The TLS Handshake Explained [A Layman’s Guide]
The SSL/TLS handshake is as much a part of cybersecurity on the internet as encryption itself — it’s all about ensuring that the other party you’re connecting to is legitimate and that no bad guys can steal your data
Think of the last time you made a purchase from your favorite online website. When you were logging into your user account, there was a risk that your information could be intercepted and stolen by cybercriminals. That’s just the cold reality of our world — there’s always a cybercriminal somewhere who would love to get their grubby hands on your sensitive information.
The reason why logging in is so risky is that when data is in transit — meaning, it’s moving from your browser to the server of the website you’re connecting to — it’s using an insecure connection. This is always the case unless the website’s owner does something to make the connection secure. A TLS handshake helps mitigate this issue: the handshake is a way to bring digital identity and data integrity into the fold to help make such online transactions secure.
But what is the TLS handshake (sometimes called an SSL handshake) and how does it help create a safer and more secure experience for website users?
What Is the TLS Handshake? TLS Handshake Explained
The simple way of looking at the SSL/TLS handshake is that it’s a communication process that enables two parties to communicate securely on the internet. This is done by enabling the use of the secure hypertext transfer protocol (HTTPS) (instead of relying on the insecure traditional HTTP) by forming a TLS connection. TLS, which stands for transport layer security, is the successor of SSL (secure sockets layer) and is the set of rules browsers use to connect to websites on the internet.
It’s customary to shake hands and introduce yourself when meeting someone for the first time. (Or, in the post-COVID era, bump elbows or some other similar greeting.) Similarly, the TLS handshake is how a web browser and the site server it’s connecting to:
- Make introductions
- Verify one or both parties’ identities,
- Agree about how they want to communicate securely, and
- Negotiate the shared secret they want to use to ensure their communications stay private.
What’s the point of the introduction? Let’s consider this question from the perspective of your site visitor and you as a site owner:
- As a user: The TLS handshake gives your web browser (client) a chance to verify the digital identity of the entity it’s trying to connect to on the other end (e.g., a website’s server). This way, you know your data is being sent to and read by the right party.
- As a site owner: The TLS handshake is an opportunity for your web server to introduce itself to the visitor’s web client. It also enables your server to choose cryptographic algorithms that will allow you to receive and access the visitor’s sensitive data securely.
A TLS Handshake Uses Identity to Enable Secure Connection on Insecure Networks
Before the development of the internet (or, more specifically, public key infrastructure), people had to travel and be in the same physical location to exchange information securely. There was a certain level of implicit trust involved, as you could see the person you were meeting with and could verify their identity by checking their official government-issued ID card.
The creation of the internet made remote access and communications possible, however, it also created a slew of new issues because it isn’t secure. Anyone with the know-how can intercept messages (this is called a man-in-the-middle attack) and steal, alter, or even delete some or all of the data while it’s in transit.
This is where public key infrastructure and public key cryptography come into play: it’s all about using secure processes and digital identity to create a secure communication channel. By using authentication of digital identity and protecting the integrity of your data, two parties can securely exchange data without having to physically be in the same place.
The TLS handshake enables one or both parties to authenticate and negotiate all of the technical details regarding how to communicate. This means that there are mechanisms in place that help prove one or both parties are who they claim to be and aren’t skeevy imposters. The handshake itself is just a term that describes the back-and-forth data exchanges that occur in the blink of an eye.
A TLS Handshake Helps You Feel Confident Exchanging Info With Someone You’ve Never Met
As we touched on, a TLS handshake is a way for one or both parties to identify themselves and engage in secure communications. In some ways, it reminds me of the time my husband and I traveled to Mexico. As native English-speaking Americans, we got first-hand experience of what it’s like being somewhere where English isn’t the primary language. (It was eye-opening, to say the least.) At the resort, we were fine because virtually everyone there spoke English. But once we traveled outside the resort, it was a different story.
One of the most shocking experiences was when we landed at the airport. There were mobs of taxi drivers and transportation service workers from different companies waiting, trying to pick up unsuspecting travelers. Thankfully, we’d done our research and read up on the travel scams that are common in the area. As such, we knew that many of these drivers would pretend to be our legitimate transportation company to get us to hire their services and pull different scams.
The legitimate transport company we hired in advance gave the driver our names and provided us with the following information:
- Specific directions about where to meet their driver at the airport,
- The driver’s name,
- A description of what he’d be wearing, and
- A description of what his vehicle would look like.
In some ways, a TLS handshake is similar. Much like how the server verified who it was we would be meeting up with and validated he was one of their employees, a server identifies itself using an SSL/TLS certificate. This is how things go in the traditional TLS handshake when you’re connecting to a website. This is known as one-way authentication because only the server has to prove its identity.
But a TLS handshake isn’t only useful for one-way authentication; it can also be used for mutual or two-way authentication, meaning that the browser and web server it’s connecting to can verify each other’s identities. In the case of our Mexico trip, since we also provided our information to the company, the driver knew our names and could check our IDs to ensure he was picking up the right passengers.
An Overview of How the TLS Handshake Works
Okay, now that we know what a TLS handshake is, let’s get into the fun part and explore how performing a TLS handshake works. The TLS handshake is basically a back-and-forth dialogue between your web server and the site visitor’s client. In a traditional TLS handshake, the browser is the one that initiates the conversation, but it’s up to the server to prove its identity. This way, the web client knows it’s connecting to your legitimate website (and not an imposter’s version of it).,
When talking about how the TLS handshake works, though, it’s important to point out that the specifics of this process vary depending on whether you’re talking about TLS version 1.2 or TLS 1.3. Why? Because these two protocols work differently to achieve the same end goal. Let’s talk through a TLS 1.2 handshake before moving on to see how differently TLS 1.3 operates.
How the TLS Handshake Works in TLS 1.2
TLS 1.2 is the older and most commonly used protocol. According to SSL Lab’s January 2023 data (based on Alexa’s list of the top 150,000 SSL/TLS enabled websites), 99.9% of websites still support TLS 1.2 to enable secure HTTPS connections. It involves two round trips — this term refers to the number of times the initiating party has to reach out and receive messages from the server.
Let’s take a quick peek at what this looks like in practice:
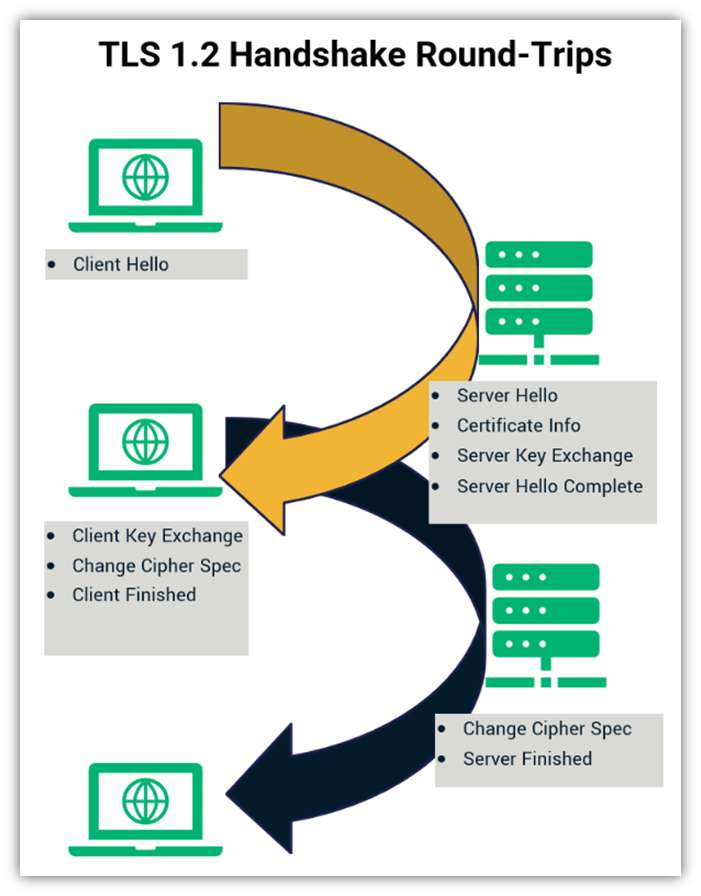
Look at the first golden arrow. It reaches out from the web client to the web server before circling back again. Then the client reaches out a second time (as illustrated with the dark arrow); it receives a response from the server, and the two use the exchanged data to establish a secure, encrypted connection. This is basically a series of four communications that occur within milliseconds:
1. Client Hello
This is when the user’s web client initially reaches out to establish a connection with the web server. Basically, it’s initiating an introduction and making it known to the server that it wishes to connect.
2. Server Hello and Certificate Delivery
This next step is when the server responds for the first time. It’s an opportunity for the server to:
- Present its SSL/TLS certificate (i.e., its version of a passport to prove its digital identity),
- Share its SSL/TLS cipher suite information (i.e., what cryptographic algorithms it supports), and
- Provide information that’s necessary for key exchanges using specific algorithms (it’s not a requirement for all SSL/TLS handshakes)
Of course, things can go wonky in this part of the process if your digital certificate is expired or there’s a misconfiguration issue. Check out our article on the TLS handshake failed error to learn more about these situations and how to mitigate them.
3. Client Key and Cipher Spec Exchange
Here, the client sends the server information its needs to decrypt and use a secure session key. (This is what will be used to create the secure, encrypted communication channel.) It also gives the server the heads up that it’s switching to that encrypted channel to communicate from this point on.
4. Server Changes to the Agreed Upon Cipher So Both Parties Can Connect Securely
Once the server gets the message, it takes the info received from the user’s web client and decrypts it. This enables it to calculate a shared session key that can be used to connect via an authenticated, secure channel.
Yup. That’s, basically, the TLS 1.2 Handshake in a nutshell! Now that we’ve seen how this works, let’s switch gears to change out the streamlined version of this process that occurs when using the TLS 1.3 handshake.
The TLS Handshake in TLS 1.3 Is Similar But Requires Fewer Steps
TLS 1.3 is the latest version of this data exchange protocol. While it’s supported by 57.8% of websites (as of SSL Lab’s October 2022 data), it’s still far from being widely accepted or supported by browsers. However, it does support stronger and more secure algorithms.
One of the biggest differences between the TLS handshake in TLS 1.2 and 1.3 is that TLS 1.3 offers a fully signed handshake process that requires fewer round trips. This increases efficiency and reduces latency because it takes less time to complete. Simply put, it’s a win for you and for your website users — particularly if you’re a large organization that handles traffic on a massive scale.
Here’s a quick look at how the process works:
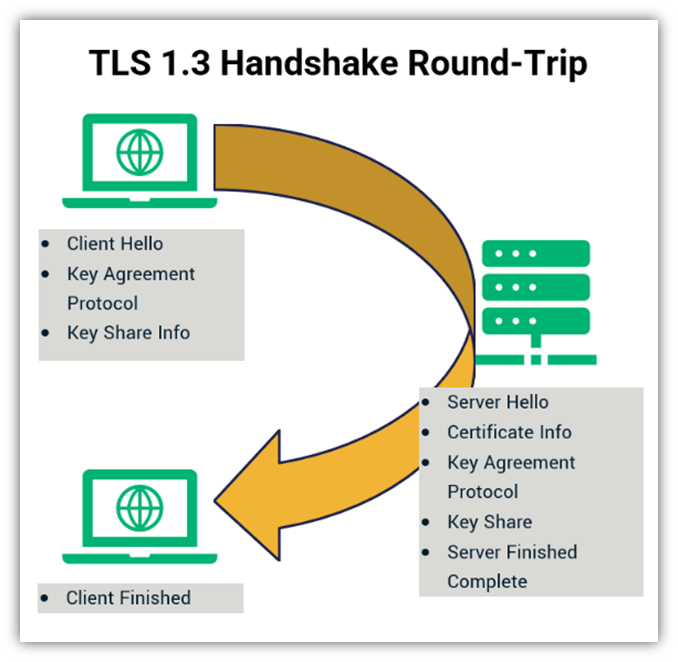
Of course, the single round-trip isn’t the only difference between TLS 1.2 and 1.3. Remember the more secure algorithms we mentioned earlier? TLS 1.3 eliminated the RSA (Rivest Shamir Adleman) key exchange, so it supports only algorithms that offer perfect forward secrecy. (This is what prevents data from being compromised retroactively by using compromised keys to decrypt saved communications.)
Another change is the addition of a feature that helps speed up TLS 1.3 even more: zero round trip time resumption, or what’s otherwise known as 0-RTT. The idea here is that users who have previously visited your site can connect more quickly because they resume the session they’d previously established.
For a more in depth look at the TLS handshake, be sure to check out this great explainer video from Computerphile:
[Embed video: https://www.youtube.com/watch?v=86cQJ0MMses]
Final Takeaways on the TLS Handshake and Its Role in Internet Security
Much like my experience in Mexico, I hope this article has been enlightening and has taught you a lot about what the TLS handshake is and how it facilitates secure communications. It’s a critical process that occurs in the background, unbeknownst to your website users.
No matter how you look at it, the TLS handshake has become integral to secure online authentication and communications. Not only is it a requirement of cybersecurity regulations and data privacy laws across many industries and geographic regions in the sense that many of these regulations require the use of encryption to protect data (in transit, at rest, or both), but it’s also just a good website security best practice to implement.
As a website owner, you have the responsibility to ensure that you keep your website and its connections as secure as possible. To learn more about how to make your website as secure as possible, be sure to check out the following resources:












![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-940x588.jpg)








2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security