ECDSA vs RSA: Everything You Need to Know
ECDSA or RSA? Which one is better? — Here’s what you should know to make an informed decision
If you’re into SSL certificates or cryptocurrencies, you’d likely come across the much-discussed topic of “ECDSA vs RSA” (or RSA vs ECC). Both what do both of these terms really mean and why do they matter?
ECDSA and RSA are two of the world’s most widely adopted asymmetric algorithms. However, both these algorithms are significantly different when it comes to the way they function and how their keys are generated. In this article, we’ll unravel both of these encryption algorithms to help you understand what they are, how they work, and to explore their unique advantages (and disadvantages). Let’s get started!
RSA Algorithm: What It Is and How It Works
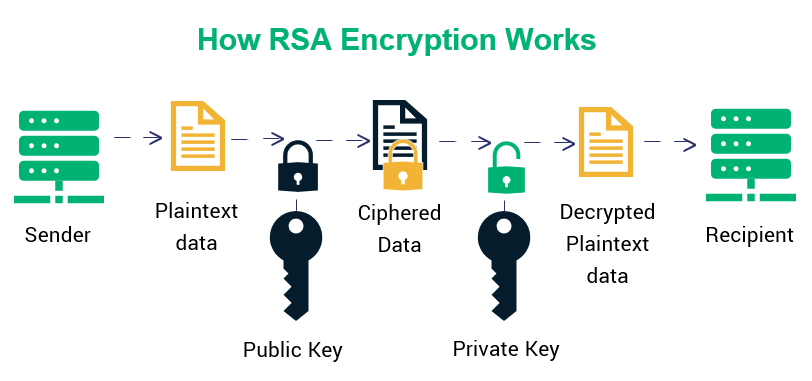
When it comes to popularity, there’s no match for the RSA (Rivest Shamir Adleman) asymmetric encryption algorithm. This algorithm is used widely when it comes to SSL/TLS certificates, cryptocurrencies, email encryption, and a variety of other applications.
Since it was invented by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977, RSA has been the gold standard when it comes to asymmetric encryption algorithms. RSA uses the prime factorization method for one-way encryption of a message. In this method, two titanic-sized random prime numbers are taken, and they’re multiplied to create another gigantic number.
The multiplication of these two numbers is easy, but determining the original prime numbers from this multiplied number is virtually an impossible task — at least for modern supercomputers. This process is called the “prime factorization” method. Figuring out the two prime numbers in the RSA algorithm is an awfully challenging task — it took a group of researchers more than 1,500 years of computing time (distributed across hundreds of computers) to be able to do so.
ECDSA vs RSA: What Makes RSA a Good Choice
Considering that this one algorithm has been the leading choice by industry experts for almost three decades, you’ve got to admire its reliability. RSA was first standardized in 1994, and to date, it’s the most widely used algorithm. The reason why this longevity is quite essential to note is that it shows that RSA has stood the test of time. It’s an extremely well-studied and audited algorithm as compared to modern algorithms such as ECDSA.
Another major thing that sets RSA apart from other algorithms is the simplicity it offers. It’s based on a simple mathematical approach and it’s easy to implement in the public key infrastructure (PKI). This has been one of the key reasons why RSA remains the most popular encryption algorithm method.
![]() ECDSA Algorithm: What It Is and How It Works
ECDSA Algorithm: What It Is and How It Works
ECDSA (elliptic curve digital signature algorithm), or ECC (elliptic curve cryptography) as it’s sometimes known, is the successor of the digital signature algorithm (DSA). ECDSA was born when two mathematicians named Neal Koblitz and Victor S. Miller proposed the use of elliptical curves in cryptography. However, it took almost two decades for the ECDSA algorithm to become standardized.
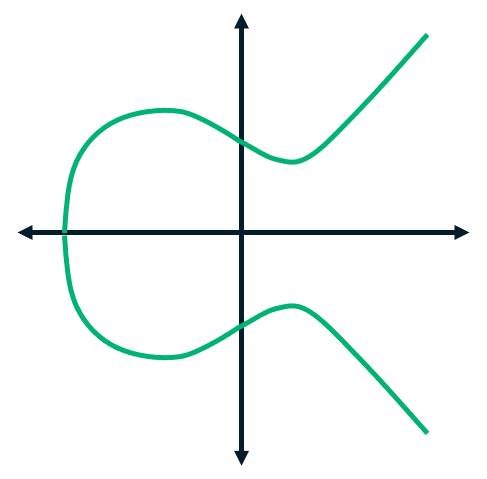
ECDSA is an asymmetric cryptography algorithm that’s constructed around elliptical curves and an underlying function that’s known as a “trapdoor function.” An elliptic curve represents the set of points that satisfy a mathematical equation (y2 = x3 + ax + b). The elliptical curve looks like this:
ECDSA vs RSA: What Makes ECC a Good Choice
As all asymmetric algorithms go, ECDSA works in a way that’s easy to compute in one direction but mightily difficult to revert. In the case of ECDSA, a number on the curve is multiplied by another number and, therefore, produces a point on the curve. Figuring out the new point is challenging, even when you know the original point.
Compared to RSA, ECDSA has been found to be more secure against current methods of cracking thanks to its complexity. ECDSA provides the same level of security as RSA but it does so while using much shorter key lengths. Therefore, for longer keys, ECDSA will take considerably more time to crack through brute-forcing attacks.
Another great advantage that ECDSA offers over RSA is the advantage of performance and scalability. As ECC gives optimal security with shorter key lengths, it requires a lesser load for network and computing power. This proves to be great for devices that have limited storage and processing capacities. In SSL/TLS certificates, the ECC algorithm reduces the time taken to perform SSL/TLS handshakes and can help you load your website faster.
The catch, though, is that not all CAs support ECC in their control panels and hardware security modules (although the number of CAs that do is growing).
ECDSA vs RSA: The Difference of Key Lengths
As we discussed, ECC requires much shorter key lengths to give the same level of security provided by long keys of RSA. Here’s what the comparison of ECDSA vs RSA looks like:
| Security (In Bits) | RSA Key Length Required (In Bits) | ECC Key Length Required (In Bits) |
| 80 | 1024 | 160-223 |
| 112 | 2048 | 224-255 |
| 128 | 3072 | 256-383 |
| 192 | 7680 | 384-511 |
| 256 | 15360 | 512+ |
ECC vs RSA: The Quantum Computing Threat
The main feature that makes an encryption algorithm secure is irreversibility. Therefore, to crack any such algorithm, you must execute brute-force attacks — trial and error, in simple words. However, thanks to the encryption key lengths, the possible combinations that you must try are in numbers that we can’t even begin to accurately conceptualize.
However, all of it will change by the possible (and probable) introduction of quantum computers in the future. The National Institute of Standards and Technology (NIST) predicts that once quantum computing becomes mainstream, modern public key cryptography will fail. Why? Because quantum computers are mightily powerful — significantly more power than today’s supercomputers — because they operate on qubits rather than bits. What this means is that they can try multiple combinations at any given point of time and, therefore, their computing time is significantly shorter. These quantum computers are likely to make today’s encryption systems obsolete — including RSA and ECDSA.
According to various studies, RSA and ECDSA are both theoretically vulnerable to an algorithm known as Shor’s algorithm. This algorithm, when applied with quantum computer, is likely to crack both RSA and ECDSA. According to research conducted by Microsoft, it’s been found that ECDSA is easier to solve compared to the RSA cryptosystem. However, there’s no need to worry about this right now as practical quantum computers are still in their infancy.
RSA vs. ECDSA: Summary
Till now I hope I’ve been able to clear up any confusion you may have regarding the topic of ECDSA vs RSA. Here’s a summary of all the differences that makes it easy for you to understand:
| RSA | ECDSA |
| One of the earliest methods of public-key cryptography, standardized in 1995. | Comparatively new public-key cryptography method compared to RSA, standardized in 2005. |
| Today, it’s the most widely used asymmetric encryption algorithm. | Compared to RSA, ECDSA is a less adopted encryption algorithm. |
| It works on the principle of the Prime Factorization method. | It works on the mathematical representation of Elliptical Curves. |
| RSA is a simple asymmetric encryption algorithm, thanks to the prime factorization method. | The complexity of elliptical curves makes ECDSA a more complex method compared to RSA. |
| RSA is a simpler method to implement than ECDSA. | Implementing ECDSA is more complicated than RSA. |
| RSA requires longer keys to provide a safe level of encryption protection. | Compared to RSA, ECDSA requires much shorter keys to provide the same level of security |
| As it requires longer keys, RSA slows down the performance. | Thanks to its shorter key lengths, ECDSA offers much better performance compared to RSA. |
Final Word: ECDSA vs RSA
No matter their unique advantages and disadvantages, RSA and ECDSA remain two of the most popular asymmetric encryption algorithms. Both of these algorithms provide the level of protection that today’s hacker can’t even think to touch. However, both are quite different in many aspects. To rehash what we just learned, these are the points on which they differ:
- Performance
- Key length required for secure encryption
- Working principle
- Scalability
- Complexity
The key to the success and strength of these algorithms lies in their correct implementation. No encryption algorithm can provide optimal security if it’s improperly implemented and follow industry standards.
As far as current standards of security are concerned, there’s not much of a point of the “ECDSA vs. RSA” debate as you can choose either of them as they both are entirely secure. I’d like to reiterate the face that the ECC isn’t as widely supported as RSA. Having said that, if you have the option to select, ECC is a better option.














 (61 votes, average: 4.07 out of 5)
(61 votes, average: 4.07 out of 5)





2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security