DoD Cyber Awareness Challenge 2020 — Your Ultimate Guide
Here are some of the key takeaways for companies and individuals from the DoD Cyber Awareness Challenge 2020
The Cyber Awareness Challenge, which is also known as the Army Cyber Awareness Training, the cyber awareness challenge or the DOD cyber challenge, is an annual computer security training that was created to increase cyber awareness among Department of Defense (DoD) employees.
It’s available online, it’s free of cost for everyone, and it’s also accessible from any part of the world so long as you have a reliable internet connection!
Everyone with a computer or that handles any type of sensitive information would benefit from it. In this guide, we’ll explore the key lessons of the DoD cyber challenge and the summary of the entire training materials.
DoD Cyber Awareness Challenge: Who Can Take It?
- Army, other armed force branches, government employees.
- Companies and organizations can use this cyber awareness challenge as an excellent resource to provide cybersecurity training to their employees.
- All individuals — especially those who value privacy and security, who work with sensitive information, or those who work in the IT field — should take this training to protect themselves and their clients from potential cyber-attacks.
You can complete this cyber awareness challenge training on the official DoD Cyber Awareness Challenge 2020 website.
Even though its lessons are focusing on securing the nation’s classified data, the cyber awareness challenge contains lots of cybersecurity takeaway for non-military users like you and me.
The Format and Main Content of the DoD Cyber Awareness Challenge
There are three main sections and their subsections in the DoD Cyber Awareness Challenge tutorials:
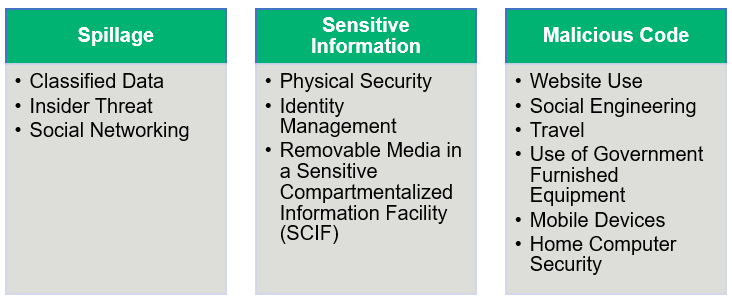
Each section has definitions, vulnerabilities, real-life scenarios, and talks about the types of decisions you should make or avoid to prevent a cyber attack.
1) Data Spillage
In the government, “spillage” is a term that refers to information that’s leaked from a higher classification or protection level to a lower one. A spillage poses a serious risk to national security. Spillage occurs when someone accidentally or intentionally makes an unauthorized data disclosure, data modification, or engages in espionage, which results in loss or degradation of resources or capabilities.
2) Sensitive Information
For any type of business or organization that handles sensitive information, it’s crucial that you do everything you can to protect this information — both for the sake of your customers as well as to remain compliant with laws and regulatory data protection requirements. Some of these regulations include:
- The Health Insurance Portability and Accountability Act (HIPAA),
- The European Union’s General Data Protection Regulation (GDPR),
- The California Consumer Privacy Act (CCPA), and
- The Payment Card Industry Data Security Standards (PCI DSS), etc.
But what is considered “sensitive information?” Sensitive information includes:
- Controlled technical information (CTI),
- Personally identifiable information (PII),
- Protected health information (PHI),
- Financial information,
- Personal or payroll information,
- For official use only (FOUO),
- Controlled unclassified information (CUI), and
- Proprietary data.
These types of sensitive information must be protected because their leakage can compromise government missions or interests. An example of such sensitive information includes data or information that’s provided by a confidential source (person, commercial business, or foreign government) with the condition it would not be released.
For businesses and healthcare organizations, examples of these types of information include:
- Employee or customers’ names, addresses, phone numbers, etc.,
- Financial records and account information,
- User credentials and passwords,
- Patient medical records and health-related information, and
- Medicare or insurance information.
3) Malicious Code
Malicious code can be spread by downloading corrupted email attachments and files or visiting infected websites. Malicious code includes viruses, trojan horses, worms, macros, and scripts. They can damage or compromise digital files, erase your hard drive and/or allow hackers access to your PC or mobile from a remote location.
Key Lessons for Corporations and Individuals from the DoD Cyber Awareness Challenge
Here, we have written a summary of cyber awareness challenge training, covering the key takeaway lessons.
Please note that we have included only handpicked the lessons which we deem beneficial to a general audience. It doesn’t have all the teachings of the course, though. To get access to all of that, you must complete the DoD Cyber Awareness Challenge yourself!
Protection Against Malicious Code
Malicious code is a term that describes the code that’s used in online forms, scripts, and software that aims to cause harm in some way. To help your employees avoid the risks associated with downloading and installing malicious code, here are some helpful tips:
- Scan all external files before uploading them to your computer.
- Don’t access website links, buttons, and/or graphics in a suspected email or a pop-up generated by an email message.
- If you suspect any email to be malicious or if any unknown/unauthorized sender is requesting some personal/sensitive information, contact your security point of contact (POC) or help desk for assistance.
- For your personal and office devices (laptop, PC, mobile, etc.), research any application and its vulnerabilities before downloading that it.
- View email in plain text and don’t view an email in the preview pane.
- Look for digital signatures if your organization uses an email signing certificate (highly recommended). Digitally signed emails are considered more secure.
Best Practices for Protecting Sensitive Information
When you trust your employees to handle customers’ confidential information, they must be aware of the sensitivity of the data and how to protect them. A single act of negligence can be catastrophic. Here are some major takeaways from cyber awareness challenge that you can use to train employees.
- While faxing sensitive information, ensure the recipient is at the receiving end. Contact the recipient to confirm receipt.
- The most commonly reported cause of PII breaches is a failure to encrypt email messages containing PII. So always use encryption when emailing PII, PHI, or any other sensitive information. Also, digitally signed emails whenever possible to provide authentication and to assure information integrity.
- Avoid storing sensitive information in shared folders or shared applications (e.g., SharePoint, Google Docs, etc.).
- Never use personal email accounts for transmitting PII and PHI.
- Store sensitive data only on authorized information systems. Don’t transmit, store, or process confidential information on non-authorized systems.
- Follow your organization’s policy concerning the retention or disposal of sensitive information.
- Mobile devices may be hacked or infected with malware. So, always use mobile devices approved by your organization and follow your organization’s policies on the use of mobile computing devices and encryption while dealing with PII or PHI.
Prevention Against Insider Threats
Incidents related to insider threats are up 47% since 2018, according to data from the Ponemon Institute and ObserveIT.
The term insider threat refers to a situation where employees themselves (intentionally or unintentionally) leak the data or execute the cybercrime against the organization. You can’t rule out the possibility of insider threats because employees have tons of information readily available to them on their fingertips. So, as an employer, you must keep an eye on your employees’ activities and also train the staff to recognize the potential threat that may exist among them. We’re not saying that all of your employees are insider threats. However, if someone is going through difficult life circumstances or experiencing persistent interpersonal difficulties, their emotional instability can make them a potential candidate to become one. Observe them and assess whether they’re showing any uncommon or concerning behaviors, such as:
- Showing hostile, vindictive or criminal behavior, or
- Taking an unusual, or excessive interest in sensitive information or
- Indicating unexplained or sudden affluence by purchases of high-value items/living beyond one’s means or
- Attempting to access and/or remove sensitive information without the need-to-know
Rather than giving the benefit of the doubt, report any suspicious activity or behavior in accordance with your agency’s insider threat policy.
Of course, there are additional steps you can take to prevent or limit the impact of insider threats:
- Perform organization-wide risk assessments.
- Create and enforce a data use policy.
- Implement the principle of least privilege to limit employee access to only necessary systems.
- Periodically review access lists and remove access immediately for employees who quit or are fired.
- Use a security information and event system (SIEM) to monitor employees’ actions and the information they access.
Best Practices for Physical Security in the Workplace
There are many reasons why physical security is so important to organizations — your colleague could be an insider threat, or some walk-ins or visitors might be spying, eavesdropping or looking for a chance to steal the important data from the files or computer. These occurrences not only happen on military installations but also within the organizations. So, you must be vigilant about your workplace security, too. This means:
- Don’t talk about work/customers/company’s policies regarding marketing, technology, etc. outside your workspace. You might unintentionally leak some confidential information that must not go out. Even inside a closed work environment, be careful when discussing sensitive information, such as PII or PHI, as people without a need-to-know may be present around you.
- Be aware of people eavesdropping when retrieving messages from smartphones or other media.
- Know and follow your organization’s policy on gaining entry in the building, securing work area, and responding to emergencies.
- Always lock your office’s cabinets and drawers if they are having any files/papers containing sensitive information.
Best Practices for Portable Devices and Removable Media
Portable devices and removable media pose a major security threat to businesses and government organizations alike. They’re easy to use and convenient. However, portable devices also can carry malware from one device to another without the user knowing. So, if you plug an infected device into a new machine, it may install that malware on the new device.
These types of media include flash media, such as thumb drives, memory sticks, and flash drives, external hard drives, optical discs, and external music players like iPods.
So, what can you do to protect your organization?
- Only use removable media to store work-related data when operationally necessary, owned by your organization, and approved by the appropriate authority in accordance with policy.
- Encrypt data appropriately when storing it in a removable media device.
- Do not use any personally owned/non-organizational removable media to store your organization’s data.
- As a best practice, label all removable media, especially if they contain PII, or PHI, or any sensitive data.
- Avoid inserting removable media with unknown content into your computer.
- Follow your organization’s policy for sanitizing, purging, discarding, and destroying removable media
Best Practices for Laptops and Mobile Devices
Your laptop and mobile devices must have stored so many saved credentials for automatic login, personal and professional data and media files. If your organization has provided you laptop or mobile for profession use, it might be a virtual goldmine for attackers. Just by hacking or stealing such devices, the cybercriminal can execute dangerous attacks. That’s why handing your mobile and laptop carefully is a crucial step.
- Consider screen protection if you are using a laptop or mobile device for doing office work in public places.
- Power off the device if you are not going to use it in the immediate future.
- Enable automatic screen locking after a period of inactivity.
- Encrypt all sensitive data on laptops/mobile.
- Always maintain visual or physical control of your laptop/mobile devices, especially when going through airport security checkpoints.
- Use public or free Wi-Fi only with the organization’s approved VPN.
- If the device is lost or stolen, immediately report the loss to your security POC or organization’s technology department.
Tips for Home Computer Security
People generally don’t store organization related information in their home computer/personal computer. However, such personal computers do contain automatic login facilities to email addresses, social media sites, applications, financial institutions’ sites, etc. Hence, the employees must be aware of how to protect their home computers, too.
Note: In the cyber awareness challenge, these tips are derived from the National Security Agency (NSA)’s PDF “Best Practices for Keeping Your Home Network Secure.”
- Always use strong passwords for your home computer.
- Create separate accounts for each user and have them create their own passwords using a strong password creation method.
- Install all system security updates, patches, and keep your defenses such as antivirus software, spyware, and firewall up to date.
- Regularly scan files for viruses.
- Change default login ID and passwords for operating systems and applications.
- Regularly back up and securely store your files.
Beware of sudden flashing pop-ups warning that your computer is infected with a virus; this might indicate a malicious code attack.
General Security Tips for Online Behavior Outside the Workplace
While employers can’t necessarily control what their employees do in their personal time, they can educate them about the dangers of social media and other online platforms. The DoD Cyber Awareness Challenge has a section that provides guidance on the best practices while surfing online.
Here are a few key takeaways from this section of the DoD cyber awareness challenge training:
- Be aware of the information you post online about yourself and your family. It might be used to guess your passwords, executing doxxing attacks, sending spear/whale phishing emails, or for identity theft.
- Create strong passwords and opt for two-factor authentication (2FA) or multi-factor authentication (MFA), if available.
- Beware of links to games, quizzes, and other applications available through social networking services. They might contain malicious codes or manipulate you to share your login credentials or other sensitive information.
- Don’t post any confidential information about your organization, colleagues, or customers on social networking sites (no matter what privacy settings you have set on your account).
A Final Word on the DoD Cyber Awareness Challenge
Cybercriminals use innovative and sophisticated ways to execute cyber attacks nowadays. People do fall for such malicious tricks and lose billions of dollars every year. That’s why cyber awareness training is a must for everyone, especially for corporate employees and people working in the field of technology.
When corporations become a victim of a cyber attack due to the negligence of an employee or insider threats, they lose not only sensitive data but also the reputation and suffer from financial loss in legal battles. As such, the DoD Cyber Awareness Challenge is an excellent resource for organizations to train their employees, make them vigilant against various types of cyber crimes, and let them know the best protection techniques. The cyber awareness challenge is a highly recommended training for all for improving the security posture of any organization regardless of size.
























 (26 votes, average: 4.38 out of 5)
(26 votes, average: 4.38 out of 5)






No comments