5 Common Types of Phishing Attacks — How to Recognize & Avoid Them
Whether they’re financially or politically motivated, different types of phishing attacks remain the number one point of compromise in 91% of cyberattacks.
It’s probably weird to still be talking about types of phishing in 2020, but, hey, phishing attacks remain the top malware infection vector. Yep, you read that right! Phishing attacks retain their top position, according to APWG’s Phishing Activity Trends Report for Q3 2019. And, unfortunately, there are so many types of phishing to choose from.
Some people (and companies), never learn, so not only is phishing the most successful attack method to date, it takes hackers zero effort to get it done. Sure, there are different types of phishing, some more sophisticated than others and with different motivations, but they all rely on psychological manipulation.
Phishing has been the preferred method of countless criminals because it’s incredibly easy to deploy, yet very effective in gaining unauthorized access to critical information. While some may feel confident that their firewall will keep them safe, phishing actually gets past traditional security solutions because social engineering enables cybercriminals to manipulate their victims into revealing sensitive information about themselves or their organizations, including their credentials.
It doesn’t take a genius to launch a phishing attack. Phishing kits can easily be bought online and used to spoof websites or collect device information (in addition to the typical personal information). The most common kits will spoof email providers or file storage services. Some scammers will just use social media to pose as customer support to steal financial information.
How Do Different Types of Phishing Work?
The answer to this question depends on the type of phishing you’re talking about specifically. It’s good to keep an eye on what’s in your inbox because scammers are continually improving their skills and tactics. Phishing has evolved from the traditional campaigns most are probably familiar with, and, unfortunately, they’re getting harder to detect even for the most tech-savvy individuals. Just recently, fraudsters sent out a smishing scam impersonating Verizon Wireless asking users to verify account security.
A phishing attack will always try to manipulate you into taking an action or revealing critical information. The goal for cybercriminals is to trigger an emotional or inquisitive reaction out of their victims. For example, they’ll use urgent or emotionally charged language to get you to engage with their email in some way.
Some examples of conventional phishing emails include:
- Messages from your bank or credit card company;
- Emails about student loans;
- A potential employer reaching out for an updated resume that includes your Social Security Number;
- The IRS enquiring about tax returns; or
- A shipping company, if you work in a department that does a lot of operational work.
What Are Some of the Main Types of Phishing Attacks?
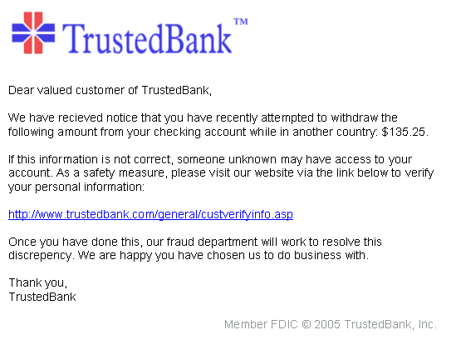
Phishing is a social engineering scheme that uses different types of email attacks, malicious websites or apps, text messages and even phone calls to psychologically manipulate a user into revealing personal information or critical data about the organization. Unless the accounting department is hit — then a ridiculously high money transfer will likely make its way into a bank account on some paradise island!
Some of the most popular types of phishing attacks are spear phishing, vishing, smishing, whaling, HTTPS phishing and business email compromise (BEC). Many types of phishing attacks are launched to spread ransomware, which is malicious software that encrypts your data and will hold it hostage until you pay a ransom in cryptocurrency.
Let’s explore five of the most common types of phishing attacks:
HTTPS Phishing Attacks
With HTTPS (Hypertext Transfer Protocol Secure) phishing, hackers have figured out a way to trick users into believing that a website is legitimate. They will rely on users’ misconceptions that the page is encrypted and secure simply because it displays HTTPS and the green padlock symbol. But today, even phishing websites can use the HTTPS protocol (i.e. incorporate website certificates) in the browser address bar to win user trust. The user will then easily fill out a form, for example, and give away their credentials or other sensitive information.
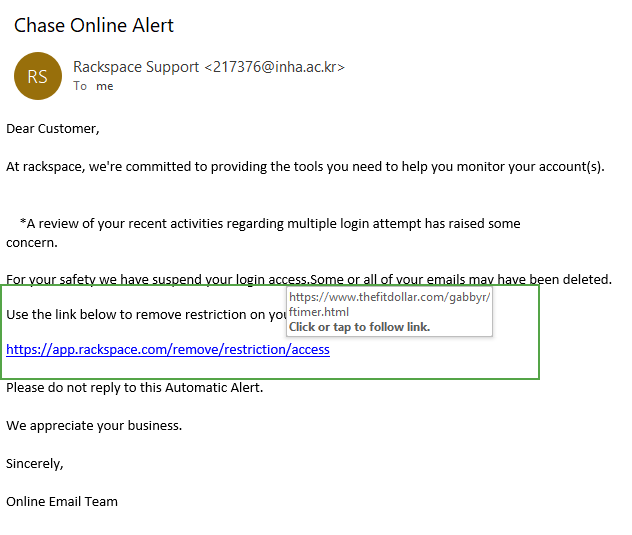
Last year, the FBI warned users that just because a website starts with HTTPS, it doesn’t mean it guarantees privacy and security. The FBI recommends being suspicious of unknown senders, especially if their email address ends in .com when it should be .gov, and looking out for misspelled words. Cybersecurity company Trend Micro reported last year that the types of phishing using digital certificates to encrypt connections spiked to 58% in Q1 of 2019, and they are on the rise. A Q3 2019 report from the Anti-Phishing Working Group (APWG) estimates that the number is actually higher — 68%!
Business Email Compromise Attacks
Business Email Compromise, also known as email account compromise (EAC) is a type of phishing attack in which a cybercriminal impersonates corporate executive management to trick employees (typically in either Human Resources or accounting) into authorizing a wire transfer payment, or sharing personally identifiable information (PII) or tax information.
The FBI has reported that BEC scams represented half of the 467,361 cybercrime losses reported in 2019, accounting for $1.77 billion. Other FBI statistics report a high number of complaints regarding spoofed emails, which impersonate an employee asking for direct deposit account changes, with a lot of the funds primarily heading to banks in China and Hong Kong, as well as the United Kingdom, Mexico and Turkey.
In order to appear legitimate and steal employee credentials, these types of phishing attacks that involve a payroll diversion scheme may include a spoofed login page for an email host. According to victim complaints received by the FBI between June 2016 and July 2019, the domestic and international exposed dollar loss exceeded $26 billion. In 2019, Facebook and Google were defrauded of over $100 million in a sophisticated scheme.
Spear Phishing Attacks
Spear phishing attacks are not your average scam. These are targeted types of phishing, tailored and researched to appear genuine. Technology and social media have been of great help in victim research to devise personalized and compelling email attacks.
As many as 91% of cyberattacks start with a spear phishing email, and they are often successful in manipulating key employees in an organization’s HR, finance, legal or IT departments to share their credentials or click on a link that will download malware into the system. The email could appear as a LinkedIn notification, an urgent request from a team member or a manager, or even an urgent email from an institution. Top companies such as JP Morgan, Home Depot, and Target have been breached following spear phishing attacks.
Whaling Attacks
Whaling attacks are similar to spear phishing attacks, only they are more specific and target c-level executives or high-ranking individuals with authority who have access to critical information or even wealth. Because whaling emails involve extensive research to deceive the victim into believing the message is legitimate, criminals engaging in these types of phishing attacks can be very patient in achieving their financial gain. Whaling emails are specific and include very personal details to convince the victim to engage with the call to action.
Voice Phishing
Vishing is just a fancy term for voice phishing or phone fraud. Whenever you get a pre-recorded message from the IRS or from your bank asking you to call a number and give away your credit card information or Social Security Number, you’re looking at a well-crafted phishing attempt. Recently scammers have started combining voice with text messages (smishing) to make the scam appear more legitimate.
Security expert Brian Krebs warned on his blog that voice phishing scams are getting smarter. Based on his friend’s experience, he says fake phone calls from credit unions or the tax department have become so sophisticated that the details mentioned by the criminal frequently make sense. The calls appeared made from trustworthy numbers, yet we know by now how easy it is for criminals to spoof the caller ID number.
The list goes on, as there are many other types of phishing attacks such as clone phishing, domain spoofing, evil twin, and watering hole phishing.
Types of Phishing Motivations
Some 30% of all phishing emails are opened by targeted users. Most data breaches have started either from the use of a weak password or from a phishing attack that exploited an employee’s behavior. If we take a closer look at statistics, some type of phishing email was behind 78% of cyber espionage episodes and more than 95% of attacks in general start with a phishing email.
A phishing attack will go after information such as:
- usernames and passwords,
- emails and contacts’ information,
- personal information that can be used to create fake accounts and for identity theft,
- proprietary corporate information or tech details,
- sensitive information to use for tax fraud, and
- medical records or health insurance details.
While some types of phishing attacks are financially motivated, it’s not always the case. Some phishing is done with the goal of performing cyber espionage, while others are politically motivated.
Financially Motivated Phishing Attacks
According to Verizon’s 2019 Data Breach Investigation Report (DBIR), 71% of attacks, including phishing attacks, were financially-motivated. Financial gain remains a top motivation — especially in attacks targeting c-level executives who are more likely to click on urgent emails and have authority to make money transfers, says the report.
Cyber Espionage-Motivated Phishing Attacks
Intellectual property and sensitive data are among the top targets for different types of phishing attacks. Nation-state backed cybercriminal gangs are supported by Russia, China, Iran and North Korea. They target Western companies and governments with spear phishing emails to execute malicious payloads and steal critical, proprietary information, according to ZDNet.
Just recently, Iran-sponsored hackers targeted government organizations in Turkey, Jordan and Iraq with spear phishing attacks to steal intellectual property.
Politically Motivated Phishing Attacks
Emails impersonating government authorities have claimed many victims. However, likely the most notorious politically motivated spear phishing attack was launched by Russian-backed hackers against the U.S. Democratic party during the 2016 election to steal information about the Clinton campaign.
Regardless of which type of phishing attacks cybercriminals use, it’s imperative that you and your employees know how to recognize them for what they are.
How to Identify Most Types of Phishing Attacks
The most common types of phishing attacks rely on an email that’s configured to steal sensitive information by manipulating the victim into clicking on an infected link or downloading disguised malware. If the malware gets into the system, it will scan the device for vulnerabilities and it will compromise the system, network and potentially any devices linked to it.
When it comes to recognizing phishing, it often boils down to knowing what to look for. Some immediate red flags that you might be looking at a phishing scam include:
- The sender’s email address. Double check the sender’s email address, as well as the domain and the URL the links in the email are pointing to.
- Unexpected requests for personal or sensitive information. All of a sudden, a well-known, trustworthy company or institution contacts you, asking you to provide personal or sensitive information.
- Language that elicits an emotional reaction or sense of urgency. The message provokes some sort of emotion, ranging from fear and excitement to a sense of urgency. It may try to get you to pay a bill or take another immediate action.
- Urgent request from upper management. Your manager or CEO has sent an email suddenly asks you to immediately pay an invoice or open a document of critical importance.
- Poor language and too many information errors. Something seems off.The sender makes grammar and spelling mistakes; the logo looks off; there are typos in the email address or in the person’s name; or, worse, you have no idea who is this person sending you an invoice for immediate pay.
- Website asking for private information. A website asking for critical personal information such as passwords, credit card numbers, social security number and bank account numbers should be considered suspicious, even though it looks legitimate.
How Can You Avoid Phishing?
Phishing messages were so much easier to spot a couple of years ago. The rare times anyone ever paid attention, they would have probably noticed a typo in the email or in the sender’s name, some grammar mistakes here and there or a big fake logo at the top — but scammers are improving their craft. Manipulative emails and spoofed websites are getting harder and harder to tell apart from their genuine counterparts.
Here are some top pointers to stay away from the different types of phishing attacks:
- Security awareness training for employees. Awareness workshops can help employees better understand the risks and educate them on inbox threat detection and email best practices.
- Double check urgent emails. When you receive a money transfer request from the CEO but something about it makes it seem suspicious, double check that it is legitimate by personally reaching out to the person in question.
- Email signing certificates (S/MIME certificates). Digital signatures confirm the sender’s authenticity and message integrity; email encryption protects messages in transit and when sitting on email servers.
- Email authentication methods. DMARC (Domain-based Message Authentication, Reporting & Conformance) and DKIM (DomainKeys Identified Mail) are email authentication protocols that fend off different types of targeted email attacks. Without these protocols, criminals can spoof a domain and send malicious emails.
- Activate two-factor authentication (2FA) and multi-factor authentication (MFA) measures. Not only does using one of these methods protect your device from password compromise, but it can also be used to secure wire transfers.
- Develop, implement, and enforce computer use and BYOD security policies. Now that BYOD (bring your own device) has become a way of life, it’s good to get some more transparency into which devices are connecting to the work network.
- Ensure patching and updates are all up to date. A large organization will have a high number of devices that run different software versions. Regularly run software updates and patches for operating systems to prevent vulnerability exploits in case of a successful phishing attack.
The different types of phishing attacks will likely maintain its top-ranking position because this form of attack is very practical and has a high success rate. Relying on targeted research and psychological manipulation, cybercriminals are going to continue to trick users into revealing personal information that they can manipulate for their own purposes. Depending on the different types of phishing, some emails can be hard to figure out, which is why security workshops alongside effective security measures could help reduce the risk of phishing scams being successful.
Don’t allow yourself or your employees to get hooked. Teach them how to recognize the types of phishing threats that we face today to help prepare them for new types of attacks that may come out tomorrow or in the near future.
























 (14 votes, average: 4.71 out of 5)
(14 votes, average: 4.71 out of 5)






No comments