What Is a DNS Leak? How to Find & Fix DNS Leaks
DNS records tell a lot about you and your online browsing behaviors — explore what a DNS leak is and how you can detect & prevent DNS leaks
A lot of people turn to Google to answer the question, “what is DNS leak?” And for many people around the world, a DNS leak may not seem like a big deal. (“If I’m not doing anything wrong, I’ve got nothing to hide, right? Wrong.) But for some individuals, depending on their country of residence and its laws, a leaky DNS is a big concern.
When you type a website’s domain name in the address bar, the browser opens up that website within seconds. But there are a lot of processes that take place in the background which you are not aware of. And if any of those procedures has a security vulnerability known as a DNS leak, it means that third parties can eavesdrop on your entire browsing behavior.
In this article, we will answer the following questions:
- What is a DNS and how does it work?
- What is a DNS leak and what causes it?
- How to perform a DNS leak test to tell if your DNS is leaking
- How do you prevent a DNS leak?
- What risks are associated with a leaky DNS?
What Is a DNS?
Since this article’s focus isn’t about explaining what a domain name system (DNS) is (but it’s still necessary to understand the topic), we’ll keep this brief. If you already know the basics, feel free to skip this part.
Everything that is connected to the internet (such as your computer, smartphone, and organization’s web servers) has a digital identity that’s written in either a numeric or alphanumeric format. This is known as an internet protocol (IP) address. IP addresses come in different formats — public, private, static, and dynamic — and are written in different ways based on their size.
- A 32-bit IPv4 address is numeric and consists of four numeric segments that are separated by periods. So, an IPv4 address for google.com looks like this: 64.233.166.113.
- A 128-bit IPv6 address is alphanumeric, which means it’s much larger. This type of IP address consists of eight 16-bit hexadecimal blocks, all of which are separated by colons. An IPv6 address for google.com looks like this: 2607:f8b0:4002:c08::8a.
So, if you want to connect to a website, you need to provide that website’s IP address to the web browser. But as you can see, that’s a lot of random numbers or letters to try to remember.
It’s inconvenient and almost impossible for the average human brain to remember IP addresses for thousands of websites. That’s where the domain name system (DNS) technology comes in handy. DNS essentially translates the website’s domain address into the IP address for you.
The domain name system (sometimes called “domain name service”) is a series of servers and computers that connect domain addresses to their corresponding IP addresses (either IPv4 or IPv6). They do this through a process known as a DNS lookup. So, instead of typing in a series of seemingly random numbers every time you want to shop on Amazon, you can instead type in “amazon.com.” This simple approach makes things a lot easier to remember.
How Does DNS Work?
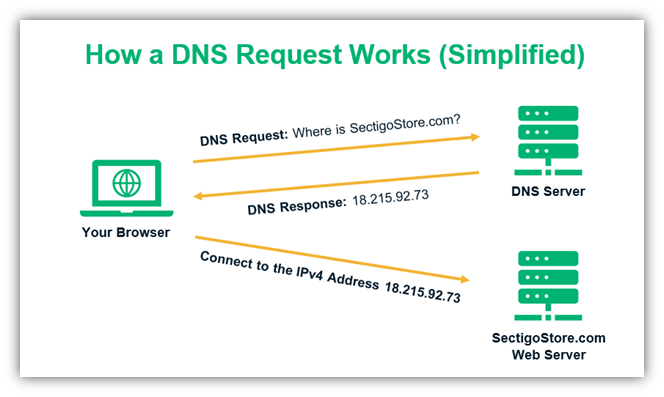
Basically, the domain name system serves as an intermediary between you and the website you are trying to open.
- When you type a website’s name, let’s say Amazon.com, in your web browser, the browser needs to find that website’s corresponding IP address to open it. So, it sends requests to DNS servers to track down the IP address. This request is sent via your internet service provider (ISP).
- The DNS server looks into its cache and responds to your browser with the website’s IP address from its DNS cache memory. If the DNS server can’t find it from the cache, it starts a four-step process that involves recursive resolvers, root nameservers, TLD nameservers, and authoritative nameservers. (Read more about these processes: DNS servers)
- After all these processes, the DNS submits the corresponding IP address of the website you are searching for to the browser. The browser connects to the server where that IP address is (website) is hosted. Hence, the DNS works like a phonebook or a directory. You gave it the name of a website, and it searches for the website’s IP address.
What Is a DNS Leak?
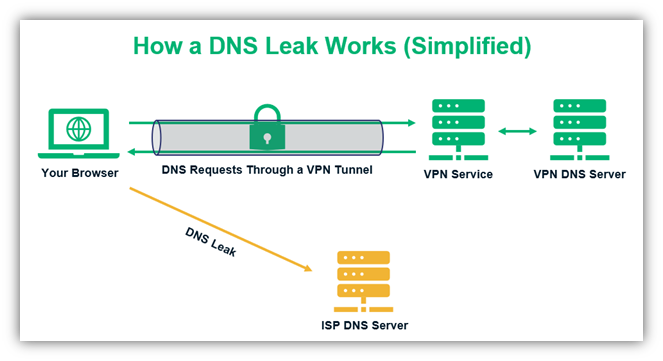
Now that we know what a DNS is and how it works, it’s time to answer the question, “what is a DNS leak?” In a nutshell, a DNS leak is a term that’s used to describe data exposure despite the use of a virtual private network (VPN). Basically, your DNS server requests are visible to third parties.
A VPN is a software that hides your original IP address and provides a new random IP address, which keeps changing frequently. It also creates an encrypted tunnel that securely transmits all the traffic between your browser, DNS, and the website’s server you are trying to connect! So, no one can track your online actions using your IP address.
But sometimes VPNs fail to hide your IP address and encrypt the communication. When this happens, they reveal your original IP address (provided by your ISP) to anyone who can intercept the traffic between your browser and DNS, causing the DNS leaks.
What Does a DNS Leak Mean in Terms of Privacy and Security?
So, a DNS leak means that someone can intercept the communications between your browser and DNS or steal the data from a DNS cache even though you’re using a virtual private network (VPN). This is also known as an IP leak.
But what does steal this type of data accomplish? It means that intruders can:
- Trace your device’s IP address,
- See what types of sites you visit (based on your browser’s DNS requests), and
- Monitor all your online activities.
But wait, don’t your ISP’s DNS servers already keep records of your DNS requests? Yes, if you’re using your ISP’s DNS servers by default instead of the VPN’s DNS servers. That’s because browsers need the internet to communicate, and your ISP (and its DNS servers) to make that happen by default if the VPN isn’t configured to use its own servers. That means your internet provider — and anyone else who can legally (or illegally) access their servers — can monitor all your actions online by tracing your IP address from the browser-IPS DNS communications.
What Causes a DNS Leak?
There are different reasons for why you can experience a DNS leak. A few potential causes of DNS leaks include:
- Your network’s DNS settings are incorrect or improperly configured.
- Your ISP may be using transparent DNS proxies.
- There are issues in your IPv4 to IPv6 transition process.
Needless to say, a DNS leak is no laughing matter. But how do you know if the DNS server you’re using is leaking?
How to Conduct a DNS Leak Test
As we mentioned before, by default, all the traffic between your browser and the DNS server is unencrypted. (This means that it’s sent in plaintext format, so anyone can read it.) Your ISP and any hacker can easily track all your online actions when they intercept this communication.
But if you’re using a VPN and worry that you have a DNS leak, you should follow these steps.
- Turn off your VPN.
- Open one of these websites: dnsleaktest.com or dnsleak.com.
- Note down the resulting information the page displays. This is going to be your ISP IP address, ISP’s name, hostname, and geographical location.
- Now, turn on the VPN and select any other geographical location of your choice.
- Once again, go to the DNS leak checking website and conduct the test. This time, you should see the different IP addresses, internet provider’s names, and geographical locations. If you still see your original ISP IP address and other details, your VPN is suffering from a DNS leak.
Check out the screenshot below of my DNS leak test — the first one I took without turning on the VPN, which shows my original IP address. Then, I turned on VPN and chose Mumbai as my geographic information. As you can see, all the details changed when I conducted the DNS test. It indicates that my VPN is not suffering from a DNS leak.
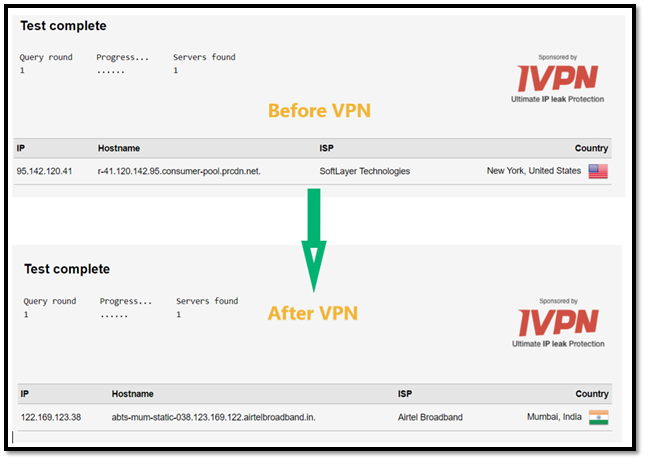
If your DNS leak test shows your DNS isn’t leaking, that’s great news. However, just know that it means that you’re not experiencing a DNS leak now — but that doesn’t mean you won’t experience one in the future. So, you may want to periodically re-test to ensure your DNS doesn’t have a leak.
But what if you discover that your DNS server is experiencing a DNS leak? What can you do to stop or prevent future DNS leaks?
How to Prevent DNS Leaks
As we know, DNS traffic and records tend to be insecure and unencrypted by default. This means that if you’re using your ISP’s DNS servers, you can’t prevent your ISP from tracking your actions or selling that data to advertisers (we’ll speak more to the dangers of DNS leaks shortly) except by taking the legal route. But these are some steps you can take to prevent DNS leaks from occurring.
Let’s break down the steps for how to prevent a DNS leak.
1. Use a Robust VPN
Using a secure and reliable VPN is the best way to hide your original IP address and encrypt the tunnel between your browser and DNS servers. But, sometimes, the browsers bypass the VPN’s IP address and access your original IP address to send the DNS requests. This causes DNS leaks. Hence, use the following tips while using a VPN:
- Enable DNS leak prevention feature. While purchasing a VPN, you should always check whether it has a DNS leak prevention feature.
- Use VPN monitoring software. VPN monitoring software keeps an eye on critical metrics to ensure the integrity of the VPN connection. They make sure that all the DNS requests pass through a VPN tunnel and can’t access the user’s original IP address.
It can immediately block the requests or alert the users if someone is trying to bypass the VPN IP address.
2. Clear DNS Caches
The DNS cache stores information of all your browsing history. If an intruder intercepts it, they can track all your online actions. So, keep flushing the DNS cache on a regular basis.
Here are a few quick steps you can take to delete your DNS cache on Windows:
- Click on the Start menu, search for cmd. Open the command prompt.
- Enter ipconfig/flushdns in the prompt.
3. Disable Microsoft Teredo
Microsoft Teredo is the technology that smooths the transition from IPv4 to IPv6 in Windows-based devices. Until all hosts are on IPv6, Teredo helps to give full IPv6 connectivity to the hosts that are on the IPv4 Internet.
While this is a great feature in many cases, it’s not perfect. Sometimes, it bypasses the VPN’s IP address and accesses the ISP’s IP address, causing DNS leaks. However, you can manually turn-off teredo by following these three steps:
- Click on the Start menu and search for cmd.
- When you see the command prompt apear, right-click on the icon and select Run as an administrator.
- Type in the following command: netsh interface teredo set state disabled.
Whenever you want to resume using Teredo again, type netsh interface teredo set state type=default into the command prompt to enable it.
4. Change Your Settings to Default to Use Your VPN’s DNS Servers
If you don’t use the default IPS DNS server, your ISP won’t be able to track your actions. You can use the VPN’s DNS server instead. Or if you decide to go the public DNS server route, only choose the DNS server provider that you completely trust. Check out this resource: How to use Google’s DNS server.
5. Use Secure DNS Service
There are some solutions, like Comodo’s Secure Internet Gateway, that provide a secured DNS connection on an enterprise level. It encrypts all the DNS traffic to prevent leaks. Apart from preventing DNS leaks, this tool also provides a DNS filtering service. It monitors all the DNS requests and blocks malicious websites. You can also manually change the settings and block the non-work-related websites to improve employees’ productivity.
Why Is a DNS Leak Dangerous?
For many people, it may not seem like that big of a deal. But for people who have concerns about their privacy or live in regions of the world where certain internet-related activities are prohibited, a DNS leak can be a big deal. DNS records can be used for anything from censorship to tracking or limiting internet use or even legal punishments. So, if you’re using a VPN to try to access content that’s prohibited or banned by your government, DNS records could be used against you.
For people who don’t have those same types of concerns, there are other privacy-related issues that can stem from DNS leaks. For example, your ISP can sell your browsing data to marketers and advertisers. They closely monitor all the webpages you visit, understand your interest areas and buying behaviors, and show the advertisements accordingly to manipulate your purchase habits.
And there’s also the cybercrime angle of concern. For example, if a hacker intercepts your data from DNS leaks, they can target you via sophisticated email phishing attacks that are based on this information. And if they know you or any of your coworkers frequently visit specific sites (such as a vendor’s website), they could create watering hole phishing websites to target you all as well.
That’s a scary thought, am I right? Let’s take a few moments to understand how hackers use your browsing history for phishing attacks with a hypothetical example.
Your DNS Request Data Could Be Used as Phishing Email Fodder
Let’s say an intruder uses your leaky DNS to their advantage and intercepts your DNS request data. They notice that you visit Chase bank’s website a lot. Although they can’t see your credentials and any confidential details due to the bank’s TLS/SSL certificates, but they notice that you frequently visit Chase bank’s website and web pages relating to student loans.
Bingo! The hacker knows that you’re at least interested in finding more about loans or are maybe even considering applying for one. So, the attacker sends you a sophisticated phishing email using Chase bank’s logo and writing style that’s designed to appear to be part of the bank’s loan approval process. In the email, they ask you for your social security number, bank account number, and other confidential details!
You, having been on the site and applied for the loan, might not think twice about such a request. This is why it’s not uncommon for people to fall for such traps.
Your Data Could Be Used for Malvertisement-Based Cyber Attacks
Malvertising means malware-laden advertisements, which attackers use to distribute viruses, trojan horses, worms, etc. onto victims’ devices. Data from DNS leak can be used to target people who visit specific websites via malvertising attacks.
Let’s consider another example. Say, a hacker intercepts your DNS cache and notices that your frequently visiting websites that provide tips to accelerate mobile phone’s speed. The hacker could create an advertisement on that website to lure you in: “Is your phone getting slow? It might be infected with a virus. Scan your phone now with this free antivirus software to detect and remove the viruses!”
If you click on that malvertisement, it could automatically download malware onto your device.
DNS Data Is a Great Social Engineering Resource for Cybercriminals
In social engineering attacks, the scam artists use social media and other tools to gather information about you to plot a cyber attack. With DNS leak, the hacker can track the pages, groups, and profiles you visited on social media and learn about your interests and the type of people you interact with. Then they use this info to:
- Guess your login credentials.
- Make fake profiles/ groups to interact with you and persuade you to share your personal info.
- Send you malware-loaded files or attachments in the inbox.
- Send you links that take you to spammy or malicious sites.
In the same way, advertisers can also track your social media activities and show the advertisements accordingly. In short, your browsing behavior is way more valuable to advertisers and hackers than you imagine!
Final Words on DNS Leaks & How to Prevent Them
Just like any other technology, DNS has its weak points. A DNS leak makes it easy for intruders (both hackers and advertisers) to gain valuable information about you from the web pages you visit. They can know a wide variety of information, including your:
- Bank,
- School,
- Workplace,
- Favorite ecommerce sites,
- Insurance company,
- Likes, dislikes, and areas of interest,
- Concerns you are facing (or may be seeking solutions for), and
- People you communicate with on social media.
While advertisers craft their ads to manipulate your buying behavior, hackers can use this info to execute sophisticated phishing attacks, distribute malware, and plot ransomware attacks. That’s why you should always use robust VPN software and other prevention methods to stop DNS leaks from happening in the first place.





















2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security