5 Differences Between Symmetric vs Asymmetric Encryption
Symmetric vs asymmetric encryption — which is more secure? We’ll break down the differences between asymmetric and symmetric encryption to provide clarity
For someone who’s not a techie or is mostly new to cryptography, choosing an encryption software to secure sensitive data can be a challenging task, particularly if they need to decide between symmetric vs asymmetric encryption.
Questions around their differences, which is considered the more secure process, and which one is most suitable for your needs, are bound to arise. But before we answer any of these questions, for the uninitiated, we’d like to go back to the basics and start with defining encryption.
An Overview: What Is Encryption?
Encryption is the process of converting human-readable data (plaintext) into unintelligible ciphertext. This scrambling of data is the result of an algorithmic operation that uses a cryptographic key. Simply put, encryption takes your data and makes it random enough so that anybody who steals it can’t read it unless they have the key to turn it back into a legible form.
The use of encryption is necessary if we want privacy and for protecting our data at rest, in use, or in motion. There are two main types — symmetric encryption vs asymmetric encryption — which we will compare in this article.
Symmetric vs Asymmetric: The Two Types of Encryption and How They Work
Symmetric Encryption
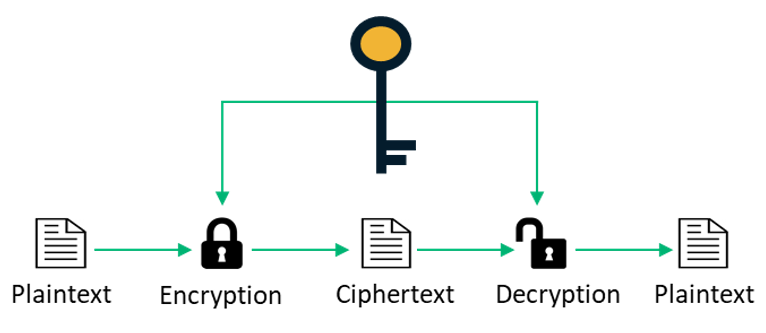
In the case of symmetric encryption, the same key is used for both encrypting and decrypting messages. Because the entire mechanism is dependent on keeping the key a shared secret — meaning that it needs to be shared with the recipient in a secure way so that only they can use it to decrypt the message — it does not scale well.
Symmetric encryption algorithms can use either block ciphers or stream ciphers. With block ciphers, a number of bits (in chunks) is encrypted as a single unit. For instance, AES uses a block size of 128 bits with options for three different key lengths — 128, 192, or 256 bits.
Symmetric encryption suffers from key exhaustion issues and, without proper maintenance of a key hierarchy or effective key rotation, it’s possible that every usage can leak information that can be potentially leveraged by an attacker to reconstruct the secret key. Although there are key management issues with symmetric encryption, its faster and functions without a lot of overheads on network or CPU resources. Therefore, it’s often used in combination with asymmetric encryption, which we’ll look into in the following section.
Key Takeaways of Symmetric Encryption
- There’s a single shared key that’s used for encryption and decryption.
- It doesn’t scale very well because the secret key must not be lost or shared with unauthorized parties, or else they can read the message.
Asymmetric Encryption
Asymmetric encryption uses a pair of related keys — a public and a private key. The public key, which is accessible to everyone, is what’s used to encrypt a plaintext message before sending it. To decrypt and read this message, you need to hold the private key. The public and the private keys are mathematically related, but the private key cannot be derived from it.
In asymmetric encryption (also known as public-key cryptography or public key encryption), the private key is only shared with the key’s initiator since its security needs to be maintained.
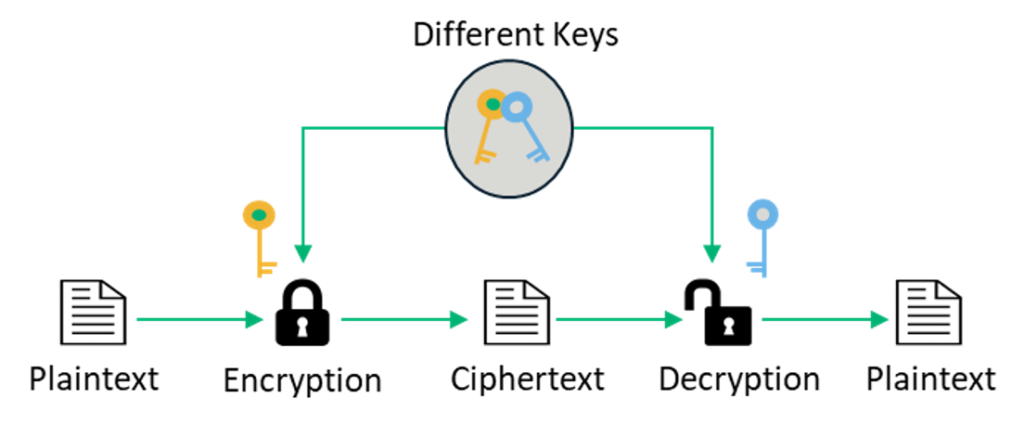
Because asymmetric encryption is a more complicated process than its symmetric counterpart, the time required is greater. However, this type of encryption offers a higher level of security as compared to symmetric encryption since the private key is not meant to be shared and is kept a secret. It is also a considerably more scalable technique.
Key Takeaways of Asymmetric Encryption
- It involves the use of two mathematically related keys. The public key (the one that’s known to everybody) and the private key (which is only known by you) are required for encrypting and decrypting the message. The private key cannot be derived from the public key.
- The public key is used by others to encrypt the messages they send to you, but to decrypt and read these messages, one needs access to the private key.
What Is the Difference Between Symmetric and Asymmetric Encryption?
As we’ll explain shortly, there are five main differences between symmetric and asymmetric encryption. Some of these differences relate to the types of keys used and others relate to how long the encryption methods take to compute.
So, when we talk about symmetric vs asymmetric encryption, which is more secure? Asymmetric encryption is the more secure one, while symmetric encryption is faster. They’re both very effective in different ways and, depending on the task at hand, either or both may be deployed alone or together.
Hopefully, you now have an understanding of the difference between symmetric encryption vs asymmetric encryption. The table below provides a more in-depth comparison between symmetric vs asymmetric encryption:
| Differentiator | Symmetric Key Encryption | Asymmetric Key Encryption |
| 1. Symmetric Key vs Asymmetric key | Only one key (symmetric key) is used, and the same key is used to encrypt and decrypt the message. | Two different cryptographic keys (asymmetric keys), called the public and the private keys, are used for encryption and decryption. |
| 2. Complexity and Speed of Execution | It’s a simple technique, and because of this, the encryption process can be carried out quickly. | It’s a much more complicated process than symmetric key encryption, and the process is slower. |
| 3. Length of Keys | The length of the keys used is typically 128 or 256 bits, based on the security requirement. | The length of the keys is much larger, e.g., the recommended RSA key size is 2048 bits or higher. |
| 4. Usage | It’s mostly used when large chunks of data need to be transferred. | It’s used in smaller transactions, primarily to authenticate and establish a secure communication channel prior to the actual data transfer. |
| 5. Security | The secret key is shared. Consequently, the risk of compromise is higher. | The private key is not shared, and the overall process is more secure as compared to symmetric encryption. |
| Examples of Algorithms | Examples include RC4, AES, DES, 3DES, etc. | Examples include RSA, Diffie-Hellman, ECC, etc. |
Table 1: Symmetric Encryption vs Asymmetric Encryption
Symmetric vs Asymmetric Encryption in the Context of the SSL/TLS Handshake
When we surf the net using the insecure HTTP protocol, data travels in an unencrypted format that can easily be intercepted and stolen by anyone listening in on the network. SSL/TLS certificates are used to encrypt the communication channel between the client (web browsers like Chrome, Firefox, etc.) and the server you’re attempting to connect with so you can browse securely over HTTPS. While there are a number of steps involved in the handshake, the entire encryption process (that begins using asymmetric encryption and later switches to symmetric encryption for bulk transmission) takes only a few milliseconds.
Every time we connect to a website over HTTPS, an encrypted communication channel is established between our client browser and the server hosting the site. Let’s get a brief overview of where encryption comes into play when setting up a secured connection:
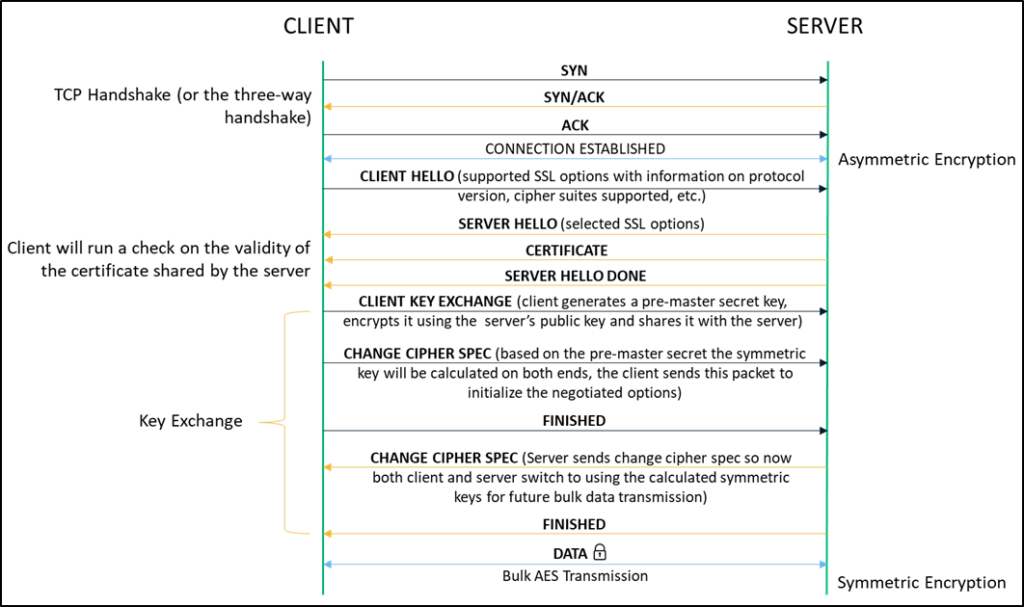
![]() Connection Negotiation
Connection Negotiation
Following the three-way handshake between the client and the server, the SSL/TLS process begins with the client hello message which, in addition to other parameters, also communicates the supported cipher suites (e.g., RSA, Diffie-Hellman, etc.).
The connection is negotiated based on the highest encryption standard that is supported by both the client and the server.
Key Exchange
With the server hello message, the client receives the server’s digital certificate that holds its public key. It uses this key to generate a pre-master secret after verifying the validity of the server certificate. The client sends over the pre-master key to the server after encrypting it with the public key. The server uses the private key to decrypt and obtain the same pre-master key. The symmetric key is calculated separately by both the client and the server based on the value of the pre-master secret key.
Change Cipher Spec
After calculating the symmetric key, both the server and the client send a change cipher spec message to each other. This indicates that the remaining communication involving any bulk data transfer will be done using symmetric keys (by applying encryption standards such as AES) over a secure encrypted channel.
In Summary: In the Debate of Symmetric vs Asymmetric Encryption, Both Are Important
We’ve just about gone over all the main concepts around symmetric vs asymmetric encryption. By now, queries around “what is the difference between symmetric and asymmetric encryption” and “symmetric key vs asymmetric key” should have been cleared up. Though they’re both exceedingly different based on varying mathematical constructs, they’ve both found their application in numerous scenarios. For instance, symmetric encryption is used to protect file content or comes into the picture in disk encryption, and asymmetric encryption is used with digital signatures.
Apart from SSL, a combination of both these techniques is used in many other scenarios. Messaging applications such as Signal or WhatsApp use end-to-end encryption where asymmetric encryption is used to initialize the encrypted communication channel, and the rest of the conversation proceeds using symmetric encryption.














 (83 votes, average: 4.24 out of 5)
(83 votes, average: 4.24 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security