What Is Security Awareness Training?
Let’s dive into the topic of security awareness training — what it is, and five topics you have to cover in your organization’s cyber awareness training
If you like keeping your data secure, then security awareness training is a must.
You secure your network and devices with firewalls, vulnerability scanning, email spam filters, and other cybersecurity tools and tactics. Luckily, there is no shortage of cybersecurity tools that can help protect your data. However, there is one critical link in the chain that even the most sophisticated cybersecurity tools can’t completely cover — and that is human error. Yes, it’s a tricky link in the chain and quite the dangerous one if it’s a weak link as well.
Phishing may be the most common type of cyber attack that exploits human error. And, unfortunately, many employees fall prey to this type of attack. For example, KnowBe4’s Phishing by Industry Benchmarking Report shows that almost 38% of untrained users are vulnerable to phishing attacks and fail phishing tests. Scary. Those near 38% of people’s mistakes can result in any number of terrible things, including:
- Your employees’ financial data being stolen,
- Your customers’ personal info being used or sold, and
- Many similar awful scenarios.
So, how do you mitigate the issue of a group of untrained people that are prone to phishing attacks? You train them! This type of training is called security awareness training. It goes beyond phishing, but the core purpose doesn’t change. Here’s what to know about security awareness training!
What Is Security Awareness Training?
Security awareness training is the process of formally or officially providing training to your employees on cybersecurity-related topics. Even though it’s sometimes called cyber awareness training, security awareness training can go beyond cybersecurity. It can also touch on all general security topics that relate to being an employee within your organization.
Security awareness training is versatile and can be conducted in a variety of formats and timeframes. For example:
- It could be held as an online course (either in-person or fully online).
- You can internally put it together and conduct the training or hire a third-party vendor.
- This could be as part of the new employee onboarding process, or as annual or quarterly training (or some combination of the three).
There are two general goals of security awareness training. One is to ensure that your employees are informed on what cybersecurity threats are, how to spot them, and how to avoid them. The other is to equip your employees with the right tools, procedures, and knowledge of how to handle cybersecurity scenarios as they arise at the workplace.
There are many topics that you should cover during security awareness training. Here are five topics you have to cover.
Top 5 Security Awareness Training Topics That Your Business Must Cover
When you are putting together a security awareness training or vetting vendors to hire, make sure the training includes these five topics…
Security Awareness Training Topic 1: Operating Safely on Social Media
Any network or platform that interacts with external users can be a security threat to your organization, and social media is no different. Many initially point to email as the prime source of successful phishing attacks, but that is not always the case. This may be in part because people are using different devices to access their organizations’ networks.
In Wandera’s 2020 Mobile Threat Landscape Report, their findings showed that 87% of successful mobile device phishing attacks came from sources other than email. And one of those other sources named in the report was social media.
While social media isn’t always permitted at work, it is a big part of most people’s personal lives. Furthermore, many positions require employees to interact with social media. That could include your personal accounts or the company’s social profiles. I’ll use a personal example of how a phishing attack on social media could look via a Facebook message I received a few years ago.
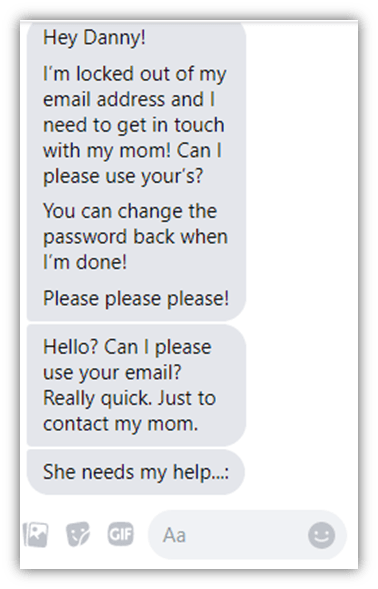
One thing to note about this message is that it came from a trusted friend whose account had been hacked and the attacker was looking to use their social media account to get into my email. This is very dangerous because it’s one thing to get phished by a stranger, but it takes a whole other level of awareness to spot it in someone you trust (an area that should be covered in your security awareness training).
Luckily, I did spot it. I was able to because I used critical thinking, which is one of the areas that you should cover in security awareness training. I asked myself several key questions:
- Why would a friend of mine need my email to contact their mom? It just doesn’t make sense.
- Who regularly talks on email in that way?
- Why can’t the friend call me instead of texting?
- Why me and not a family member?
It’s important for your employees to question things, use logic, and think critically through this type of situation rather than simply reacting to it.
In the phishing attack example above, the hacker tried to elicit an emotional response of sympathy while also using urgency to get me to respond. The begging and “really quick” is meant to frazzle the target, while the reason for them needing access to contact their mom is meant to make the victim feel like they are doing their “friend” a favor. Those are two more topics that you should cover in security awareness training. If I gave this hacker my email, they could have used it to get into my bank account, attack other social media profiles, and even attempt to infiltrate my employer.
The lesson here regarding social media is that it’s commonplace in our personal lives and, many times, the workplace as well. Therefore, it needs to be covered thoroughly in your security awareness training.
Security Awareness Training Topic 2: Internet Browsing with Knowledge
Hey, you… Shouldn’t you be working and not enjoying this wonderful blog on security awareness training? Okay, maybe that was a reach, but let’s be real — most people’s minds wander while at work, which can lead to some casual (and oh-so-satisfying) internet browsing at work. Heck, some companies even put it in their policy to allow a certain percentage of time that could be used for casual browsing.
Web surfing is harmless… until your internet browsing causes cybersecurity issues for your employer. Then it’s not so “harmless” anymore. This is why it’s important to teach your employees how to safely browse the internet whether it is casual or research for work purposes. (Yeah, I’m sure you really needed to watch that 20-minute YouTube video… you weren’t milking it at all.)
In all seriousness, though, you can cause quite a bit of trouble when browsing the internet on a work device. This could include:
- Stumbling onto phishing or other malicious sites,
- Clicking on dangerous links, and
- Interacting with unsecure websites.
The last one is especially important to note. Your employees must know what SSL/TLS certificates are and how to spot unsecure websites. (These are the certificates that make the padlock icon appear in your web address bar, telling you that you’re using a secure, encrypted connection.) The reason is that hackers can use insecure connections to intercept your employees’ interactions or communications and use that information against them — or your business — in a cyber attack.
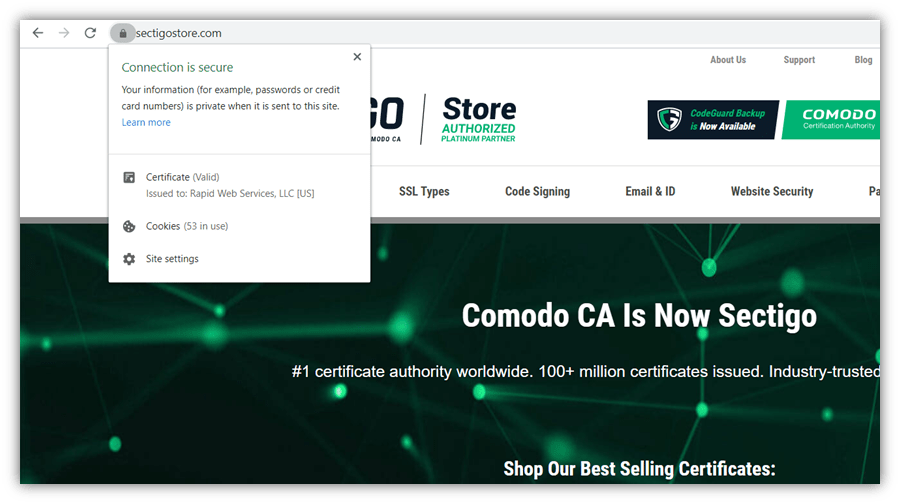
Take a look at the screenshot above. The padlock icon in the web address bar indicates that a website is secured by HTTPS. Furthermore, you can click on the icon to see if the website admin has been validated by a trusted CA and their organization details are shown in the certificate.
Security Awareness Training Topic 3: Spotting Dangerous Emails
We covered social engineering on social media, but email is still a vital topic to cover in your security awareness training. While you may think email spam filters designed to catch malware will solve the problem, it won’t. It’ll help mitigate it but not as much as you might think. April-June 2019 data from FireEye shows that 86% of cyber attacks (via email) had no malware in them. This means that your spam filters will not catch these emails and you will need to rely on your employees to spot an attack.
I will share another personal story in relation to a social engineering attack. I received the email below on my personal email account six months ago. Besides the most obvious error, such as the fact that I’m not married, this email sends up many red flags for other reasons you should cover in your security awareness training.
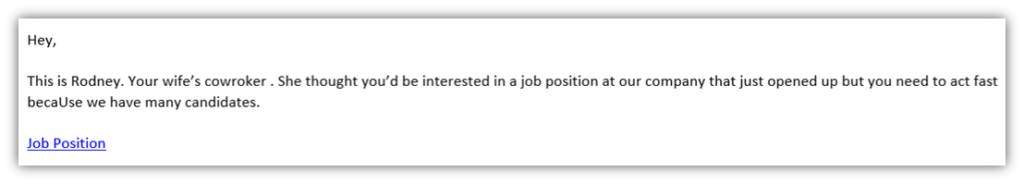
Emails that have these characteristics can be dangerous:
- The email is from an unknown sender.
- It looks like a legitimate company email address but it’s slightly different.
- A warning message from your email service provider is associated with the email.
- The sender attempts to get you to share something or click on something unsolicited.
- The sender uses language that creates a sense of urgency, fear, or curiosity.
- The email contains awkward wording, poor grammar, and/or impersonal verbiage.
Security Awareness Training Topic 4: Making Secure Passwords
The ultimate headache — passwords. Can’t remember them, always have to change them… Not another “forgot my password” roundabout. Well, passwords are there for a reason. They try to help keep bad people out of your accounts. So, it’s important to make them strong. All employees should be brought to speed on good password habits.
Here are a few tips on picking a good password that should be included in your security awareness training:
- Avoid predictable passwords.
- Never share or reuse passwords.
- Don’t use short passwords (try to make them more than 10-15 characters in length).
- Think in terms of creating nonsensical but easy-to-remember passphrases instead of passwords (think “H1pposArent4BirdsRU” instead of “SXN8t875yu2fcPe”).
- Use lowercase letters, capital letters, special characters, AND numbers (yes, all four).
Security Awareness Training Topic 5: Communication is Key
No, this paragraph is not about relationship advice (although communication is key with that, too). This is still about security awareness training. However, you could consider this somewhat of a suggestion on relationship advice as it is about the relationship between employees.
The topic of communication in security awareness training should cover two general areas:
- Making employees feel comfortable to ask for help.
- Ensuring employees know where to turn for help.
After investing time and resources into providing security awareness training, employees should feel like it’s their responsibility or duty to know which websites/emails/messages could be malicious and which ones aren’t. However, this sense of obligation may make some employees feel like they shouldn’t reach out if something happens — that maybe it makes them look like they weren’t paying attention or have a poor eye for this stuff. Not good!
You want your employees to feel comfortable with seeking assistance in these situations. This will be conducive to a good work culture. Also, this gives you the highest chance of catching a cyber threat and limiting the damage it causes. So, make sure you make it clear in security awareness training that employees are encouraged to reach out for assistance if they come across something fishy (or should I say “phishy”).
Now that they are comfortable with seeking assistance in these situations, it is time to ensure they know who to reach out to when facing a potential cyber threat. I suggest having:
- A designated “go-to” person in your IT department who is there to help identify dangerous emails, websites, links, etc.
- Contact info for this go-to person readily available to all employees.
- A backup go-to person if the first one is unavailable.
If there’s a legitimate issue, this go-to person can take over the situation (i.e., if they need to make all employees aware of the threat and so on).
Cyber Awareness Training – Conclusion
Security awareness training is surely an important addition to any organization. Whether you do it yourself or hire someone to do it, make sure your training is thorough and covers the topics above as a minimum. You can also use external resources from authoritative resources as part of your training as well, such as the DoD’s Cyber Awareness Challenge online training course.
Your employees are ultimately your first and last line of defense, so you want to make sure they are well prepared. Always remember that your organization’s defenses are only as strong as its weakest link. Arm your employees with the knowledge and tools they need to keep your organization safe and your data secure.














 (16 votes, average: 4.19 out of 5)
(16 votes, average: 4.19 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security