What Is a Phishing Email? 5 Examples of Phishing Emails and How to Avoid Them
Follow 9 tips mentioned in this article to protect yourself from phishing emails
No one falls for the “Nigerian Prince” email trap nowadays! Not even my 85 years old grandma! After all, we are smart people who learn from our own (and others’) mistakes. But, nowadays, phishing scams are way more sophisticated and advanced.
Modern phishing emails are crafted with intense research and using the advanced level of hacking techniques that can easily manipulate the victim psychologically if they are not vigilant enough.
According to the FBI, loss from the phishing attacks exceeded $3.5 billion in 2019 alone.
In this article, we’ll explore the topic of phishing emails in detail. The content includes plenty of the latest real-life examples, the types of scams being executed via phishing emails, and tips to protect your organization (and yourself) from such traps.
What Is a Phishing Email?
When we talk about a phishing email, we’re referring to a hoax email that’s sent out to defraud the recipient or to get them to do something they shouldn’t. Attackers send phishing emails impersonating someone else to cheat the recipient.
The cybercriminals psychologically manipulate the victims to take actions such as sharing financial or personally identifiable information (PII), login credentials, trade secrets, company’s confidential data, etc., or wire transferring money to the attacker’s bank account.
They can send an email pretending to be:
- Your employer/colleague
- A company you trust
- A reputable educational institute
- A recruitment agency/job board
- The local or federal government
- Friends/relatives/spouse
- Your bank/financial institution
For example, look at the screenshot below:
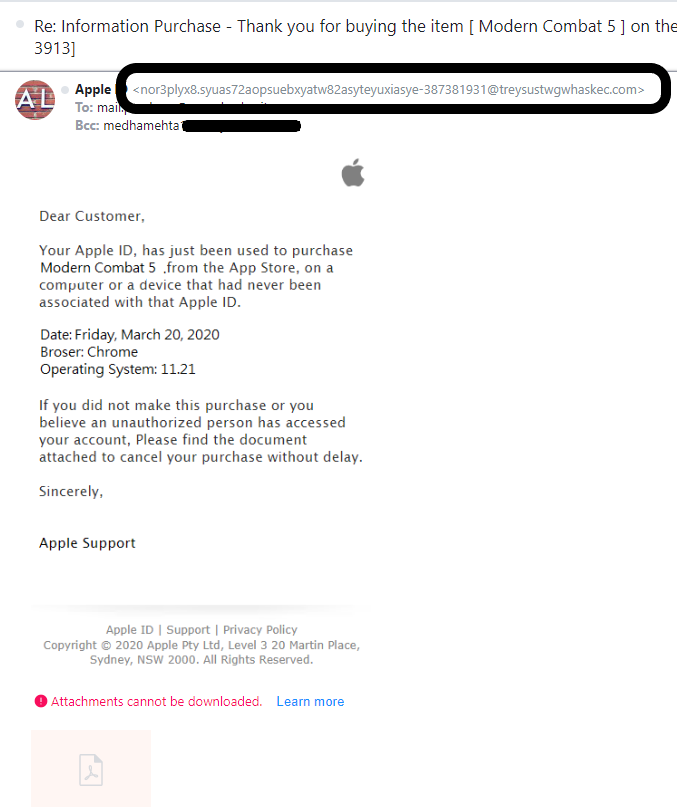
This email that I received looks like coming from Apple. But when I checked the email header, the original sender’s email address indicates a fraudulent one.
We’ll show you more phishing email examples later in this article.
Phishing can be executed by many methods such as voice phishing (or vishing), SMS phishing (or smishing), HTTPS phishing, watering hole phishing, etc. Among them, email phishing, also known as email spoofing, is one of the most common phishing techniques attackers utilize to execute various online scams.
5 Phishing Email Examples to Avoid
Now that we know the answer to the question “what is a phishing email?” let’s explore what types of scams are typically executed using phishing emails. To aid this task, we’ve pulled together a few phishing email examples.
Example 1: Charity Scams
As the name suggests, in this type of phishing attack, the perpetrator sends phishing emails asking for donations for various fundraising campaigns. They share heart-melting emotional stories and graphics of individuals suffering from a disease, poverty, starvation, or social circumstances. often, cybercriminals run fundraising campaigns for natural calamities like earthquakes, floods, cyclones, etc.
Needless to say, all of these campaigns are fake, and any money transferred is going into the con artist’s pockets only.
Sometimes, these types of phishing emails contain trojans, viruses, malicious attachments, or links that send you to a spammy website.
Check out another such phishing email that I received:

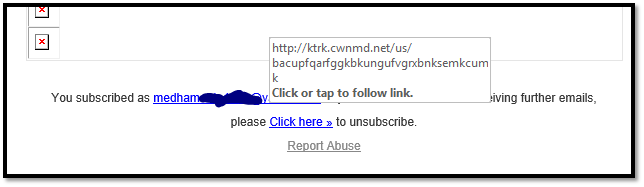
As you can see, when I hover over my cursor over the “Know More” button, the link it shows looks too dangerous to click on and visit.
The email also contains links for “unsubscribe” and “report abuse,” which are also malicious (as you can see in the screenshot below)
Example 2: Employment and Recruitment Scams
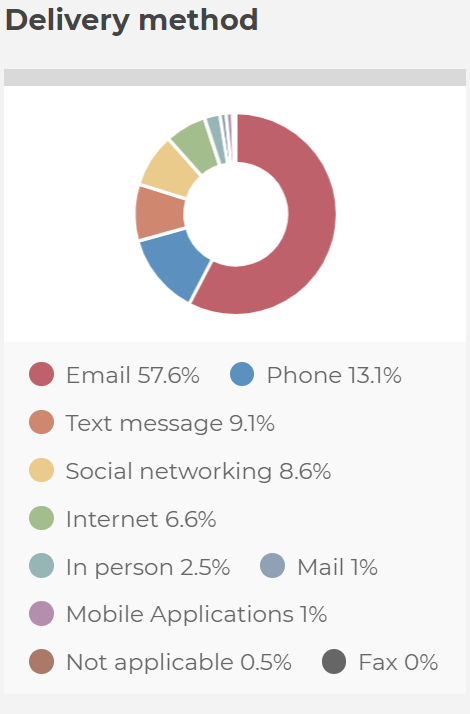
This is the type of scam where the scammers impersonate recruiters of legitimate companies to trick you into sharing your personal information or transfer funds. For recruitment scams, many platforms are used, such as employment websites, phone calls, text messages, etc. But sending phishing emails is the most utilized (58%) recruitment scam tactic.
The scammers send phishing emails directly to their targets’ email addresses as a part of a fake recruitment process.
They ask job seekers to share
- PII for running background check/credit check,
- bank account details for depositing salary in the future, or
- SSN for tax purposes.
The attackers sometimes ask the victims to transfer money, too, for various purposes such as buying online training materials or software.
The job seekers fall into the trap because the phishing emails are often well-crafted using the original company’s logo and text format.
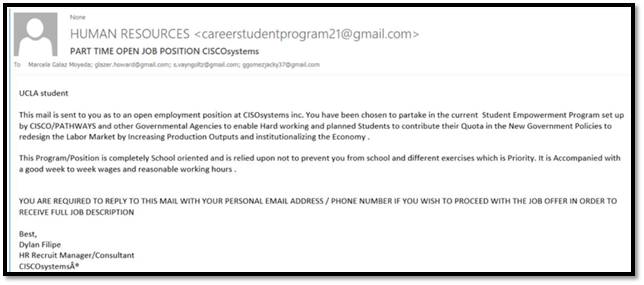
For example, check out the email below. The so-called “recruiter” is offering a job in CISCO systems but sending the email from the Gmail account! Also, notice the spelling and grammatical errors in the emails.
Example 3: Customer Support Scams
In this type of scam, the criminal sends phishing emails impersonating customer support representatives for well-known organizations such as travel industry companies, financial institutions, ecommerce companies, technology companies, or virtual currency exchange companies.
They offer help to the victims for solving issues such as
- removing virus on a computer,
- updating their PII on the system,
- adding new services to their existing account,
- renewing the software license, etc.
They ask victims to provide their PII, login credentials, financial information, etc., or ask them to click on the spammy links or download malicious attachments.
Check out the screenshot below that the people connected with McGill University received:
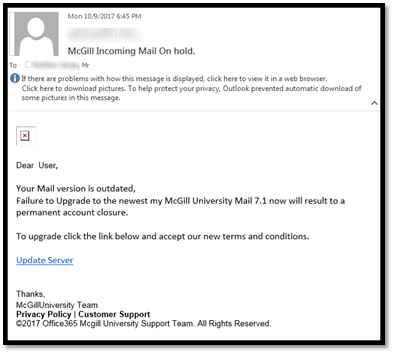
Even though the email looks somewhat legit and comes from the customer support team from McGill University, it’s a phishing email that was created to gain access to the recipients’ personal information. Upon discovering the scam, the university urged the recipients not to reply and share any information in addition to warning them to not click on the Update server link.
Example 4: Corporate Communication Scams
Sometimes the attackers send phishing emails impersonating your boss or colleague or any key company stakeholder such as a lawyer, tax officer, or accountant.
These messages are known as business email compromise (BEC)/email account compromise (EAC) scams. In 2019, the Internet Crime Complaint Center (IC3) received nearly 24,000 BEC complaints, and the organizations lost more than $1.7 billion.
For executing these types of scams, the perpetrator generally invests time to find out key employees and stakeholders’ names, designations, and email addresses.
Examples of common BEC,
- A phishing email that looks like coming from the technology department asking you to download new software.
- Sometimes, the attackers use an employee’s compromised email address to request the human resources or payroll department to update their bank account information in which their salaries are getting deposited. Obviously, the new bank account details belong to the attacker. Companies that are actively involved in online wire transfer of funds are generally at higher risk of being targeted by such scams.
- Check out the screenshot of an email I received recently. The sender impersonates himself as John Tuncer, my employer, and asks for the phone number! However, it’s easy to weed out such phishing emails just by checking the sender’s email address and noting their unusual way of typing. For example, notice the lack of spacing between the comma and the statement that follows:
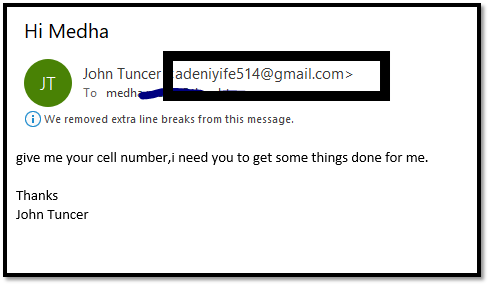
Spear phishing attacks and whaling attacks are some of the most popular methods to execute corporate communication scams.
Example 5: Financial Institution Scams
This is another type of BEC/EAC attack, where phishing emails are sent impersonating a financial institution such as a bank, credit card company, investment company, brokerage company, pension funds, or mortgage loan company.
The emails are crafted in a way that they resemble a company’s authentic emails. They generally use the company’s logo, font styles, and colors to make the emails look official.
These emails will typically ask you to:
- Click on a link that redirects you to a malicious website (that sometimes looks exactly like the original institution’s website),
- Download an attachment, or
- Reply with your PII or financial information.
Check out the screenshot below. Even though at first glance, it looks like an official Well Fargo email, when you check it carefully, you can see the red flags:
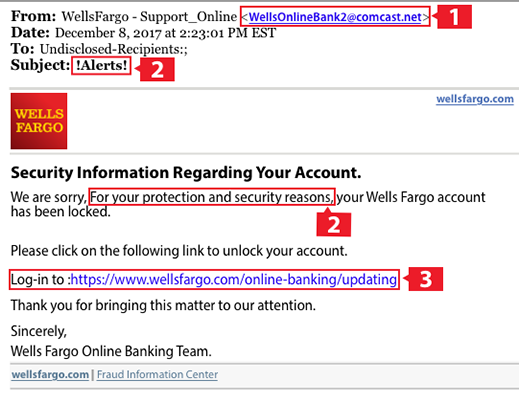
So, what are some of the indications that this is a phishing email?
- The sender’s email address is a non-wells Fargo email address.
- There’s a sense of unusual urgency in the email.
- Even though the Wells Fargo domain in the email looks like authentic, when you hover over it with your cursor, you can see that it redirects to another unknown website.
These types of phishing attacks became popular when in 2014, bulk emails were sent out by a hacker impersonating JPMorgan and urging recipients to click on a link to read a secure message. When users clicked on the link, Dyreza banking Trojan malware started to get downloaded in their systems!
The Motives Behind Phishing Emails
While it’s easy to assume that phishing emails are sent strictly for financial gains, there are frequently other reasons for their attacks. Let’s try to get a better understanding of attackers’ intentions:
- They want your money. Phishing emails deceive the recipients in sharing their payment card numbers or bank account details and misuse such information to get financial gains. Sometimes, the victims are tricked to make a wire transfer money to the perpetrator’s bank account.
- They want your personally identifiable information. Phishing emails also induce people to share their PII, such as phone number, physical address, social security number (SSN), etc. This PII is used to execute crimes involving identity theft (for example, opening a bank account or applying for a loan in someone else’s name). Or to sell that information in the dark market.
- They want to distribute malware. The attacker wants you to click on a link or download the software that inserts malware on your computer. These viruses can lock down the system and files as a hostage. The attacker asks ransom to give back access. This malware can allow the attacker to control your computer from a remote location, which can intervene with your privacy and steal your confidential files and other data.
- They want to tarnish your reputation. Sometimes, the attacker deliberately sends phishing emails using your name (or that of your organization) to tarnish your reputation and make the victims take action against you. It’s also known as “Joe Job.”
- They have an agenda or a political goal. Sometimes, government-sponsored hackers send phishing emails to acquire confidential political information, intellectual property, or the PII of other countries’ citizens. These state-sponsored phishing attacks are forms of cyber espionage.
One example of such an attack involved a Vietnam government-sponsored group named OceanLotus. They target foreign diplomats and foreign-owned companies inside Vietnam by sending them spear-phishing emails containing macros. Once the macro is enabled, it executes malicious payloads on the victim’s computer.
9 Tips: How to Stop Phishing Emails & Prevent Yourself from Becoming a Victim
You can’t prevent someone from sending you the phishing email. However, by following some below-mentioned tips, you can develop a vigilant attitude and protect yourself from becoming the victim.
- Check the sender’s email address. Always read the sender’s email address. Employees from reputable companies typically send emails from an email address with the company’s domain name. So, for example, if someone is claiming to be the official representative of Wells Fargo but sending you an email from Gmail/Yahoo/Hotmail email address, or any other unusual address, it’s a red flag. Official Wells Fargo emails will come from an account wending in “@wellsfargo.com.”
- Don’t ignore the errors. If there are spelling or grammatical errors, unusual tone, punctuation mistakes, or a sense of urgency, don’t ignore them. Legit companies don’t send such poorly crafted emails.
- Check out the links. Always hover your cursor over any links provided via emails to check out where those links are redirecting you to.
- Don’t share PII/financial info before you get hired. No legitimate company asks for SSN, tax-related data, physical address, bank account numbers or payment card details, etc. before hiring you. So, unless you have appeared on the interview in-person or via video call, don’t share any PII with a recruiter over email.
- Reach out to the contact directly through official channels. If you suspect any email that appears to be coming from someone you know, like a colleague, relative, or friend, contact them directly before taking any actions suggested in the email. Note: Use other contact information (other than what is listed in the suspected phishing email) to reach them!
- Provide training to improve your “human firewall.” Provide your employees with cyber awareness training.
- Use email signing certificates. Always use email signing certificates to protect your organization and its stakeholders from phishing emails. It allows the sender to assert a digital signature on all the outgoing emails and encrypts the email contents. It gives assurance to your recipients that the email is coming from you/an authentic employee of the company, and it is in the same condition at the time it was sent.
- Set up email security protocols. Establish the common email security protocols such as sender policy framework (SPF), domain keys identified mail (DKIM), and domain-based message authentication, reporting, and conformance (DMARC).
- Report phishing scams to authorities ASAP. If you become a victim of such phishing emails, file a detailed complaint with www.ic3.gov. And ftc.gov/complaint. You can also send your email phishing to complain to [email protected]
Wrapping Up
We hope when you hear the word “phishing email” in the future, you won’t get a picture of that “Nigerian prince” in your mind. Don’t take phishing emails lightly, always keep alertness, and train your employees to recognize such emails.
























 (29 votes, average: 4.28 out of 5)
(29 votes, average: 4.28 out of 5)





No comments