How to Tell if Someone Hacked Your Router & How to Fix It
Make sure you know what to do if your network is hacked via your router and the steps you can take to resolve the issue! Wondering how to tell if…

TLS is a secure protocol that protects sensitive information exchanges like passwords and credit card numbers against theft from cyber attacks (which are up 8% year-over-year for organizations). Here’s what…

SpyCloud recovered 721.5 million stolen credentials from the darknet in 2022. Don’t be the next victim. Go passwordless! Protect one of attackers’ favorite network entry points. Discover how to log…

We’ll walk you through how to add your digital ID to Outlook in the form of an Outlook email signing certificate so you can send digitally signed messages Knowing how…
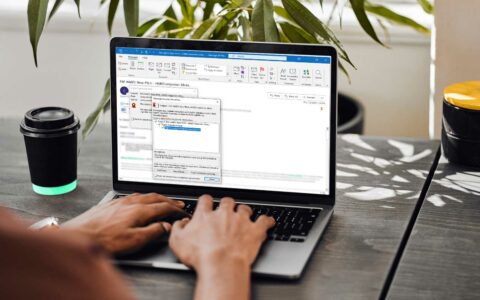
Digital signatures add your verified digital identity to outgoing emails so recipients will know they’re legitimate. Here’s a quick rundown of what Outlook digital certificates are, what they do, and…

Perfect forward secrecy in TLS 1.3 is what helps to prevent the encrypted session data you’ve sent or received from being decrypted should the receiving server’s private key become compromised…
Make sure you know what to do if your network is hacked via your router and the steps you can take to resolve the issue! Wondering how to tell if…
FireEye reports that one in every 101 emails is malicious! But how do you know if an email is fake or legit? Let’s find out from these 7 tips! Ever…
Your ultimate guide to understanding asymmetric encryption — what it does, how it works, and its strengths and disadvantages What is asymmetric encryption? How does asymmetric encryption work? These two…
DNS records tell a lot about you and your online browsing behaviors — explore what a DNS leak is and how you can detect & prevent DNS leaks A lot of people turn to…
In honor of National Cyber Security Awareness Month, here are 10 essential cybersecurity tips for startups to protect your website, devices & data We all know cybersecurity for startups is…
What is a malware attack? And how to protect your devices from it? Malware, a portmanteau of “malicious software,” is any malicious code, scripts, or software that’s developed to gain unauthorized access to your data, network, devices, or other IT systems. Any cyberattack deployed using malicious…
Coinmarketcap.com reports that the cryptocurrency market’s worth has surpassed $393 billion. Cryptojacking is one of the ways that cybercriminals try to get a piece of the action… What is cryptojacking…
10 warning signs to help you know if you’ve been hacked and how to handle the issue afterwards Unfortunately, the answer to “have I been hacked?” or “was I hacked?”…
Although crypto mining has only been around since Bitcoin was first mined in 2009, it’s made quite a splash with miners, investors and cybercriminals alike. Here’s what to know about…
Statista reports more than half of the global population is connected to the World Wide Web. But how did the web go from being a proposal to a network that…
2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security