What Is SMS Spoofing & How Can You Prevent It?
Think spoofed text messages is a modern-day problem? They actually date back nearly a millennia…
SMS spoofing might be a 21st-century problem, but you’d be surprised to know that its roots are believed to go back by centuries. In 1271, Sultan Baybars, an Egyptian commander, successfully captured the formidable Krak des Chevaliers by handing the besieged knights a forged letter, supposedly from their commander, that instructed them to surrender. The knights surrendered in the end, and the letter turned out to be fake.
Interesting? Maybe, yes. But as exciting as it may sound, this capability is undoubtedly destructive in nature when used with malicious intentions. That brings me to “SMS spoofing,” the subject that brought you here.
SMS Spoofing: What Is It?
Thanks to the people who name these terms, we get a good idea of terms just by looking at it. If you think “SMS spoofing” is some kind of technique to defraud people using SMS, then you’re absolutely correct.
SMS spoofing is a technique that allows us to change the sender information on a text sent via the short message service (SMS) system. SMS text messages are used by cell phones, personal digital assistants, and similar devices and are typically just known as text messages.
When you send a spoof text, they replace the originating mobile number (sender ID) with alphanumeric text. In simpler words, SMS spoofing allows you to change the sender’s display number. As it allows you to change the originator details, it’s also regarded as “SMS originator spoofing.”
Here’s an interesting illustration of SMS spoofing:
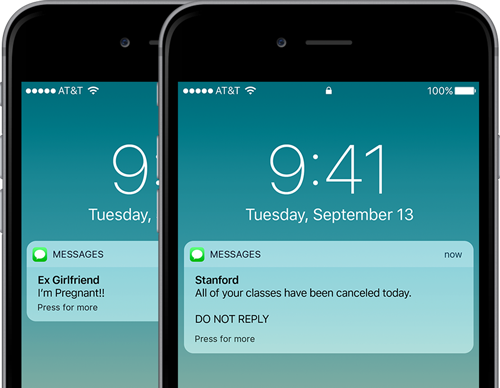
SMS Spoofing vs Smishing
Many people associate SMS spoofing with another technique called “smishing.” Some even believe them to be the same. While they both relate to phishing, however, both are quite different. Smishing, the short form of SMS phishing, is a security attack in which the user is tricked into downloading a Trojan horse, virus or other malware via a text message. And as you now know, SMS spoofing has to do with making a message look like it’s coming from another system or device.
They both are totally different, right? So, why do people associate them even though they’re entirely different? Well, that’s because they both are frequently used in combination to fool users. For example, a scammer may spoof the text message sender name, turning it into a name that seems like the name of a bank and include a phishing message that tricks users into clicking on a link. That’s how SMS spoofing and smishing are commonly used to fool users.
How Does SMS Spoofing Work?
As we saw, SMS spoofing allows you to send SMS impersonating another entity. This is done by changing the sender’s name, phone number, or both. Surprisingly, this is not at all hard to execute.
In BackTrack and some other versions of Kali Linux, there’s an SMS spoofing attack vendor tool in the social engineer tool kit. All it takes is this tool, and you can send a text message to someone using the identity of whatever phone number/sender name you want.
Apart from using SET in Kali Linux, an even more straightforward way to execute SMS spoofing is by using an online service. Yes, you read it correctly; there are “businesses” offering you SMS spoofing services on the internet (we’ll talk about their legality later on). These platforms are highly user-friendly; anyone with basic computer knowledge can send spoofed messages. All you need to do is pay some money (very cheap, btw), add the name that you want to display, and send the SMS to the people you want to send. Scary, isn’t it?
Ways SMS Spoofing Is Misused
Although it’s a technology, SMS spoofing has become a trick used by marketers, hackers, and fraudsters to mislead users with fake displayed sender information. It’s a medium that can be used and modified in many ways to achieve the intended result. Let’s see some of the most ways SMS spoofing is misused.
False Sender Company Name
We all have received an SMS that pretends to be from a well-known company, but in the end, it turns out to be a fake one. Well, that’s SMS spoofing for you. Many marketers and fraudsters send SMSes that pretend to be from a well-known company. For example, a fraudster could change the sender’s name to Vodafone and tell you that your contract is due for renewal. Not all people will believe this, but what about the ones whose contract is about to expire? If they see this SMS, they’re highly likely to respond to it. And that’s precisely what the scamsters want. Isn’t it?
Fake Money Transfers
One of the smartest ways that fraudsters use SMS spoofing is in offline shopping. In this trick, the fraudster visits a retail store (such as high-end electronic equipment, jewellery, branded merchandise, etc.) and purchases multiple items. For payment, the fraudster asks for the bank details of the store so that they can transfer the money online.
Now, if the fraudster knows about the store outlet’s phone number on which the bank sends SMSes for updates, they (the fraudster) can access an SMS spoofing website and use it to send a fraudulent SMS. The message is manipulated so it appears to come from the bank as it would contain the store’s account number (hashing all but the last four digits), the amount transferred, and the transaction date. This dupes the SMS recipient into believing that the “buyer” has made the payment and allows them to complete the purchase.
Personal Agenda
AsSMS spoofing gives you the power to create your identity (and impersonate others), it can be used to carry out a personal agenda against a person. This could be in the form of a prank, stalking, tricking, or abusing.
Extract Sensitive Information
What fraudsters and scamsters often do is send SMSes that prompt users into taking immediate actions. Not long ago, I received an SMS from a supposed e-wallet service saying that they will disable my account within 24 hours, and that I’ll lose all of my money if I don’t submit my documents. The message included a link that I was supposed to click on that would direct me to log in and provide information.
Unsurprisingly, the web page that the link directed looked almost the same as the website of the actual wallet provider, but it wasn’t. If I had logged in without looking at the URL, I’d have given my credentials to the fraudsters behind this scam, and they could’ve taken away all my money. Such scams are becoming more prevalent these days.
Legitimate Uses of SMS Spoofing
“Legitimate uses of SMS spoofing? Really?” – If this was your reaction after reading the header, then we can’t blame you. After all, it looks like a trick to defraud innocent people. Doesn’t it? It surely does, but there’s more to SMS spoofing than it meets the eye. SMS spoofing has its advantages, and it’s being used in many places. Let’s have a look at some of them.
- Bulk Messaging Services: Bulk SMS services are the ones who send out SMSes from a computer network. They must spoof their number so that people can identify them.
- Official Messages: When organizations such as banks, social media platforms, email providers, mobile network providers, etc. want to send official messages to their customers, they must do it in a way that users can identify them. So, they replace their number with their company name.
- Identity Protection: In some cases, protecting the sender’s identity is of paramount of importance. Whistle-blowers are the best example of this as they might be wanting to communicate in such a way that doesn’t reveal their identity.
How Users Can Protect Themselves Against SMS Spoofing
When it comes to protecting digital security, there’s a bit of education as far as emails and websites are concerned. However, SMS security is one such area that hasn’t received the attention it deserves. That’s why, as a user, you must learn how you can protect yourself from being scammed. Here are some tips that will help you:
- You should avoid clicking on links you receive via SMS as much as possible. If the SMS is asking you to take urgent action, then you should visit the website directly and not click on the SMS link.
- Don’t get tempted by “too good to be true” offers or news such as winning a lottery or heavenly discounts. While that free Chipotle burrito offer may be real, it also may be a scam. Exercise caution.
- Don’t click on the URLs mentioned in the “password reset” SMS messages.
- If you receive a fund transfer update through SMS, you should always insist on checking your bank/wallet balance by logging in to your banking website or mobile app directly. Again, don’t automatically click on a link you receive via SMS!
- Beware of SMSes about verification codes, especially if you didn’t request a password reset or sign up to a service that uses two-factor authentication.
- Share your phone number only in urgent cases.
- Banks, service providers, and telecommunication companies don’t ever ask you for your personal details through SMS. So, don’t ever give your details through SMS!
- Contact law enforcement and your network provider if you receive a spoof text message.
How Organizations Can Protect Their Brands Against SMS Spoofing
Not only do customers need to be aware of spoof text messages, but organizations also need to be wary of SMS spoofing as well for two reasons. One, these scams are quite easy to fall for. If scammed, you could incur a hefty financial loss, and that’s not something you want, right? And the second reason is that if your organization’s name and brand are used by cybercriminals in SMS spoofing attacks, it can have a major impact on your reputation.
Here are some of the steps you could take to stay a step ahead of the fraudsters:
- If you receive a fund transfer update through SMS, you should always insist on checking your bank/wallet balance by logging in.
- Rely on conventional payment methods (i.e., cash, debit, or credit card).
- Contact law enforcement and your network provider if you receive a spoof SMS.
- If someone uses your organization’s name or information in SMS spoofing scams, report it to the Federal Communications Commission (FCC) and the police.
- Avoid using your personal phone number for SMS updates and keep a separate phone number for the same. And of course, don’t share this number with the outside world.
- Raise awareness about SMS spoofing among your customers so that they don’t fall for spoofing attacks that target your company.
Last Word
One of my best friends was so afraid of doing anything online that she’d wait for half an hour in a bank to do a transaction that could be easily completed online within minutes. Recently, she’s started to do some stuff online — but that, too, with the eye of a cat that wants to protect itself from the dogs.
Yes, my friend comes across as a bit of a freak and I like to make fun of her for it. However, there’s something that we all could learn from her. If we practice even a quarter of her awareness, we could easily stay away from SMS spoofing and spoofed text messages. It’s all about the eyes, my friend!

























 (17 votes, average: 3.94 out of 5)
(17 votes, average: 3.94 out of 5)






No comments