A History of Email and SMPT: The Evolution of Email Security
A 50-year journey back into email and SMTP history to understand how email security evolved into the email as we now know it
As someone who loves to research and learn, I thought it would be great to explore the history of email security to better understand the security technologies that we take for granted each day.
If we’re to look back at the history of email in general, the protocol we continue to use today is as good a place as any to start with. Simple mail transfer protocol (SMTP) was first given to us, at least in a standardized format, by Jonathan B. Postel in August 1982. However, computer-based messaging had become possible long before that, and SMTP had several precursors like Telex and AUTODIN.
Although security is a primary concern nowadays, SMTP was designed in a vastly different environment — during the time of ARPANET (i.e., the precursor to the modern internet), which was a closed network of trusted users mainly comprising of researchers and government officials. In those days of open relays, secure SMTP ports and the concept of authentication weren’t even on the radar; instead, the focus was on providing reliable email delivery.
Now, nearly 40 years later, the internet is no longer just a closed network of trusted users; rather, it’s an interconnected network of global users who may or may not be credible. Not only that, but our exchanges have also transitioned from simple text-based communication to significantly more complex forms.
In the section below, we take a look at the email history timeline in general with an emphasis on SMTP history.
A Timeline on How Email Evolved with SMTP in All of Its Glory
The history of email and email security actually dates back nearly 50 years. Considering the breadth and vast history, I thought it best to break this topic down by decade to help keep things organized.
SMTP Email History Timeline — The 1970s
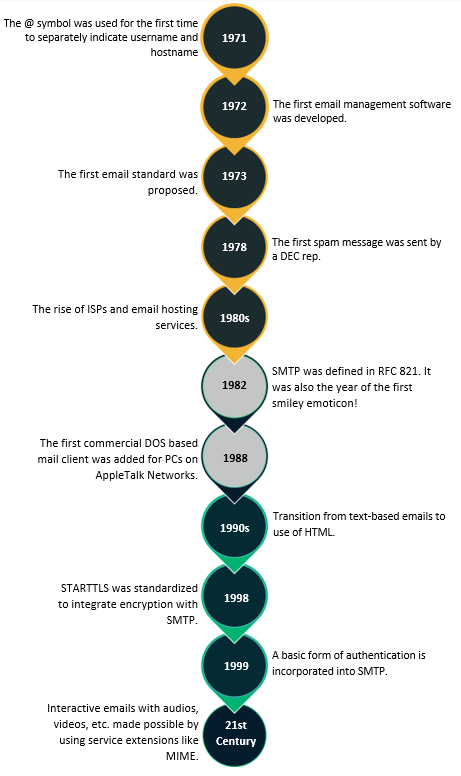
No trip down memory lane is worth its while without the mention of the guy who started it all, which, in our case, happens to be Raymond Samuel Tomlinson. SNDMSG was used earlier to send electronic mails but only on single multi-user, time-sharing computer.
In 1971, Tomlinson extended this functionality and sent the first email as a test to validate whether messages could be sent to users on other computers on the ARPANET system. He first used the @ symbol to divide up the username and the hostname, a construct we still use to this day while sending out emails! This mode of communication proved a huge success, and ideas began to crop up around how one might be able to send an electronic mail to a user outside one’s internal network.
In 1972, Larry Roberts, the so-called founder of the internet (because he built ARPANET), wrote the first-ever mail management software, “RD,” which could display a menu of messages that users could sort, file, or delete. RD gave rise to many mail managers, MSG, developed by John Vittal, being one of the most prominent ones that included features like mail forwarding.
1973 saw the first email standards being proposed at DARPA with features like mail forwarding. 1978 was the year when possibly the first spam message was sent out by a marketing representative from Digital Equipment Corp. (DEC) and was met with a massive outcry from ARPANET users.
SMTP Email History Timeline — The 1980s
The 1980s saw ISPs and email hosting services enter the picture, which eventually led to an era of global connectivity. In 1984, FidoNet (worldwide network of bulletin board systems) was released, adding to the networks from the 70s such as PLATO IV, Unix mail, etc.
It was also during the early 1980s that the first draft for SMTP got defined with RFC 821 getting published in 1982. It was also the year that Professor Scott Fahlman gave us the first smiley face emoticon! 😊
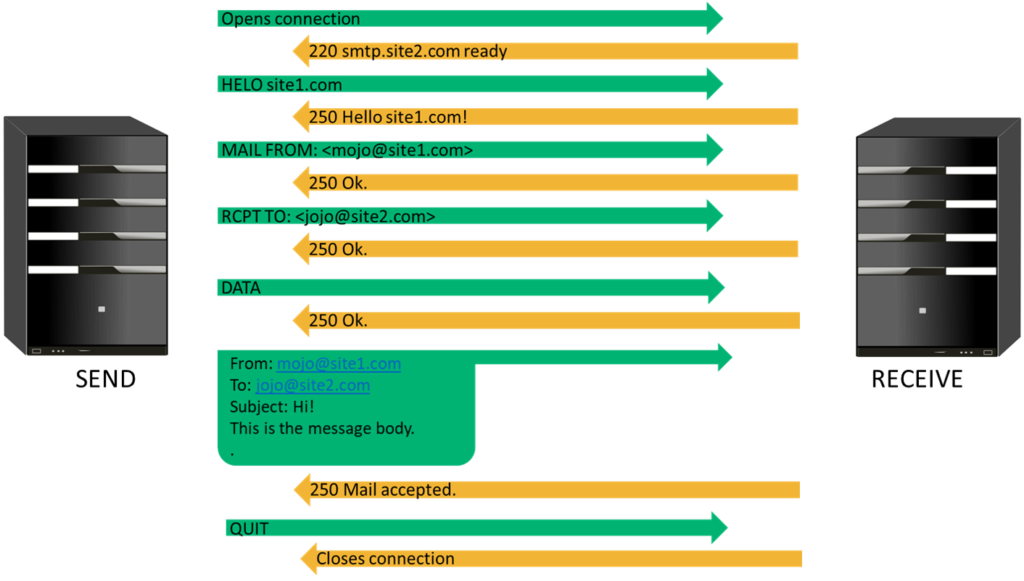
One important thing to note is that the way SMTP was designed in 1982 — the “From” field (purported responsible address, or PRA identity) in the message body (as shown in Figure 2) didn’t need to match the “Mail From” address, and this paved the way for a whole bunch of issues. Today, of course, we have SMTP security controls like authentication checks using SPF, DKIM, etc. (more on this later), which helps us to verify the legitimacy of the email received.
In 1988, the first commercial MS-DOS based mail client was added for personal computers on AppleTalk Networks. Companies like CompuServe, Sprint (in the U.S.), and Pipex (in the U.K.) became the first to offer internet connectivity through dial-up connections.
SMTP Email History Timeline — The 1990s
The 1990s saw a shift from text-based emails to the use of HTML, and providers like Yahoo! Mail, AOL, and Hotmail took the internet community by storm.
STARTTLS was standardized around late 1998 in an attempt to incorporate some form of encryption into the SMTP protocol to prevent intruders from reading messages. IONOS describes the STARTTLS command as something that’s “mainly used as a protocol extension for communication by email, based on the protocols SMTP, IMAP and POP.” What it does is extend the transport layer security (TLS) protocol so that any information is transmitted via the encrypted protocol.
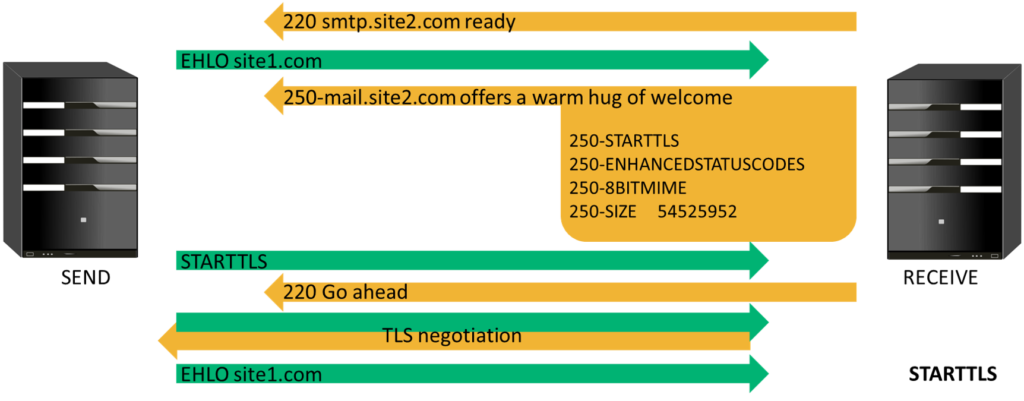
Even at this point, there was still no authentication, and it was all about open communication and open relays. While that facilitated reliable mail transfer, it also enabled any unscrupulous user on the network to abuse the computing resources of these open relay servers to send out large volumes of unsolicited spam messages.
Subsequently, around March 1999, a basic form of authentication was incorporated as an option into the SMTP protocol. This made it so that, upon receiving the extended hello (EHLO) message from the sender, the receiver responded with an additional 250-AUTH PLAIN LOGIN option. SMTP continued to build on its previous features and assimilated security improvements as time progressed.
SMTP Email Security as We Know It Today
The 21st century gave us interactive and responsive emails that enable videos, animation, etc. to be shared via email by using service extensions (multipurpose internet mail extension allows the exchange of other formats) and comes with features ranging from calendars and mail recall to screen share and conferencing. It also gave us “MTA Authorization Records In DNS” (MARID), a mechanism for anti-spoofing email authentication. The MARID Internet Engineering Task Force (IETF) working group was formed in 2004 and disbanded within less than a year because of intellectual property battles, disagreements, etc. around how best to refine the SMTP standard.
Around the same time, SMTP also started using message headers like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), etc. to prevent spam and email-based security attacks. Why?
Because, according to RFC 5321, SMTP security on its own isn’t enough:
SMTP mail is inherently insecure in that it is feasible for even fairly casual users to negotiate directly with receiving and relaying SMTP servers and create messages that will trick a naive recipient into believing that they came from somewhere else. Constructing such a message so that the “spoofed” behavior cannot be detected by an expert is somewhat more difficult, but not sufficiently so as to be a deterrent to someone who is determined and knowledgeable. Consequently, as knowledge of Internet mail increases, so does the knowledge that SMTP mail inherently cannot be authenticated, or integrity checks provided, at the transport level. Real mail security lies only in end-to-end methods involving the message bodies, such as those that use digital signatures (see RFC 1847 [43] and, e.g., Pretty Good Privacy (PGP) in RFC 4880 [44] or Secure/Multipurpose Internet Mail Extensions (S/MIME) in RFC 3851 [45]).”
SPF, DKIM, DMARC, and S/MIME certificates are some of the controls used today to prove to ISPs and mail servers that email senders are, indeed, authorized parties and are not attempting to impersonate legitimate users. SPF maps IP addresses to domain names and DKIM asserts authenticity and assures that the content of an email message has not been modified. Domain-based Message Authentication, Reporting and Conformance (DMARC) builds on SPF and DKIM and determines how to respond to potentially spoofed emails.
While the other three are DNS TXT records, Secure/Multipurpose Internet Mail Extension (S/MIME) is a protocol standard defined by IETF that is focused on email security. S/MIME certificates are used to sign or authenticate and encrypt our email communication both in storage and in transit.
Wrapping Up the History of Email Timeline
Looking at SMTP history — from how the protocol was developed originally to how encryption and authentication are being incorporated in the present day — one needs to acknowledge that there are some inherent weaknesses can be improved upon but can’t be omitted completely. This is why it’s essential to have a secure email strategy to help guide your organization’s efforts to increase email security through a series of tools and authentication methods.
























 (22 votes, average: 4.27 out of 5)
(22 votes, average: 4.27 out of 5)





No comments