Spam vs Phishing: What’s the Difference Between Them?
56.51% of all emails are spam (Kaspersky), and 65% of U.S. organizations faced successful phishing attacks in 2019 (Proofpoint)! But are they different? Let’s explore spam vs phishing in laymen’s terms!
Spam vs phishing — although people use the words “spam” and “phishing” interchangeably, the terms have related but different meanings. They’re both terms that describe pesky, unsolicited communications that try to manipulate targets into doing something. This could be providing some type of information about yourself — personal info, login credentials, etc. — or engaging with a malicious link or file.
But what is the meaning of spam and what does phishing mean? In this article, we’ll talk about spam vs phishing in detail. We’ll also explore the difference between spam and phishing in terms of email, phone calls, and text messages.
Spam vs Phishing: Meaning
Spam: Any unsolicited or unwanted commercial message is generally considered spam. The purpose of a spam is to inundate as many people as possible to advertise the products and services. Spam messages are not harmful in nature. They’re just unwanted and occupy unnecessary space in your inbox. Spam is all about the numbers. When you hit enough people with your spam messages, even minimal success rates pay off in the long run.
Phishing: Phishing is a way for scammers and cybercriminals to impersonate a legal entity or to use other methods to defraud their targets. The goal of phishing is to get users to share confidential information and credentials, click on malicious links, download malware, or engage with virus-loaded attachments.
Spam Vs. Phishing: Spam messages are unsolicited commercial messages for marketing purposes while phishing is done to defraud people and make them victims of cybercrimes. Hence, when we talk about spam vs phishing, the difference lies between the sender’s intentions and the messages’ contents. Spam and phishing are typically done via these three popular mediums.
- Emails
- Phone calls
- SMS
Let’s explore spam vs. phishing in the context of each of them.
Spam vs Phishing: Emails
Emails are the most popular spamming and phishing techniques. This table will help you understand the difference between spam and phishing quickly. After that, we will cover the differences in detail.
| Spam | Phishing | |
| Purpose | To promote and market products and services | To defraud recipients |
| Nature | Unwanted commercial emails, typically benign in nature. | Misleading messages that appear to come from legit entities but are designed to be malicious in nature. |
| Contain | Product/service advertisements, coupon codes, deals, discounts, inquiry, or survey forms | Malware-loaded attachments, infected links, links that redirect to spammy websites, deceptive messages that make recipients share their PII/financial information |
| Legislation | The U.S. Non-Solicited Pornography and Marketing Act of 2003 For other countries: Anti-Spam laws | The U.S. federal criminal law, Various state laws |
Now, let’s have an in-depth explanation of the differences.
What Is Spam in the Context of Email?
Any electronic messages sent out for the commercial advertisement or promotion of the product, service, or website content are considered spam. Email spamming is a legal activity under the Controlling the Assault of Non-Solicited Pornography And Marketing Act of 2003, which is known as the CAN-SPAM act.
These are some key CAN-SPAM rules that the sender must comply with:
- Email must have an active and visible unsubscribe link or button. The sender gets 10 days to act on the unfollow request and to cease emailing the recipient.
- Sender’s email address must be accurate. The “from” line not misleading and the subject of the message must be relevant to the body of the message.
- Sender’s physical address must be mentioned. A physical address (or P.O. Box number) of the sender (company, individual sender, advertiser, or the third-party marketing agency) must be present in the email.
- Recipients must be warned if the email has adult content. If the content is adult in nature, it must be labeled as “SEXUALLY EXPLICIT.”
- Sender should send email from multiple email addresses. The sender should not send spam messages to the same recipient from different email addresses.
- Emails must not contain malware: The spam messages must not contain malware (viruses, worms, trojan horses, etc.) or redirect users to malicious websites.
When companies send emails to the current customers or to the business leads (people who have inquired about products/services) for follow-up, feedback, suggestions, or any other type of communication, such messages are also not considered to be spam. These messages are classified as relationship messages under CAN-SPAM. Even political and religious emails are also except from the SMAP’s definition in CAN-SPAM.
Most of the email clients automatically detect spam emails and dump them in the spam/junk folder. All the attachments and images are also blocked in such an email. But if you’re still getting unwanted spam emails in your inbox, you can unsubscribe from them. (Just be careful to check the unsubscribe link first to ensure it’s not a phishing or malicious link.) Also, you can right-click on the email in your inbox to move it to the spam folder. You can also block the sender.
Here’s an example of a typical spam email:
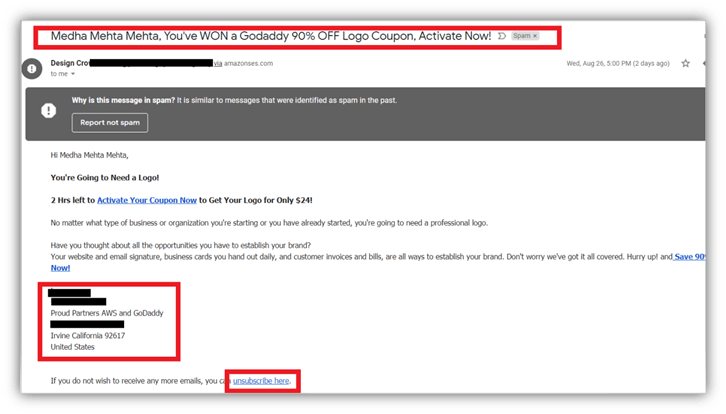
This is a spam email I got from a logo designing website. The content in the subject line matches the content of the email. You can also see the email has an unsubscribed tab and the physical address of the company. That means it is a spam email that is following all the SPAM-CAN’s guidelines.
What Is Phishing in the Context of Email?
Scammers send phishing emails posing as a company or person that the recipients trust. These emails are deceptive in nature. Phishing emails are crafted in a way that they look like coming from your bank, ecommerce site, university, government, employer, relatives, or colleagues. 96% of phishing attacks occur via email, Verizon’s 2020 Data Breach Investigations Report (DBIR) shows.
These emails might contain malware-laden attachments, malicious links, or redirects to spammy websites. Sometimes the attackers try to trigger an emotional response from the recipients and indulge in sharing their confidential information such as:
- Payment card numbers,
- Phone numbers,
- Physical address,
- Social security number (SSN),
- Tax-related information, and
- Health information
The general motives behind phishing emails include:
- Financial fraud,
- Identity theft,
- Login credentials theft,
- Spreading malware (worms, viruses, trojans, rootkits, adware, etc.), and
- Redirecting recipients to malicious websites.
Below is an example of a typical phishing email. The email looks like coming from PayPal, but if you check the sender’s email address carefully, you would see that it is coming from a scam artist, and the benign-looking PDF attachment might contain dangerous malware.
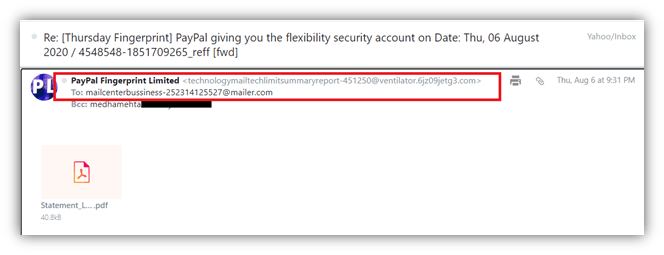
Many U.S. states have different laws for phishing. There is no federal law that directly criminalizes phishing, but the federal criminal laws apply to financial fraud and identity theft crimes done via phishing.
If you have become the victim of a phishing email, you can register your complaint to the www.ic3.gov, ftc.gov/complaint or [email protected].
Spam vs Phishing: Voice Messages and Phone Calls
Perpetrators use phone calls to spam and phish targets.
Spam Calls
If you receive an unsolicited phone call for marketing purposes, especially from a company you’ve never dealt with before, it can be categorized as a spam call. The definition of marketing calls and spam calls can be blurred.
For example, if you suddenly get a phone call to apply for a credit card from a card company you never dealt with before, it is considered to be a spam call. But if someone calls you to sell the new card or insurance policies from the bank you already have an account with, it’s considered a mere marketing call to sell additional products. In the U.S., the Telephone Consumer Protection Act (TCPA) and the Federal Communications Commission (FCC) place restrictions on spam calls and telemarketing messages.
Voice Phishing (Vishing)
When the perpetrators make phone calls impersonating someone else with the purpose of defrauding you, it is known as voice phishing or vishing. For example, a cheater calls you posing as a bank manager and asking you to provide the last four digits of your social security number and some other personal details to send you a new credit card.
Sometimes, attackers use a leaked database or utilize their social engineering skills to do a little research about the potential victims before calling. For example, they call college students impersonating as a bank employee who handles student loans or a representative from the state/federal student aid department that wants more information regarding their scholarship application. In short, instead of cold calling random numbers, scammers make a phone call understanding their target audience so that they sound legit to the potential victims.
Spam vs Phishing: Text Messaging
There are websites and tools available these days that can send bulk text messages at unbelievably low costs. That’s why spammers and phishing scammers love to send their messages via text messages, too! You’re able to reach users on their cell phones wherever they are.
Spam Text Messages
When companies send unsolicited bulk text messages for commercial, non-malicious purposes, they’re known as spam text messages or spam SMS messages. These messages may contain product information, details of special deals/discounts, offers, schemes, coupon codes, etc. They might also have links to the product/service website.
Some spam SMS texts are sent as a survey to gain more information about potential customers. The purpose of such text messages can be selling a product or service, branding, collecting more information (such as demographics, buying habits, purchasing power, like/preferences, etc.) of the recipients. Text spamming is also covered under The Telephone Consumer Protection Act (TCPA).
SMS Phishing (Smishing)
Here, scammers send text messages while impersonating legitimate organizations. The nature and purpose of such phishing SMS messages are the same as phishing emails — i.e., to defraud the recipients. The attackers try to trick or manipulate you into:
- Sharing your personal or financial information,
- Completing financial transactions,
- Downloading malware-laden attachments, or
- Clicking on the links in the SMS texts that lead you to malicious websites.
Wrapping Up on Spam vs Phishing
The topic of spam vs phishing, or more specifically the difference between spam and phishing, can be confusing. But by now, we can safely assume that you know spam is the annoying yet more benign type of message, whereas phishing facilitates cybercrime. But the fine line between phishing and spam gets blurred when the spammer violates some of the CAN-SPAM’s (or your country’s laws related to SPAM) guidelines. For example, the email’s content or sender’s email address is deceptive in nature, or the email/text messages contain malware (or links to malicious websites).
Spamming can sometimes be so annoying that you feel like changing your phone number or email address! On the other hand, phishing can lead you into becoming a cybercrime victim. So, educate yourself and your employees further about phishing scams and how to recognize them successfully.














 (24 votes, average: 4.67 out of 5)
(24 votes, average: 4.67 out of 5)





2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security