What Is DES Encryption? A Look at the DES Algorithm
The data encryption standard (DES) was endorsed by the National Security Agency (NSA) from 1974 to 2002. For around 30 years, the DES algorithm ruled the cryptography world as the go-to encryption algorithm. But what is DES encryption exactly, and what were the reasons behind its discontinuation?
What is DES encryption? In a nutshell, the data encryption standard a type of encryption cipher, meaning a way to disguise information from unauthorized parties. If we think about the most basic form of cipher, we might think of the “secret” conversation two parents have by spelling out words they don’t want their child to hear. Unfortunately for parents, as their child becomes older, the code stops working. One day, bam! The kid knows how to spell “C-H-O-C-O-L-A-T-E.” The secret code no longer serves its purpose.
Something very similar has happened in the cryptography space. In times past, the data encryption standard was used to encrypt online communication. Nowadays, it has fallen out of use due to technological developments making it an increasingly insecure encryption method.
What Is the DES Algorithm? A Definition of DES Encryption
So, what is DES? The data encryption standard, or DES, is an encryption algorithm that converts plaintext into blocks then uses a key to convert it to ciphertext. DES is based on an earlier cipher by cryptographer Horst Feistel, called Lucifer. Developed in the 1970s, Lucifer was one of the earliest block ciphers.
DES is a symmetric algorithm, meaning that it uses a single key both to encrypt and decrypt communications and other data. This is different from asymmetric encryption, which uses two unique keys to encrypt (public key) and decrypt (private key) data and communications.
Why Is It Important to Learn About DES?
You might be wondering why you should learn about DES if it’s already obsolete. Well, although it’s true that the DES algorithm is no longer used for security purposes, it is still the basis for other security algorithms. So, learning what DES encryption is and how it works will also benefit your cybersecurity knowledge and understanding of cryptography as well. As such, your knowledge of DES will help you understand how other encryption algorithms work.
So, let’s learn about DES in some detail.
How Does DES Work? A Look at the Data Encryption Standard Process
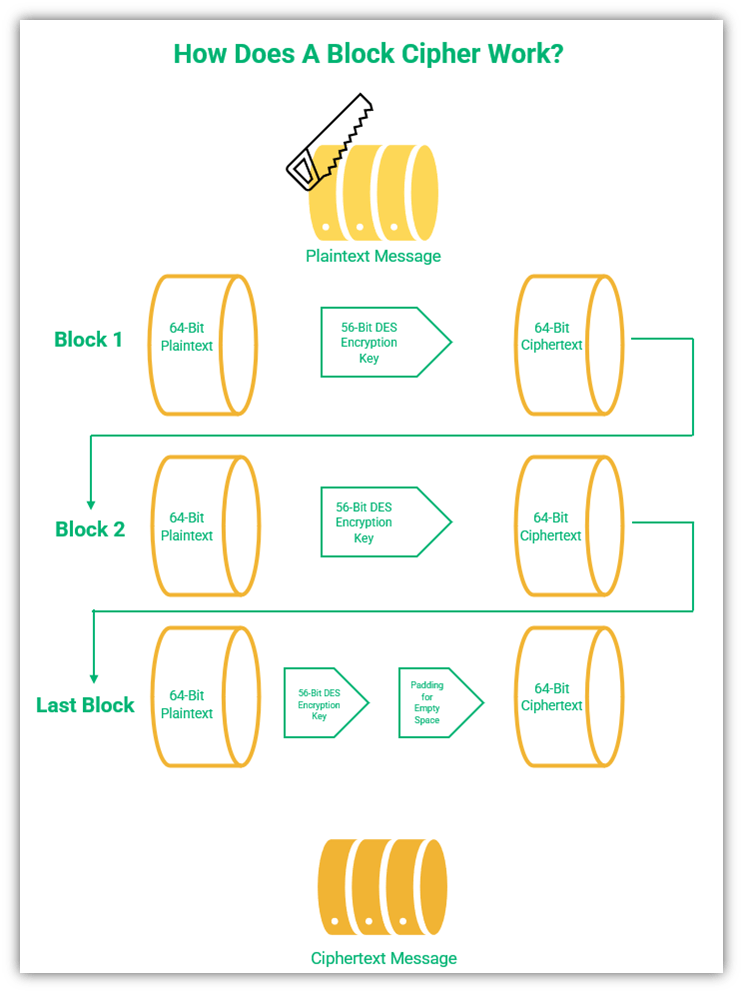
The basis of DES is bits, that is, binary numbers — i.e., 0s and 1s. Hexadecimal, or base 16 numbers, are made up of four bits. To encrypt a message, the data encryption standard:
- Creates blocks of 16 hexadecimal numbers (equal to 64 bits) using an encryption key.
- Encrypts 64 bits of plaintext (blocks) and returns 64 bits of ciphertext.
- Performs 16 rounds of processing using Feistel function (more on it later),
- Fortifies the encryption with additional initial and final permutations
The initial length of the key is 64 bits. However, every eighth bit is dropped, effectively making it a 56-bit key. Before being dropped, these eight bits, known as parity bits, are used to check the two versions of the message and detect errors in the code.
So, with DES a message is divided into blocks of 64 bits. One problem with this is that not all messages have a length exactly divisible by 64, so the last block might be smaller than 64 bits. This means that the last part of the message has to be padded with extra bits to fill the space. There are different methods of padding the messages. One method is to use 0s at the end of the message to fill the gap and the numbers are then removed upon decryption.
A figurative representation of how a block cipher encryption works
DES Encryption Is a Six-Step Process
Now that we know what this block cipher method of encryption is, let’s quickly break down how DES encryption works:
- The message is divided into 64-bit blocks.
- An initial permutation is carried out on the plain text blocks.
- Permuted blocks are divided into two halves, each of which is 32 bits – left plain text (LPT) and right plain text (RPT).
- Both LPT and RPT go through 16 rounds of encryption. Each round of encryption has five steps:
- Key transformation — Key transformation is a process wherein 16 different subkeys measuring 48-bits each are derived from the main key to encrypt plaintext. The key schedule is used to derive these keys. The following video explains the key schedule in detail:
- Expansion permutation — A half-block of 32-bits is expanded to 48 bits using expansion permutation. It adds adjacent bits from each side of the block to the 32-bits of the block to create a 48-bit block.
- S-Box permutation — A substitution box permutation, or S-box, is the only non-linear component in the DES algorithm. It provides additional security to the cipher. After the block is mixed with the subkey, it is divided into eight 6-bit parts. The S-box process uses a lookup table to convert the eight 6-bit parts into 4-bit output each, resulting in 32-bit output in total.
- P-Box permutation — The 32-bit output from the S-box permutation is rearranged according to the P-box permutation. The design of the P-box permutation ensures that the output of each S-box is spread across four different S-boxes for the next round of encryption.
- ExclusiveOR (XOR) and swap — XOR is a mathematical function that compares two sets of bits that can be either 1s or 0s. If the bits from both sets match, the XOR output is 0. On the other hand, if they don’t match, the output is 1. This bit-wise comparison results in stronger encryption, and XORing is something we’ll speak more about in our next article on how DES encryption works.
- LPT and RPT are combined.
- The final permutation is performed on the combined LPT and RPT, resulting in the final ciphertext.
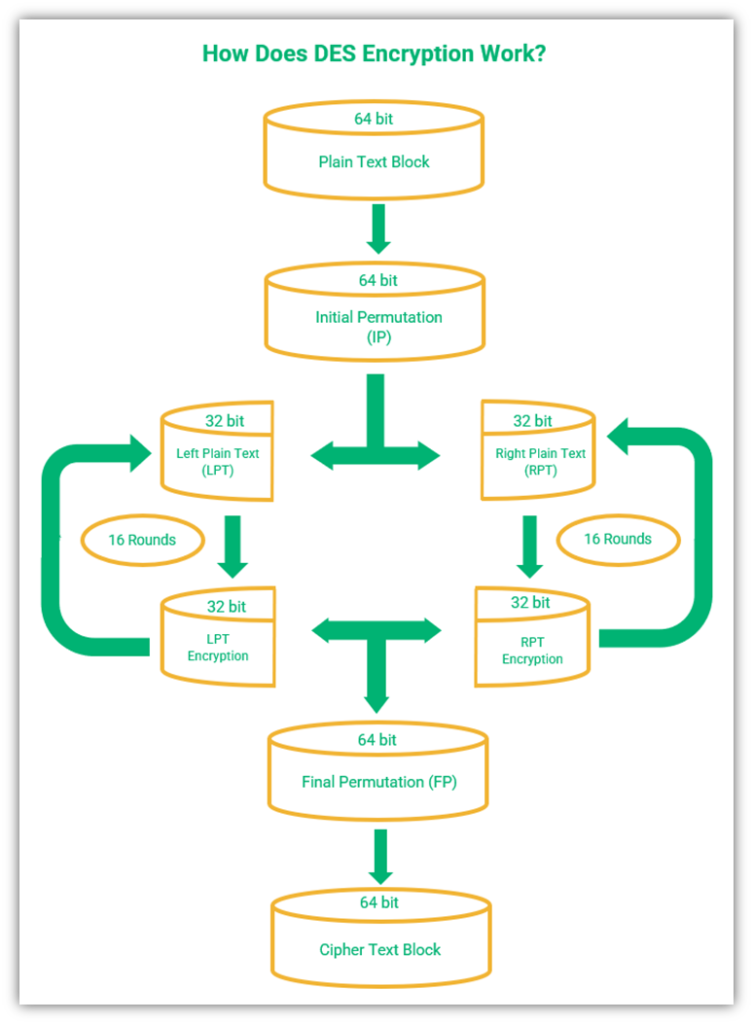
So, that’s how you get a ciphertext using DES. But how are the messages decrypted?
Well, as we know, DES is a symmetric encryption algorithm. Therefore, the very key that is used to encrypt your plaintext data can also be used to decrypt it. In a basic sense, decryption requires the same steps as encryption but runs through them in reverse order.
DES vs Triple DES (3DES)
Triple DES (TDES or 3DES) is another encryption algorithm that involves using DES three times to encrypt a text. While DES encrypts a block of data in 16 rounds, 3DES uses 48 rounds. Although it is a little stronger than DES, 3DES has proven to be ineffective in securing transmissions. Because 3DES is vulnerable to brute force attacks, the National Institute of Standards and Technology (NIST) has officially disallowed the use of 3DES after 2023. It seems the cryptography world has moved on to AES.
The 4 DES Modes of Operation
Being a block cipher algorithm, DES has several modes of operation, some of which start with initialization vectors (IVs) that help eliminate predictable patterns. Some of the most well-known modes of DES operation are as follows:
1. Electronic Codebook (ECB) Mode
ECB is the simplest operation mode of all block ciphers. It’s used to encrypt data one block at a time. The first block is encrypted, then the second block, and so on until the last block is encrypted. All blocks are encrypted using the same key — no other variable is used.
When ECB is used in the same plaintext multiple times, it will result in the same ciphertext making it pretty easy to crack. This weakness can result in man in the middle and brute force attacks.
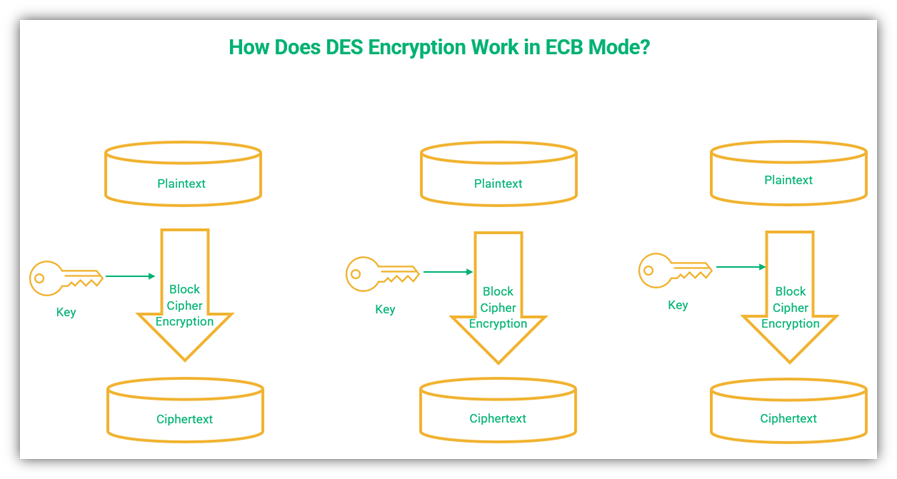
A graphical representation of the ECB mode of operation in DES encryption.
2. Cipher Block Chaining (CBC) Mode
Cipher block chaining is an operational mode that involves incorporating data from the previous block into each new block. CBC mode uses an initial vector (IV) in addition to the symmetric encryption key to encrypt data.
The main feature of CBC is that it uses a chaining process while encrypting blocks, so the decryption of a particular block is dependent on the previous block. An XOR coding mechanism is used in CBC to integrate the inputs. This prevents two identical blocks of plaintext from producing the same ciphertext.
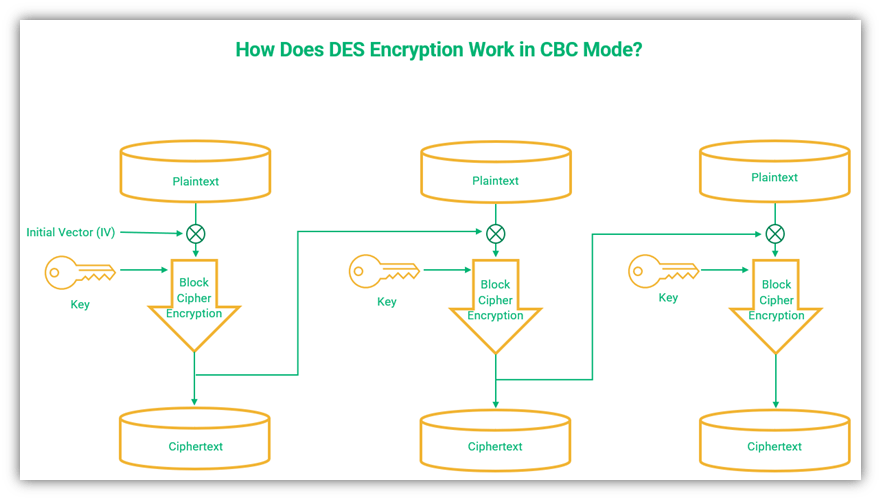
A figure showing how DES encryption works using the CBC mode of operation.
3. Cipher Feedback (CFB) Mode
The cipher feedback mode is a type of block cipher that uses segments instead of blocks to carry out feedback encryption to create pseudorandom bits. Each segment can range from one bit to the full block size specified by the algorithm you use (DES, AES, etc.).
CFB mode uses an initial vector (IV) to start the encryption of the first data block. Each new input block uses the previous output block’s ciphertext to encrypt the next block, which is a process known as feedback. The encryption algorithm generates the keystream that is placed in the bottom register. An XOR function is carried out between this keystream and the plaintext.
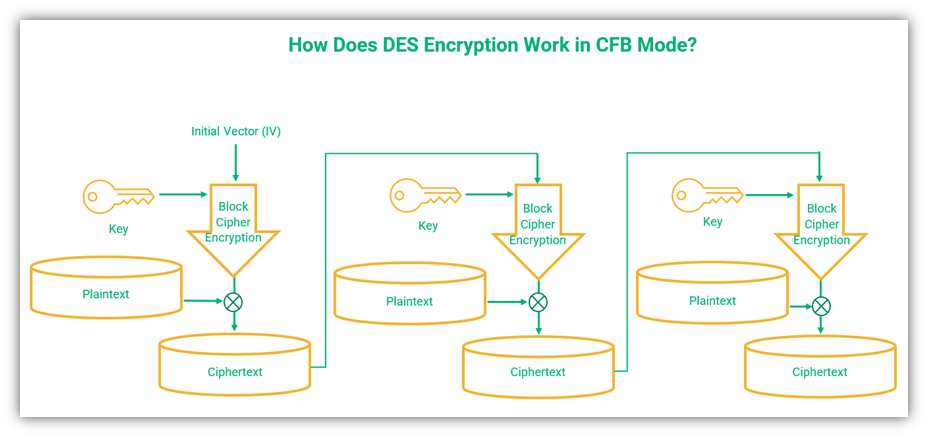
A simplified illustration of DES encryption using the CFB mode of operation.
4. Output Feedback (OFB) Mode
OFB is similar in design to CFB mode but has some clear-cut differences. The output of CFB mode is further encrypted with a key to generate the ciphertext. The key is generated through an internal mechanism independent of the plaintext and the ciphertext. This results in different ciphertexts for identical blocks.
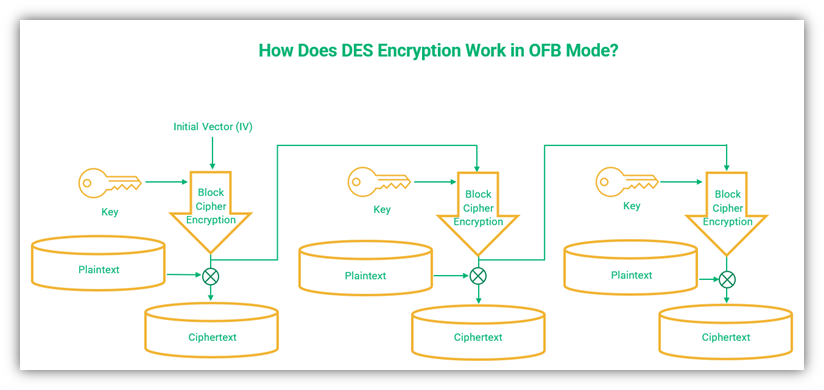
A simplified visual representation of DES encryption using the OFB mode of operation.
If you want a more in-depth look at the different block cipher modes of operation, be sure to check out this article on block ciphers vs stream ciphers that breaks all of that down.
What Makes DES a High-Risk Algorithm?
Don’t worry if that last section had you scratching your head. It’s not as important that you understand exactly how DES works in a more technical sense as it is that you realize that it’s no longer a reliable method of data encryption in today’s digital world. Let’s explore why not.
While DES was designed by IBM, the NSA played a significant role in its development. Although the NSA has historically denied that a backdoor be placed in the code, they admitted to requesting that the original 64-bit key be reduced to 48 bits. Eventually, a compromise was reached, and the 64-bit keys were reduced to 56 bits.
The shorter key length was considered sufficient at the time, but as available computing power has increased over time, it’s no longer strong enough. This increase in computing power means DES is susceptible to brute-force attacks, where the cybercriminal applies every possible key until they find the right key. A 56-bit key can be cracked in 256 attempts, which back in 2017 might have taken a year. Today, websites like crack.sh offer to crack 56-bit DES keys within 26 hours for a price.
Block ciphers get much of their security from the s-box, or substitution box. It’s kind of complicated, but the s-box is where one value is replaced with another to produce the encrypted text. When you change the values in the s-box, the output changes. The method by which the DES s-boxes were generated was not made clear, and there has been much speculation about the possibility of them acting as backdoors for the NSA. Despite repeated denials by the NSA about these claims, the debate continues.
To conclude, the reasons behind the discontinuation of the DES encryption standard are as follows:
- Devices with improved processing capabilities were developed, thereby reducing the time for brute force attacks
- DES cracking proved to be an intelligence challenge in the cyber community
- Stronger encryption standards were developed, including Triple-DES
3 Methods Used to Crack DES Encryption
There are many ways to crack the DES encryption. Let’s explore a few of them:
Differential Cryptanalysis (DC)
In 1990, two cryptographers named Eli Biham and Adi Shamir (one of the namesakes of the RSA algorithm) independently discovered differential cryptanalysis (DC), a method to crack cipher codes. We say “independently” because IBM and NSA had knowledge of DC previously (perhaps from the 1970s), but it was a well-guarded secret.
When the two cryptographers discovered differential cryptanalysis and released an open publication, cracking the 16 rounds of DES encryption became possible for the amateur cryptographer for the first time. As such, DES had to be redesigned to withstand DC attacks.
Linear Cryptanalysis
In 1993, Japanese cryptographer Mitsuru Matsui discovered that DES was susceptible to linear cryptanalysis. Linear cryptanalysis is a plaintext attack where a cybercriminal uses something known as probabilistic linear relations between parity bits of the plaintext, the ciphertext, and the secret key to try to figure out the secret key’s parity bits.
You see, the parity bits of the key can be guessed if the probability of the approximation is high. When the attacker successfully approximates parity bits in the key, they can crack the DES code.
Davies’ Attack
Donald Davies designed a technique in the 1980s to crack DES, which was further improved by Biham and Biryukov in 1997. The improved attack has a 51% success rate and is faster than a brute force attack. Translation: an attacker has more chances to crack DES encryption through improved Davies’ attack than by using either differential cryptanalysis or linear cryptanalysis.
The DES Timeline
The main events that took place during the lifetime of DES are as follows:
- 1973-74: The DES algorithm is developed by IBM.
- 1974: The NSA adopts DES as a government-wide standard for encryption.
- 1976: DES is approved in the United States as a federal standard.
- 1983, 1988, 1993, and 1999: Federal approval is reaffirmed by the NSA.
- 1999: The more secure triple DES algorithm is recommended by NIST.
- 2005: NIST withdraws affirmation of DES. However, Triple DES is given confirmation for sensitive government information.
Meanwhile, in 2002, the more secure advanced encryption standard (AES) was becoming the algorithm of choice.
In the 70s and 80s, DES was considered to be a strong encryption standard. But, like when children learn their parents’ secret spelling codes, people eventually learn how to crack more complex codes. As DES was used by the U.S. government and had a stamp of approval from the NSA, it was under scrutiny from many people in the security world. Many cryptography challenges were initiated to test the security of DES, including public competitions where competitors were invited to crack the code and decrypt a message as quickly as possible.
Four public competitions sealed the fate of DES:
- DES I (1997): It took the DESCHALL Project 96 days to crack the code and decrypt the message using brute force.
- DES II-1 (1998): Distributed.net took 39 days to decrypt the message.
- DES II-2 (1998): This time, theElectronic Frontier Foundation (EFF) cracked the code in just 56 hours.
- DES III (1999): Finally, a joint effort between distributed.net and the EFF cracked DES in less than a day — 22 hours, 15 minutes to be precise.
After the competitions, the vulnerabilities in DES algorithm were revealed to all. Unbelievably, DES is still used sometimes even though it’s long since been superseded by AES. So, if you’re still using DES, it’s time to bid it farewell!
What’s Next for DES Encryption? Nothing Since You Should Now Be Using AES…
In 1997, NIST declared that it was time to look for a replacement for DES. After a thorough evaluation, they selected the Rijndael cipher. After making a few changes to Rijndael, the advanced encryption standard (AES) came into being and was unveiled in 2001. AES features key lengths of 128, 192, and 256 bits, and uses bigger blocks of 128 bits, which makes it a pretty reliable cipher. If you compare DES and AES, you’ll see that AES is far more secure than DES.
With constant improvement in technical expertise and increased computer processing capabilities, it’s inevitable that security algorithms become obsolete after a few years. Although there are no indications that AES-256 is vulnerable, it is probable that security enthusiasts will discover vulnerabilities in AES at some point in the future. However, it’s vital that if you’re still using DES, you upgrade your operating system and your user accounts immediately to the more secure AES.
Shor’s algorithm was discovered by an American mathematician Peter Shor. Under specific circumstances Shor’s algorithm can crack public key cryptography algorithms like RSA, finite field Diffie-Hellman, and elliptic curve Diffie-Hellman using quantum computers. AES 256 is considered quantum resistant. The time taken to crack the algorithm, even with quantum computing, is so long that it isn’t practical to do so.
AES 128 can be cracked within 264 attempts, whereas AES 256 require 2128 attempts to crack. Although AES 128 is theoretically vulnerable to brute-force attacks, AES 256 coupled with a strong password is virtually unbeatable at this point because it would take too long and require too many resources to be feasible.
Final Thoughts on the Data Encryption Standard (DES)
DES was a crucial encryption standard for many years and has played an important historical role in data security. However, with improvements in computing power and technical know-how, it eventually had to be replaced with the stronger AES algorithm.
Encryption is a part of our online lives and understanding how it works helps us to stay secure. To learn more, read our next article on the subject where we explore the intricacies of how DES works.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security