What to Do If Your Website Is Hacked
As recently as 2018, 67% of small and midsize businesses reported they suffered a cyber-attack and data breach. If you’ve discovered that your site is one of them, here’s what…

TLS is a secure protocol that protects sensitive information exchanges like passwords and credit card numbers against theft from cyber attacks (which are up 8% year-over-year for organizations). Here’s what…

SpyCloud recovered 721.5 million stolen credentials from the darknet in 2022. Don’t be the next victim. Go passwordless! Protect one of attackers’ favorite network entry points. Discover how to log…

We’ll walk you through how to add your digital ID to Outlook in the form of an Outlook email signing certificate so you can send digitally signed messages Knowing how…
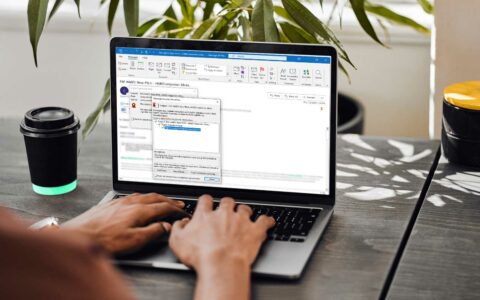
Digital signatures add your verified digital identity to outgoing emails so recipients will know they’re legitimate. Here’s a quick rundown of what Outlook digital certificates are, what they do, and…

Perfect forward secrecy in TLS 1.3 is what helps to prevent the encrypted session data you’ve sent or received from being decrypted should the receiving server’s private key become compromised…
As recently as 2018, 67% of small and midsize businesses reported they suffered a cyber-attack and data breach. If you’ve discovered that your site is one of them, here’s what…
Explore how to recognize a malvertisement and protect yourself from getting hacked Malvertising = malicious advertising. Basically, it’s a way for cybercriminals to spread malware (malicious software) through ad displays on websites and apps. Malware means…
Verizon’s 2020 DBIR reports that 80% of breaches within hacking involve brute force or the use of lost or stolen credentials. Learn how passwordless authentication can help you avoid such…
We’ll take an in-depth look at the difference between vulnerabilities and exploits, why they matter, and how you can use that knowledge to keep your website safe Ever wonder how…
X.509 certificates are the bricks and pavers that help to create the public key infrastructure that internet security is built upon… If you’re looking for the answer to the question…
Make yours a secure WordPress site with these 10 proven, easy-to-implement tips and keep the hackers away WordPress is a real blessing for bloggers, freelancers, and startup business owners. You don’t need to pay…
Cloud-based attacks rose 630% between January and April 2020! Let’s explore 20 of the cyber attacks we’ve seen (so far) in 2020… As if the world isn’t facing enough difficulties…
Juniper Research estimates that there will be 83 billion IoT devices in existence by 2024, — a lot of potential zombies for botnet armies. The term “botnet” refers to a…
Malware analysis is a practical process for identifying and assessing threats — here’s a quick explanation of the malware analysis process and how it works What is malware analysis? It’s…
“There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked” — John Chambers, former CEO and executive chairman at…
2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security