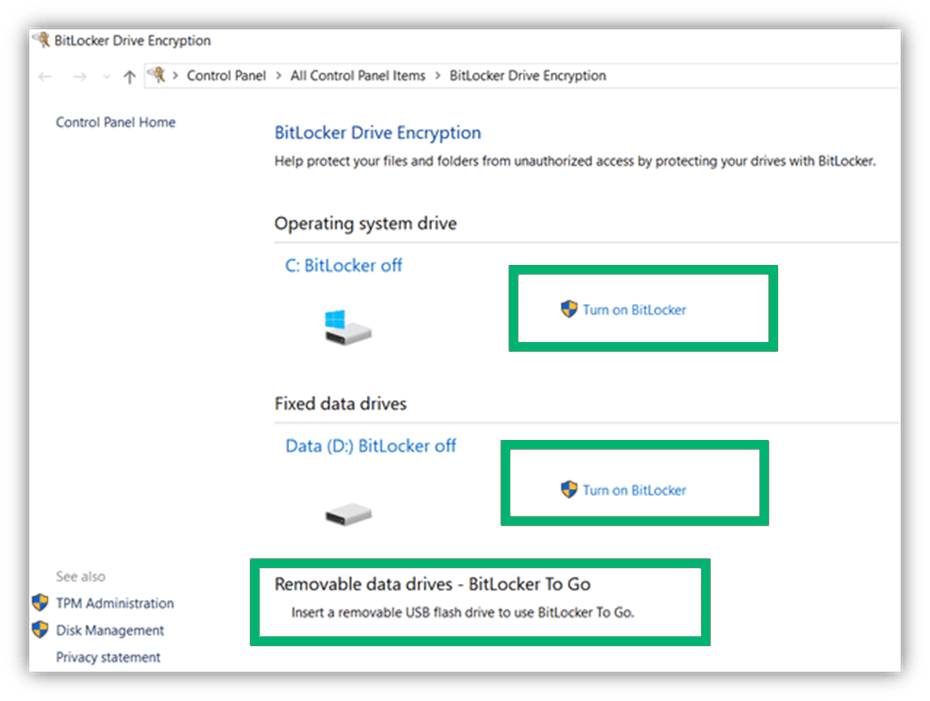
Here’s a quick breakdown of how to encrypt your hard drive in Windows using BitLocker:
- Go to Control Panel and select All Control Panel Items
- Click on BitLocker Drive Encryption
- Select Manage BitLocker
- Click on Turn on BitLocker for all drives (C: drive, D: drive, and USB)
- The system will ask administrator’s credentials to complete this task
The big takeaway here is that you never want to sell your device before wiping its entire memory. Here’s a list of tools you can use for Apple and Windows computer users:
- For Mac Users: FileVault is free software for encrypting hard drives for Mac computers.
- For Windows PC users:
6. Never Store Backups in the Same Location as Your Original Data
You probably already know the importance of creating regular data backups. So, if your personal data gets stolen, deleted, hacked, corrupted, or locked by the hacker, you can retrieve it from the backup. However, people often make the mistake of storing the backup data on the same device as the original data. That means if a hacker gets access to your device virtually or inserts malware in it, all your data, including the backup, can be compromised.
In order to protect personal data, store your backups on a separate USB drive (costs approximately $10 for 128 GBs), a portable hard drive (costs approx. $60 for 2TB), or on a cloud platform. With a cloud platform, you can retrieve the data anytime you want, and you don’t need to worry about losing the physical device. Plus, if there’ a virus in your device, it won’t automatically affect the cloud data.
We aren’t recommending any of the services mentioned below — we’re just sharing some popular examples of cloud storage providers. Be sure to do your due diligence and research storage providers on your own to find the best option that will suit your needs.
Here are some famous freemium cloud storage options:
- Google Drive: 15 GB free
- Dropbox: 2 GB free
- Blomp: 20 GB free
- Degoo: 100 GB free
- pCloud: 10 GB free
Note: You can upgrade to their premium plans if you need more storage space.
7. Enable Two-Factor Authentication (2FA) on Your Phone
When you enable 2FA, you’ll get a unique OTP, code, or a link on your registered mobile number or email address whenever you try to log in to your account. While it is the website/app owner’s decision to enable a 2FA on their platforms, some third-party apps facilitate 2FA for many other apps on your phone. This gives you an additional layer of protection over your passwords.
A few examples of free apps you can use to enable 2FA on your mobile include:
Note: Some of the above-mentioned apps work on Android devices only.
8. Never Use Public Wi-Fi Without VPNs
It’s tempting to use public Wi-Fi when your phone’s internet data is limited, slow, not available, or when tethering is not possible. Using a public wireless network is a convenient option since it’s one of the common amenities offered by cafes, restaurants, libraries, airports, and hotels. But using public Wi-Fi can be dangerous, no matter how “normal” it seems these days. If public Wi-Fi is not secured properly, hackers can break into the internet connection and execute the following attacks:
- Man-in-the-middle attacks (MitM): The hacker breaks the communication channel and positions themselves between a user and a website/application to eavesdrop on the communication and steal their data.
- Session hijacking: Attackers use weak internet security to steal an active session token and gain unauthorized access to the web server.
- Wi-Fi phishing: Another problem with public Wi-Fi is phishing. Attackers make fake Wi-Fi ports with a similar name to a nearby well-known public Wi-Fi connection to lure the victims. As soon as the user connects to the fake Wi-Fi, the hacker can easily monitor all the actions and intercept the sensitive data.
That’s why it’s best to avoid using public Wi-Fi whenever possible. But if you must, at least use a virtual private network (VPN) while using public Wi-Fi. A VPN changes your IP address and provides you with a private encrypted tunnel for web traffic transfer to prevent eavesdropping. You just need to install the VPN app on your phone or computer and turn it on. VPNs are easy to use and there are many free and free and paid options available.
9. Deny Unnecessary App Permissions
When you install a new app, you are requested to allow the app to access some of your mobile’s features and data. Review each of these requests carefully and deny the unnecessary permissions. Ask yourself a question “does this app really require accessing the requested feature?” For example, a cab service provider needs the location tracking feature, but a gaming app or eCommerce app doesn’t require location tracking.
In an iPhone, you can check which app has access to which phone feature. Go to Settings > Privacy. Review carefully each feature and which app has access to it. Turn off the unnecessary permissions.
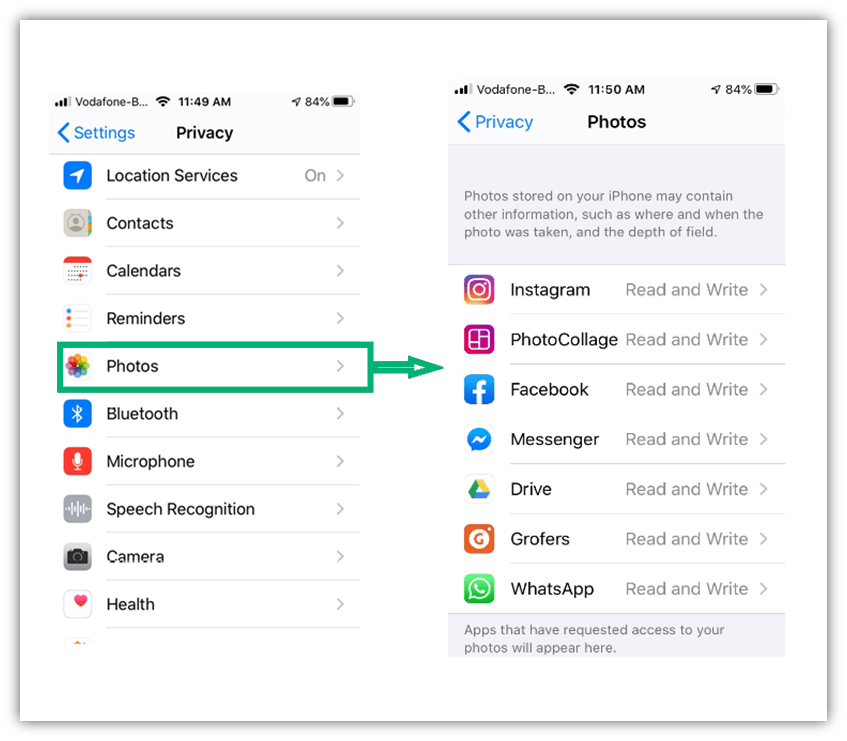
For Android, there is no unified way to check this as all the brands use different paths. For Samsung, you can check app permissions in this way: Go to Settings > Permission Manager.
Why is this step necessary? Because there are nearly five million apps in the Google Play Store alone in 2021, according to appventurez.com. You don’t know whether the person behind the app is trustworthy or a hacker. And here, bad actors don’t have to put in much effort to steal anything because you’re giving them permission to access your personal data via your phonebook, photo gallery, calendar, email clients, and location.
Wrapping Up How to Protect Sensitive Information and Data
We all want to prevent unauthorized people from accessing our private or professional information. That includes friends, relatives, colleagues, and of course, cybercriminals. Some types of data leaks can invade your personal life while others can put your professional life in jeopardy. Hence, protecting sensitive data must not be neglected or procrastinated. We hope this article has provided you with useful resources and insights on how to protect sensitive information.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security